Pfsense with pihole correct configuration?
-
No not really... The redirect is suppose to be to loopback 127.0.0.1
Which then you setup to ask pihole. Pihole then asks clouldflare.
Such a setup runs into asymmetrical flow.. I have gone over this multiple multiple times. if you want to do such a redirect then you would need to do a source nat on the traffic..
The only way such a redirect works if if pihole is on a different vlan then your clients your redirecting.
-
@johnpoz you recommend me erase that rule correct? so just leave this lan rules?
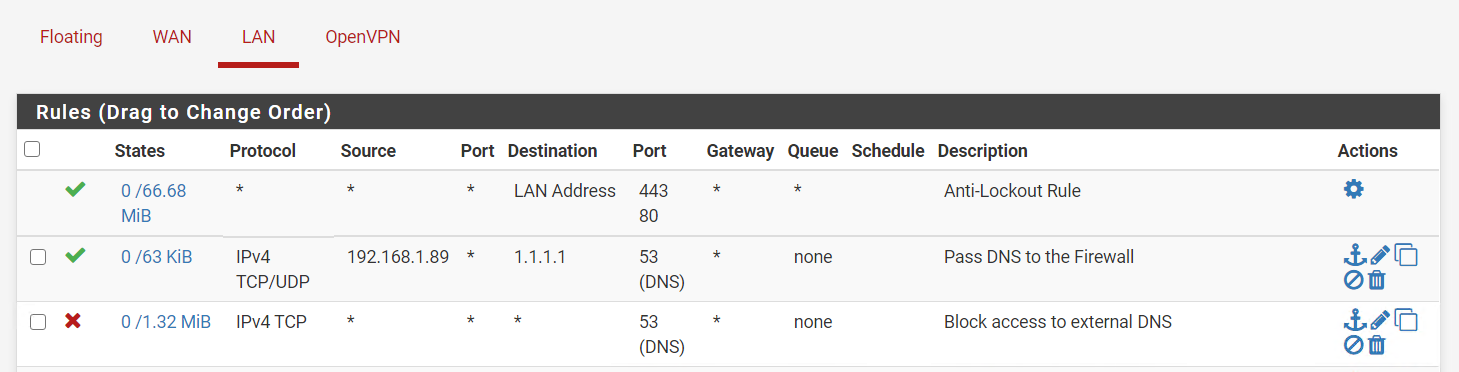
or like this
Allow all port 53 (DNS) traffic from your LAN to pi-hole server
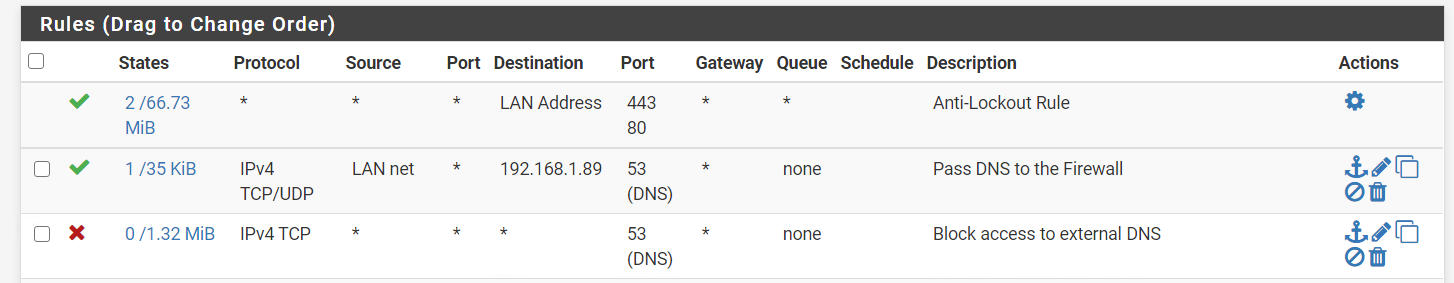
-
May I ask why you run Pihole and not pfBlockerNG ?
