How to separate 3 LANs on a quad-port NIC so they have no access to the other networks?
-
I am new to pfSense and recently installed it on the and old desktop with the intention of having 3 networks each of which are separate and not able to see the devices on the other networks:
- Lenovo Thinkcentre M series, 3.0Mhz process, 10gb ddr3 RAM
I added a quad port NIC ( HP NC364T Network Card ) and have setup 1 as the WAN port and 3 separate LAN ports:
LAN1: Home network
LAN2: IOT network
LAN3: Guest networkAll 3 LANs connect to separate downstream WIFI routers and I have cable running through the home to connect them to pfSense. The setup is
LAN1: connects to Lan port of WiFi router with DHCP disabled. PfSense provides the DHCP
LAN2: connects to WAN port of WIFI router with DHCP enabled
LAN3: connects to WAN port of WIFI router with DHCP enabledI have setup two Block rules on the Firewall for both LAN2 and LAN3 not to (a) have access to LAN1 devices and (b) not have access to the firewall web page.
All works fine but for some reason both LAN2 and LAN3 can access pfSense web page on 192.168.0.1 even though their subnets are totally different.
How can correct this and ensure that all 3 LANs remain separate? Any help would be appreciated!
-
@fireq said in How to separate 3 LANs on a quad-port NIC so they have no access to the other networks?:
All works fine but for some reason both LAN2 and LAN3 can access pfSense web page on 192.168.0.1 even though their subnets are totally different.
Don't know, which interface this IP is assigned to, you didn't mention.
However, assuming you're using RFC1918 subnets only internally, just create an alias (Firewall > Aliases) of type IP, networks and add all RFC1918 network ranges to it.
Then add a block rule to the top of each interface rule set with this alias as destination and protocol = any.
So that will block any access to RFC1918 IPs.If you use pfSense for DNS resolution you have to allow this access by a separate rule. So add a pass rule allowing DNS access to "this firewall" and put it above the block rule.
You may also handling the desired behavior with floating rules if you are familiar with it.
-
@fireq said in How to separate 3 LANs on a quad-port NIC so they have no access to the other networks?:
LAN2: connects to WAN port of WIFI router with DHCP enabled
LAN3: connects to WAN port of WIFI router with DHCP enabledWhy would you do that?
-
@viragomann Thanks for your quick reply. The 192.168.0.1 is on the LAN1 So I setup the following Floating rule:
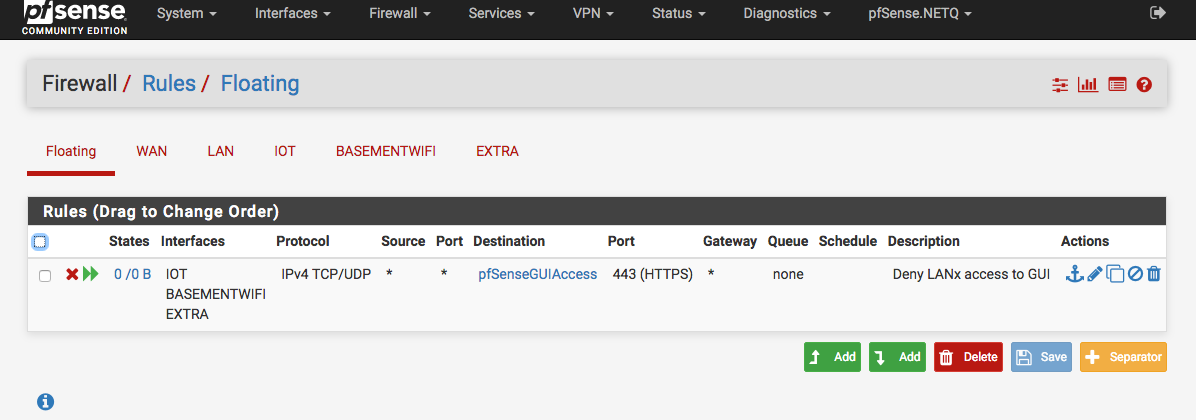
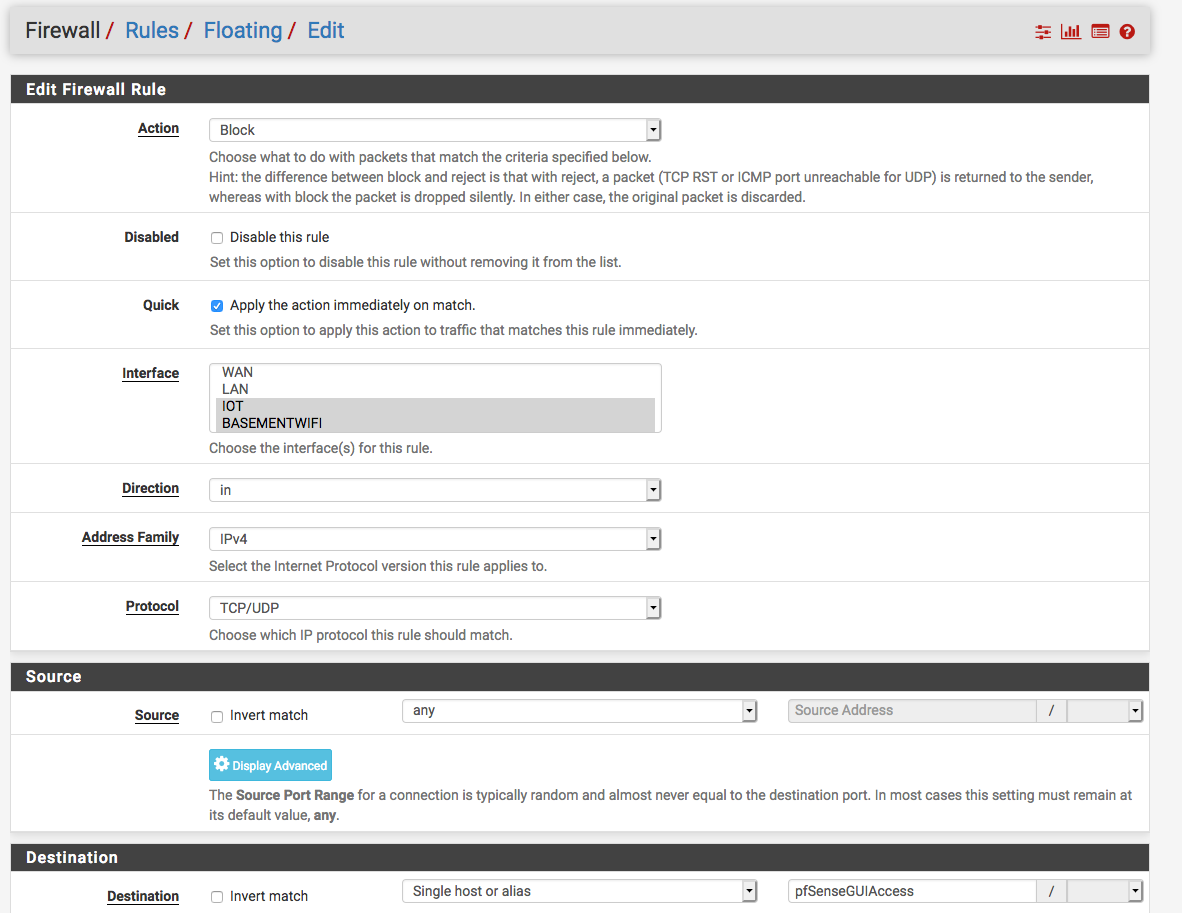
and for the separate LANs have the following rules:
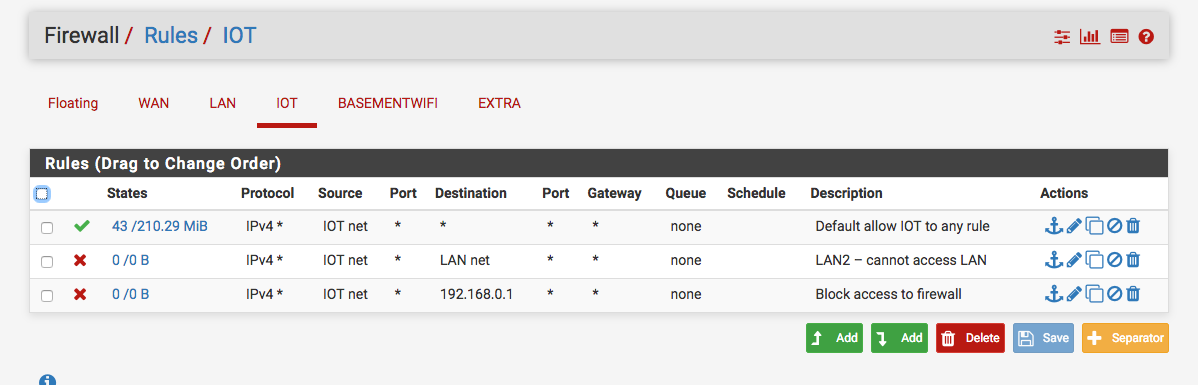
Do these seem right?
