BIND filter-aaaa
-
@johnpoz said in BIND filter-aaaa:
Grab that script that is linked too, put in a file called no-aaaa.py and copy that file to your /var/unbound dir
Upgraded to 2.4.5_1 and noticed that this file [that was there for quite some time] - no-aaaa.py - is gone. Copied it over, rebooted and noticed that the file is gone again. Finally, realized that /var/ is mounted in RAM. So, where this file should be stored?
-
Would be safe in
/rootor/confor a subdirectory of those. -
Not sure what your taking about on 2.4.5p1 and file is right where it was in /var/unbound
2.4.5-RELEASE][admin@sg4860.local.lan]/root: cd /var/unbound [2.4.5-RELEASE][admin@sg4860.local.lan]/var/unbound: ls -la total 84 drwxr-xr-x 5 unbound unbound 1024 Jun 16 05:37 . drwxr-xr-x 31 root wheel 512 Jun 2 16:54 .. -rw-r--r-- 1 root unbound 185 Jun 14 07:14 access_lists.conf drwxr-xr-x 2 unbound unbound 512 Jun 2 16:54 conf.d drwxr-xr-x 2 root unbound 512 Mar 28 07:52 dev -rw-r--r-- 1 root unbound 698 Jun 14 07:14 dhcpleases_entries.conf -rw-r--r-- 1 root unbound 65 Jun 14 07:14 domainoverrides.conf -rw-r--r-- 1 root unbound 6838 Jun 14 07:14 host_entries.conf -rw-r--r-- 1 root unbound 1404 Mar 28 07:51 no-aaaa.py -rw-r--r-- 1 root unbound 0 Jun 16 15:00 pfb_dnsbl.conf -rw-r--r-- 1 root unbound 300 Sep 17 2017 remotecontrol.conf -rw-r--r-- 1 unbound unbound 758 Jun 16 05:37 root.key -rw-r--r-- 1 unbound unbound 759 Dec 4 2019 root.key.67289-2 -rw-r--r-- 1 root unbound 3369 Feb 28 2019 sslcert.crt -rw------- 1 root unbound 0 Feb 28 2019 sslcert.key -rw-r--r-- 1 root unbound 5297 Jun 14 07:14 unbound.conf -rw-r----- 1 unbound unbound 2455 Sep 17 2017 unbound_control.key -rw-r----- 1 unbound unbound 1330 Sep 17 2017 unbound_control.pem -rw-r----- 1 unbound unbound 2459 Sep 17 2017 unbound_server.key -rw-r----- 1 unbound unbound 1318 Sep 17 2017 unbound_server.pem drwxr-xr-x 3 root unbound 512 Mar 28 07:52 usr [2.4.5-RELEASE][admin@sg4860.local.lan]/var/unbound: cat no-aaaa.py def init(id, cfg): return True def deinit(id): return True def inform_super(id, qstate, superqstate, qdata): return True domains = [ "netflix.com.", "nflxso.net.", ] def operate(id, event, qstate, qdata): if event == MODULE_EVENT_NEW or event == MODULE_EVENT_PASS: if qstate.qinfo.qtype != RR_TYPE_AAAA: qstate.ext_state[id] = MODULE_WAIT_MODULE return True for domain in domains: if qstate.qinfo.qname_str == domain or qstate.qinfo.qname_str.endswith("." + domain): msg = DNSMessage(qstate.qinfo.qname_str, RR_TYPE_A, RR_CLASS_IN, PKT_QR | PKT_RA | PKT_AA) if not msg.set_return_msg(qstate): qstate.ext_state[id] = MODULE_ERROR return True # We don't need validation, result is valid qstate.return_msg.rep.security = 2 qstate.return_rcode = RCODE_NOERROR qstate.ext_state[id] = MODULE_FINISHED log_info("no-aaaa: blocking AAAA request for %s" % qstate.qinfo.qname_str) return True qstate.ext_state[id] = MODULE_WAIT_MODULE return True if event == MODULE_EVENT_MODDONE: qstate.ext_state[id] = MODULE_FINISHED return True -
I see something different on my system (apu2)...
Then I realized that I haveUse memory file system for /tmp and /varset. Now all is clear. It looks like I never rebooted my router after the previous upgrade! -
@jimp said in BIND filter-aaaa:
Would be safe in /root or /conf or a subdirectory of those.
OK, stored it in /conf and created an earlyshellcmd script (similar to the old one) to restore the file from the persistent location. Solved!