-Rico
-
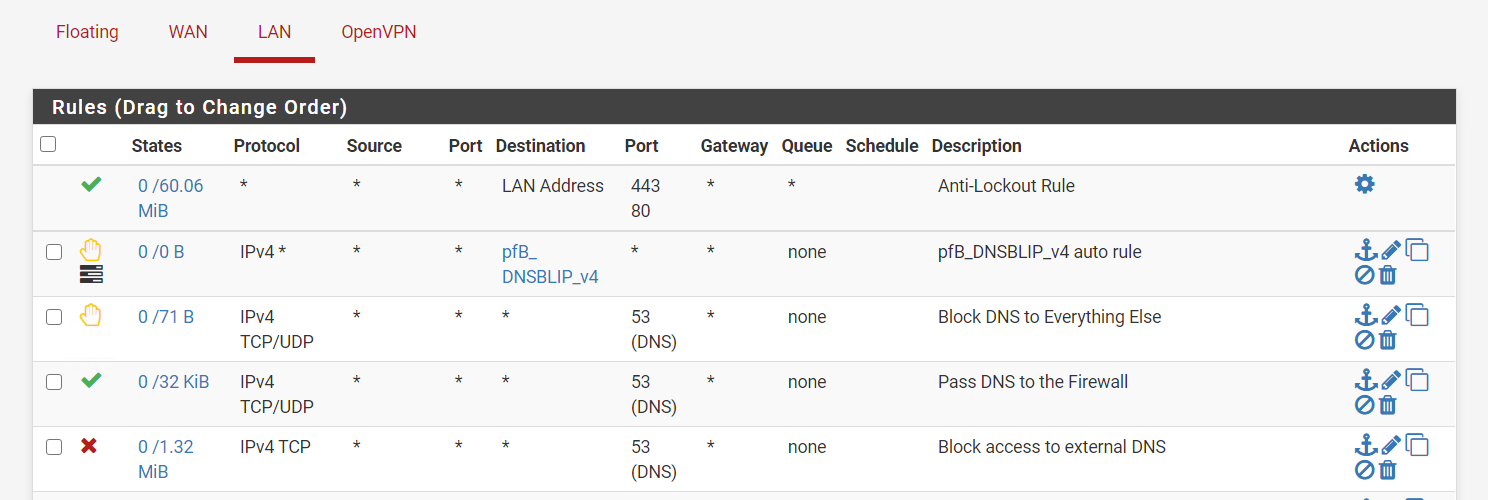
If your going to do a port forward.. Then you need a rule to talk to where your port forwarding.
It should be loopback if your doing the redirection. If you want to forward to pihole directly then you need to make sure you setup outbound nat for such a reflection.

Or you end up with this
dig @1.1.1.1 www.google.com ;; reply from unexpected source: 192.168.3.10#53, expected 1.1.1.1#53When you do something like this.
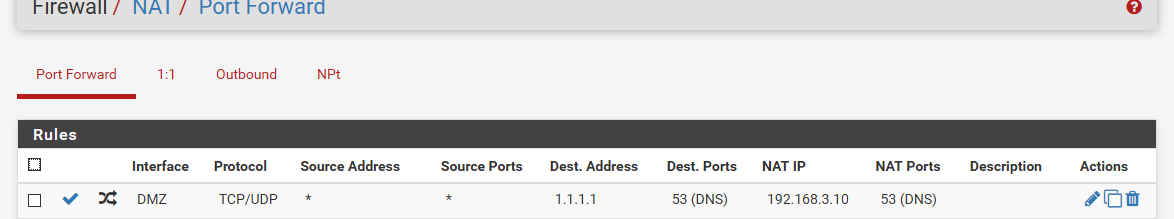
edit: I am not a fan of redirection.. If you want devices to use pihole, then hand them pihole via dhcp.. And just block all other dns.
Then just have pihole ask pfsense directly for stuff.. This allows you to resolve your own local stuff, and for pihole to see who asked.
If you don't want devices to use any thing else - then just block them from doing that. Users hate when their ISP does interception of dns.. But seems ok to do on your own network? Then why are you so mad when the ISP does it ;) It is their network after all that your connected too.
-
@johnpoz got it, now im clear, its better to have a diff segment for my pihole instead of using the same network on pfsense i should use vlan
-
@agaitan026 Putting you pi-hole on a network dedicated to such things is a good plan. I'm not prepared (no time) at the moment to lay out my setup but I'll say this:
Get your network working with unbound as a resolver.
