Multi WAN, TO VM NAS with seperate Firewall
-
@jochenmehlich said in Multi WAN, TO VM NAS with seperate Firewall:
Unfortunately I don't know how to use multiple IPs over one NIC
Firewall > Virtual IPs
Here you can assign further IPs to one interface. Use type IP alias.However, if you get routed the additional IPs to you primary that isn't necessary. That's why I asked before.
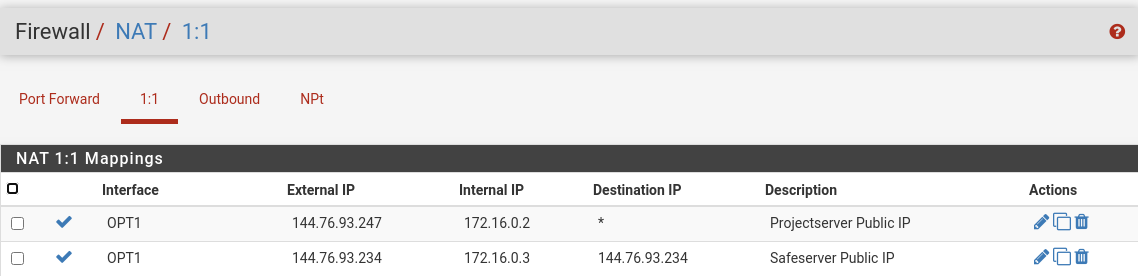
If you want each VM to be accessible and also go out with a unique IP set up a NAT 1:1 for each.
-
I configured it now so:
Dashboard:
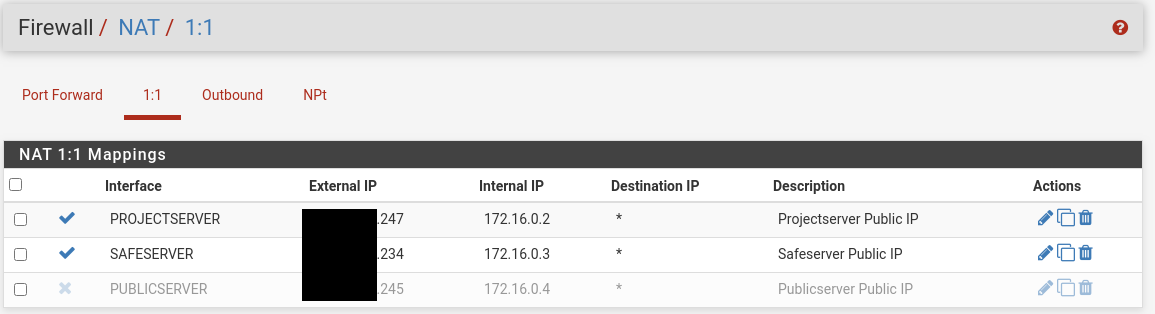
Nat 1:1:
and Virtual IPs:
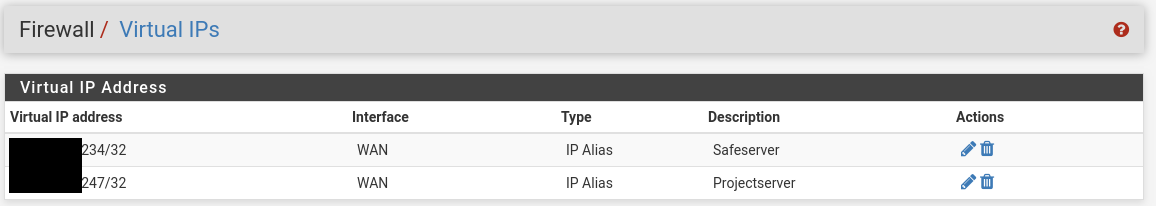
put when i try to ping to one of the server, i dont get any response. What did I wrong?
-
One Problem could be, that the Ip of the PfSense VM has a completly other gateway as the from the others VM. Would it be fixed, if I setup a second NIC?
-
Falls du willst, können wir gerne auch auf Deutsch schreiben.
-
@jochenmehlich said in Multi WAN, TO VM NAS with seperate Firewall:
Falls du willst, können wir gerne auch auf Deutsch schreiben.
Vom Interesse des Forum her sollte am Ende jedenfalls hier eine Lösung deponiert werden, sofern es eine gibt.
