host over ride does not work on chrome
-
Well if you redirect, and your browser cache doesn't match up - or again client settings thinking its using say 8.8.8.8 and gets back rfc1918.. Then that would be a rebind yes..
Again - there is nothing you can do on pfsense to stop your browser from thinking what it gets back is rebind. That is on the browser..
-
@johnpoz said in host over ride does not work on chrome:
Again - there is nothing you can do on pfsense to stop your browser from thinking what it gets back is rebind. That is on the browser..
Well very strange I've observed when I remove the check from
Syste-->General Setup : DNS Server Override . My all clients unable to surf internet . I've one rule in LAN which I allow(Pass) all src and destination my firewall IP dst port 53 . on top of my rules . and block all lannet src not firewall IP and dst port 53 . The block rule does not have any impact . -
@scorpoin said in host over ride does not work on chrome:
Syste-->General Setup : DNS Server Override
That allows dhcp from your isp to set dns on pfsense.. Again has ZERO to do with anything..
Without that checkbox - dhcp from your isp would not be able to set dns on pfsense - for your forwarding..
That should really never be checked to be honest... Unless your forwarding and want to forward to your isp dns? And or if your resolving, and you want pfsense itself to be able to ask your isp dns if resolving fails. Which would have nothing to do with what clients get when asking pfsense.
And again - what your "client" thinks is a rebind or not has zero to do with pfsense or unbound, or pfblocker on pfsense.. ZERO.. What you use for dns on pfsense be it you resolve, be it you forward.. None of that has anything to do with what your client thinks is a rebind or not - period!!
If you setup a host override for some fqdn to resolve 192.168.1.100 for example.. And pfsense returns that when you ask it via a dns query.. If your client thinks that is a rebind - that is on your client.. And there is NOTHING you can do in pfsense to change that..
rebind protection comes into play when unbound or dnsmasq for that example are forwarding or resolving and they ask some other dns server for anything.. .If that anything is returned as rfc1918 then its a rebind.. But in such a case pfsense would not return the address to the client asking for some fqdn.. Unless you disable rebind protection or set the domain in question as private so that unbound/dnsmasq would return the rfc1918 address to the client.
None of that has anything to do with a host override.. Are you actually doing a domain override? Rebind protection on pfsense would not return a rfc1918 address if it did a domain override - unless you again set the domain as private or disabled rebind on pfsense.
But none of that has anything to do with anything when you do a host override.
As per my example - do a dig, or host, or nslookup to pfsense for whatever fqdn you set a host override for - did you get back rfc1918 address?? If so then pfsense is doing what you told it - if your client thinks that is a rebind - that is on your client! Period!!
-
@johnpoz said in host over ride does not work on chrome:
That should really never be checked to be honest... Unless your forwarding and want to forward to your isp dns?
@johnpoz thanks for your prompt response , I have static IP and I;ve added manual DNS in
Settings-->General Setup --> DNS Servers
Tick DNS Server Override.