-
With the new version of pfblocker if you have enabled the python mode you can no longer select no-aaa in Unbound. How can the ipv6 removal script be integrated with pfblocker?
-
Hummm.
Dmnd.
You're right."no-aaaa" is a strange beast.
The idea that unbound can use external python script to 'filter' DNS traffic for unbound is what is pfBlockerNG V3 all about.Comparing no-aaaa.py and pfb_unbound.py shows similarities.
no-aaaa is small.
There is a table with domain names.
And there is that small function that does the work : "operate".
I'm not a python expert, but I can read it.Right now, our no-aaaa stops if the request isn't an 'AAAA' type.
This is what the first 'if' test does :
if qstate.qinfo.qtype != RR_TYPE_AAAA:it should be inverted.
This way, execution continues with comparing the DNS request with the domains stored in the domains[] array.To make a long story short :
# DNSBL Validation for specific RR_TYPES only if pfb['python_blacklist'] and qstate is not None and qstate.qinfo.qtype is not None and qstate.qinfo.qtype in pfb['rr_types']: q_name_original = get_q_name_qstate(qstate) q_type = qstate.qinfo.qtype if q_type == RR_TYPE_AAAA: for domain in domains: if qstate.qinfo.qname_str == domain or qstate.qinfo.qname_str.endswith("." + domain): msg = DNSMessage(qstate.qinfo.qname_str, RR_TYPE_A, RR_CLASS_IN, PKT_QR | PKT_RA | PKT_AA) if not msg.set_return_msg(qstate): qstate.ext_state[id] = MODULE_ERROR return True # We don't need validation, result is valid qstate.return_msg.rep.security = 2 qstate.return_rcode = RCODE_NOERROR qstate.ext_state[id] = MODULE_FINISHED log_info("[pfBlockerNG] : no-aaaa: blocking AAAA request for %s" % qstate.qinfo.qname_str) return True # Create list of Domain/CNAMES to be evaluatedThe first and last line are comments are already present in the code.
Just replace / place what's in between them.
The 'operate' function is at the bottom.edit : python is tabindent sensible.
Also, just above the 'operate' function, add your domains array :
domains = [ "netflix.com.", "nflxso.net.", "nflxext.com.", "www.netflix.com.", "assets.nflxext.com.", "scdn.nflximg.net.", "secure.netflix.com.", "www2-ext-s.nflximg.net.", "so-s.nflximg.net.", ]I advise strongly to to make a backup of your pfb_unbound.py file.
Keep in mind : for every domain that is AAAA filtered, an 'A' is retrieved, and no more pfblocker python code - the rest of the operate function, gets executed.
Until proven wrong, this breaks everything .
.edit : but think about it : the domains listed in our domains array are sites we WANT to visit - and only using 'A', NOT 'AAAA'. No real need - for me - to log or do other things with the domains that are (white !) listed using the domains [].
The log line shows that something is working :
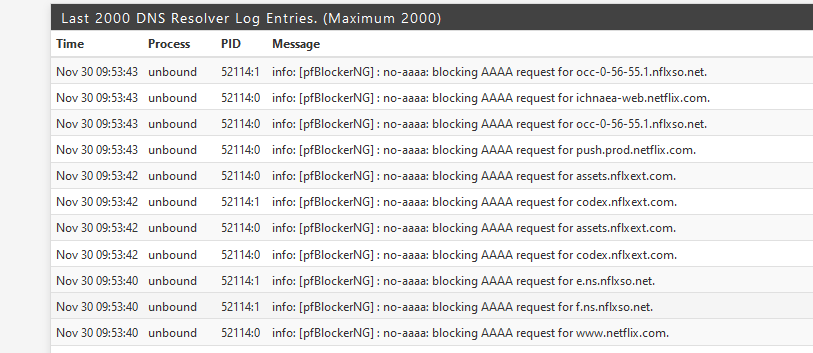
Now me hoping someone more python minded steps in.
The domain array should be lifted into the pfBlockerNG GUI.
I don't even now if this kind of scripting belongs into pfBlokcerNG ....
And why can't there be 2 python scripts : the already known no-aaaa.py and the new kind on the block : pfb_unbound.py ?
Why should we have to choose ? Is this an unbound limitation ? A pfSense limitation ?
For more edits, I'll continue to get home first. Right now, people start to wake up all arround me, and I'm exploding the DNS way to often == "no internet". And me learing python in the proces is not a good mix.edit : I'm using no-aaaa because I have to use tunnel.he.net for my IPv6 access.