-
@jochenmehlich said in Multi WAN, TO VM NAS with seperate Firewall:
One Problem could be, that the Ip of the PfSense VM has a completly other gateway as the from the others VM. Would it be fixed, if I setup a second NIC?
You've set the virtual IPs with a /32 mask. Consider that the gateway must be within the subnet of the IPs, cause if you access one pfSense sends responses back with that source IP.
So you got a second gateway from the provider for use with the additional IP as I understand? Have you already added this to pfSense?
However, if it can work with the gateway outside the subnet depends on the GW configuration. -
The main Reason why I'm setting this up, is because i want to have for each vm a seperate firewall.
I hope it is not so critical to post now the public IPs, because it's very hard to check if every ip is censored. So i have following IPs.
Projectserver
IP: 144.76.93.247
Gateway: 144.76.93.225
Netmask: 255.255.255.224
Broadcast: 144.76.93.255Publicserver
IP: 144.76.93.245
Gateway: 144.76.93.225
Netmask: 255.255.255.224
Broadcast: 144.76.93.255Safeserver:
IP: 144.76.93.234
Gateway: 144.76.93.225
Netmask: 255.255.255.224
Broadcast: 144.76.93.255PfSense:
IP: 136.243.196.130
Gateway: 136.243.196.129
Netmask: 255.255.255.248
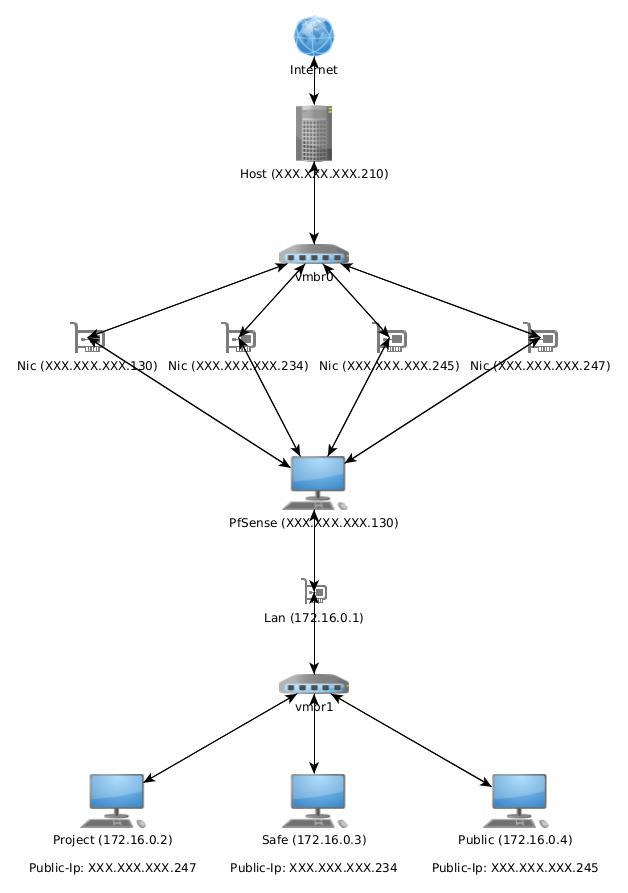
Broadcast: 136.243.196.135So I have
- a WAN-Interface (136.243.196.130)
- a LAN-Interface (172.16.0.1)
- a OPT1-Interface (144.76.93.247)
All Traffic from the VMs and for the VMs should go through opt1.
