DNS Leaks using DNS Resolver
-
10.8.8.1 is for the ProtonVPN gateway. I have set up NAT forwarding rules for it.
Here are the DNS server settings, sorry, will double check when I post now to make sure everything is in the message.
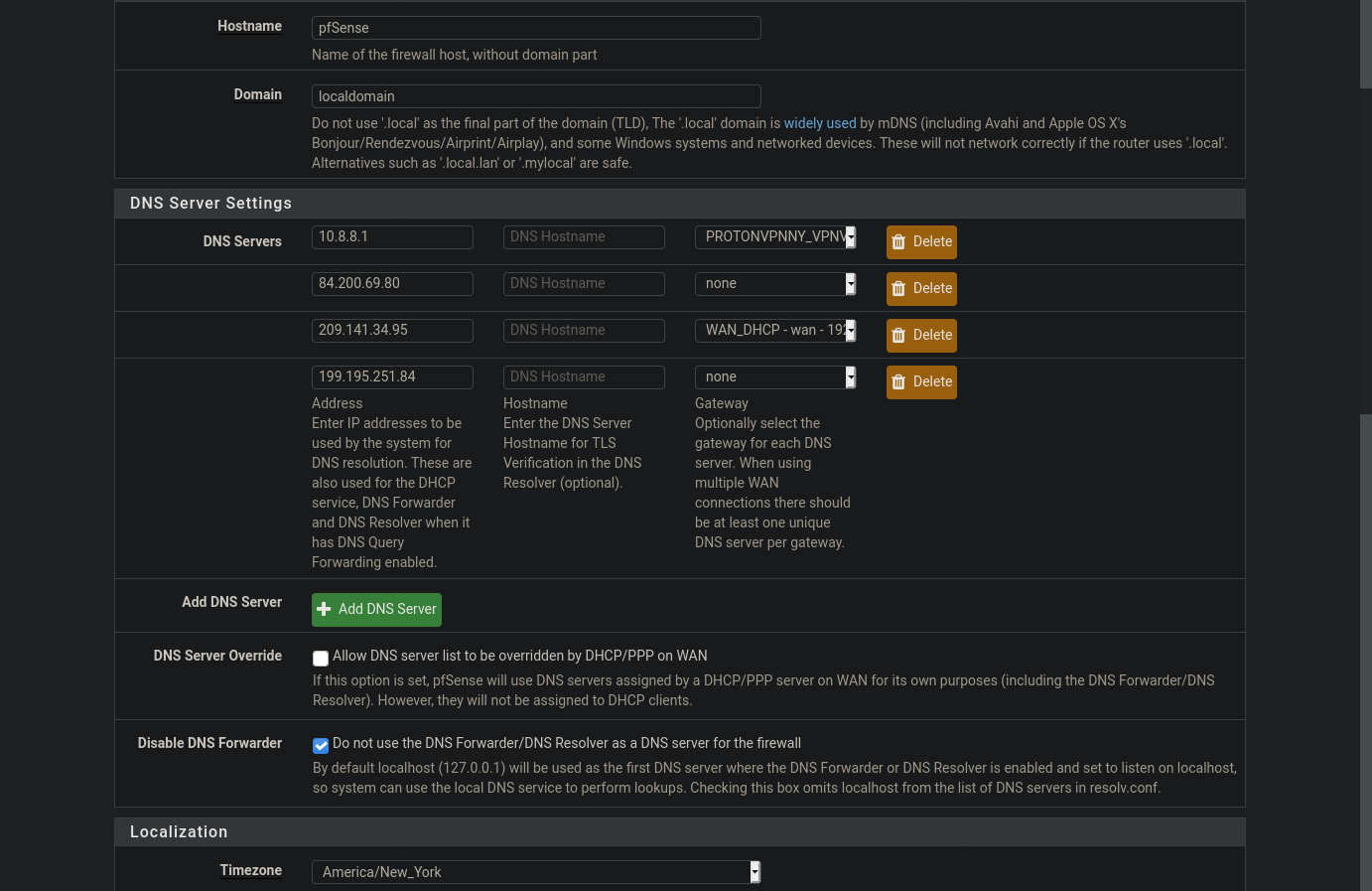
These are the NAT settings that I have, for context about the Proton gateway
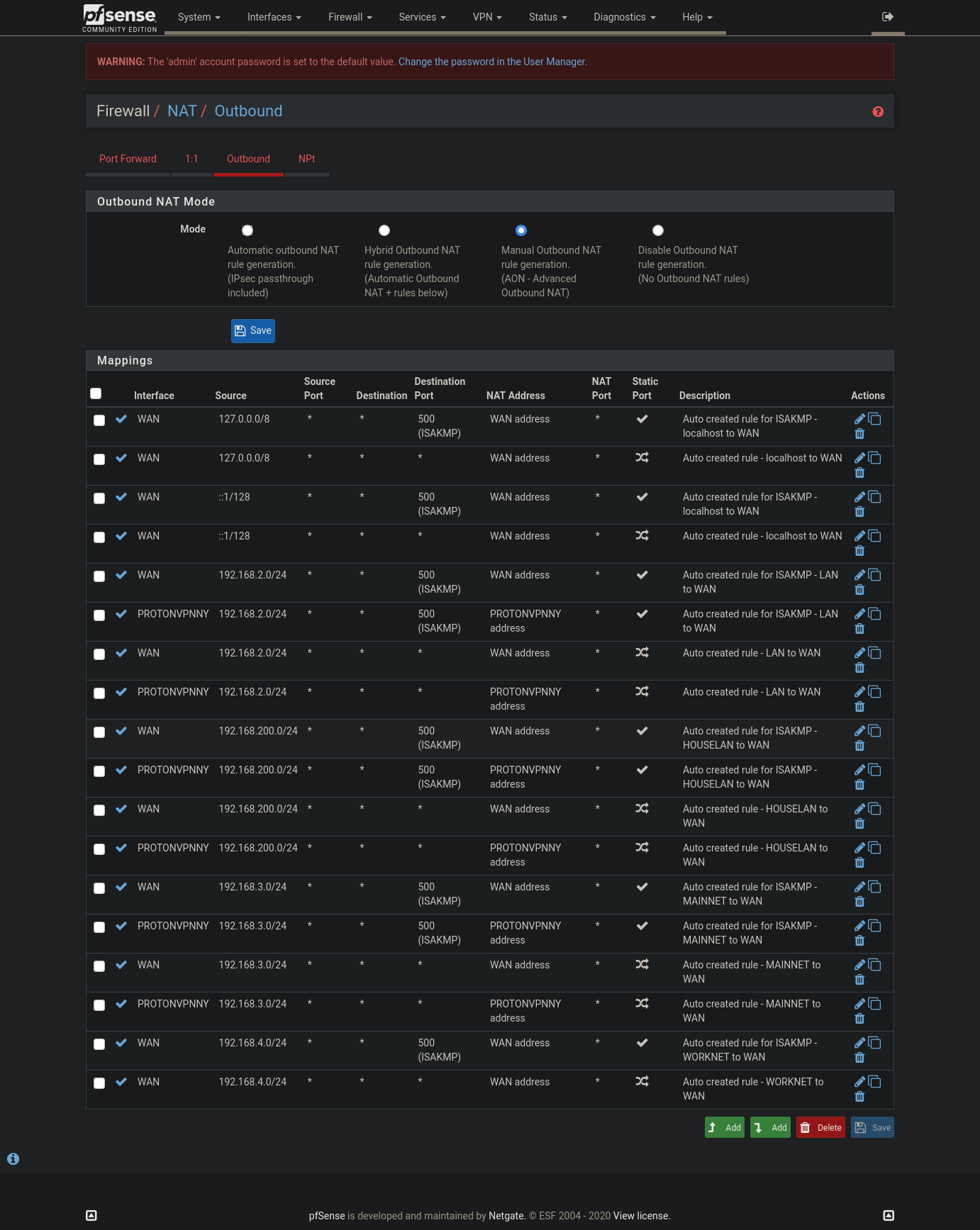
edit:
Here are the settings in my Netgear modem.
