Test Request: UPnP Fix for Multiple Consoles playing the same game / static port outbound NAT
-
It's important to first get a baseline of what works/doesn't. The basic configuration that should be currently in place is:
System / Advanced / Firewall & NAT- NAT Reflection mode for port forwards: Pure NAT
- Enable automatic outbound NAT for Reflection: Checked
Firewall / NAT / Outbound
- Rule with the following: Interface: WAN | Source: Alias with console IPs | NAT Address: Interface IP | Static Port: Checked
Firewall / Rules / LAN (or whichever interface the consoles are on)
- Rule at top with the following: Protocol: UDP | Source: Alias with console IPs | Destination: Any | Allow IP options: Checked
Services / UPnP & NAT-PMP
- Enabled with UPnP & NAT-PMP both checkd
- External Interface: WAN
- Interfaces: LAN (or whichever interface the consoles are on)
- Default Deny: Checked
- ACL: (e.g.) allow 0-65535 10.0.5.0/24 0-65535
Test
After these settings are set, power off the consoles, reboot the firewall (to clear states, old mappings, and ensure a control state for testing), then power on the consoles. Now test the same game at the same time on two consoles.- Does it work?
- What is the output of (Diagnostics / Command Prompt): pfSsh.php playback pfanchordrill
Now upgrade to 2.5.0 and run through the same test steps. Please back up the configuration before upgrading.
-
Thanks @Marc05 my settings are exactly as you have them. I will do some testing and post my results here.
-
@jimp said in Test Request: UPnP Fix for Multiple Consoles playing the same game / static port outbound NAT:
miniupnpd
Here is the github issue.
https://github.com/miniupnp/miniupnp/issues/226
Ideally if we could see the rules created on linux, then its trivial from that to send the correct syntax to that github post, and then I expect we will see progress.
-
My network setup:
cable modem -> pfsense (WAN igb0) -> Access Point (opt1) (igb1) -> opt2 (igb2) -> opt3 (igb3) Xbox One 1 Static IP: 10.100.100.100 Port: 56450 (wired) (igb2) Gateway: 10.100.100.1 Xbox One 2 Static IP: 10.200.200.120 Port: 53063 (wireless) (igb1) Gateway: 10.200.200.1 Ignore the PS4 info as well as any other irelevant IP's in the miniupnd debug info I posted below since I was only testing the 2 Xbox One's. PS4 Static IP: 10.0.0.100 (igb3) Gateway: 10.0.0.1 PS4 Static IP: 10.200.200.121 (igb1) PS4 Static IP: 10.200.200.122 (igb1) Gateway: 10.200.200.1My miniupnpd.conf file:
ext_ifname=igb0 port=2189 listening_ip=igb1 listening_ip=igb3 listening_ip=igb2 secure_mode=yes system_uptime=yes presentation_url=https://10.200.200.1:30000/ uuid=c09cf14b-f345-e551-63c7-0514bc6bb0d serial=C09CF14B model_number=20.7.3 allow 53-65535 10.200.200.120/32 53-65535 allow 53-65535 10.200.200.121/32 53-65535 allow 53-65535 10.200.200.122/32 53-65535 allow 53-65535 10.100.100.100/32 53-65535 allow 53-65535 10.0.0.100/32 53-65535 deny 0-65535 0.0.0.0/0 0-65535 enable_upnp=yes enable_natpmp=no clean_ruleset_interval=600 min_lifetime=120 max_lifetime=86400I manually built miniupnpd from source:
root@pfsense:~ # miniupnpd --version miniupnpd 2.2.0-RC1 Aug 23 2020 using pf backend My Build Options for Miniunpd: CHECK_PORTINUSE: on IPV6 : off LEASEFILE : off PF_FILTER_RULES: on UPNP_IGDV2 : off UPNP_STRICT : offUnforunately I couldn't run a test where I only had just the 2 Xbox One's connected to the network. I ran miniupnpd in debug mode. I had other devices connected wired and wirelessly. Ignore anything except for the Xbox One static IP's and their gateways. I started both of my Xbox One's at the same time and started the same game (Apex Legends) at the same time. I then attempted to play same game with both xbox's while in the same lobby and it didn't work. One of the Xbox's would not connect but the other would. See the output below at pastbin.com since I couldn't post the entire output here:
-
I wanted to add the below information in my original post as well but the forum wouldn't allow me after a certain amount of time ellapsed.