Onther end DNS Resolver
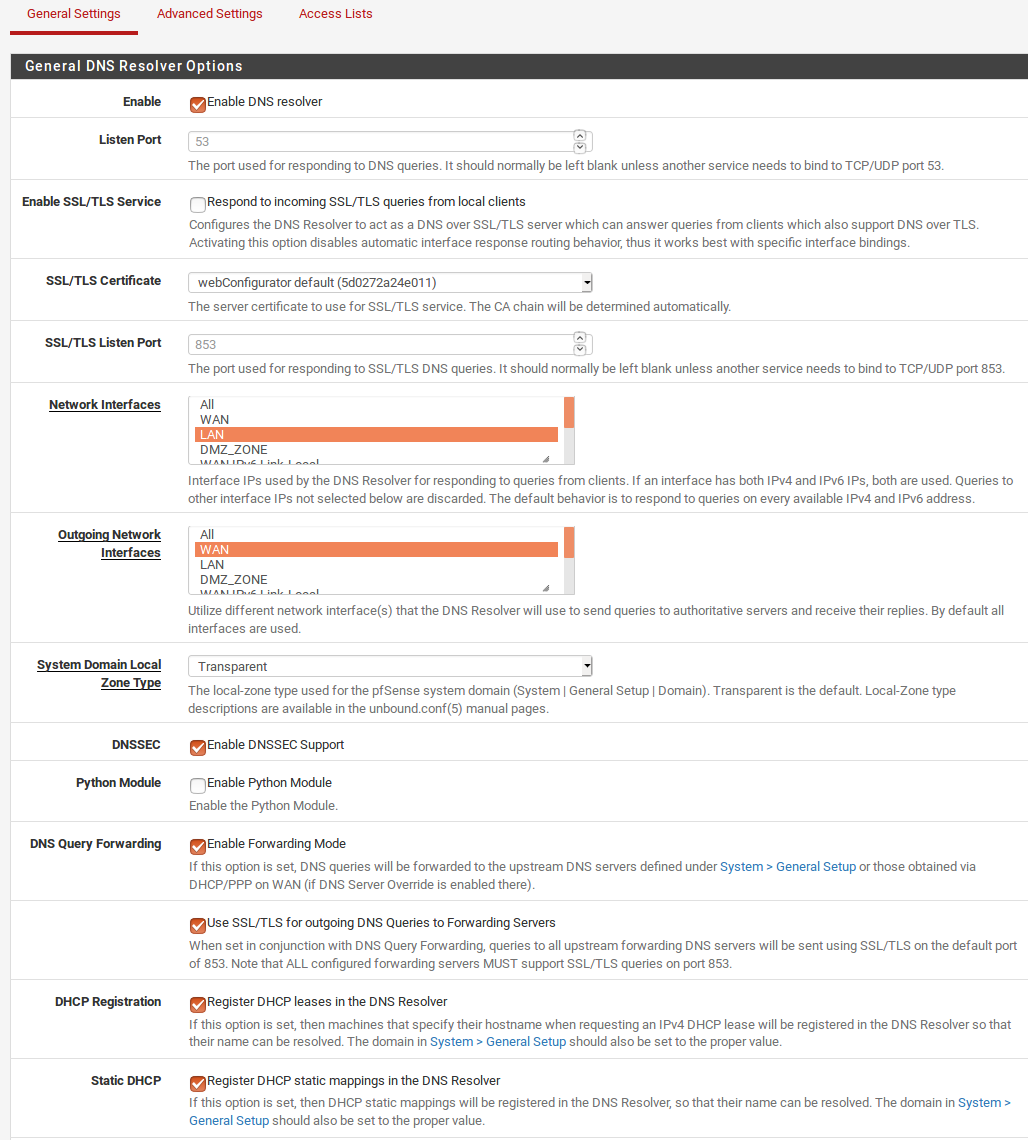
If I remove check of DNS Override from Setting General setup my client internet stop working :/ .
-
It seems you have no understanding of how any of this works at all.
Your in forwarding mode, you have dnssec enabled (pointless while forwarding) and you also want to use dns over tls.. But you also haven't set any dns in general? And just let your isp hand you theirs? Which sure and the F are not going to work for dns over tls..
None those settings make any sense..
Do you want to forward? To where? google, quad9, cloudflare? You want to use dns over tls?
Or is it your just randomly clicking shit you do not understand in a hope to get something working?
-
@scorpoin said in host over ride does not work on chrome:
getting DNS rebinding attack message from pfsense
A screenshot might help but I'm going to guess your browser is connecting to pfSense and not the web server, in which case this message is because pfSense sees you connecting via an unexpected URL. (System->Advanced->Alternate Hostnames)
-
^ possible.. That could be that he is hitting web gui vs his public IP for whatever fqdn he is looking up..
What is the fqdn your trying to set an override for - do you get back the local IP you put in the override for this when you do a query to pfsense?
See the above example I did for cnn
-
@teamits
I guess you are right but thing is those names are not for pfsense itself , those are suppose to be local web server on LAN.
