XG-7100 - IPsec high CPU Usage
-
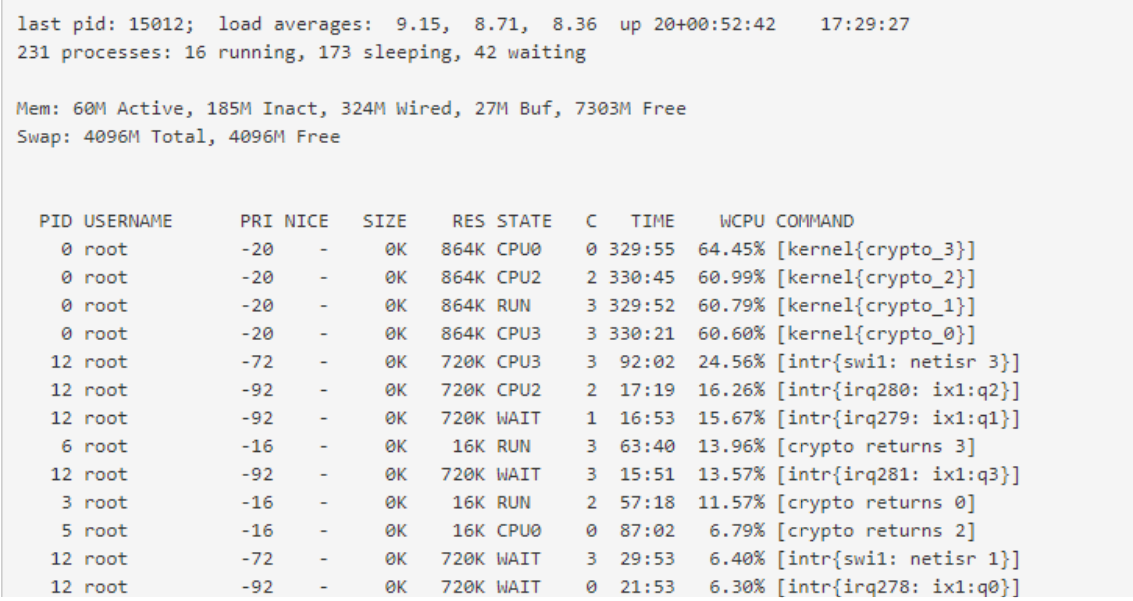
50MB/s.... That’s a lot of data to encrypt, so there’s your answer. The CPU usage is caused by performing IPsec encryption.
Just because the CPU has AES-NI does not mean it will not use CPU. AES-NI is just an Intel x86 CPU instruction that can be used to accelerate encryption over doing it matematically with use of several normal instructions. So it will save som CPU usage, but FAR from eliminate it.
-
Hello @keyser,
Thank you for your answer.
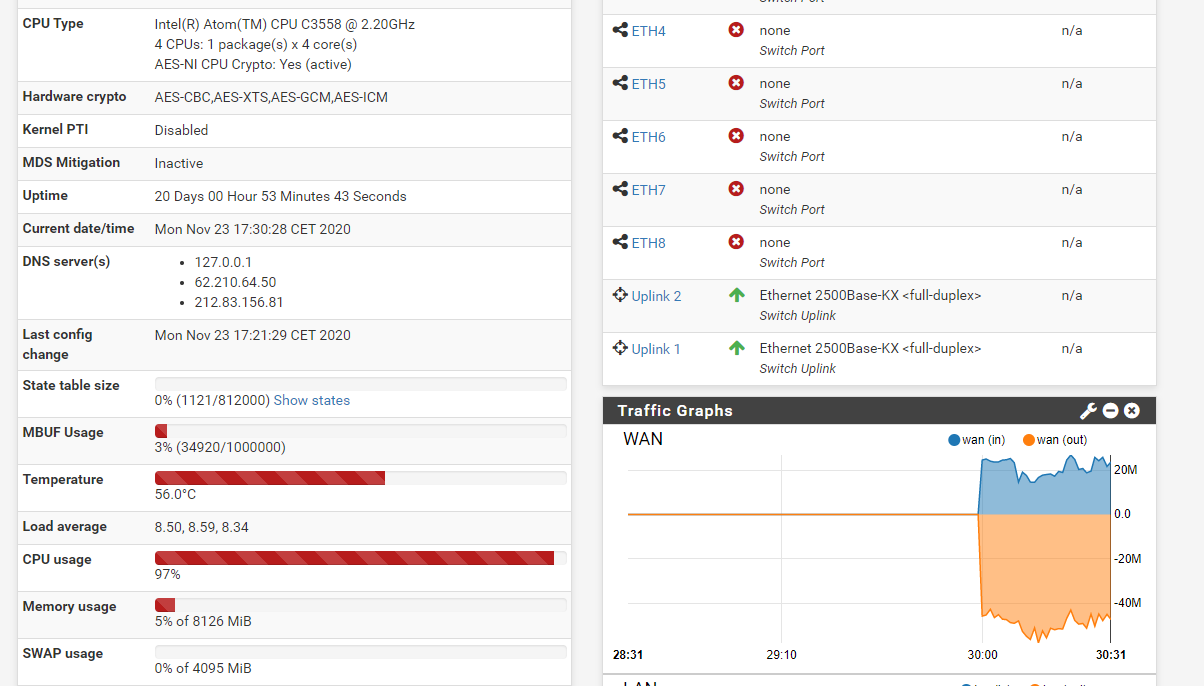
I know that, but in the documentation of XG-7100 it's annouced 1280 Mb/s ( =160MB/s ).50MB / s is not half of what is advertised.
