ipsec vti routing can only get to firewall, no clients
-
@Topogigio Here is my VLAN 20 rules for site A (this is where my request originates from)
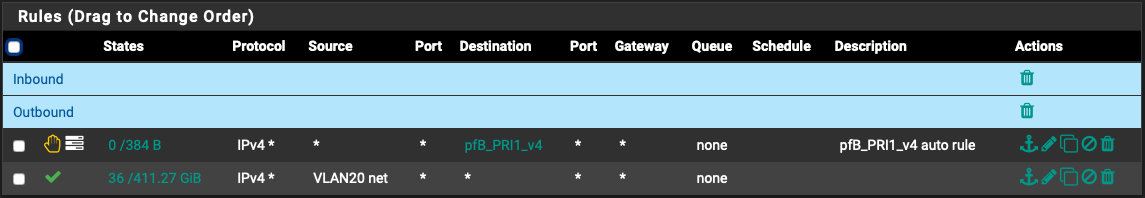
Here is my IPSec rules on site A:
Hetzner DMZ is an alias to 10.38.70.0/24
Hetzner LAN is an alias to 10.38.1.0/24
Hetzner Tunnel is an alias to 10.8.1.1/30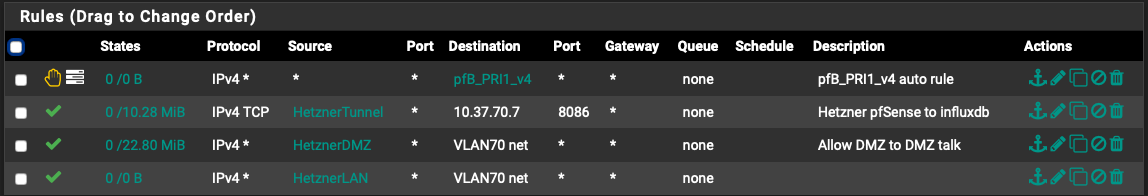
Site B IPSec rules:
Here you can see where I initially tried the SSH. I get the "do you want to connect to this fingerprint?" and then as soon as I hit yes I get a time out. So it get's there at least initially, but dies.
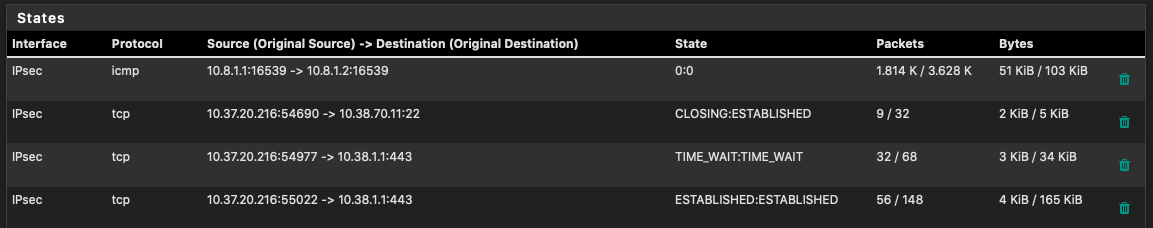
Here are the states on the site b
-
This post is deleted! -
I think I may see the issue?
Site A:
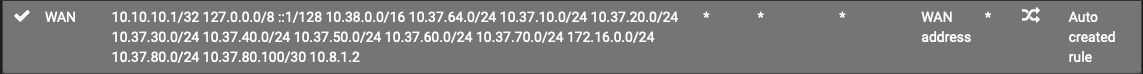
Site B:
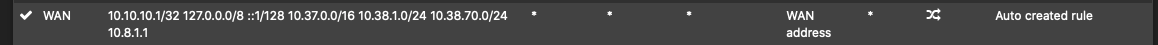
Should the site b subnet be in the outbound NAT of site A on the WAN interface and vice-a-versa? I would think not since those should go over the IPSec interface, right?
-
No NAT is required to route through VPN tunnel...
Your policies seem ok if VLAN70 net is the local VLAN of site B.
However if you have some kind of TCP session estabilished (the fngerprint request from SSH), firewall rules may be ok.
-
Right, there shouldn't be, so I was wondering if that should even be there? I didn't put it there.
VLAN70Net is a local DMZ VLAN on site A (10.37.70.0/24)
Wouldn't the site A IPSec rules only cover incoming traffic over the IPSec tunnel? The stuff outbound from site a would go through the interface it came from? So in my case I am initiating an SSH connection from a client on VLAN 20. The request would go through the VLAN 20 interface firewall rules, then be routed over the IPSec tunnel. Any requests coming from site B would hit the IPSec firewall interface rules, right?
-
It looks like I can ping hosts from site B into site A fine. It looks like the problem is on my site A (homelab) router side.
-
Here is my setup:
https://imgur.com/a/lBjOEJ5 -
Here is a TCP dump on my VLAN20 interface where my client I am trying to connect from lives, it just keeps repeating:
[2.4.5-RELEASE][admin@pfSense.localdomain]/root: tcpdump -ni lagg0.20 host 10.38.70.11
tcpdump: verbose output suppressed, use -v or -vv for full protocol decodelistening on lagg0.20, link-type EN10MB (Ethernet), capture size 262144 bytes
00:08:29.827060 IP 10.37.20.230.53844 > 10.38.70.11.22: Flags [S], seq 1814817855, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 393680583 ecr 0,sackOK,eol], length 0
00:08:30.908274 IP 10.37.20.230.53844 > 10.38.70.11.22: Flags [S], seq 1814817855, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 393681583 ecr 0,sackOK,eol], length 0
-
@realityman_ sorry, it's quite hard for me because you use rules in a different way as me (for example, I don't use floating rules).
It seems that ping can work in both direction (not TCP protocols, you have in site A for example incoming allowed from IPSEC only if it's ICMP).
I suggest to try on both sides, on the firewall rules:
- in IPSEC tab: from all to all, ICMP (or all or TCP based on what do you want test)
- in VLAN20 (or other local interface where SOURCE host is) tab: from all to all, ICMP (or all or TCP based on what do you want test).
After that, if it's work, you can arrange it with filters you need about source IP address and/or protocols or ports.
your routing table seems ok and so IPSEC VTIs
-
@Topogigio Yea the only reason I have floating rules is because I use codel on my WAN since I have a stupid small upload (40mbps) and when my lab backs up it will murder my latency.
Interesting thing happened. I restarted the VPN, and when I first started I was able to ping the host 10.38.70.11. I then tried SSHing to it, and I got the login prompt. The connection died once I sent my password though. So it does work for a period, but then stops.
Let me try what you suggested and see what happens. Thanks for your help!
-
@Topogigio tried your recommendation, still no traffic went to that host
-
@realityman_ my opinion this is not pfSense...
maybe do you have some dynamic firewall on the host the ban your IP?