Regards
-
You are right I'm doing DNS forwarder here is Setting-->General Setup
And DNS Resolver Config Screen
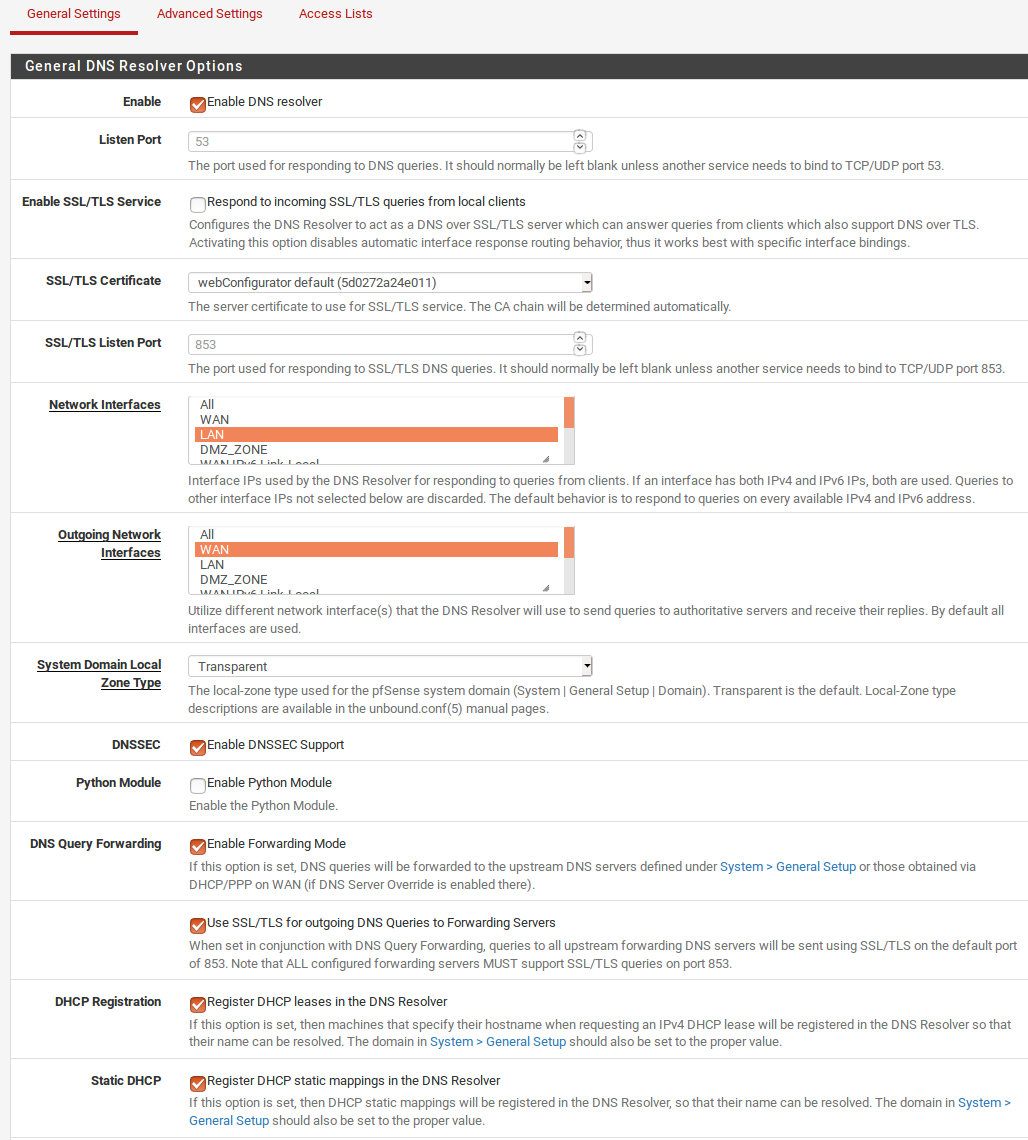
I've a static IP from ISP . When I remove the check of DNS Server Override in General Setup . Internet on client side stop working and unable to resolve any thing : / . Although on DHCP Server DNS list I've added my Pfsense IP as primary and seconday google-DNS .
RegardsRegards
-
Fix your dns.. Problem solved.
Although on DHCP Server DNS list I've added my Pfsense IP as primary and seconday google-DNS .
That setup is borked out of the gate.. You don't control what dns a client uses if you give them more than 1. If they don't both resolve the same thing, then you have no idea what a client might be able to resolve or not..
