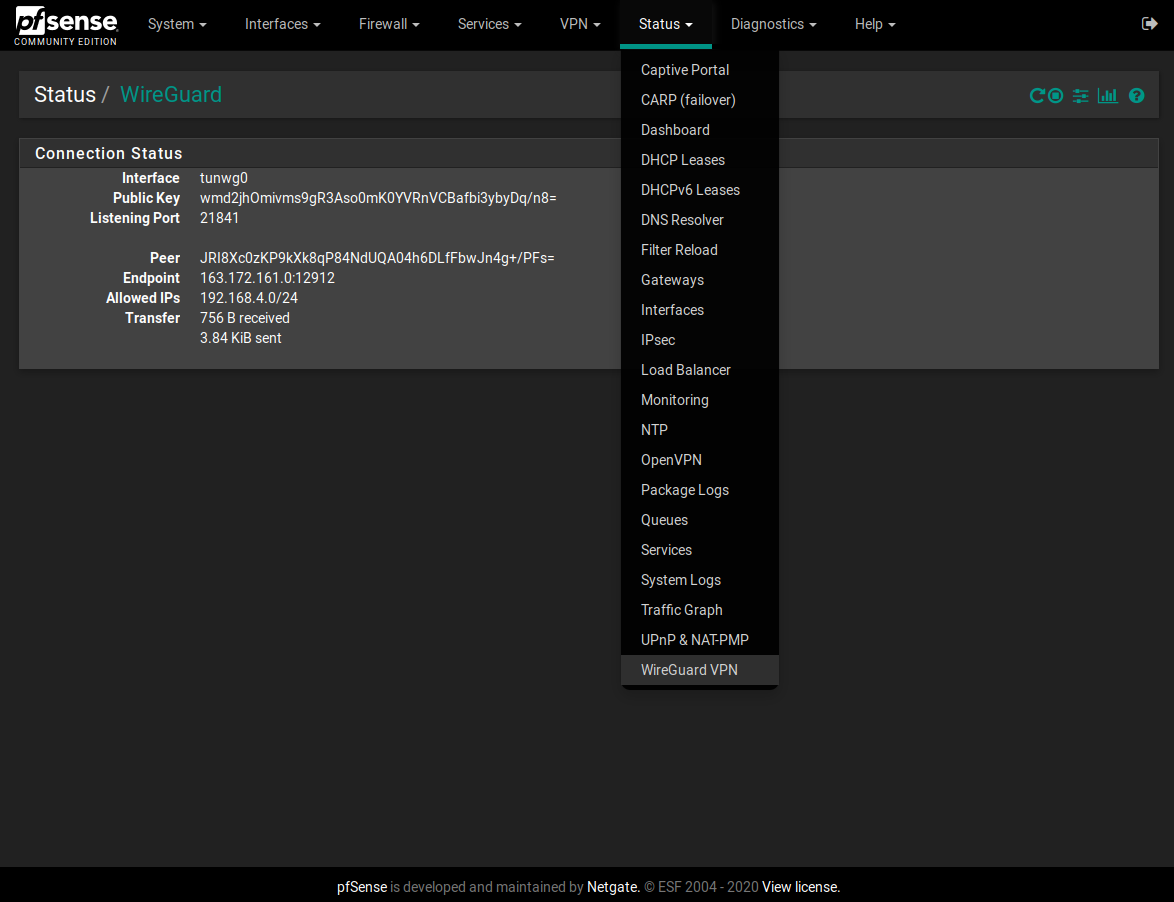
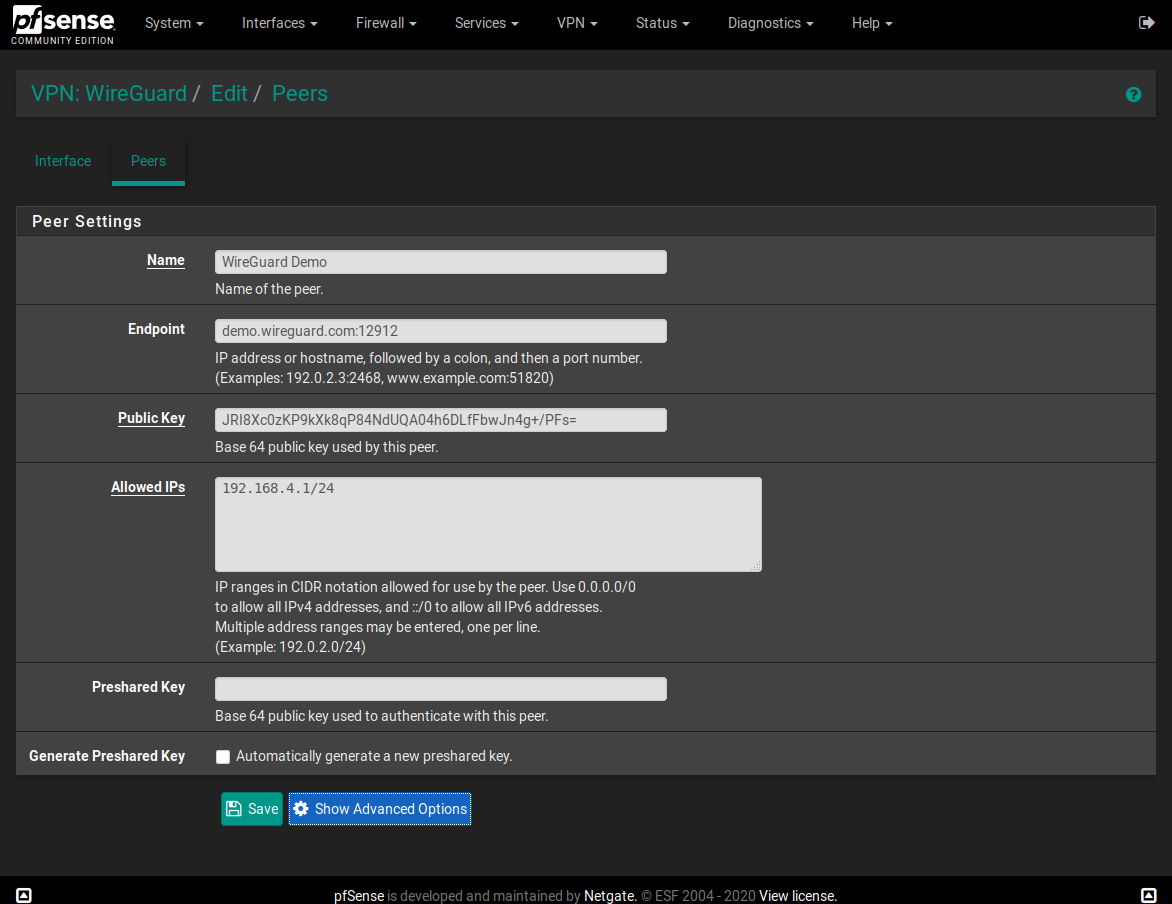
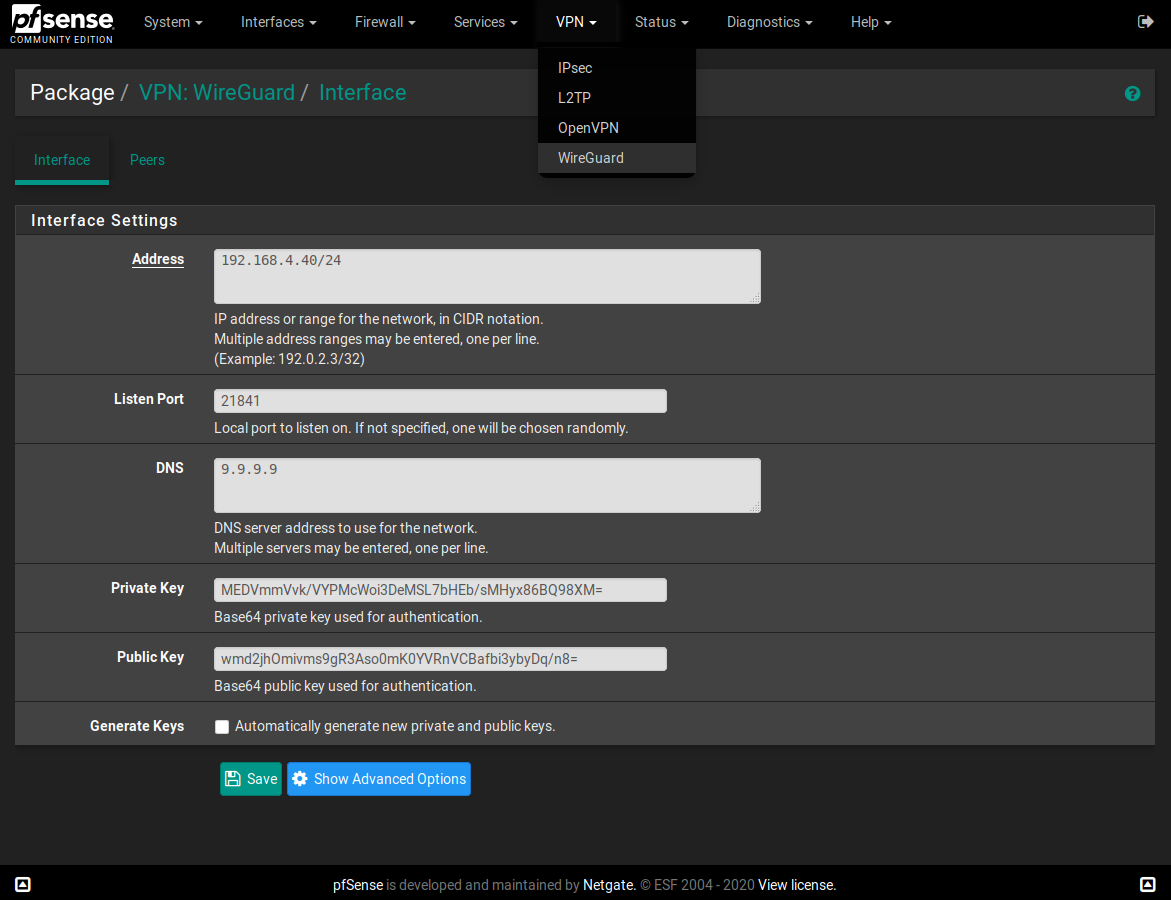
I made a WireGuard package for pfSense
-
@pepe00 said in I made a WireGuard package for pfSense:
https://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz
Did this work for you? I am seeing the GUI, but the Generate button does nothing, nor does the generate peer config button, so I removed the packages fearing other things may not work either. Looking for a setup that works per the config instructions on 2.45p1.
Actually, I get this as well, and this is likely the issue but I've done nothing special to my 2.4.5-p1 install so I don't know why it would be unique to me:
Newer FreeBSD version for package wireguard-go:
To ignore this error set IGNORE_OSVERSION=yes- package: 1104001
- running kernel: 1103507
Ignore the mismatch and continue? [y/N]: n
-
I've also posted this same question in the torguard forms, but my issue is far more related to routing than torguard itself so I'm hoping someone can point me in the right direction.
I got wireguard in pfsense and all is fine with wireguard itself(at least I think it's not the issue)
Now want to direct some traffic out wireguard and other traffic out WAN
Once I connect the wireguard all NON-vpn devices lose access to the Internet - they can still communicate with each other inside the network but lose the ability to do anything internet based. However my VPN devices are working as they should, I haven't confirmed they are doing DNS properly yet as I want to get my other devices working first.