Setup your DHCP and Unbound to register leases and static mappings in unbound. Set hosts names along with your static mappings in dhcp.
Add the pi-hole on a vlan/network of it's own or with other like devices.
Tell your devices (not the ones on the vlan with the pi-hole or the pi-hole) to use the pi-hole for dns with dhcp.
Use NAT to redirect (to the pi-hole) those who don't listen to dhcp, if you want.
Your devices would then use pi-hole which would then forward to pfsense (unbound).
Setup pi-hole to do 'conditional forwarding' (It's in pi-hole dns settings) so that the logs show the hostname dot local domain name.Sounds more complicated than it is. When time permits I'll post up all the settings in pfsense and pi-hole that are relevant.
-
@jwj sounds good, if its possible for you please share your settings :) thank you
-
@agaitan026 Will do. Might not be today, however. Sorry if the language above is not precise, it will make more sense when you see the settings.
I should add that I like pfblockerng. I use it for some light geo blocking and some other ip lists. I do prefer pi-hole for the GUI and the flexibility to create groups and manage blocklists, blacklisted domains and whitelisted domains on a client by client basis or a group of clients. For example a couple of apps on my Apple TVs will not work unless some domains are whitelisted. I don't want to whitelist them for every client (google ad network stuff), just the apple TV's. With pi-hole you can do that easily directly in the GUI.
-
@jwj correct thats what i like from pihole
-
This post is deleted! -
what i saw with my current setup, if i stop pihole, all my conectivity goes down, any chance to have pfsense as backup dns resolver?
-
@agaitan026 Yeah. No DNS resolution but you still can connect to anything by IP.
When it happens, say your on a MAC, you just go to network settings and manually put in the gateway until the problem is fixed. I assume windows has likewise settings. You can do that on an iPhone also.
Mine (on a Raspberry PI) has never died unexpectedly. I guess you could setup two...
I guess the question really is if I have say, 192.168.100.12 and 192.168.10.1 as servers will it use the first always unless the first is unavailable. I'm not sure but I think the answer is no. @johnpoz would know for sure.
-
You can not give a client more than 1 NS and know for sure which one they might query... You just can never know..
If your going to give a client more than 1 NS, then you need to make sure that both NS you give it resolve the same stuff.. For example if 1 filters and the other does not - you can not be sure that the client will use the unfiltered one only if the filtered one is offline.
Not sure were people get the idea that dns is some fragile thing that requires backup.. If it goes down... Yo will know about it - that is for sure.. Just fix it ;) Or point your client to another NS while you do.
The nice thing about dhcp, it is really simple to point your whole network to different NS if you setup goes down for some reason..
Using 2 piholes for example works sure - but now your logs are split and you have to look to both to know what say client ABC looked for, etc.
I have most of my clients use pihole, unless I don't want them being filtered. If so then I set them to use pfsense. If my pihole went down... Which it never has - running on a old pi 3B.. It would take only minutes to point just directly pfsense for dns.
This is my home network - this is not some mission critical network where millions are lost an hour if network is down, etc. Can tell you for damn sure my internet goes out way more often then my dns ;)
Do you have a backup internet connection? I would be putting that in place before ever thinking of needing to run more than 1 pihole on my network.
If your really concerned. Have a 2nd place you can fire up pihole in a couple of minutes. I would take all of 2 minutes for me to fire up a pihole docker or vm.. And then again don't really need that because if pihole went down - I would just point to pfsense directly, until I could get pihole working again. So I run unfiltered dns while I do that - not concern to be honest. So my wife gets a few ads on her game she is playing on the ipad ;)
Clients have a tendency to flip, and check both to see which one is faster, etc. And if for some reason NS1 doesn't answer fast enough, or at all - then switches to 2, and it might not go back to 1 ever or quite some time later. And if you send back a NX, client not going to ask the other one etc. It was told the record didn't exist - so why should it ask another NS? So you could run into a problem where your local records would not resolve, yet all your dns is up.. If your 2 different NS can not resolve the same stuff, etc.
You are much better off just using 1 NS, having a fall back you can switch to quickly then trying to running multiple NS at that same time that your clients point to..
