How to separate 3 LANs on a quad-port NIC so they have no access to the other networks?
-
@johnpoz I thought that would provide an extra layer to keep the networks separate and I don't care too much about the bandwidth on the IOT and Guest networks. Would it be better to just disable DHCP on all downstream routers?
-
Yeah it gives you more insight and control into what is on your network, and what they are doing.
Why would you hide stuff behind another nat on your own network?
-
@johnpoz I don't want guests or the IOT devices with weak security to be able to access my main LAN or the firewall.
-
Just create block rules on the network you want to isolate.
-
What does that have to do with downstream nat.. Unless you have the rules inplace on your firewall to stop access they would still be able to access your lan.. Unless you were using the same network as what is behind your routers?
Not sure what good removing your insight and control of stuff on your network - if the goal is blocking access.. Which is as simple 1 firewall rule..
-
@fireq
It may be more reliable to use the preset "this firewall" alias for blocking access to pfSense itselft then creating your own alias. -
@johnpoz thanks john. am still learning so obviously making mistakes but the feedback is helpful
-
@viragomann thanks, I tried that first but still had access to the gui so changed to the specific IP.
-
@fireq said in How to separate 3 LANs on a quad-port NIC so they have no access to the other networks?:
I tried that first but still had access to the gui
Keep in mind that just because you create a block rule doesn't mean there isn't an existing state that is allowing the traffic.
When you go to block something - you need to make sure there is no existing state that is allowing.
The "this firewall" is the best way to block access to the firewall for vlans you don't want to be able to access stuff on the firewall you don't want.. because it also includes the wan IP which is quite often public. So would not be included in any rfc1918 alias you use..
Here is a example set of rules for a locked down vlan..
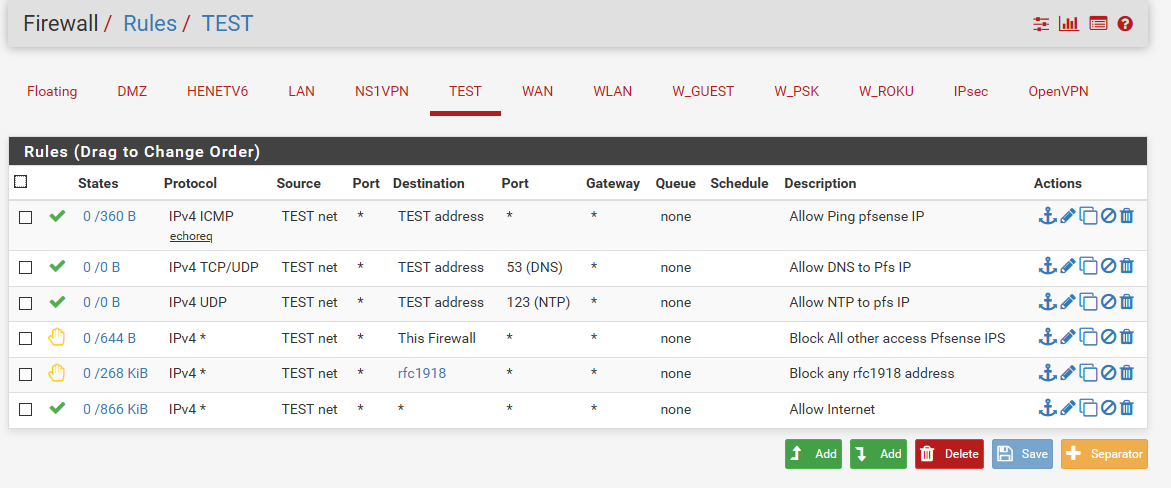
Can be modified for your wants/needs. It allows this vlan to ping pfsense IP on that vlan - for connectivity testing. It allows access to dns and ntp.. But then all other access to any other vlan or any firewall IP is rejected. Rejected can help with letting the client know - you ain't getting there... So no need to keep trying via retrans, etc. This can be helpful on local networks - would never do on wan.
Then it allows everything else, ie the internet.
-
@johnpoz great! thanks for the explanation. will use that example and modify for my setup.