To get wireguard working I used steps from:
https://forums.torguard.net/index.php?/topic/1975-ascrod-ashus-pfsense-pkg-wireguard-tutorial-guide/
Worked well, only "issue" was figuring out the repo's and current version stuff...Basically I only have a few hosts to send out wireguard, the majority will use WAN (including DHCP clients)
I'd like to take a group of IP's and make those go out the VPN, and anything else not.
WAN interface has public internet IP - 68.x.x.x
LAN gateway, this is gateway on all devices - 192.168.1.1
DHCP Range - 192.168.1.130 - 192.168.1.254Created an alias:
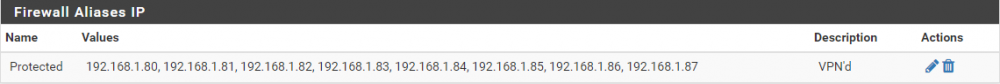
configured NAT/Outbound - Hybrid Outbound
I THINK this is allowing the wanted "protected" devices out via the VPN - this is good and what I'm wanting.
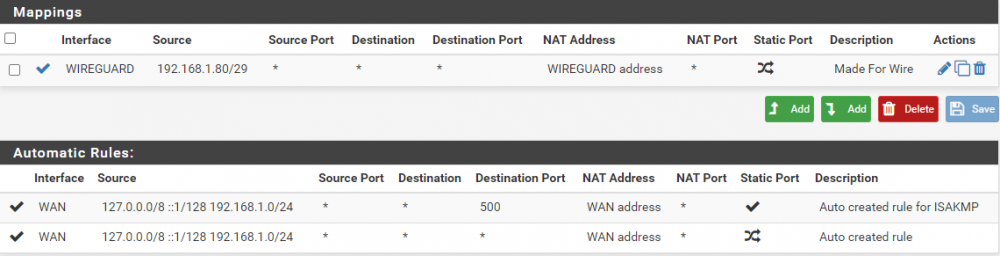
In Firewall/Rules/LAN I have the following:
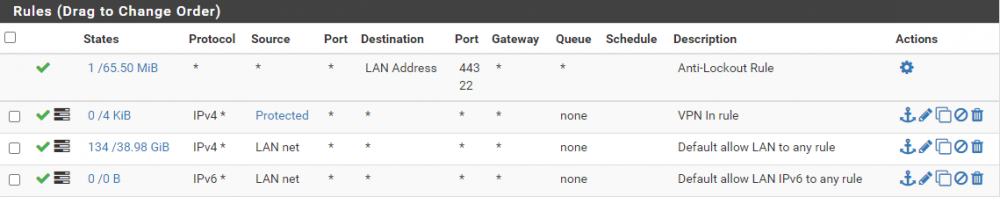
Most examples for building this type of routing rules have involved openVPN and are from 2015. While this should be getting me close I still am not getting it to work. The things i"ve read indicate that the VPN connection should become a second gateway, and I'd just set that as the gateway on the VPN devices. However when I bring the wireguard connection up there is no second gateway getting auto-magically created. Do I have to create one? Shouldn't the rules I've put in place allow the flow of traffic over VPN, and if not meeting VPN then it flows over regular?
-
While risking getting banned, I wanted to inform you guys I've decided to move over to opnSense. It is an open-source pfSense fork where official authors do keep it up-to-date with latest technologies and support Wireguard natively.
-
I don't think there is any problem, people are free to choose what they want, and for a home user maybe opnSense can be a good choice, for me it's a question of who to trust
someone with more stuff without quality check or someone with less stuff but rock-solid?
in my case, quality over quantity was my answer -
@trevorstuart Everything I've been reading on setting up the routing so some goes out VPN and the rest not indicates I should have a second gateway. But I'm only seeing my original default gateway?
Will a new gateway appear when wireguard is connected? -
@johnpoz This would be handy, a nice guide on setting up a box until PfSense are ready.
-
@trevorstuart If this is anything like how I send traffic out via OpenVPN , then you need to set that protected Alias to go out via the WIREGUARD as a gateway, you can create a gateway.
