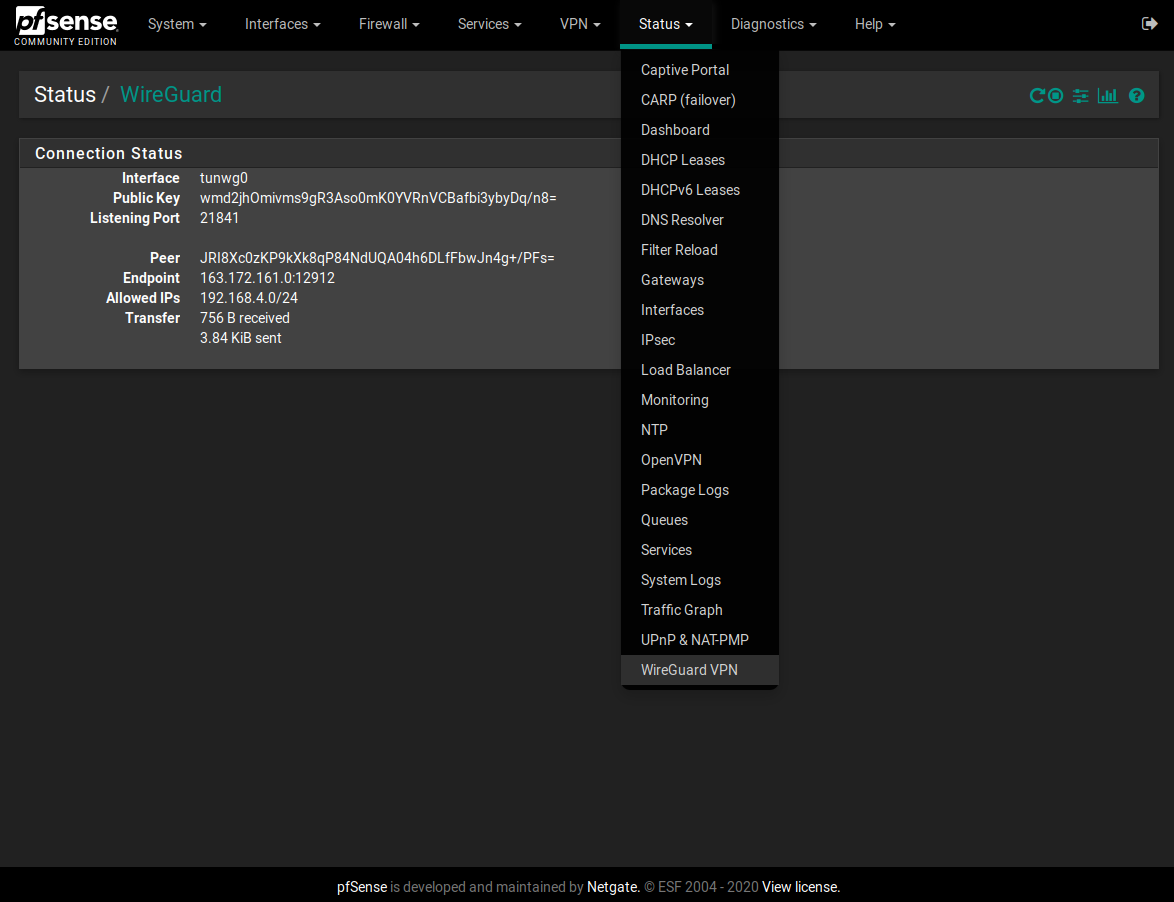
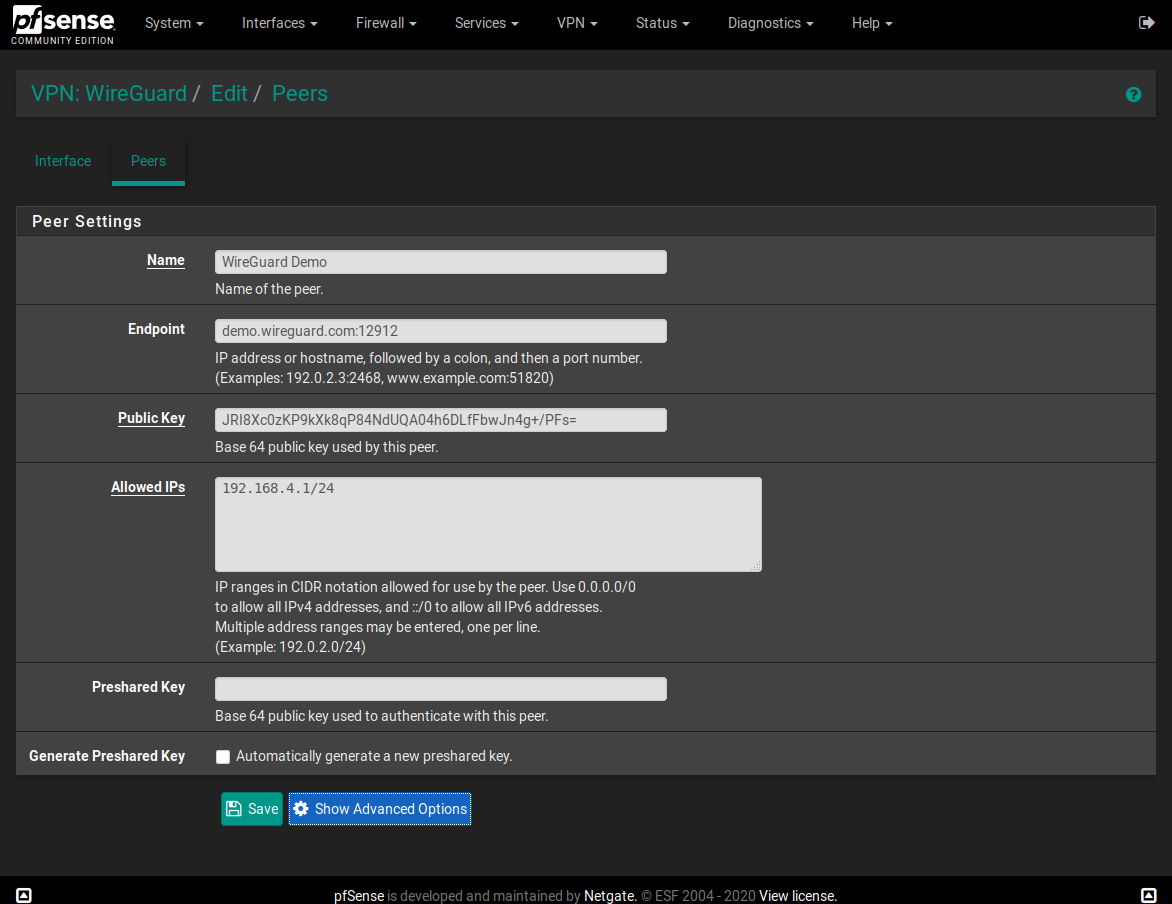
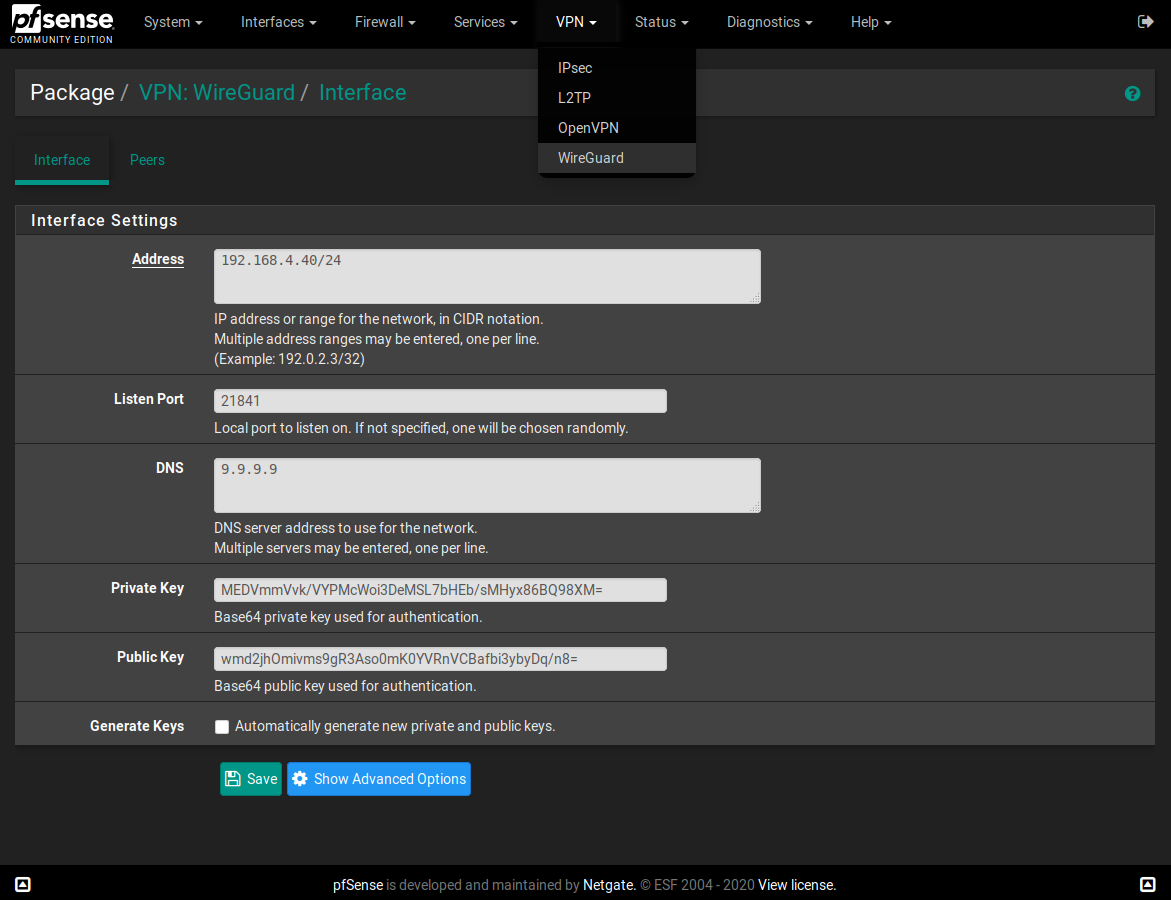
I made a WireGuard package for pfSense
-
Ascord, Fantastic job with this thank you !!!