If you want to forward to google, then do that.. But your clients should only get pfsense for their dns, if you ever expect a client to resolve local resources.
Also if your going to forward, dnssec is pointless to have checked.
Why are you forcing pfsense dns out some gateway?
-
That was an optional and I've removed it as well . Now issue is when I remove the check from DNS Overide in General Setup or from DNS Resolver configuration all of sudden clients are unable to access internet :/ which I could not figure it out yet . where am I doing wrong in configuration .
Regards
-
@scorpoin said in host over ride does not work on chrome:
Now issue is when I remove the check from DNS Overide in General Setup
This one :
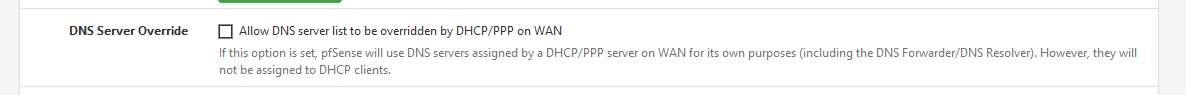
?
That was a practice in the past, somewhere in the last century I guess, when users had to use the DNS of their ISP.
The ISP boxes forward to the DNS of the ISP - and the box handles all it's clients DNS requests, who forwarding it upstream with some caching facilities.I guess this option still exist for historical reasons.
pfSense, when you unpack it, is set up for perfect DNS handling. If there are DNS issues, the issue is upstream. => Ditch your ISP.@scorpoin said in host over ride does not work on chrome:
Now issue is when I remove the check ..... from DNS Resolver configuration all of sudden clients are unable to access internet
What check where on that page ?
These settings :
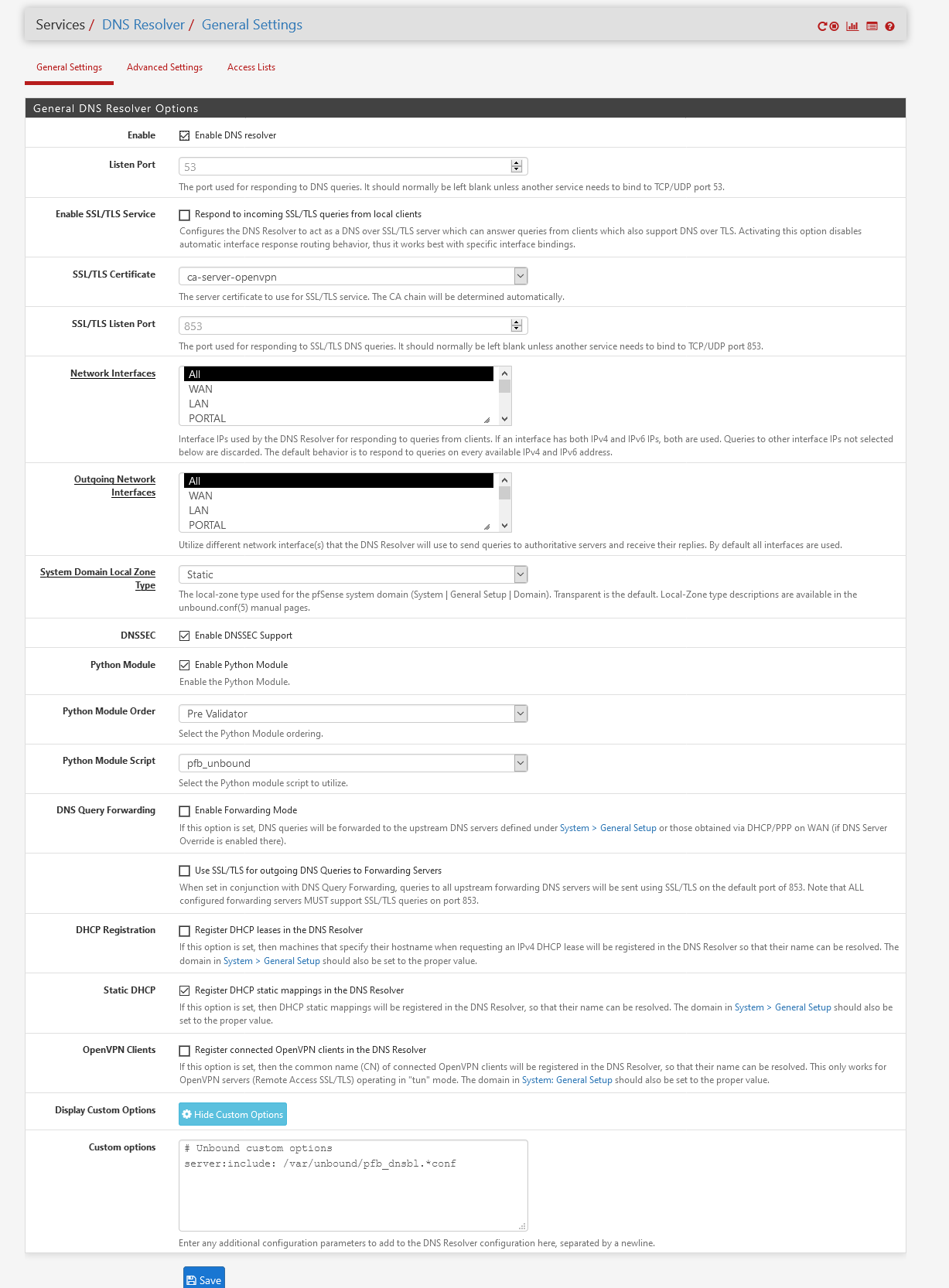
are default and perfect.
( Note that I also use pfBlockerNG 3.0.0.3, so two options are set accordingly.
-
Thanks I've tried selecting python mode but I'm unable to find any thing in drop down list.
Python Module Script :
there was not any thing like pf-unbound or such .
Regards
-
@scorpoin said in host over ride does not work on chrome:
I've tried selecting python mode but I'm unable to find any thing in drop down list.
Because :
@gertjan said in host over ride does not work on chrome:
Note that I also use pfBlockerNG 3.0.0.3, so two options are set accordingly.
AND
I activated unbound + python mode in pfBlockerNG 3.0.0.3 - and after this you'll see
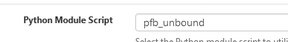
because unbound uses this python module to do "pfBlockerNG " stuff.
-