-
@RumMonkey69 created a gateway and set the VPN alias to use that. But it's still sending all traffic out the VPN, not just the IPs in the alias.
-
I now have the split traffic going the way I want.
It required changing the Default LAN to any rule to specifically use the "real" Gateway. Seems wireguard becomes the pfsense "default" so the built in LAN to any rule stops functioning... -
@burntoc You are right, the packages and the gui are installed, but it doesn't work correctly.
The problem is that the repositories for FreeBSD11 no longer work and I can't find the correct packages.
Could anyone help us find the packages for 2.4.5_p1 or FreeBSD11?
-
Dear pepe00,
Hello and I hope that you are well and safe. I wrote a tutorial walk through for this whole process and posted it here below :https://forums.torguard.net/index.php?/topic/1975-ascrod-ashus-pfsense-pkg-wireguard-tutorial-guide/
The bottom line is that you should use this FreeBSD repo mirror located in South Africa :
http://pkg0.jinx.freebsd.org/FreeBSD:11:amd64/latest/All/
for pfSense 2.4.5_p1 and forpfsense 2.5.0 this repo below :
http://pkg0.jinx.freebsd.org/FreeBSD:12:amd64/latest/All/
Again the tutorial pretty much explains all - once again look at :https://forums.torguard.net/index.php?/topic/1975-ascrod-ashus-pfsense-pkg-wireguard-tutorial-guide/
Peace and Be and Stay Well
-
Hey Ascrod, thanks for your great work!!! would you be able to make that work for a clustered environment (pfSense High Availability)? and a second idea: would it be complicated to make your WEB-GUI working for more than one interface?
thanks again! Cheers, Sven.
-
Nice work ;)
I have A Netgate SG-3100 running 2.4.5-RELEASE-p1 (arm) built on Tue Jun 02 17:45:24 EDT 2020 FreeBSD 11.3-STABLE
Is there A install for that?
I'm now running this error.
pkg: wrong architecture: FreeBSD:11:amd64 instead of FreeBSD:11:armv6Thanks in advance.
-
Hi all - A question on routing with Wireguard
I have Wireguard setup pfSense acting as a VPN concentrator (Road Warrier) and also as a Site to Site connection.
From my local pfSense I want to be able to use the site-2-site connection , reach the remote Wireguard server and then break out to internet from there. I have successfully configured this.To get this to work I use 0.0.0.0/0 in the allowed-IP of peer-config in the pfSense.
As you you would imagine this also adds a default route to the pf routing table (with a higher pref than the local route ) and all LAN traffic then starts flowing over the site-to-site tunnel. What I want to get to is use this site-2-site tunnel for only certain LAN devices and not all. So for instance my appleTV behind pfSense could use this and break out to the internet from the remote Wireguard server.
What have I have explored
- Tried to change the gateway of the other devices to the WAN_DHCP - this breaks a few things for me
- Tried adding Table = off in the peer config to prevent this route from getting added. Does not work
- Adding specific IP's to the peer config instead of default will not work as administrative headache of maintaining those is too high.
PFsense Wireguard config
[Interface]
Address = 10.100.100.1/24
ListenPort = 51820
DNS = 192.168.11.5
PrivateKey = xxxx[Peer]
PublicKey = yyyy
AllowedIPs = 0.0.0.0/0Route Table after activating Wireguard Site to Site tunnel.
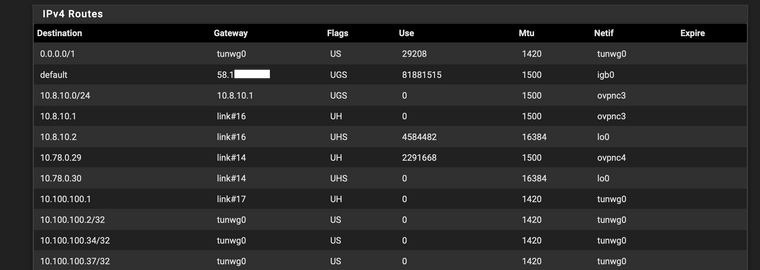
-
@ab5g the config is different for pfsense and the peer. By specifying 0.0.0.0/0 on pfsense you are telling that it can send all traffic down the tunnel. That's not what you want, you only need traffic destined for your client/peer to go down the tunnel.
