How to set up PfSense to home switch, and to cyber lab switch
-
So I have a PC set up as a dedicated PfSense box, with a 4-port Intel card in it. I have it set up right now between my ISP fiber modem, and my Ubiquity home network (16-port POE switch with controller, and 2 WAPs).
Interface 1= WAN
Interface 2 = LAN (Ubiquity)I also have just set up a home lab for cyber security work that consists of 3 poweredge servers and a Cisco 3750 Catalyst [WS-C3750-48PS-S] switch. (There is also a Cisco 2811 router, but it is not useable due to having no CF card and no software....and I'm not paying Cisco for a service contract just to be able to download the software...)
I would like to set up the home lab on Interface 3 of the PfSense box, but have the Cisco switch act as the home lab DHCP server. How would I set this up in PfSense, and in the switch, so that the homelab can get out to the internet, and the switch is it's own DHCP server?
Interface 3 = Cisco Catalyst C3750 switch
I started to configure everything, but got a little confused at the point I am having to set up the default gateway in the switch. I want my IPs in the Cisco switch to be 10.0.0.0/24, my PfSense interfaces are 10.10.x.x. , the default gateway for everything else in the home network is the 10.10.10.1 PfSense LAN...just not sure if the Cisco switch's gateway should be the 10.10.10.1, or 10.0.0.1.
-
So you want to use your c3750 as a downstream router?
If so then you would connected it via a transit network.. Or do you just want everything in your lab on this 10.0.0/24 network? With the switch just acting as the dhcp server for the 10.0.0/24 network? And pfsense doing all the routing?
Will you have other networks behind the L3 switch?
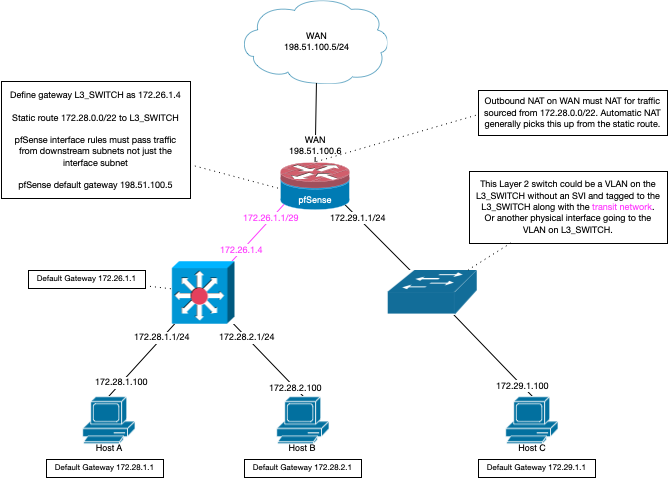
Derelict has a nice drawing in this thread on how to use a downstream router (L3 switch)
https://forum.netgate.com/topic/152311/resolved-pfsense-config-when-using-vlan-routing-on-an-l3-switch
-
Yes, I would like everything in the lab on the 10.0.0.0 network, behind the L3 switch. In that diagram, the 172.29.x.x switch would be my Ubiquity L3 switch for the home, and the 172.28.x.x switch would be the Cisco L3 switch for the home lab.
-
Well there is nothing to do here really.. Other than turn off dhcp on pfsense for the interface your connecting this switch. Your just using it as a L2 switch.
If you gave the switch an IP on the 10.0.0/24 network - then the switches gateway would be the IP of the pfsense interface, 10.0.0.1 But the one only reason you would need a gateway on the switch is if you want the actual switch to be able to get to other networks, ie the internet.
All the devices on this network would use pfsense as their gateway, 10.0.0.1
Your just using the switch as a dumb switch then.. Do you plan on using any vlans on this switch, then you would need to change the connection to trunk port that is connected to pfsense. And setup the vlans on pfsense so you could route between them.
Out of curiosity, since your not going to use this switch as L3 and route on it - what is the point of running dhcp on it - why not just run that on pfsense? Can tell you for sure the dhcpd on pfsense is easier to use and more robust than the dhcpd you can setup on that switch ;)
-
I would like to get the practice with the Cisco switch, in a kind of enterprise environment. I do want the lab to be able to reach the internet for updates and downloads and such but don’t want the lab to be able to reach any other networks. I currently have 4 VLANS on the PfSense, through the Ubiquity switch, one VLAN for my stuff, one for IoT stuff, one for the kids and one other. I may set up VLANS on the Cisco switch as I will have some VMs on the servers in the home lab...one kali machine, one metasploitable machine, one for a SIEM, and probably a Windows server and Ubuntu server. I will want to set up one for active directory as well. I basically want the lab to be its own network, with internet access through the PfSense box.