It's static with the gateway with the CDIR 27.Alias-IP
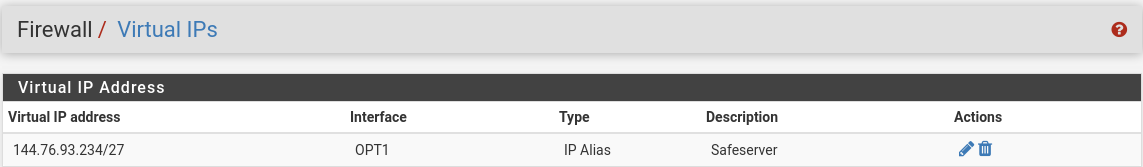
Nat 1:1
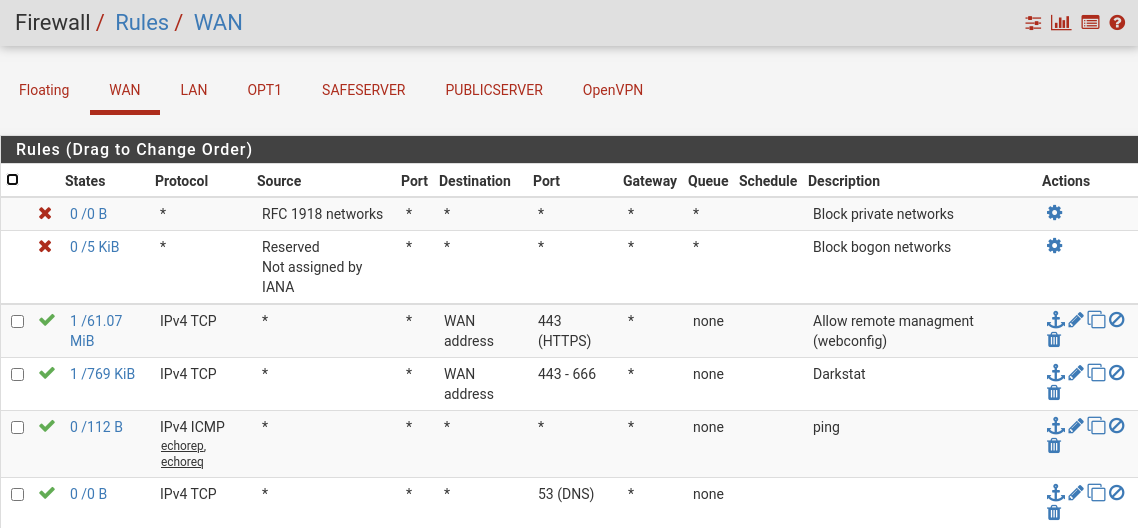
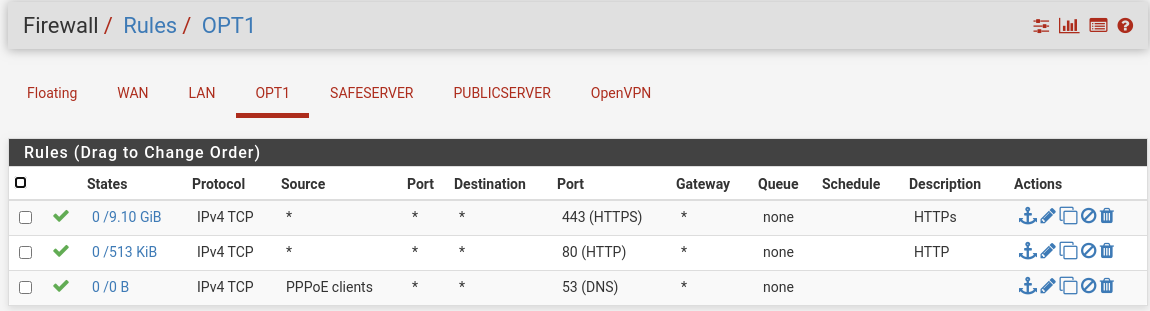
Firewalls:
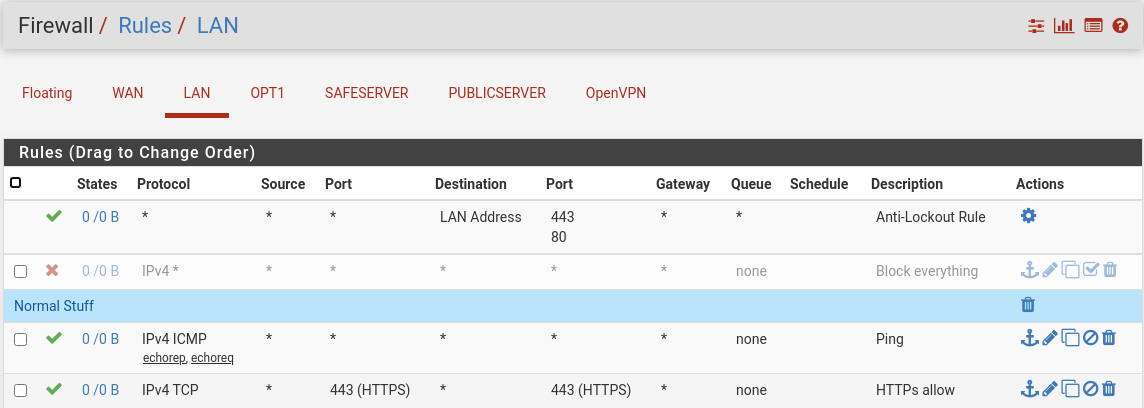
Floating is empty.