On pfsense the AllowedIPs should be the one IP address the client/peer is using. Mine looks like this:
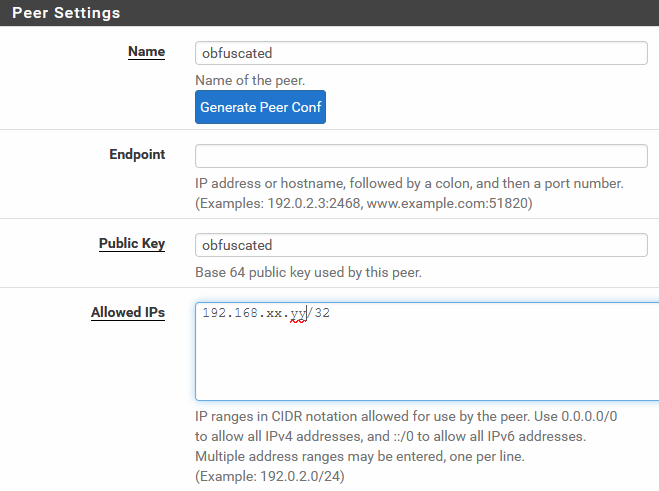
The client/peer config on the other hand would look something like this;
[Interface]
Address = 192.168.xx.yy/32 #make sure this matches the IP in the pfsense config
DNS = 192.168.xx.1 #you can make this an interface on the pfsense (even the tunnel interface, just make sure the resolver is listening on the interface
PrivateKey = obfuscated[Peer]
Endpoint = [pfsense public ip]:[pfsense wiregaurd port]
PublicKey = obfuscated
AllowedIPs = 0.0.0.0/0 -
Thank you for replying. The reason I have a 0.0.0.0/0 on the pfSense WireGuard Peer is because I want certain LAN devices (like AppleTV) to use the Wireguard tunnel and exit to the internet from the remote site.
Remote IP is 10.100.100.50
Remote LAN is 192.168.29.0/24So if I specify allow only the 2 IP above in my peer config on pfSense- I will only be able to reach the remote LAN, but not break out to the internet from remote Wireguard server.
Unfortunately with a 0.0.0.0/0 as the WireGuard Peer, it creates a more specific route in the routing table, forcing all LAN traffic to flow to the remote site instead of certain LAN devices
-
@ab5g
I see. I don't have experience on an outbound "VPN" like this with wg. But I note others in this thread have had the same problem. I'm not sure if a resolution was found. -
You can goto System>Routing and Add a new Gateway pointing it to the new WireGuard interface. You can then use it like a a normal gateway. The gateway will not appear automatically.
After you create a gateway, I ran into some routing issues related to my setup that I have explained in a post above. -
Solved it. Added the following configuration to the tunwg0.conf file ( can be done through the command line or the GUI).
PostUp = route delete 0.0.0.0/1
This deletes the route from the routing table, allowing pfSense to route based on source IP's.
-
@burntoc I'm in the same boat.
[2.4.5-RELEASE][admin@my-pfsense]/root: pkg add https://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20201118.txz Fetching wireguard-go-0.0.20201118.txz: 0% Fetching wireguard-go-0.0.20201118.txz: 100% 890 KiB 911.1kB/s 00:01 Installing wireguard-go-0.0.20201118... Newer FreeBSD version for package wireguard-go: To ignore this error set IGNORE_OSVERSION=yes - package: 1104001 - running kernel: 1103507 Ignore the mismatch and continue? [y/N]:I'm on an SG-5100 running 2.4.5-RELEASE-p1 which is supposed to be the most up to date (as of this post). Anybody this out? I'm assuming I shouldn't mismatch.
-LamaZ