My ISP doesn't know what IPv6 is - and the IPv6 they can propose is a #@!^@!& broken simple /64. My ISP - the biggest in Europe (?) doesn't quiet understand that companies can have more then one LAN .....Without no-aaaa, my network setup 'prefers' IPv6 if available, and it is as I'm using tunnel.he.net for my IPv6 access. Netflix is also IPv6-ready. Netflix doesn't want to stream over tunnel.he.net because it's considers I'm hiding myself as what happens when I would use a typical VPN service. Content fails to stream .... That's why no-aaaa exists.
Netflix works now for me using the patched pfb_unbound.py file

edit (again) :
I didn't notice this before :
Where I am right now, @work, I never watch Netflix.
I restarted pfSense with pfBlocker completely disabled.
My browser couldn't even connect to ww.netflix.com. That's new. Before, I could login, see the screen with series and movies, only the actual streaming wouldn't work as it would use IPv6 etc.
With pfBlocker enabled - same thing - netflix isn't accessible, but the first test is needed to be sure the netflix domain or IP's is not in some of the feeds I use.With the patched code above, Netflix is accessible and works.
-
Added to the above :
This : /var/unbound/unbound.conf :
# Python Module python: python-script: no-aaaa.py python-script: pfb_unbound.pywould be nice.
No need to edit @BBcan177 's python script !Guess what : unbound, the version we use - only accepts ONE python module. Not multiple modules.
When I modify the config generating code so I obtain an unbound.conf as shown above, only the python script "no-aaaa.py" gets loaded. Not the second "pfb_unbound.py".
Accoring to :
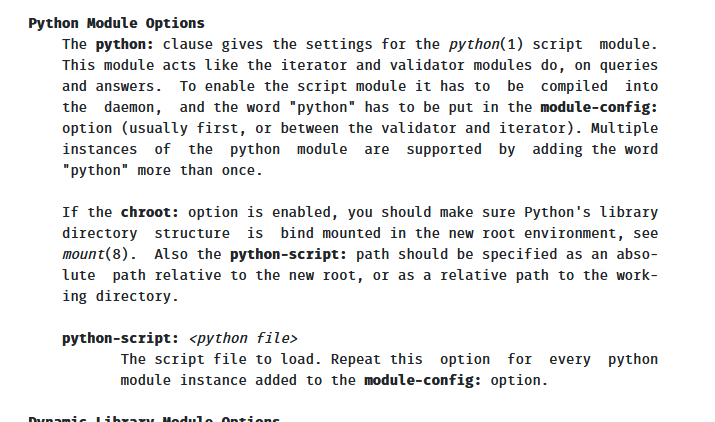
See the last paragraph here https://nlnetlabs.nl/documentation/unbound/unbound.conf/ - it should be possible.
Our 2.4.5-p1 unbound version is probably to old. -
I hope the next version of pfsense will integrate the functionality of using more than one python script having an updated version of unbound.
-
@mikekoke said in BIND filter-aaaa:
I hope the next version o
The next version of pfBlockerNG-devel, probably the upcoming 3.0.0_4 will have the "No AAAA" build in.
No more script files to manage. Just enter your list with host names that won't work well using IPv6, and you're done :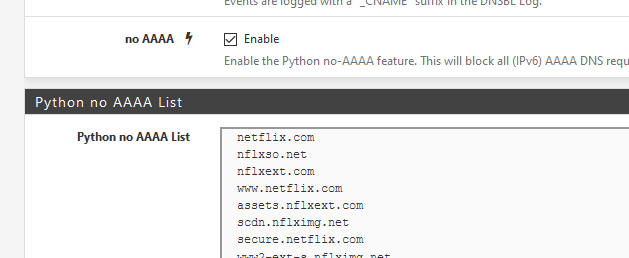
-
@gertjan
Great news as soon as I can I will update pfblocker, can I know which domains you have added to the list? -
https://forum.netgate.com/topic/159016/pfblockerng-devel-v3-0-0_5
@mikekoke said in BIND filter-aaaa:
which domains
Normally : none.
Read https://forum.netgate.com/topic/118566/netflix-and-he-net-tunnel-fixed-using-unbound-python-module -
@gertjan
Need a little help please...I upgraded my pfBlockerNG-devel from a pre-v3 version to 3.0.0_7 this afternoon. I was previously using the no-aaaa script in unbound, and I am now trying to migrate that across to pfBockerNG-devel. I think I have ticked all the required boxes and I have entered my domain list, but it only seems to work for the domains as entered, and not for any hosts which are part of that domain, i.e. it is as if each line entered is treated like an individual host.