What did I wrong? Because i can reach the projectserver but not the safeserver.
-
@jochenmehlich
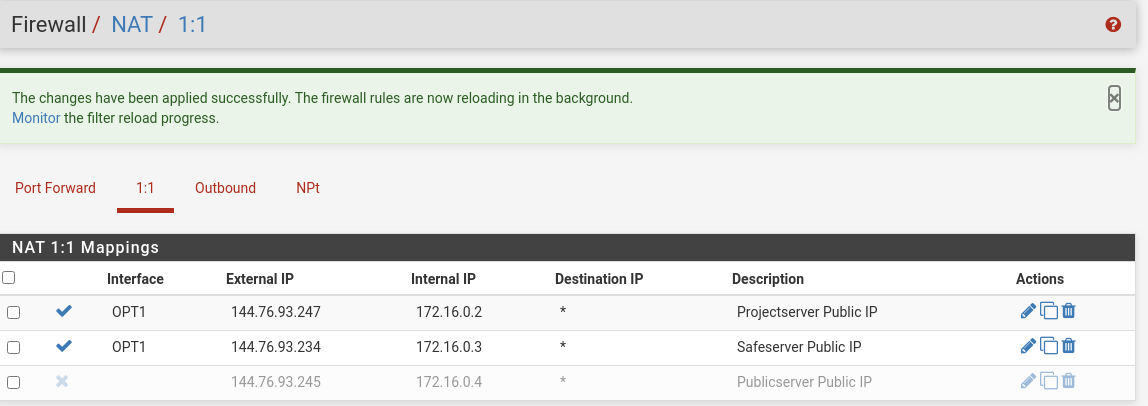
It's not really recommended to post the real public IPs here. The info that all except pfSense are in the same subnet with a separate gateway would be sufficient.Why did you set a destination in the 1:1 NAT for the Safeserver? The own public IP makes no sense at all.
However, that won't be the problem, I think.Your firewall rules page shows the interfaces "Safeserver" and "Publicserver". Are the VMs really connected to separate interfaces on pfSense? That cannot work, at least not with the server IPs shown in the NAT rules.
-
It's not really recommended to post the real public IPs here
Ok, thanks for the information
Why did you set a destination in the 1:1 NAT for the Safeserver?
I think it would fix my problem.
The own public IP makes no sense at all.
How could I fix it, that every vm has it own public ip?
Your firewall rules page shows the interfaces "Safeserver" and "Publicserver". Are the VMs really connected to separate interfaces on pfSense?
No, they are not connected, that are the old interfaces (from beginning, but not plugged in (link down via ProxMox)
That cannot work, at least not with the server IPs shown in the NAT rules.
How can I do it?
-
@jochenmehlich said in Multi WAN, TO VM NAS with seperate Firewall:
Why did you set a destination in the 1:1 NAT for the Safeserver?
I think it would fix my problem.
The destination should be any if there are no special reasons for to set specific one.
@jochenmehlich said in Multi WAN, TO VM NAS with seperate Firewall:
How could I fix it, that every vm has it own public ip?
The rest of the 1:1 NAT rule is fine. One external IP to one internal.
@jochenmehlich said in Multi WAN, TO VM NAS with seperate Firewall:
No, they are not connected, that are the old interfaces (from beginning, but not plugged in (link down via ProxMox)
That cannot work, at least not with the server IPs shown in the NAT rules.
How can I do it?
Ok, if the server are both on LAN within the same subnet there is no problem.
Test the access again with the corrected NAT rule.
-
@viragomann said in Multi WAN, TO VM NAS with seperate Firewall:
The destination should be any if there are no special reasons for to set specific one.
@viragomann said in Multi WAN, TO VM NAS with seperate Firewall:
The rest of the 1:1 NAT rule is fine. One external IP to one internal.
