Trouble accessing SG-1100 web UI via IPsec
-
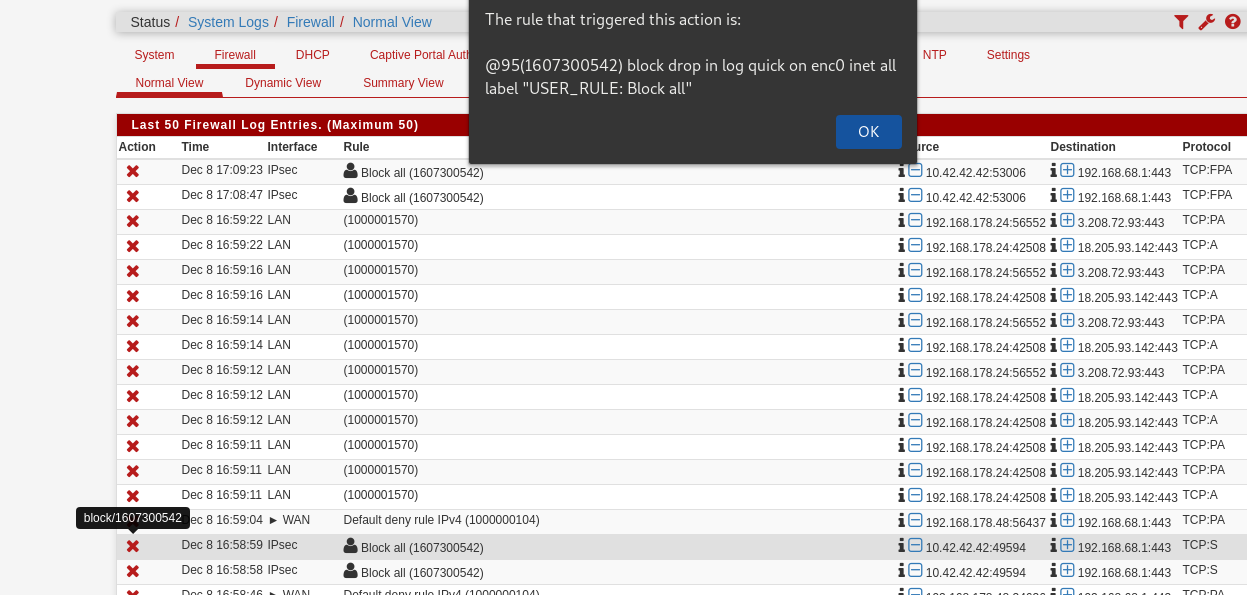
Can we see a screenshot of the blocks that happen when you do that?
Steve
-
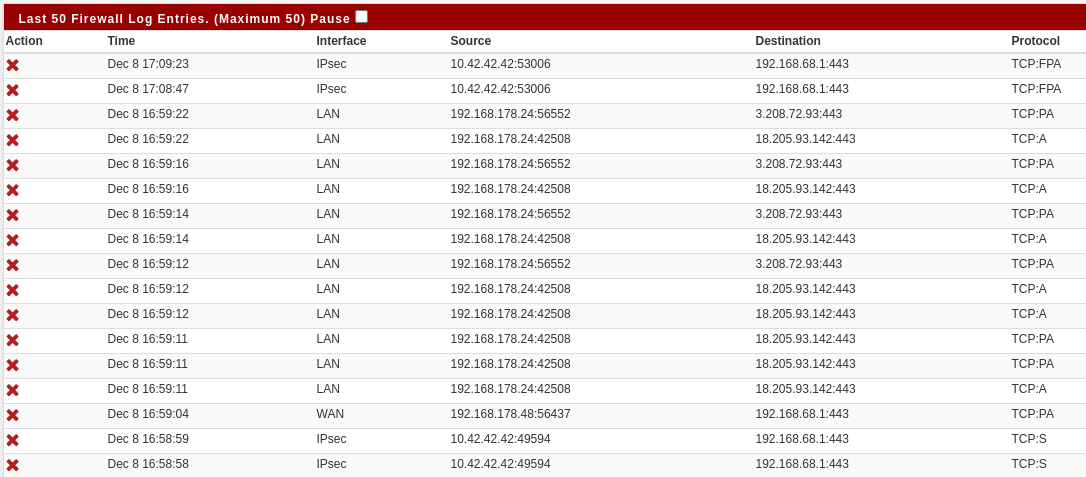
The 10.42.42.42 is my IPsec IP. The 192.168.178.24 was my LAN IP.