For example, I have entered office.com in the list, and resolution of office.com returns only an IPv4 address, but outlook.ms-acdc.office.com returns both IPv4 and IPv6 addresses. The previous no-aaaa script had "office.com." as the domain, but if I include the last "." in pfBlockerNG-devel it doesn't work at all. Effectively I want IPv4 resolution only for "*.office.com". I presume that is possible in pfBlockerNG-devel?
Thanks
-
@aberdino might be good to post this over on the announcement thread, a lot of minor changes were being patched by the dev fairly quickly as they were reported over there.
https://forum.netgate.com/topic/158592/pfblockerng-devel-v3-0-0-no-longer-bound-by-unbound
-
@aberdino said in BIND filter-aaaa:
For example, I have entered office.com in the list, and resolution of office.com returns only an IPv4 address, but outlook.ms-acdc.office.com returns both IPv4 and IPv6 addresses. The previous no-aaaa script had "office.com." as the domain, but if I include the last "." in pfBlockerNG-devel it doesn't work at all. Effectively I want IPv4 resolution only for "*.office.com". I presume that is possible in pfBlockerNG-devel?
The upcoming version of pfBlocker, the one after 3.0.0_7 (not yet released, it's upcoming) will do this correctly :
Consider :
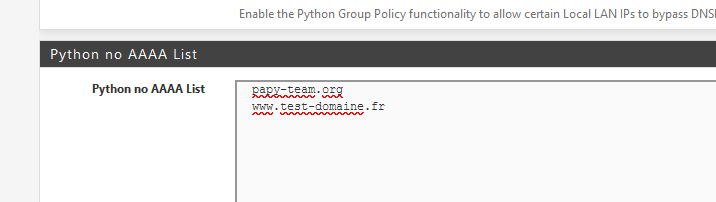
( do a Force Update after saving these settings ! - flush local DNS caches)
[2.4.5-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: host papy-team.org papy-team.org has address 87.98.136.44 papy-team.org mail is handled by 20 mail2.papy-team.org. papy-team.org mail is handled by 10 mail.papy-team.org. [2.4.5-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: host www.papy-team.org www.papy-team.org has address 87.98.136.44 [2.4.5-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: host pop.papy-team.org pop.papy-team.org has address 87.98.136.44So, the domain itself, and all sub domains will be A only.
But - in the case of "www.test-domaine.fr" :
[2.4.5-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: host test-domaine.fr test-domaine.fr has address 5.196.43.182 test-domaine.fr has IPv6 address 2001:41d0:2:927b::15 test-domaine.fr mail is handled by 20 mail2.test-domaine.fr. test-domaine.fr mail is handled by 10 mail.test-domaine.fr. test-domaine.fr mail is handled by 30 mail.test-domaine.fr. [2.4.5-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: host www.test-domaine.fr www.test-domaine.fr has address 5.196.43.182 www.test-domaine.fr has IPv6 address 2001:41d0:2:927b::15Strange !!
Only the sub domain www.test-domaine.fr should be "A" only (no AAAA). The domain itself will return an AAAA (that's ok), but the sub domain listed in the Python no AAAA List "www.test-domaine.fr" - see above - also returns an AAAA !
(note : I'm using the upcoming 0.0._8 version here, not yet released)I wonder :
.papy-team.orgshould block AAAA for the domain and all possible sub (and sub sub etc) domains ,
and without the starting dot, likepapy-team.orgshould block AAAA for the domain - and NOT for the sub domains ?
Remark
- don't know if such a feature is needed.
- The syntax with the starting dot should be inversed ? Like ".papy-team.org" is blocking this domain and all sub domains, and without the starting dot, like "papy-team.org" only that domain without doing the wildcard thing ?
-
@gertjan your suggestion sounds best to me. Make it work exactly like the dnsbl whitelist function, leading ". " for all subdomains, otherwise a single record.
-
@bruor
Agreed, and thank you both. -
-
-
@aberdino said in BIND filter-aaaa:
@Gertjan and @bruor
I might have spoken too soon, as it's not working now, I'll do some further digging...Just to close this issue, I'm now on pfSense 2.5.0 with pfBlockerNG-devel 3.0.0_10 and the wildcard AAAA blocking works great. Thank you guys

-
T throwaway29 referenced this topic on