But I have a few issues though.. i can get my device to handshake with the 'Netgate Wireguard'. but i'm unable to access any of my servers on the lan .. am i missing really obvious something ?
-
Hi all,
Good Job , thank you.
I have a question about the package if it's only works as client or can work as a server too? -
@moelharrak There is not much difference in server vs client configuration, so in general, yes, it works. Server just has the listen directive to know on that UDP port it can receive communication through firewall. Client has to know ip and port, where to connect in endpoint directive. The connection is then managed by wireguard automatically.
https://www.wireguard.com/quickstart/#nat-and-firewall-traversal-persistence
https://docs.sweeting.me/s/wireguard#How-WireGuard-Routes-Packets -
Anyone know if this wireguard setup keeps working after updating pfsence to 2.4.5_1?
Im currently on 2.4.5 and have no issues with wireguard. Just debating if i should update or not. Thanks. -
@alirz Hi, I'm using it without any kind of problem, since the release of 2.4.5-RELEASE-p1.
-
@dubatech thanks, do you think if I upgrade from 2.4.5 to 2.4.5-1, I will have to reinstall and re-configure the wireguard?
-
Greetings to all! And immediately I apologize for my English. Dear Ascrod, the wireguard service does not start if I specify several Allowed IPs in the peer settings. If one is Allowed IPs, then the service starts.
I'm using 2.4.5-RELEASE-p1 (amd64)
FreeBSD 11.3-STABLE -
@wion said in I made a WireGuard package for pfSense:
Greetings to all! And immediately I apologize for my English. Dear Ascrod, the wireguard service does not start if I specify several Allowed IPs in the peer settings. If one is Allowed IPs, then the service starts.
I'm using 2.4.5-RELEASE-p1 (amd64)
FreeBSD 11.3-STABLEthe problem was adding subnet 172.20.0.0/20. Until I changed the mask to / 16, the service did not work
-
@alirz You will have to reinstall the wireguard package, but not reconfigure the firewall.
-
I have upgraded to 2.4.5-p1, based on FreeBSD 11.3-STABLE.
I have uninstalled the old version of wireguard, but cannot install the new one.
I am trying to download "wireguard-go-0.0.20200320.txz" and "wireguard-1.0.20200513.txz" for FreeBSD: 11: amd64 without success.
Could someone share it or upload it somewhere?
-
I have got it:
https://pkg.freebsd.org/FreeBSD:11:amd64/quarterly/All/wireguard-1.0.20200827.txz
https://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz
-
will a reinstall of the new WG modules keep the WG config in place or will have to reconfigure it again.
-
@pepe00 said in I made a WireGuard package for pfSense:
https://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz
Did this work for you? I am seeing the GUI, but the Generate button does nothing, nor does the generate peer config button, so I removed the packages fearing other things may not work either. Looking for a setup that works per the config instructions on 2.45p1.
Actually, I get this as well, and this is likely the issue but I've done nothing special to my 2.4.5-p1 install so I don't know why it would be unique to me:
Newer FreeBSD version for package wireguard-go:
To ignore this error set IGNORE_OSVERSION=yes- package: 1104001
- running kernel: 1103507
Ignore the mismatch and continue? [y/N]: n
-
I've also posted this same question in the torguard forms, but my issue is far more related to routing than torguard itself so I'm hoping someone can point me in the right direction.