Another quick way for recovery, is just bring your backup dns online with the same IP... This is really simple via a docker or VM, or another pi for example.. You could have pihole all setup on some other pi, and if your pihole pi goes down. Just bring up other pi with the same IP or secondary IP that is the same as your other device that was running pi.
Its not like it takes hours to restore dns if where its running currently goes down - shoot in a pinch, just point everything to googledns while you bring up your local cache, etc.
-
@johnpoz you right i will keep my settings as it right now, is very unlikely that a pihole goes down for 4 5 6 hours,
-
If it did - pretty sure you would know.. Pretty much instantly ;)
Put a plan in place that if your pi takes a dump, you can restore dns quickly and you will be good.
Depending on your network - it could be something as simple as adding a vip to pfsense so that queries to your pi IP now go direct to unbound on pfsense. Or have a VM you can fire up quickly that has pihole installed on it that you can bring up on the pi that took a dumps IP, etc.
Might be a good idea to test your restore plan as well ;)
You can always just blame any outage on your ISP, to keep the family off your back... Damn ISP down again - those MF's going to call them and give them a piece of my mind ;)
-
@johnpoz yeah, im using right now pihole for whm servers for shared hosting and another projects (win active directory etc). What i did right now was to create a VLAN in the pfsense and configured vmware esxi. Now im trying to configure the best way. Something i noted when i use dns resolver, the website loading is kinda slow, but pihole directly its instantly, i may be doing something wrong.
What exactly you guys recommend me? to have clients connect first to pfsense, then pfsense to pihole? or directly to pihole
as you said @johnpoz you are not fan of redirections
-
@agaitan026 Definitely client -> pi-hole -> unbound
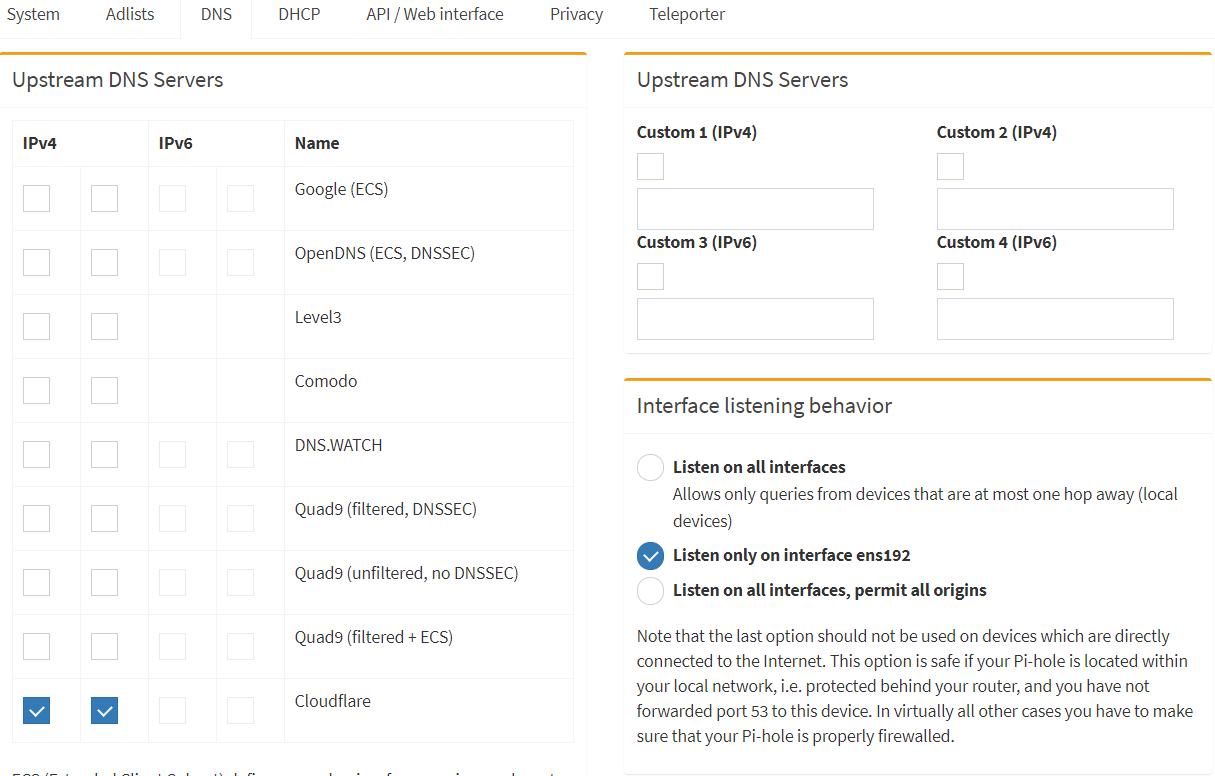
You want unbound resolving not forwarding. There is zero reason to be using cloudflare or google or cloud9. Why would you hand over all that potential data to some third party who may decide to monetize it when you can do that yourself. Unbound resolving is the default on pfsense for good reason.
