Ping between subnets on separate NIC's on the same pfSense machine
-
@viragomann
Thanks. Did the pings like you suggested, and they worked! I was able to ping a computer on the "2" subnet (OPT1) from the "1" subnet (LAN). So with that I will assume all is well, and continue this project to switch away from my ASUS router.Thanks again.
-
If you can ping from Diag > Ping with a source in a different subnet but not from a host in that subnet it implies your firewall rules are probably incorrect. Traffic generated from Diag > Ping does not have to pass them.
Alternatively you may be policy routing traffic (have a gateway set on pass rules). In which case you would need an additional pass rule to allow traffic between local subnets above that.Steve
-
Steve,
Thanks for that. I think the issue is on the policy side ... I have the WAN interface connected to my existing ASUS router, and when I did a tracer route it showed that when pinging the 192.168.2.1 the route goes right to it, but when pinging the computer on 192.168.2.12 it goes to the ASUS router on 192.168.20.1.
I disconnected the WAN and pings went through just like expected. So I assume that the issue lies in how things get routed. I also assume once I move my pfSense setup into “production” and connect the pfSense WAN to my fiber modem this will not be an issue.
Thanks for your suggestions. Learning a little bit more every day!
-
Sounds like you might be doing policy routing.. If you rules force traffic out a gateway.. You would need a rule above that just use normal routing to allow clients on 1 network to talk to 2nd network also attached to pfsense.
This is gone over in the multiwan policy routing section.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html
-
Thanks. That makes sense.
Will be working on this during the day, and if I run into trouble post to this string.
Anders
