LAN Clients can Ping out, but nothing else
-
@theokonos said in LAN Clients can Ping out, but nothing else:
using the official guide
This one https://docs.netgate.com/pfsense/en/latest/recipes/virtualize-proxmox.html ?
-Rico
-
@rico Yes, that one. but how could something be borked upstream when pfsense has no issue without outbound access? I can ping and port-test beyond my router from pfsense itself. And all of my LAN traffic is being NAT'd with the WAN IP of pfsense, so it should all appear the same to the upstream router.
-
Can you draw how your stuff is connected together including IP/network addresses?
-Rico
-
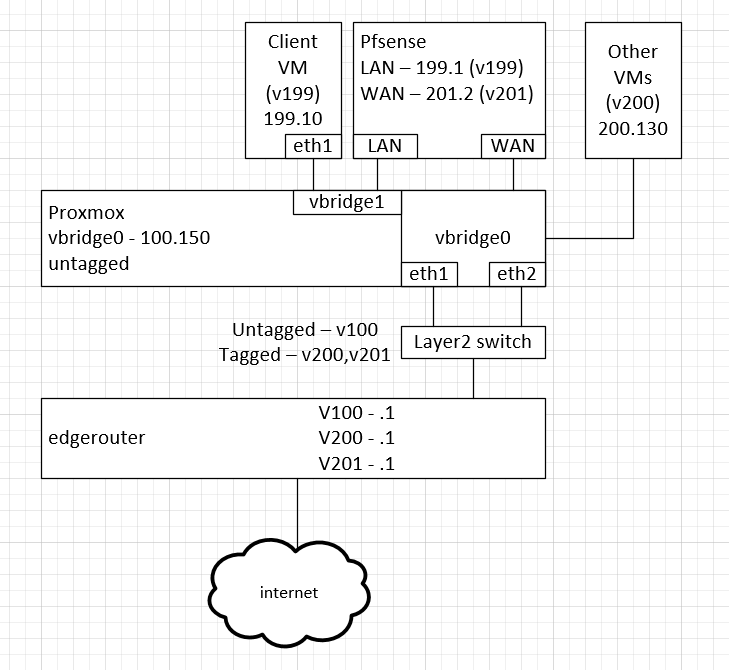
@rico So, here are a couple of illustrations. One is more proxmox-centric and the other is more topology-centric.
Basically, I have three gateway interfaces on my router: one for proxmox's management subnet (.100), one for my other normal VMs (.200), and one for a point-to-point link between my router and pfsense's WAN (.201).
Proxmox is enabled with two bridges; one that allows VMs to connect to my router directly (vbridge0), and one without any ports in it (just an empty virtual switch) that allow other VMs to connect to pfsense (vbridge1).
pfsense has its WAN on vbridge0 and its WAN on vbridge1.
In this topology, pfsense should be able to talk directly to my router's vlan 201 address as its upstream gateway. Then any VMs connecting to pfsense would connect to vbridge1 on vlan 199. (I'm doing all of my VLAN tagging actually on the individual VM interfaces, not in the OS or pfsense config.)
Here is an illustration of the bridges and the system architecture:
And here is one that's more straightforward regarding the network topology:
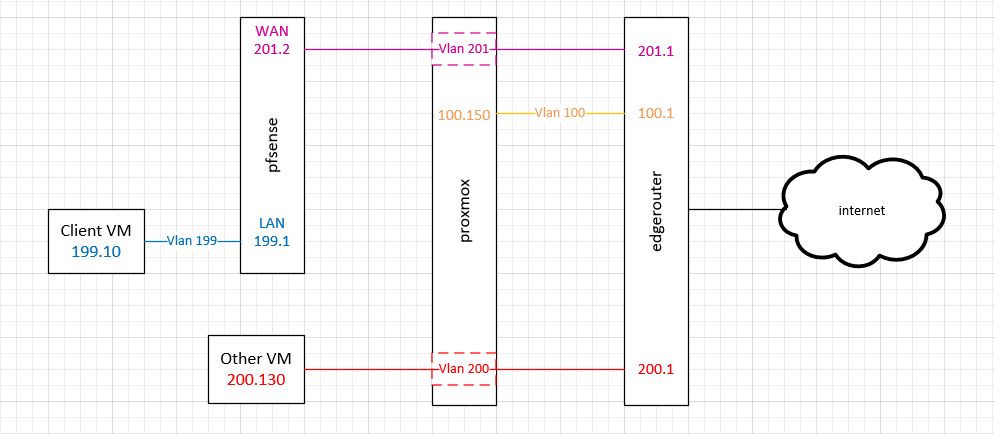
(all IPs are 10.1.x.x)
-
Hmm, well that should pass. I would look in the rules file
/tmp/rules.debugto see what rule that tracker is for.Are you using dhcp on the LAN side?
You have any floating rules?
Steve
-
@stephenw10 @Rico Well, thank you both for your input and your help. Time for me to eat some crow!
Because while I said that I had followed the official pfsense guide for proxmox installation, I had neglected to change a configuration setting toward the end of the guide. I think I had done it initially, but after several factory resets I at some point forgot to re-apply the setting.
In proxmox, hardware checksum offloading must be disabled in pfsense for proper functionality. The guide makes it seem like it's just for performance reasons, but in a virtual environment like proxmox, the hardware obviously isn't available. And apparently this can mess with pfsense's routing, because as soon as I disabled the offloading, everything started passing.
The setting in question is found here in the guide: https://docs.netgate.com/pfsense/en/latest/recipes/virtualize-proxmox.html#configuring-pfsense-software-to-work-with-proxmox-virtio
Thanks again for your help!
Theo -
Using VirtIO NICs?
I have a number of pfSense VMs in Proxmox without that disabled and they work fine.
That would not explain that blocked traffic either. I suspect there might have been more happening here. Disabling Hardware Checksum Offloading is certainly a good idea though.
Steve
-
@stephenw10 Yeah, VirtIO NICs. And yeah that's another one of the reasons why I hadn't re-applied it. But low and behold, after trying everything else, I disabled it and it started working.
-
Take the win and move on.

-
Glad you have it working now.

-Rico