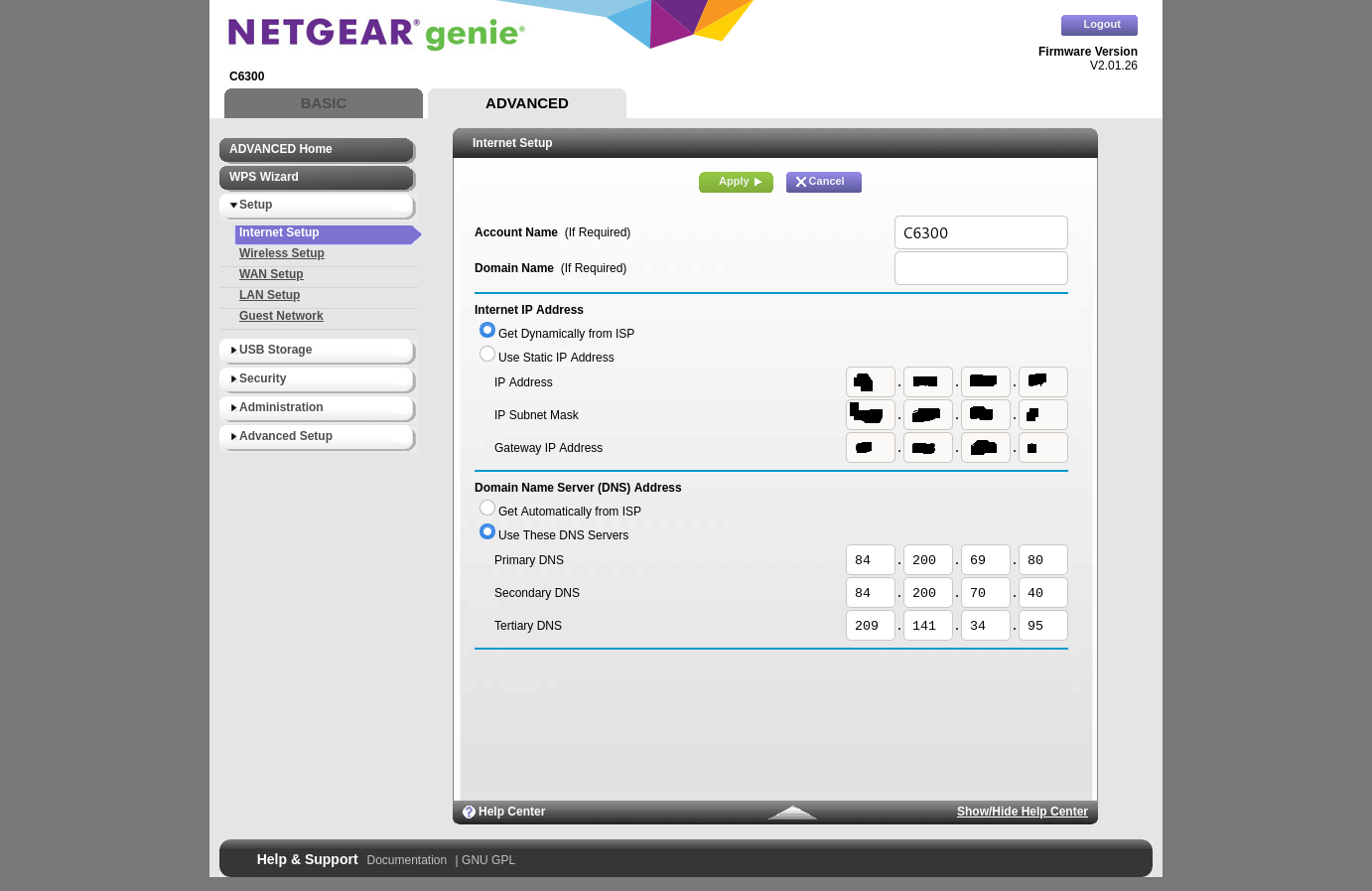
I have set the desired DNS servers so when I run a leak test, it only shows one or more of these three. But when I have it set to get automatically from ISP, ill see their DNS servers show up in a leak test. This is what I am trying to avoid. There is no way for me to leave these blank, dont even know if that would serve for this but either way, my DNS requests will be sent to one or two of the servers I have set in pfsense but I will also see my ISPs DNS servers in the leak test. I will change this back to my get automatically from ISP and run a leak test at dnsleaktest.com and ipleak.net so i can show the results
-
Pfsense is not set to ask that router for dns - is I don't see it listed.. so pfsense would never ask it.. Unless pfsense was set to get dns from isp... Which you turned off - so unless something asks that router for dns - your isp dns would not be used.
-
This is exactly my frustration. I'm a complete noob to pfsense so I wasn't sure if i missed something or that I misread directions on how to set this up.