I got wireguard in pfsense and all is fine with wireguard itself(at least I think it's not the issue)
Now want to direct some traffic out wireguard and other traffic out WAN
Once I connect the wireguard all NON-vpn devices lose access to the Internet - they can still communicate with each other inside the network but lose the ability to do anything internet based. However my VPN devices are working as they should, I haven't confirmed they are doing DNS properly yet as I want to get my other devices working first.
To get wireguard working I used steps from:
https://forums.torguard.net/index.php?/topic/1975-ascrod-ashus-pfsense-pkg-wireguard-tutorial-guide/
Worked well, only "issue" was figuring out the repo's and current version stuff...Basically I only have a few hosts to send out wireguard, the majority will use WAN (including DHCP clients)
I'd like to take a group of IP's and make those go out the VPN, and anything else not.
WAN interface has public internet IP - 68.x.x.x
LAN gateway, this is gateway on all devices - 192.168.1.1
DHCP Range - 192.168.1.130 - 192.168.1.254Created an alias:
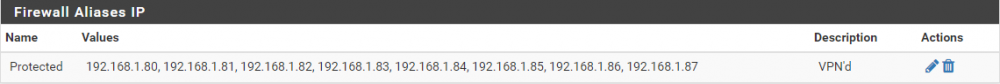
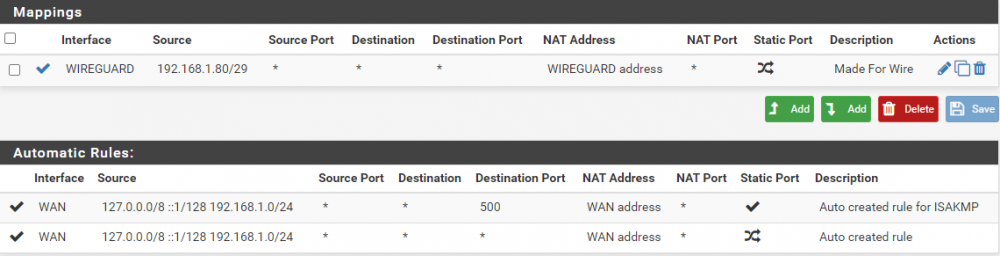
configured NAT/Outbound - Hybrid Outbound
I THINK this is allowing the wanted "protected" devices out via the VPN - this is good and what I'm wanting.
In Firewall/Rules/LAN I have the following:
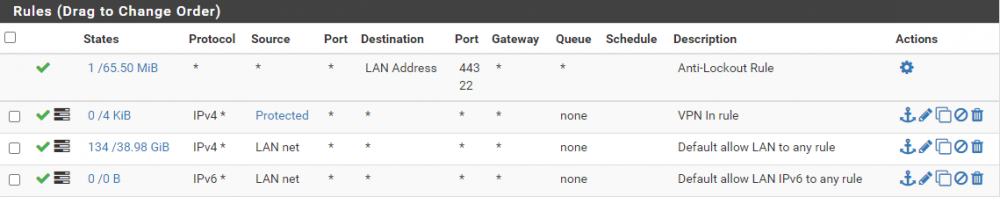
Most examples for building this type of routing rules have involved openVPN and are from 2015. While this should be getting me close I still am not getting it to work. The things i"ve read indicate that the VPN connection should become a second gateway, and I'd just set that as the gateway on the VPN devices. However when I bring the wireguard connection up there is no second gateway getting auto-magically created. Do I have to create one? Shouldn't the rules I've put in place allow the flow of traffic over VPN, and if not meeting VPN then it flows over regular?
-
While risking getting banned, I wanted to inform you guys I've decided to move over to opnSense. It is an open-source pfSense fork where official authors do keep it up-to-date with latest technologies and support Wireguard natively.
-
I don't think there is any problem, people are free to choose what they want, and for a home user maybe opnSense can be a good choice, for me it's a question of who to trust
someone with more stuff without quality check or someone with less stuff but rock-solid?
in my case, quality over quantity was my answer -
@trevorstuart Everything I've been reading on setting up the routing so some goes out VPN and the rest not indicates I should have a second gateway. But I'm only seeing my original default gateway?
Will a new gateway appear when wireguard is connected? -
@johnpoz This would be handy, a nice guide on setting up a box until PfSense are ready.
-
@trevorstuart If this is anything like how I send traffic out via OpenVPN , then you need to set that protected Alias to go out via the WIREGUARD as a gateway, you can create a gateway.
-
@RumMonkey69 created a gateway and set the VPN alias to use that. But it's still sending all traffic out the VPN, not just the IPs in the alias.