-
@aswede
OK ... so I have moved pfSense to my "production" system, where I do not have a router upstream - my WAN connection is now to directly to my ISP (fixed IP address). I am set up with three subnets - 192.168.20.0, 21.0, 22.0. My intent at this point is to give the subnets full access to each other.-
With the way I have my settings everyone can get to the internet, so that is a success!
-
I have also followed the instructions I found online to set up an openVPN client (using NordVPN) on the subnet 20.0, with a rule so that any machine that has an IP less than 192.168.20.10 will be routed through the VPN. That works fine too!!!
My problem is that using a computer on subnet 20.0 I cannot configure the printer and AP's that are connected to subnet 21.0. From that same computer on subnet 20.0 I cannot either ping anything on subnet 21.0 or 22.0. However, if I use the ping functionality built in pfSense the pings go through, wheather the source is LAN, OPT1 or OPT2
I have attached a simple outline of the network. This is the behavior I see:
I can access the Internet from each subnet.
From 192.168.22.15 I can ping 192.168.21.250 and 192.168.20.63.
From 192.168.22.15 I can reach the web interface on 192.168.21.250
From 192.168.20.63 I cannot ping anything on subnet 21.0 or 22.0, nor can I reach the web interface for 192.168.21.250I am looking for some advice where to start looking for a problem.

-
-
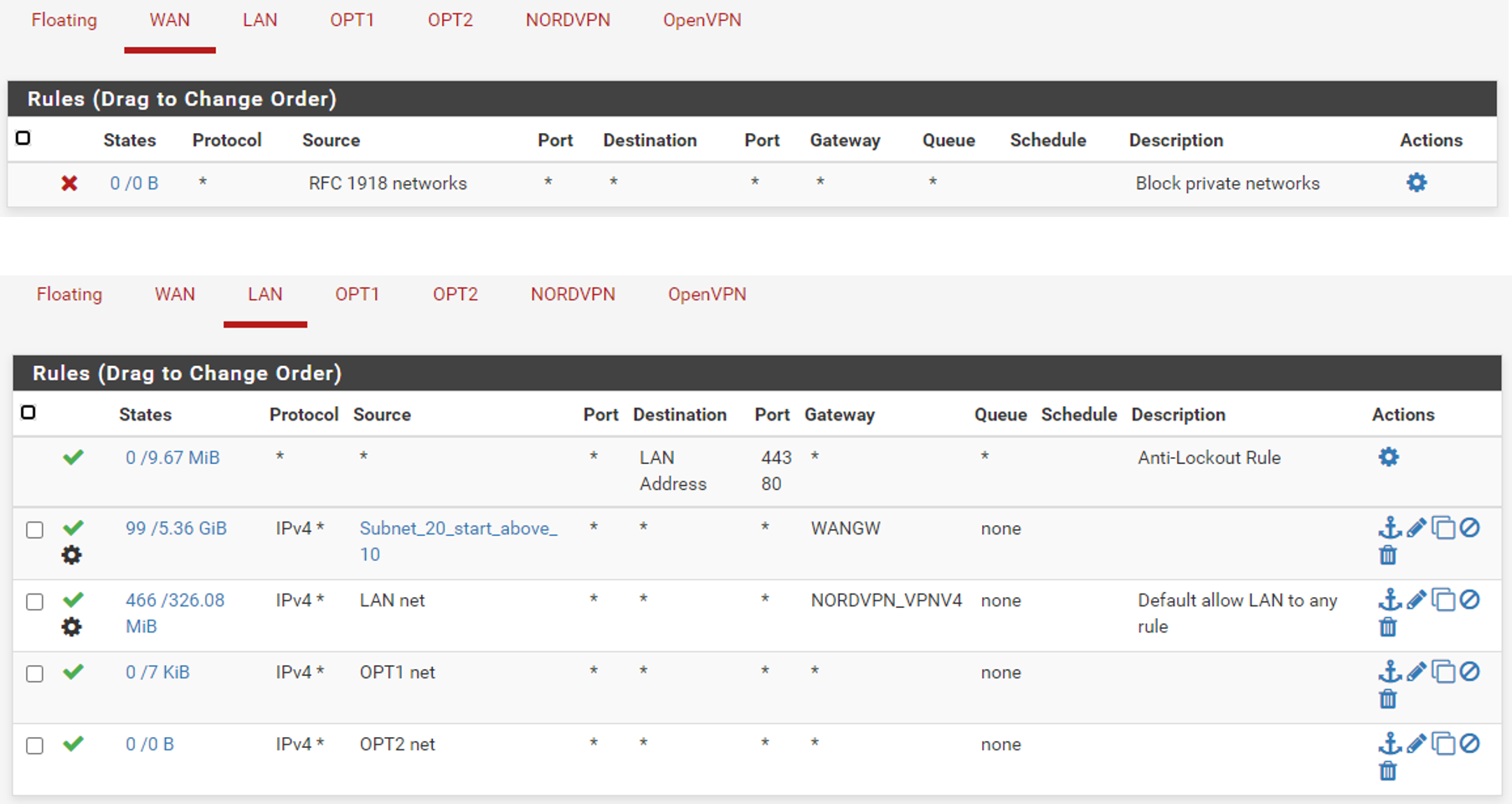
@aswede And lets see your rules.. Again if your policy routing - Ie forcing something out a gateway you wouldn't be able to get t your other vlans.
If you can not ping say the IP address of pfsense opt1 IP from lan, that points to either firewall rules not allowing it on lan, or a policy route forcing traffic out gateway before allowing access to your other local networks.
-
Hope this has the info.