I'm going to set the modem router to use my ISPs DNS and then run a couple tests so I can get screenshots of the repro.
@johnpoz Thanks for confirming that I haven't done this to myself and just set it up wrong. -
What client are you testing from - if its on that routers wifi, and using that routers dhcp the client would ask your router, which would then ask whatever you have in that router for dns.
-
I was using wifi, which was connected to a wifi AP that Ive setup. That is set to forward all requests to pfsense. I also am testing on a client that is connected to a switch that has two VLANs running through it. The clients I was testing with were not connected to the Netgear routers wifi.
Here are the DNS tests that I ran to see what happens when I set the modem router DNS to googles resolvers 8.8.8.8 and 8.8.4.4 pfsense still has the same DNS servers as before.
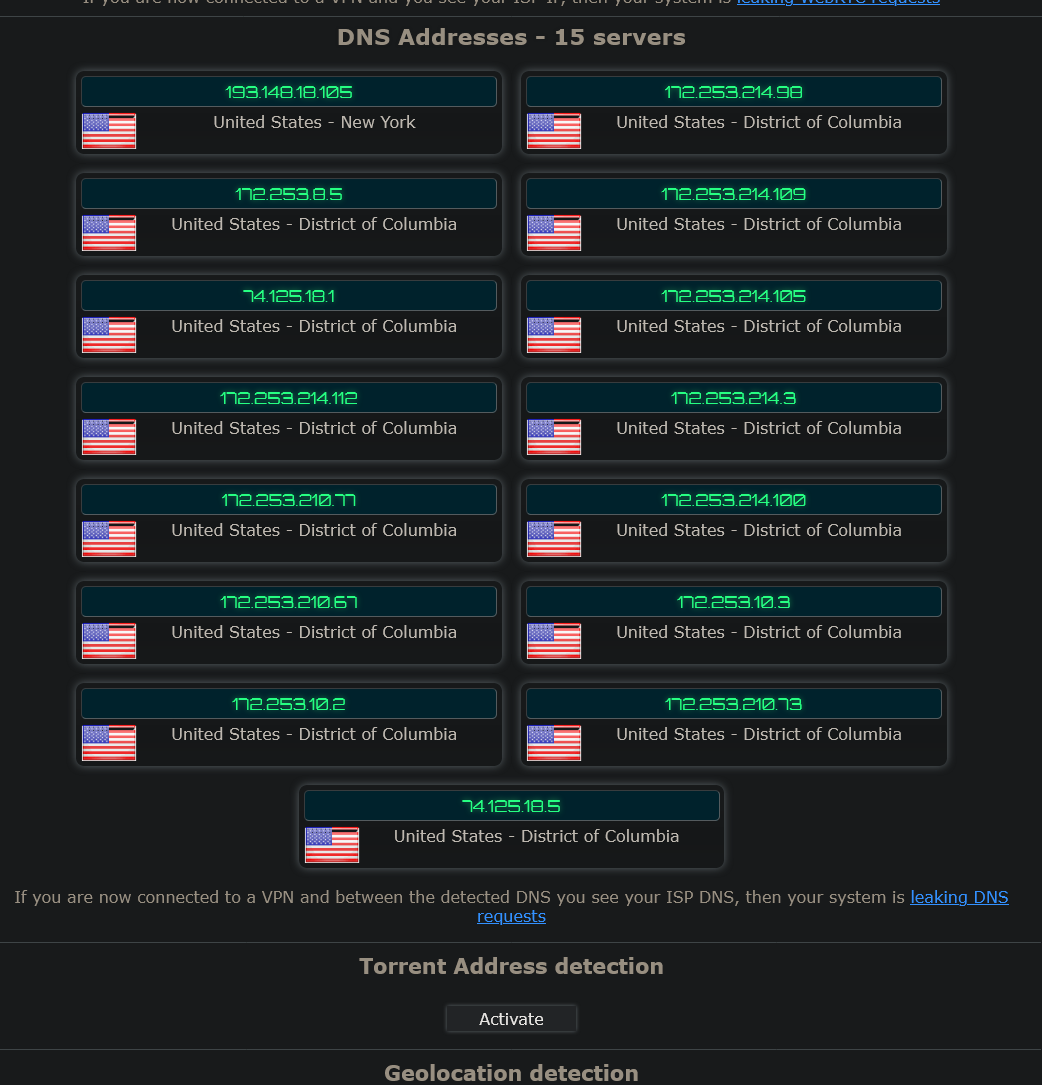
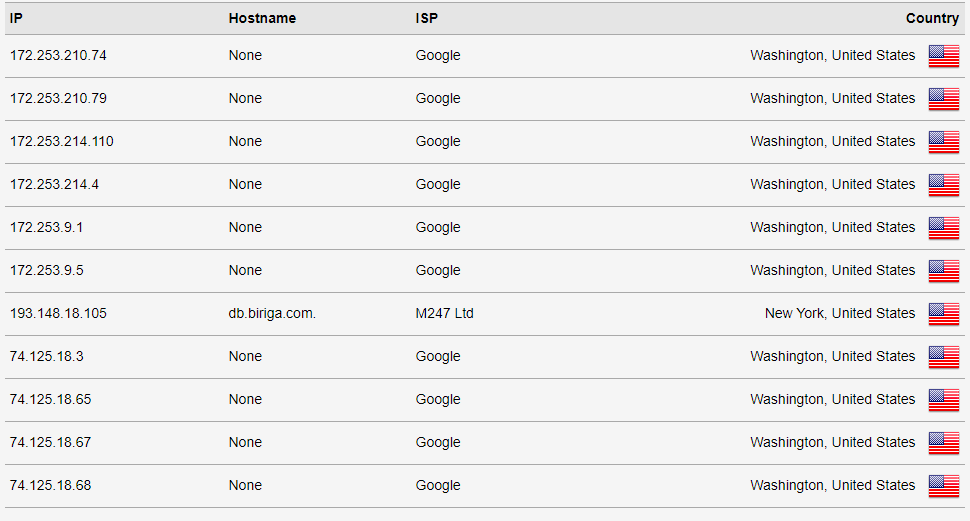
-
You understand that is what suppose to show up right if your using google.. did you think it would be 8.8.8.8
You have no freaking clue to what your 10.8.8.1 could be doing - prob forwarding to google ;)
I would suggest as I stated before - pick 1!!! Don't try and use multiple.. For those nixnet ones - why would you not just use the anycast address?
Maybe your router is intercepting dns? Sniff on pfsense wan and validate it sending the dns query to where you think its going..
Just like how pfsense can intercept dns - your router could be doing the same sort of thing.
-
Haha yes, that is exactly what should happen because those are googles servers. Im not that dense, buddy. The reason I set those in the Netgear modem router is to prove the fact that DNS requests are getting handled there when they should just be handled by Unbound DNS resolver in pfsense.