Okay :D
@viragomann said in Multi WAN, TO VM NAS with seperate Firewall:
Ok, if the server are both on LAN within the same subnet there is no problem.
They should be.
-
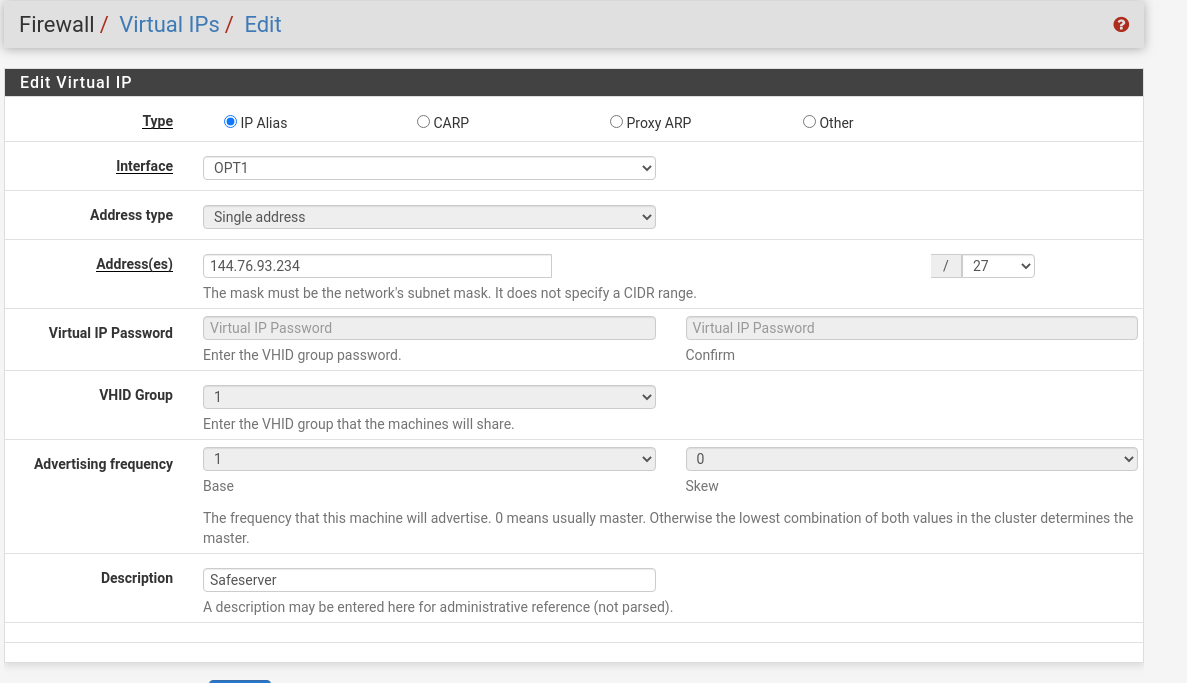
its not working. the vms can go out.
only project is reachable.here is the virtual-ip configuration
and the interface
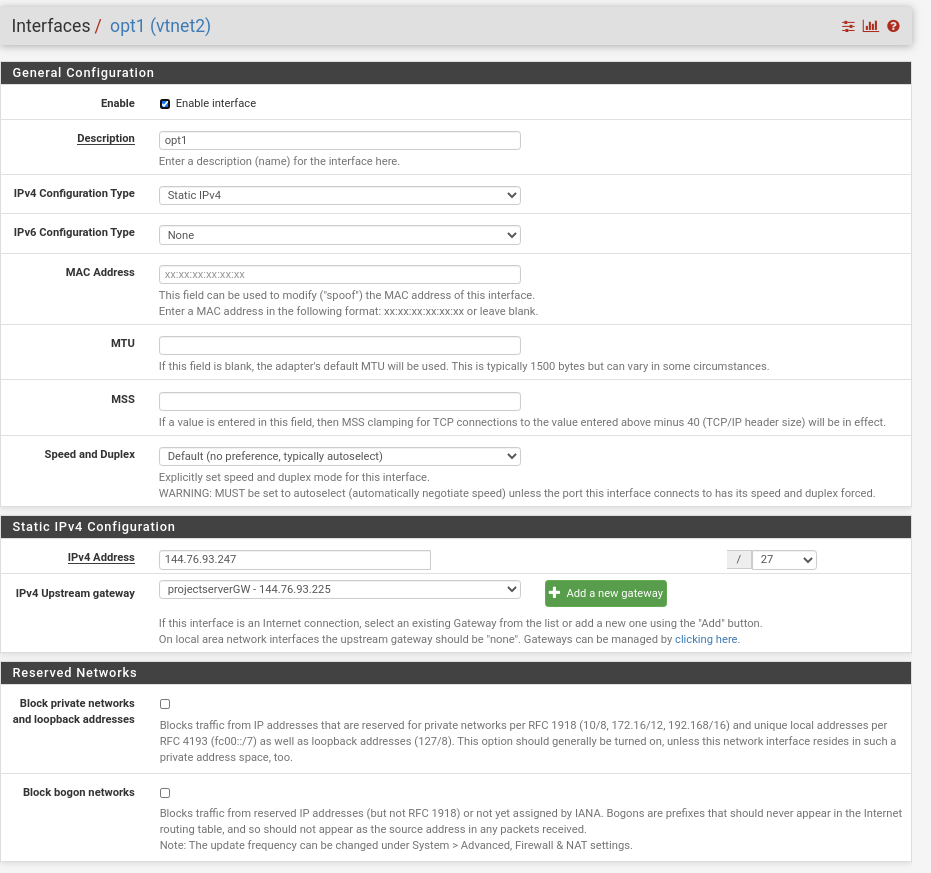
Did i something wrong? Or should I ask my hoster, if any feature is missing?
-
Are you sure, the safeserver is responding to the access from the internet?
To investigate use the packet capture tool from the Diagnostic menu on pfSense.
Take a capture on LAN interface while trying to access the Safeserver from outside.
If you see nothing take a capture on OPT1 to check if the packets arrives pfSense. -
In OPT1 its showing the ping request
