Setup management interface on separate network
-
Hello,
I have seen quite a few similar questions, but no answers that help me so far. I have a pfSense setup with 4 network interfaces, 2x WAN (load balanced), 1x LAN (client network on 10.x.x.x) ip range, and a 4th interface, called MGMT, which I want to use to access the management GUI and SSH from our staff network 192.168.0.0/16. I have set the interface to a static IP 192.168.1.1/255.255.0.0 and I added two firewall rules (no routing to the internet or LAN on this network, and no DHCP):
- allow access from 192.168.0.0/16 to port 22 and 443
- block all other access
However this does not seem enough to allow access to the management GUI, can anyone tell me what else I need to do please? (I was wondering if I need to tell pfSense to listen on 192.168.1.1, but I can't work out how to do that.)
Thank you for your help, I am completely new to pfSense, so forgive me if I have overlooked something obvious.
-
The webgui and ssh daemon listen on all IPs pfSense owns so you should be able to connect if rules allow it.
You have multiwan. You might be policy routing traffic to the loadbalancing gateway group. If that catches traffic before the pass rule to the MGMT IP it will be sent out of the WAN(s) even if the destination is local.Can we see a screenshot of those firewall rules?
Do you really need a /16 subnet there? 65,536 IPs?
Steve
-
@ymcan said in Setup management interface on separate network:
192.168.0.0/16
Great. Your staff would do management using one of the 65534 devices on the MGMT interface ??
@ymcan said in Setup management interface on separate network:
10.x.x.x
Ok, I got it : a 16 million size LAN network ....
Confirm that you work for a F500 company. If not, please make your live easier, and go to /24 on both networks. You will thank yourself later on.
Put these 4 rules on your LAN firewall :
( edit : have to wait - can't upload right now... )
edit again :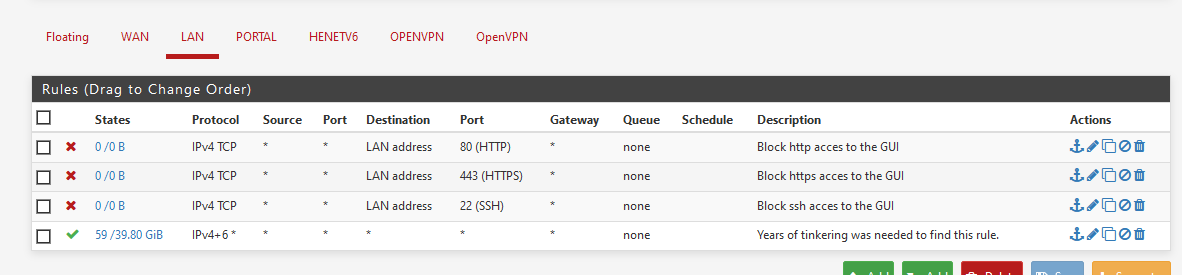
Note : if your LAN uses IPv6, use "IPv4+6" instead.
Ports 21,80 and 443 could be grouped in an alias, so you can set up one firewall rule blocking these ports.
-
@Gertjan Are these block rules (looking at the description - ie "Block SSH")? They look like allow rules.
-
Mmm, they are allow....
-
@ahking19 said in Setup management interface on separate network:
They look like allow rules.
Nice catch.
When making the image, I wouldn't lock myself out while doing so, so I edited the image - and finally posted the wrong one.
Corrected.
( well .... Error Something went wrong while parsing server response) -
I am currently working from home and don't have access to the client network from here, so I will post an image of the firewall rules as soon as I can get to that again. (I can get onto the staff network, but if I could get to the firewall rules from there, I would not have written this post.
 )
)As for the size of the ip ranges.
-
The 10.x.x.x was a typo it should have said 10.1.x.x, I have up to 400 devices on the client network and so /24 would not cover it. I know I could have done /23 or /22, but I was lazy, and in a hurry to get this up and running.
-
The staff network spans several sites, and the IP ranges are different on every site, 192.168.0.x - 192.168.15.x, so again not the full /16 range, but me be lazy.
I will post those firewall rules as soon as I get back on site. That might be a few weeks though.
-
-
If it's a supernet to include a number of subnets that's fine. As long as there is a reason for using it.
You'd be surprised how many people believe there are only 3 private subnets available.
Steve