I was able to achieve Open NAT for the "Xbox Live Service" for both Xbox One's. Gaming is completely separate from the Xbox Live service where the problem resides. miniupnpd did not add any port mappings for the game Apex Legends only for the static port that each Xbox One has port 56450 & port 53063. Search the miniupnpd debug log I posted at pastbin and you will only see 2 AddPortMapping requests. There should have been more port mapping requests for the port dynamically needed for the game Apex Legends. Unfortunately, this was not the case.
-
what is the state of this, has it been fixed/ implemented ?
-
@Marc05,
I have performed a test per your previously listed specifications.Here is my testing scenario:
- Devices:
- Firewall: Netgate SG-3100 on 2.5.0-DEVELOPMENT (built on Thu Nov 12 12:57:50 EST 2020) - 192.168.1.1
- Consoles: 1x PS4, 1x PS4 Pro - 192.168.1.2/31 respectively
- Test game: Tony Hawk's Pro Skater 1+2 (uses same ports as EA COD games)
- admin pc - 192.168.1.106
First, I reset the device to factory defaults, then followed your instructions to the letter, with the additional pre-work steps as follows:
- Uncheck DHCPv6 Server for LAN interface and set IPv6 Configuration Type on the LAN interface to None
(i.e. steps to disable IPv6 on LAN interface) - Create static DHCP reservations for two consoles
- Create an alias containing both of the consoles' IPs
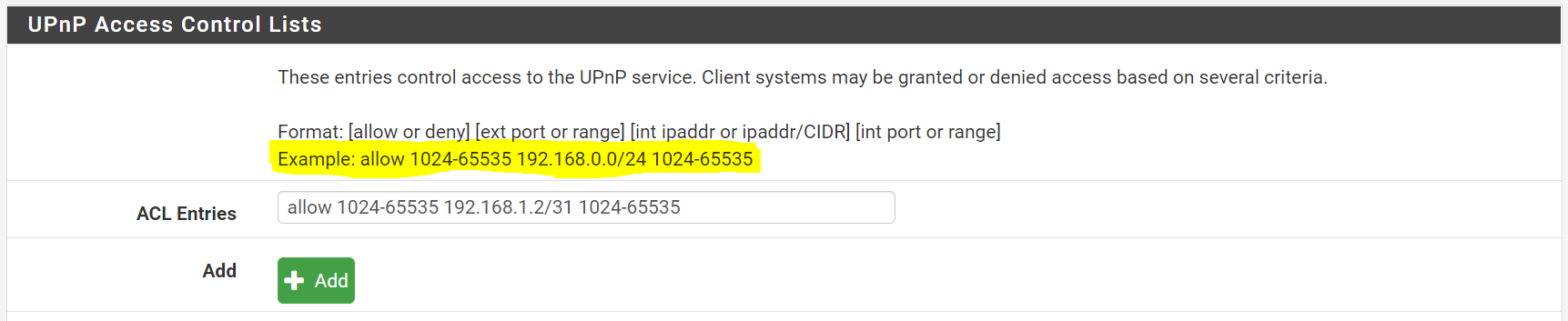
My UPnP ACL is
allow 0-65535 192.168.1.2/31 0-65535.--
I unplugged the consoles from power to make sure they were completely off. Next, I rebooted the SG-3100. After pfSense fully booted, I plugged the consoles back in to power and started them up. Answers to your questions are below:Test
- Does it work? No - One console can connect and play fine, but the other can not start game sessions or join lobbies
- What is the output of (Diagnostics / Command Prompt): pfSsh.php playback pfanchordrill
ipsec rules/nat contents: miniupnpd rules/nat contents: nat quick on mvneta2 inet proto udp from 192.168.1.3 port = 9308 to any keep state label "192.168.1.3:9308 to 9308 (UDP)" rtable 0 -> 68.186.83.135 port 9308 nat quick on mvneta2 inet proto udp from 192.168.1.3 port = 9306 to any keep state label "192.168.1.3:9306 to 9306 (UDP)" rtable 0 -> 68.186.83.135 port 9306 nat quick on mvneta2 inet proto udp from 192.168.1.2 port = 7777 to any keep state label "DemonwarePortMapping" rtable 0 -> 68.186.83.135 port 7777 nat quick on mvneta2 inet proto udp from 192.168.1.3 port = 7777 to any keep state label "DemonwarePortMapping" rtable 0 -> 68.186.83.135 port 7898 nat quick on mvneta2 inet proto udp from 192.168.1.2 port = 3478 to any keep state label "DemonwarePortMapping" rtable 0 -> 68.186.83.135 port 3478 rdr pass quick on mvneta2 inet proto udp from any to any port = 9308 keep state label "192.168.1.3:9308 to 9308 (UDP)" rtable 0 -> 192.168.1.3 port 9308 rdr pass quick on mvneta2 inet proto udp from any to any port = 9306 keep state label "192.168.1.3:9306 to 9306 (UDP)" rtable 0 -> 192.168.1.3 port 9306 rdr pass quick on mvneta2 inet proto udp from any to any port = 7777 keep state label "DemonwarePortMapping" rtable 0 -> 192.168.1.2 port 7777 rdr pass quick on mvneta2 inet proto udp from any to any port = 7898 keep state label "DemonwarePortMapping" rtable 0 -> 192.168.1.3 port 7777 rdr pass quick on mvneta2 inet proto udp from any to any port = 3478 keep state label "DemonwarePortMapping" rtable 0 -> 192.168.1.2 port 3478 natearly rules/nat contents: natrules rules/nat contents: openvpn rules/nat contents: tftp-proxy rules/nat contents: userrules rules/nat contents:Output of