-
@johnpoz I thought that would provide an extra layer to keep the networks separate and I don't care too much about the bandwidth on the IOT and Guest networks. Would it be better to just disable DHCP on all downstream routers?
-
Yeah it gives you more insight and control into what is on your network, and what they are doing.
Why would you hide stuff behind another nat on your own network?
-
@johnpoz I don't want guests or the IOT devices with weak security to be able to access my main LAN or the firewall.
-
Just create block rules on the network you want to isolate.
-
What does that have to do with downstream nat.. Unless you have the rules inplace on your firewall to stop access they would still be able to access your lan.. Unless you were using the same network as what is behind your routers?
Not sure what good removing your insight and control of stuff on your network - if the goal is blocking access.. Which is as simple 1 firewall rule..
-
@fireq
It may be more reliable to use the preset "this firewall" alias for blocking access to pfSense itselft then creating your own alias. -
@johnpoz thanks john. am still learning so obviously making mistakes but the feedback is helpful
-
@viragomann thanks, I tried that first but still had access to the gui so changed to the specific IP.
-
@fireq said in How to separate 3 LANs on a quad-port NIC so they have no access to the other networks?:
I tried that first but still had access to the gui
Keep in mind that just because you create a block rule doesn't mean there isn't an existing state that is allowing the traffic.
When you go to block something - you need to make sure there is no existing state that is allowing.
The "this firewall" is the best way to block access to the firewall for vlans you don't want to be able to access stuff on the firewall you don't want.. because it also includes the wan IP which is quite often public. So would not be included in any rfc1918 alias you use..
Here is a example set of rules for a locked down vlan..
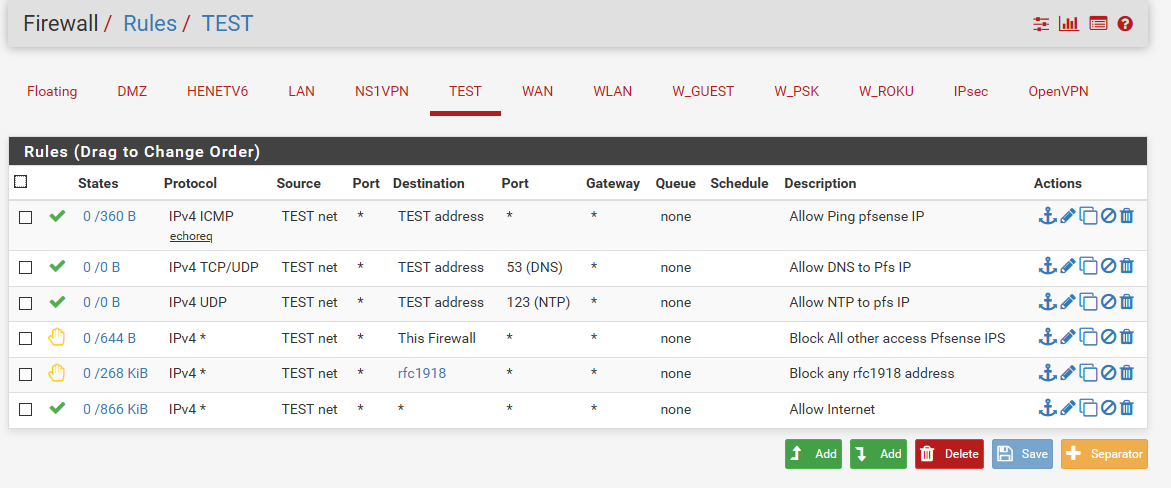
Can be modified for your wants/needs. It allows this vlan to ping pfsense IP on that vlan - for connectivity testing. It allows access to dns and ntp.. But then all other access to any other vlan or any firewall IP is rejected. Rejected can help with letting the client know - you ain't getting there... So no need to keep trying via retrans, etc. This can be helpful on local networks - would never do on wan.
Then it allows everything else, ie the internet.
-
@johnpoz great! thanks for the explanation. will use that example and modify for my setup.