You would only redirect if you have clients that ignore the config sent from DHCP. The alternative is to just block DNS for those clients that insist on doing their own thing or let them go to google or whatnot.
My Sonos speakers insist on using name servers of their choosing. I redirect them to the pi-hole...
Are you good now? Do you still want to see how I have my DNS related stuff configured? Sounds like you are moving along getting things arranged. I am happy to share some words and screenshots but if your good then I'll save the time...
-
@jwj of course will be nice to see your setup. Appreciate it
-
@agaitan026 Okies. Tomorrow morning I think. :)
-
@agaitan026 OK, here you go. Part 1
First things first.
These settings may not be entirely correct! I think this is complete but I’m not 100% sure. If you use them bad things may happen like:
• Your network might stop working
• Your wife might take up an annoying hobby, like playing the trumpet
• All of the kids in your neighborhood start playing on your front lawn. This will cause you to scream: “Hey you kids, get off my lawn”. Not a good look!This is all applicable to an ipv4 network. I’m not going to touch on ipv6 at all. For a lot of simple setups it still just all works. When you add in a pi-hole you’ll have to figure out a few things. That varies depending on your particular situation. Does you prefix change or not and so on. How do you turn off privacy extensions on the host your running pi-hole. What the heck are those weird looking domain names. Stuff like that. Too many moving parts and if I go down one road and it’s blindly followed it will break things on setups that have different requirements. So, sorry. Not going to get into it. I will say Dynamic prefixes suck. Not all dynamic prefixes change as long as you don’t get a new cable modem or the like. Depends. The inconstant way ipv6 is implemented vendor to vendor sucks. One Linux distro does it different that some other. It doesn’t need to be this hard. As to the issue why use ipv6 at all? Yes, you should, it’s the future. Ipv4 is broken. It’s all workaround. Will your life suck if you don’t implement ipv6? Not at the moment it won’t.
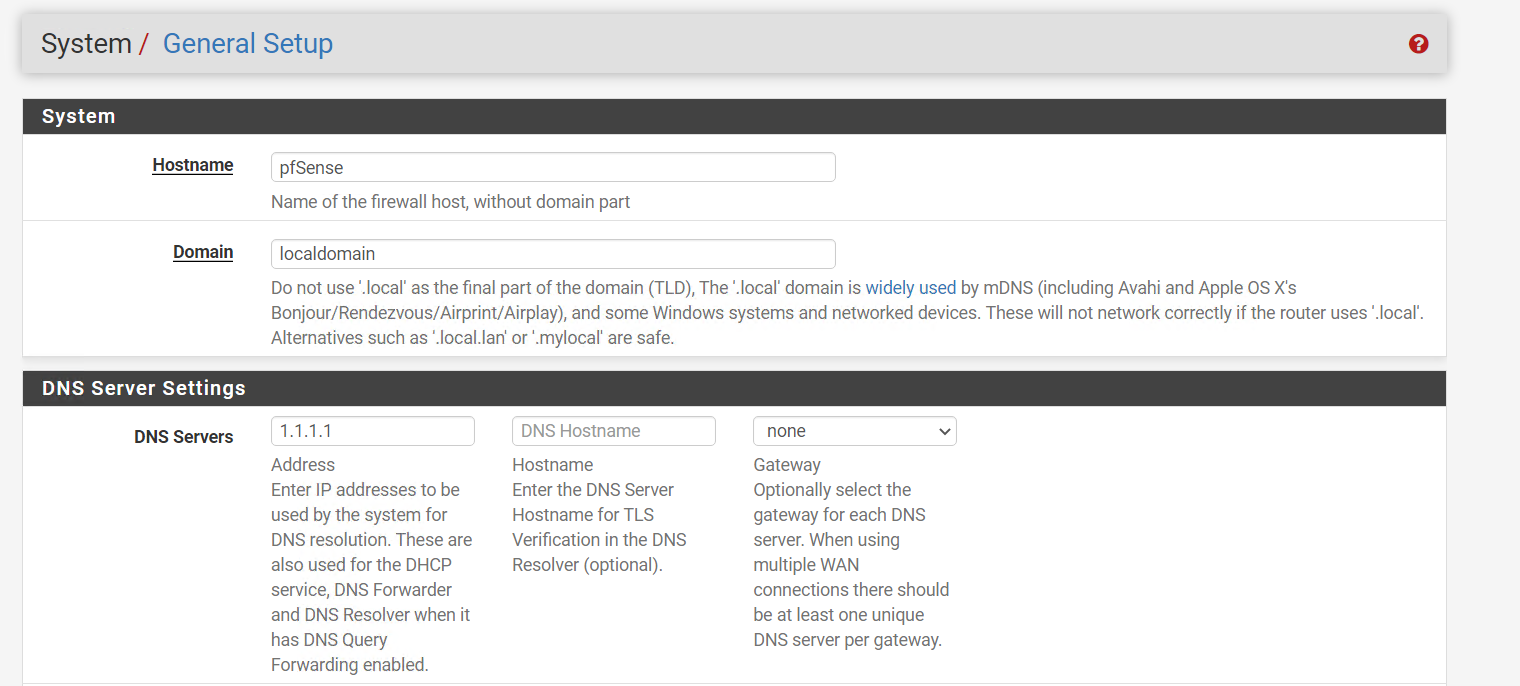
The first step is to make sure your DNS setup is reasonable. You want to be using Unbound as a resolver.
In general settings take note of the domain set. You’ll want this later.
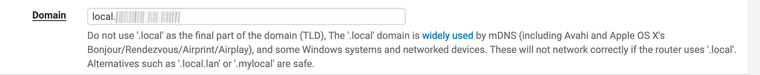
Make sure you haven’t set any external name servers. You want it to look like this.
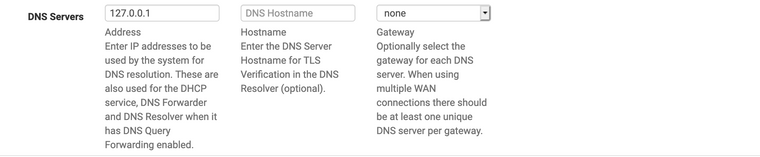
Make sure this isn’t set:
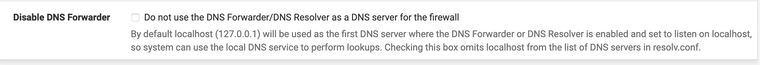
In Services -> DNS Resolver you want default values and then:
Now hop over into Services -> DHCP Server
Assuming you have ONE private network. If you have more you check this on each tab.
Blank is what you want.
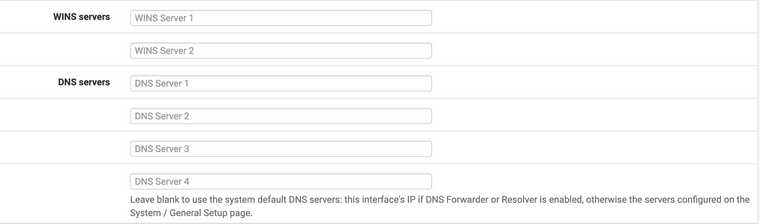
I think it’s a good idea to setup static reservations for each known device on each private network.
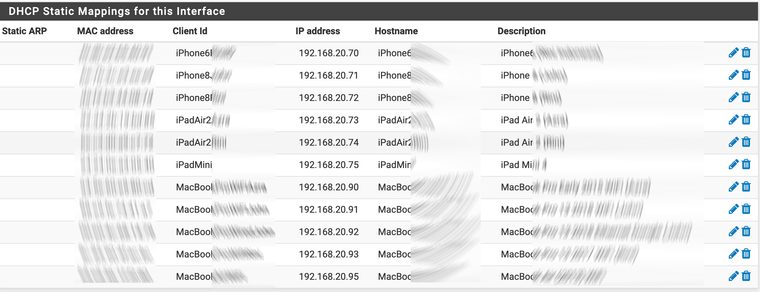
Looking at one of them.