miniupnpd --versionisminiupnpd 2.2.0-RC1 Nov 11 2020 using pf backendAdditionally, I would like to note that when running the "Test Internet Connection" program from the PS4 Settings menu, one console comes back with a "NAT Type" of "Type 2", while the other comes back with a "NAT Type" of "Failed".
It was mentioned earlier in this thread that this is somewhat of a niche problem with not enough testers with sufficient hardware. I am more than willing to test this out on the testing environment listed above.
I believe this is a bigger deal than just a niche problem, especially seeing how COTS routers from major brands can handle this situation out of the box, and how long this issue has been open.If there is any information I can provide that would make my testing more useful, please let me know.
w26
- Devices:
-
@food007 Maybe try two separate ACL entries, the first "allow 0-65535 192.168.1.2 0-65535" and the second "allow 0-65535 192.168.1.3 0-65535" if .2 and .3 are the addresses of your PS4s.
-
@trunix , sure. I can try that. I will change the setting, test, and report back.
I don't think it should change anything though, as even the helper text above the ACL Entries field uses CIDR notation for its example. (see highlighted text in pic... screenshot from 2.4.5, but I believe the helper text is the same in 2.5.0 as well)
-
@food007 where u able to test it out ?
-
@aniel Yes, I tested specifying each address individually... no difference.
-
@food007 do u think this will get fixed with the release of 2.5.5 ?
-
@aniel I wouldn't bet on it. Unfortunately I tried to help on this in the spring of last year. Still not working reliably.
-
-
@food007 that is to bad :(
-
Guys
An update
So I added an xbox series S to my network, forwarded the xbox ports and noticed nat was down, and it was reporting errors with testudo network.
Did a bit of research and it turns out microsoft now use ipv6 for their multiplayer, and if native ipv6 is not detected it will use testudo, now I never figured out why testudo wouldnt work, something somewhere seemed to be blocking it.
But as soon as I put it on my main VLAN which has working ipv6, it all works fine. With native ipv6 it will have its own routable ip so all solved.
-
@chrcoluk thanks for the update. Glad to hear it's working for you.
I'm not using IPv6 in my networks behind my WAN link, so UPnP being broken is still a blocker on this issue for me. :(w26
-
@food007 agreed, feels like a workaround as opposed to a solution.
-
Well i am looking into this again, trying to play UNO on steam.
Ubisoft in their wisdom decided to use the same port as xbox (port 3074), I see connection attempts adhoc in the firewall.
I have no experience with upnp at all, so its a learning crunch to try and understand how it is supposed to work, supposed to be configured etc, but all I know at the moment is that players cannot connect to me when I host a game but I can connect to others when they are host.
As usual the game vendors documentation is awful, so left trying to figure this out. If I get any success I will report back here.
-
@chrcoluk they will fixed by verison 2.5.next