And the IPsec tab firewall rules are:
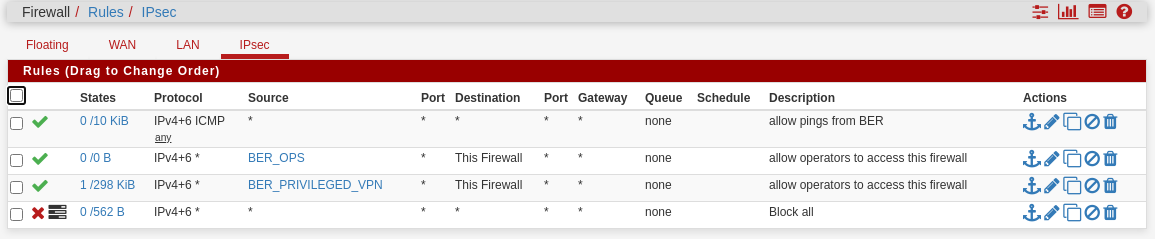
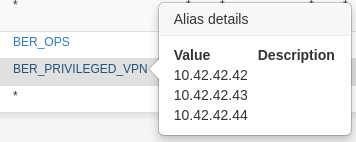
with the relevant alias "BER_PRIVILEGED_VPN" looking like this:
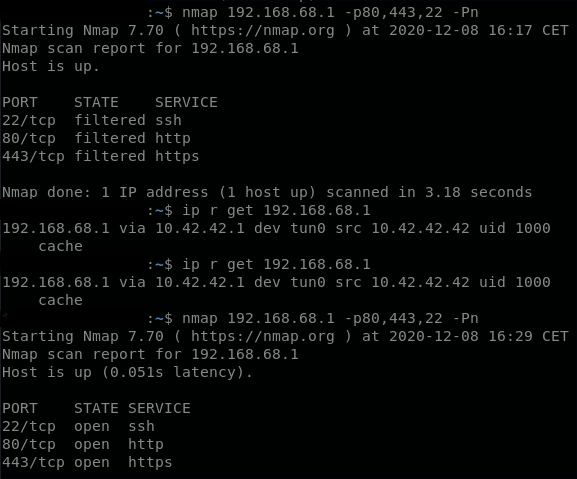
and the port scan before and after retry (this one from an earlier case like that. I apparently didn't even port scan anymore on the last one, just triggered the reboot):
-
The blocked TCP:S is odd given those rules.
What rule does it show is blocking that traffic if you mouse-over the X?
-
-
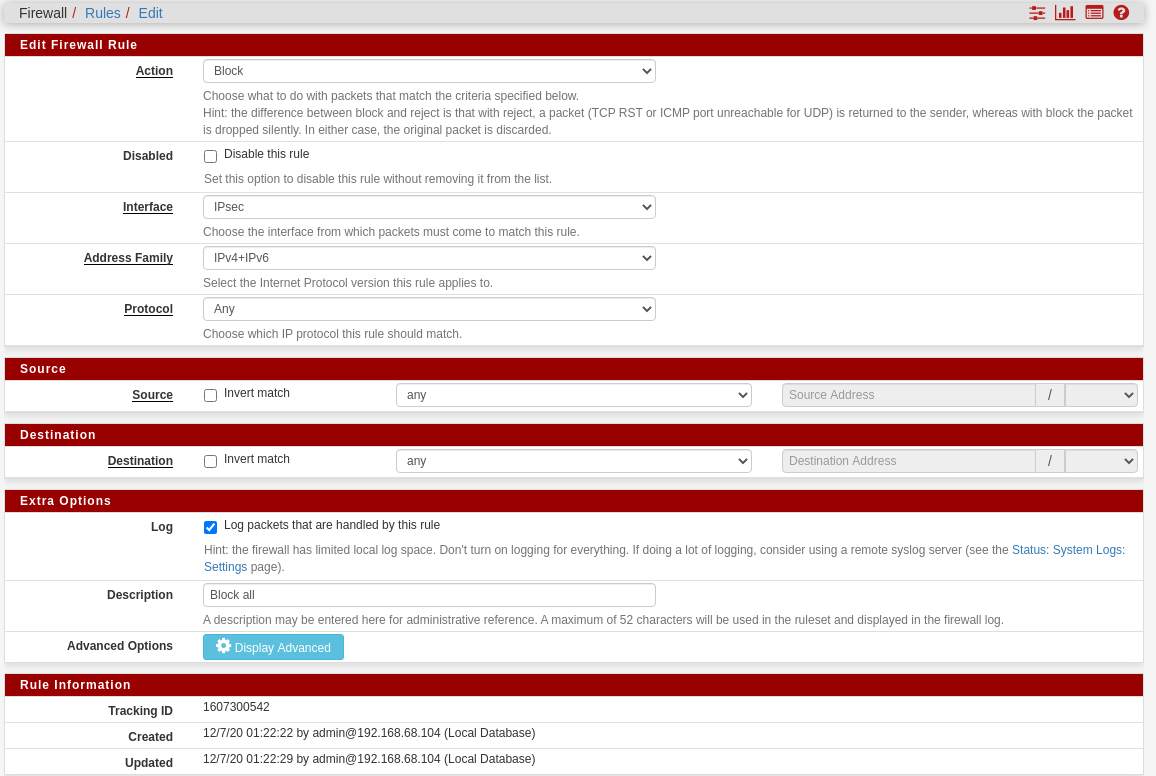
Ok, so it's not matching the pass rule somehow. Either the alias is not populating for some reason or the ruleset is not loading. Try going to Status > Filter Reload and reloading it. Check for errors.
Steve
-
@stephenw10 the alias seems fine:
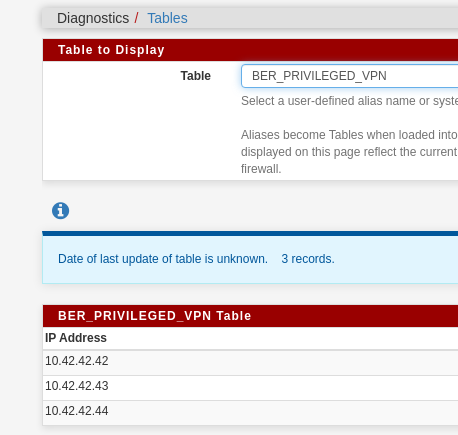
After a filter reload
Initializing Creating aliases Creating gateway group item... Generating Limiter rules Generating NAT rules Creating 1:1 rules... Creating outbound NAT rules Creating automatic outbound rules Setting up TFTP helper Generating filter rules Creating default rules Pre-caching Block all... Creating filter rule Block all ... Creating filter rules Block all ... Setting up pass/block rules Setting up pass/block rules Block all Creating rule Block all Creating filter rule Block all ... Creating filter rules Block all ... Setting up pass/block rules Setting up pass/block rules Block all Creating rule Block all Pre-caching Default allow LAN to any rule... Creating filter rule Default allow LAN to any rule ... Creating filter rules Default allow LAN to any rule ... Setting up pass/block rules Setting up pass/block rules Default allow LAN to any rule Creating rule Default allow LAN to any rule Pre-caching Default allow LAN IPv6 to any rule... Creating filter rule Default allow LAN IPv6 to any rule ... Creating filter rules Default allow LAN IPv6 to any rule ... Setting up pass/block rules Setting up pass/block rules Default allow LAN IPv6 to any rule Creating rule Default allow LAN IPv6 to any rule Pre-caching allow pings from BER... Creating filter rule allow pings from BER ... Creating filter rules allow pings from BER ... Setting up pass/block rules Setting up pass/block rules allow pings from BER Creating rule allow pings from BER Creating filter rule allow pings from BER ... Creating filter rules allow pings from BER ... Setting up pass/block rules Setting up pass/block rules allow pings from BER Creating rule allow pings from BER Pre-caching allow operators to access this firewall... Creating filter rule allow operators to access this firewall ... Creating filter rules allow operators to access this firewall ... Setting up pass/block rules Setting up pass/block rules allow operators to access this firewall Creating rule allow operators to access this firewall Creating filter rule allow operators to access this firewall ... Creating filter rules allow operators to access this firewall ... Setting up pass/block rules Setting up pass/block rules allow operators to access this firewall Creating rule allow operators to access this firewall Pre-caching allow operators to access this firewall... Creating filter rule allow operators to access this firewall ... Creating filter rules allow operators to access this firewall ... Setting up pass/block rules Setting up pass/block rules allow operators to access this firewall Creating rule allow operators to access this firewall Creating filter rule allow operators to access this firewall ... Creating filter rules allow operators to access this firewall ... Setting up pass/block rules Setting up pass/block rules allow operators to access this firewall Creating rule allow operators to access this firewall Pre-caching Block all... Creating filter rule Block all ... Creating filter rules Block all ... Setting up pass/block rules Setting up pass/block rules Block all Creating rule Block all Creating filter rule Block all ... Creating filter rules Block all ... Setting up pass/block rules Setting up pass/block rules Block all Creating rule Block all Pre-caching allow all OpenVPN... Creating filter rule allow all OpenVPN ... Creating filter rules allow all OpenVPN ... Creating IPsec rules... Creating uPNP rules... Generating ALTQ queues Loading filter rules Setting up logging information Setting up SCRUB information Processing down interface states Running plugins Doneand unplugging from LAN again, then going in via IPsec, the result of a port scan is filtered and the log shows it again:
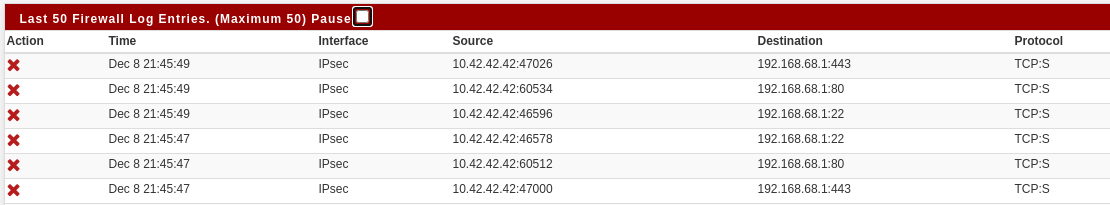
Gonna reboot the SG-1110 now and expect to be fine again.
-
@tumble
can you please try apfctl -vvsTables?
is the table loaded?you should see something like
--a-r-- BER_PRIVILEGED_VPN Addresses:etc etc
you can also test it withpfctl -t BER_PRIVILEGED_VPN -T test 10.42.42.42do you have floating rules ? extra packages installed ?
it's strange because I have a lot of tables, some with 1000/2000 ips, and I never encountered such a problem, there must be some misconfiguration somewhere
but i have a guy on the italian section of the forum with a similar problem
tcp:s blocked by a deny rule even if the ip is inside an alias and a pass rule is present for it -
@kiokoman said in Trouble accessing SG-1100 web UI via IPsec:
do you have floating rules ? extra packages installed ?
Nope, the SG-1100 is pretty much as it comes out of the box. All I did was setting the domain, configuring the DNS resolver and configure the IPsec tunnel + the rules you can see above.
@kiokoman said in Trouble accessing SG-1100 web UI via IPsec:
it's strange because I have a lot of tables, some with 1000/2000 ips, and I never encountered such a problem
Same here on my bigger appliances (XG-7100).
Unfortunately, I had to ship the SG-1100 to our branch office so I lack physical access to it for now and unless it comes back to me for some reason, I won't get physical access again too soon/ever.
-
@tumble
the guy on the italian forum found out that the problem was associated to a wrong value on MTUwrong MTU -> blocked TCP:Sproblem reappeared, it was not mtu for him but maybe related to
https://redmine.pfsense.org/issues/9296 -
Hard to see how that could be. The packet is arriving over the IPSec. TCP Syn packets are tiny anyway. But if you've seen something similar before I guess....
But that pass rule should match and clearly isn't. IP Options on it or something odd?
Steve