I built my infrastructure based on this.In comparison, the traffic is coming from a Cisco ASA 5512 and the ASA's CPU is about 40% during the transfer. ASA hardware is pretty basic: ASA5512, 4096MB RAM, Clarkdale 2793MHz CPU, 1 CPU (2 cores)
Any idea to improve this and to bring it closer to the announced speeds?
-
My guess is the advertised speeds are based on simpler AES128 encrytion with a somewhat short key. I don't know for sure, but that is usual procedure when it comes to marketing takeover of product specs.
-
I will test and feedback here.
It could be interesting for anyone want to design an IT architecture. -
If you have SHA1 set you are probably using AES-CBC. Using AES-GCM, which does not require a separate authentication hash, is more efficient.
Steve
-
Ahh, sorry, didn't pay enough attention to your device being a XG-7100 - I somehow had the SG-3100 in my mind.
You are obviously right. 50MB/s is too little for the XG-7100. The issue must be some combination of AES and key selection that prevents it from using AES-NI acceleration and then doing it old-school CPU only.
-
That number is shown here: https://www.netgate.com/products/appliances/
You can see that was tested using iperf3 over a tunnel configured as AES-128-GCM.Sending a file will not likely match that, especially if you're using smb.
Steve
-
Yes, my original post was correct in terms of the tunnel needing to be AES128 to reach those figures, but like Stephen pointed out you need a different key selection to make the key authentication simpler/faster.
-
Thank you both, @keyser and @stephenw10 .
I will try with with parameters discribed in Pfsense VPN Scaling doc : https://docs.netgate.com/pfsense/en/latest/vpn/performance.html#optimal-encryption-settings

I'll get back to you quickly.
Anthony
-
OK, now it's better. With AES128-GCM I can hit the speed of 85MB/s and the processor is around 80%.
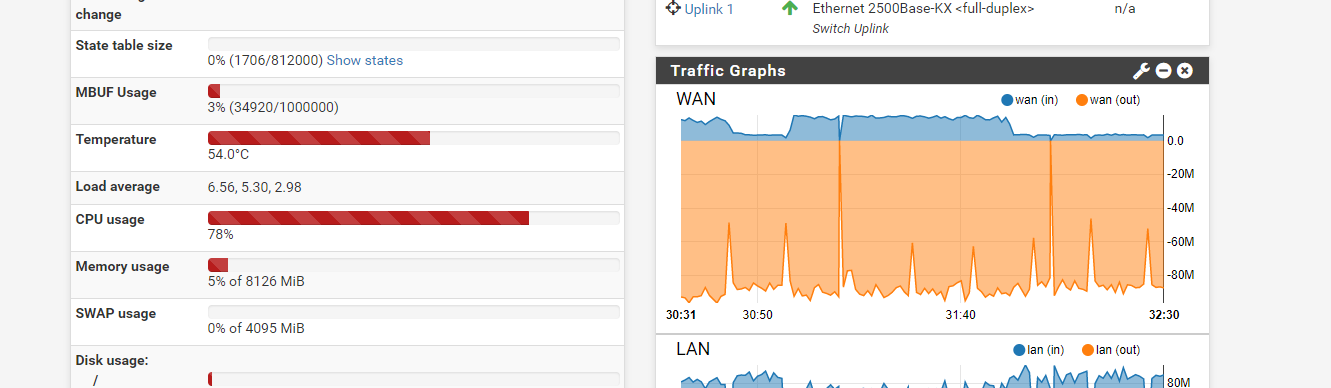
We can imagine firewall will never hit 160MB/s but, it is closer to the performances announced by Netgate. And my internet bandwith is 1Gb/s, so it's really close to the maximum.
Thank you for your help.
Anthony