The 10.8.8.1 is so the DNS requests are sent to the protonvpn interface so that the DNS requests made through the protonvpn interface go through protonvpn.You can clearly see that the 10.8.8.1 should only be used by the protonvpn interface thats set in the general setup in one of my earlier posts.
Shouldnt ubound be stopping my ISP from intercepting requests? Isnt that part of the point of it lol? -
Well I would think you router is intercepting your dns then...
Its a common setting in many a soho router.. Prove it to yourself.. do a sniff on pfsense wan - if you only see it sending queries to what you set, then your router is intercepting the traffic.. Just like pfsense can do if you set that up.
You can clearly see that the 10.8.8.1 should only be used by the protonvpn interface thats set in the general setup in one of my earlier posts.
But you don't know when pfsense(unbound) would use those.. You have multiple dns listed - which interface used to talk to something doesn't mean its not used.
If you have dns 1,2 and 3 listed as forwarders - any of those can be used.. You don't have control over when which is used..
I would for your testing, turn everything off but 1 dns in unbound.. And then sniff on your wan - do you see it sending to that IP.. But your dns leak shows what your router is using - then its intercepting the traffic!
Just like you can setup pfsense to intercept traffic... Here I set my client to use 4.2.2.2 as dns
Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Realtek PCIe GbE Family Controller Physical Address. . . . . . . . . : 00-13-3B-2F-67-63 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.9.253 DNS Servers . . . . . . . . . . . : 4.2.2.2 NetBIOS over Tcpip. . . . . . . . : EnabledAnd before I tell pfsense to intercept that via your dnsleak test site - I see exactly that, 4.2.2.2 is a level3 public dns... So if I set that level3 is what shows as dns doing the lookups.