Notice the DNS Servers are blank.
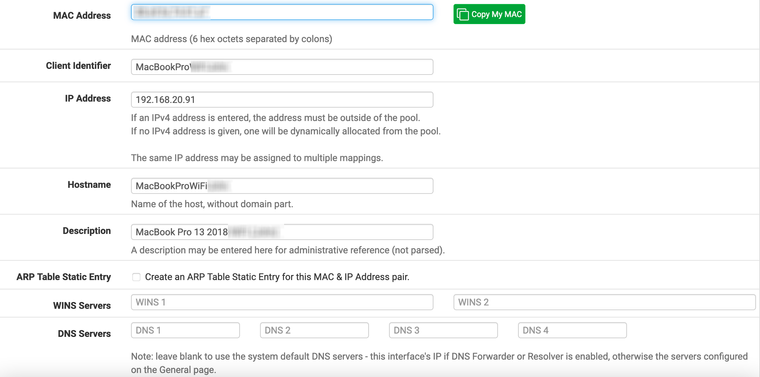
The hostname set is the hostname that will be registered with Unbound. That’s handy. You can then lookup devices by that hostname <hostname>.<local domain name>. The local domain name is set in general settings that you noted earlier. Some devices, Sonos, use crazy hostnames. Like ZSonos or something like that for every speaker. Setting a hostname in the DHCP reservation cleans that up.
At this point things should be working. It’s a nice simple default setup. You might be asking about redirecting DNS? It’s in the pfsense documentation so it must be something you want to do? Well… That depends.
If your clients are well behaved you don’t need to do that. If they use the DNS servers given to them by DHCP you’re good to go.
What if they don’t?
That’s a bit more complicated.
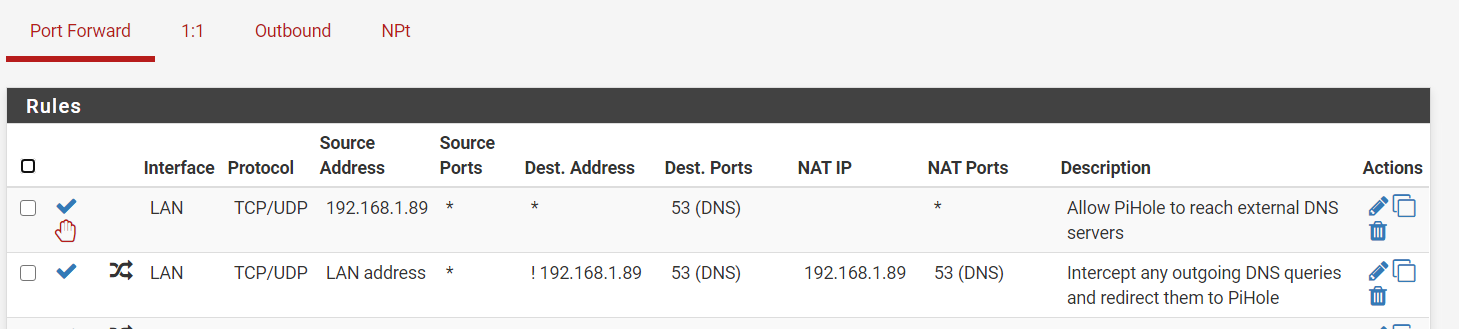
You could just block DNS for them with a firewall rule. The thinking is that you either play by the rules or you get no DNS resolution. OK. I guess. Maybe…
You can redirect them. Setup a NAT port forward and force all DNS traffic to the gateway (or pi-hole). Look at the pfsense documentation for how to do that. That sounds like a good idea until you have a valid reason to point a device to some other name server. It won’t work because it will be redirected. Not going to get into a shouting match about this. Do as you please.
At this point we have ticked a few boxes, setup DHCP reservations and started enjoying an out of the box setup. Still not blocking ads.