00:07:12.007358 IP 5.100.XXX.XXX > 144.76.93.234: ICMP echo request, id 6, seq 4, lengthbut there is nothing in lan
-
so i thing, something with the redirection is broke. (maybe the nat 1:1)?
-
You have not allowed ping on OPT1. Your rules only allow http and https. So you cannot see a ping on LAN, cause pfSense blocks it.
So either test with http or allow ping. -
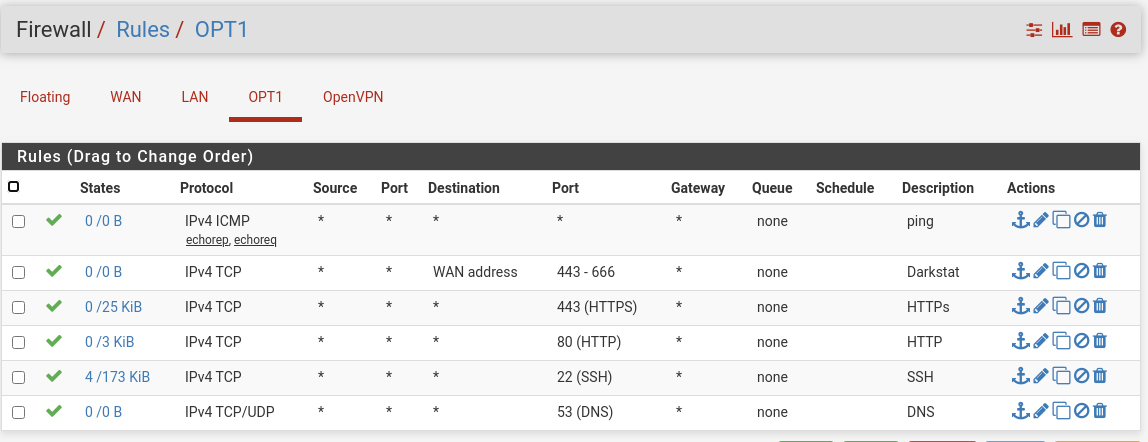
now it should be allowedbut there is no difference. No incoming ping in LAN and no incoming https.
-
Strange. Yes, it should work.
What if you add a usual port forwarding rule to OPT1 instead of the 1:1 for that server?
-
nothing will pass.
no https response from the projectserver or the safeserver.
-
is there any other method to make a firewall.
it must not be efficient, it must only work.every vm must have its own rules and use its own public ip4 addresses.