I then set pfsense to intercept the traffic - and even though my client is still sending to 4.2.2.2, you can not see that pfsense intercepted the traffic and my public IP (resolver) is what is seen as the dns on the leak test.
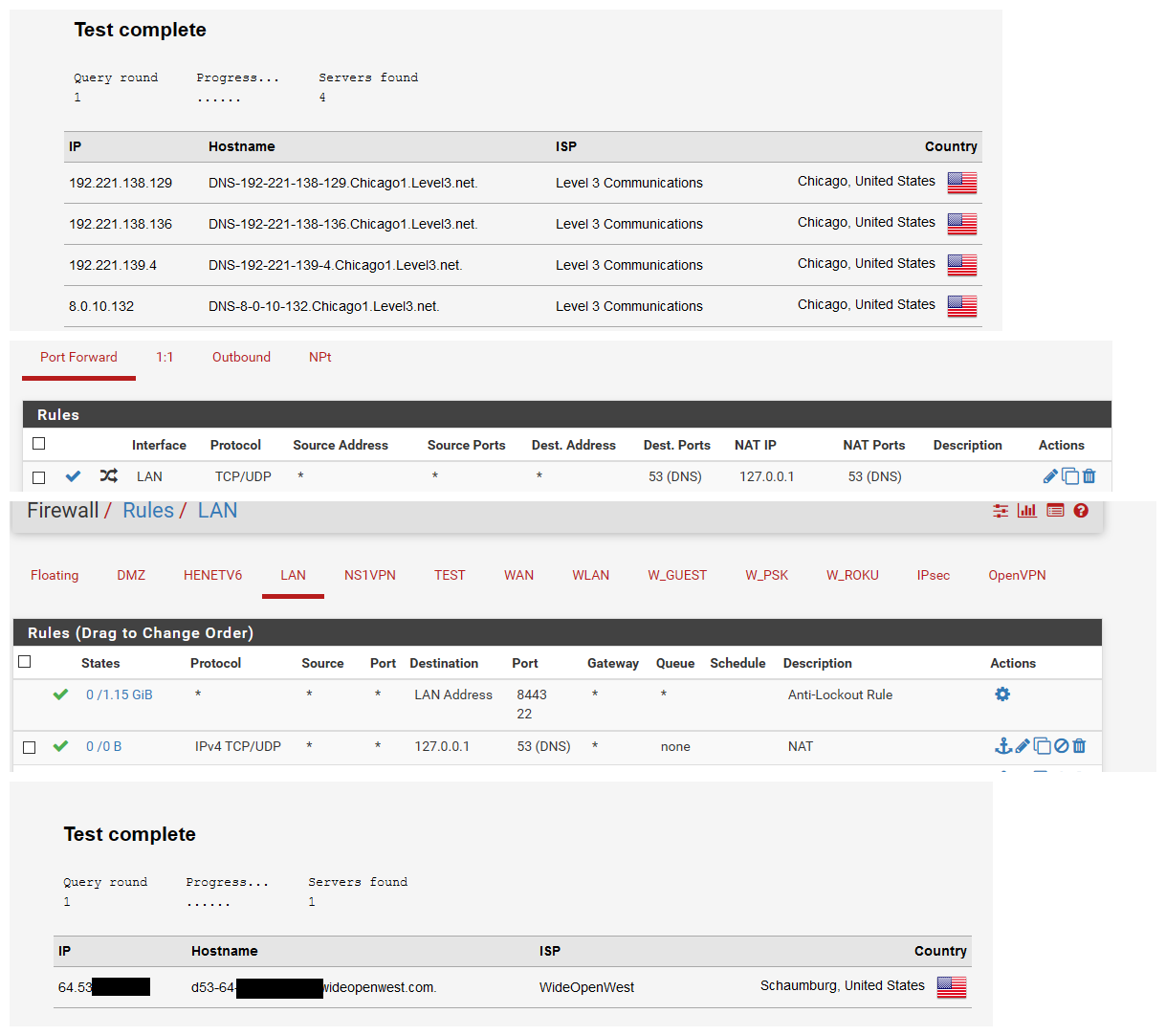
If your router is doing dns intercept - that is exactly what would happen no matter where pfsense is trying to query for dns.
-
A Netgear doing DNS intercepting ?
Google up the firmware, that would be known on the net.The ISP doing intercepting, that would be the next question.
-
This post is deleted!