-
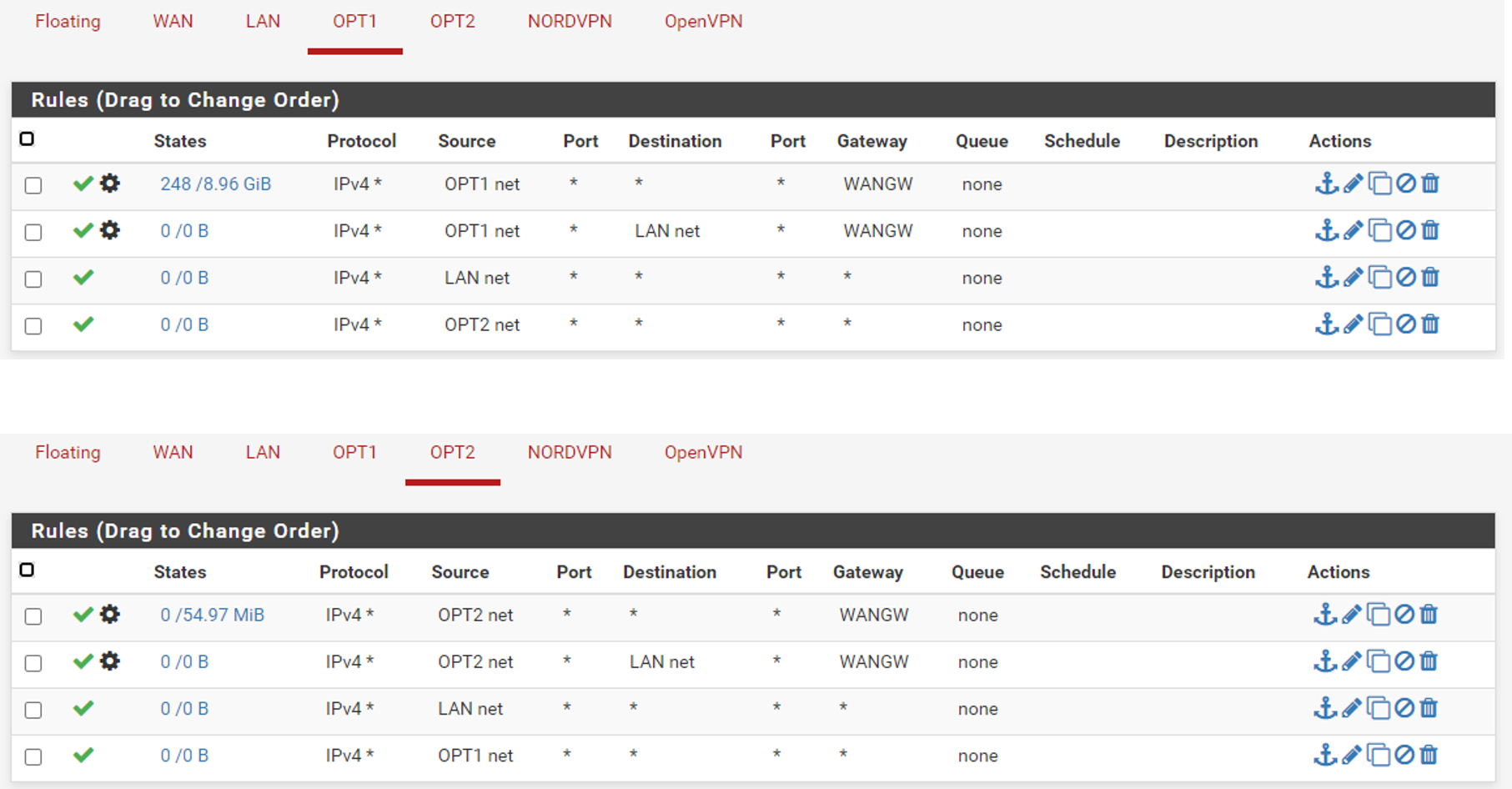
As I mentioned a few posts back - your policy routing
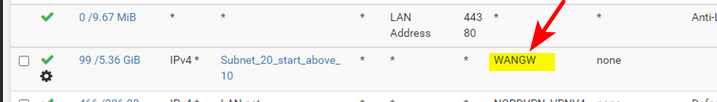
So no your not going to be able to get to other networks locally - can the wan gateway get to your other networks - no!
Your other rules there on lan with opt net as source are just pointless - how would opt net ever be the source network into your lan interface????
Read the link I provided a few posts back - read the section about bypassing policy routes.
-
@johnpoz
OK. Thanks. Now I know where to focus. I appreciate the guidance. Will look at the link you recommended.Thanks again.
-
Rules are evaluated as traffic enters an interface from the network its attached too. So as traffic enters lan, from lan.
First rule to trigger wins, no other rules are evaluated..
If you force traffic out wan, then no you can not get to optX, etc. Or some vpn.
You need rules above that to allow the traffic you want to get to your other networks, without forcing it out some gateway. So that local routing can be used.
it would be impossible for traffic to have a source IP of optX network into the lan interface, from the lan network.
-
@johnpoz
Got it. Changed the top rule, and voila ... it works.
Thanks for your help! Much appreciated.