Lets forget pfblocker until you actually have dns working and working for your host overrides.
Where do you want to forward too?
202.143.112.206
206.112.143.202.in-addr.arpa. 86400 IN PTR ftth-112-206.satcomm.pkIs that your ISP dns? Do they support dns over TLS? I doubt it to be honest..
If your going to use dns over tls, you have to set the host name for the dns to be used.. So the cert will work.. While it still might work - you can run into issues where it wont even work.. If your going to use dot, you really should have hat that set correctly for the dot server your going to use.
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html
The hostname is technically optional but dangerous to omit. The DNS Resolver must have the hostname to validate that the correct server is providing a given response. The response is still encrypted without the hostname, but the DNS Resolver has no way to validate the response to determine if the query was intercepted and answered by a third party server (Man-in-the-Middle attack).
I would suggest you get basic forwarding working.. Before you try and move to dns over tls.
So either go back to default setup, where unbound just resolves. Or start with basic forwarding, then move to over tls.
Be it your forwarding or resolving works or doesn't work has nothing to do with a host override, because that is just a local resource.. if unbound is running, it would return any host overrides it has setup.
So do a simple query to an IP that pfsense is listening for dns on, by default this is all.. And do a query for your host override.. If that works.. Then ANYTHING that does not return that be it chrome or firefox or some pc, laptop or phone, etc.. is NOT USING pfsense as its dns.. If it was - then it would return the IP you setup in your host override..
I showed an example of this.. So use your fav dns tool, nslookup, dig, host, etc. and do the query.. What do you get?
-
well when doing dig my-domain.com or subdomain.com it does return local ip address which I set in DNS Host override .
Regards
-
Well then as I was saying your override is working, and your browser or device is not using pfsense as your dns..
Most likely doh, you know the browser makers looking out for your security by sending all your dns queries to them, vs where you actually want to send them.