Need help with my VLAN firewall rules to make sure they do what I think they do
-
@johnpoz Just go after some list they host somewhere on pi-hole.net.
-
@johnpoz
Did you find the git PR that shows the cookie issue ?
I had a brief look , but didn't find any./Bingo
-
Ahh think it's this one
(Win SRV 2008R2) , that is even out of support ... Grrrrr
https://github.com/pi-hole/pi-hole/issues/3578That leads to this one
https://github.com/pi-hole/pi-hole/issues/3595That even contains
Try with dig +nocookie -t txt versions.pi-hole.netSigh .... Redmond again

-
Yeah and it was with 2008r2 that is DEAD... full end of life was jan 2020, so why would they be doing something to work around an issue with that in july of 2020?
All seems a bit stupid to me..
-
-
@imthenachoman
Yes .. We're talking about pi-hole , and DNS blocking.
And that pi-hole won't update if you block DNS to anything but the pfSense. -
@bingo600 I see. Interesting. Thanks!
-
I just got a new update for my pihole, i suppose you ought to see it too
This time i tried
PIHOLE_SKIP_OS_CHECK=true sudo -E pihole -rSelected repair , and the update went through wo. opening for ns1
But damm annoying


-
Looks like an update to FTL.. lets see what happens.. I have these rules in place..
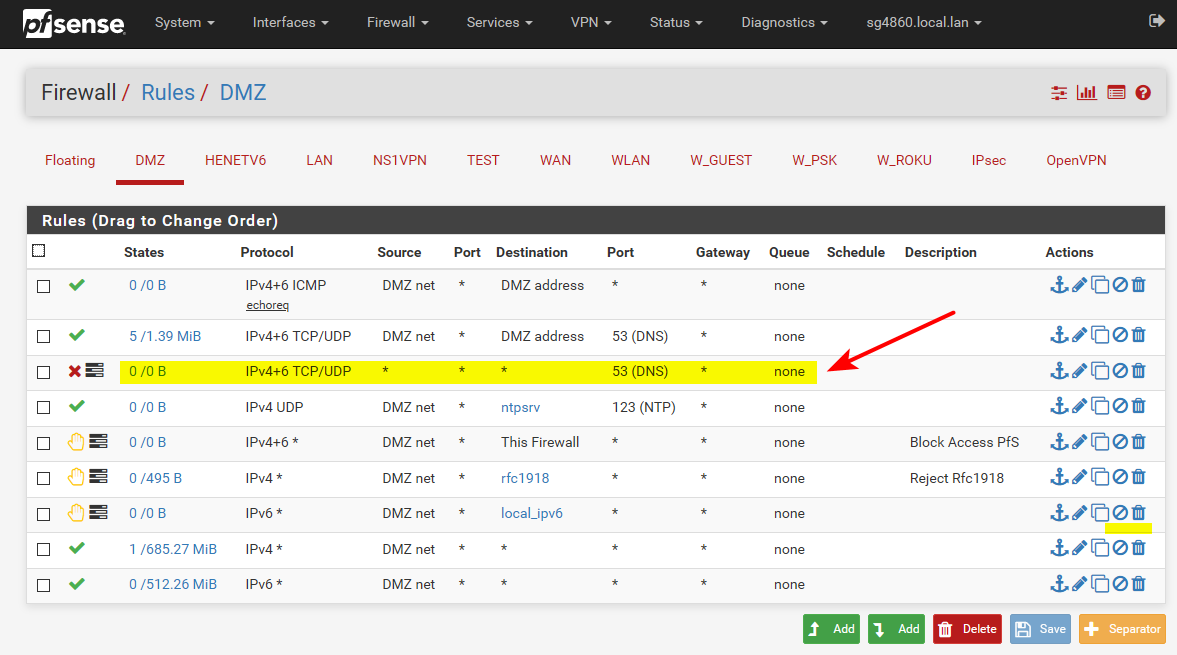
For the vlan that my pihole sits on..
Yeah this is nonsense...
[✗] Retrieval of supported OS list failed. dig failed with return code 9. Unable to determine if the detected OS (Raspbian 10) is supported Possible causes for this include: - Firewall blocking certain DNS lookups from Pi-hole device - ns1.pi-hole.net being blocked (required to obtain TXT record from versions.pi-hole.net containing supported operating systems) - Other internet connectivity issuesThis is zero issue with grabbing that info.. Other that you forcing a direct query to ns1.. Gawd this just pisses me off that they do nonsense like this.. Arrrghh.. Why are people so freaking stupid?????
root@pi-hole:/home/pi# dig versions.pi-hole.net txt ; <<>> DiG 9.11.5-P4-5.1+deb10u2-Raspbian <<>> versions.pi-hole.net txt ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 16772 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;versions.pi-hole.net. IN TXT ;; ANSWER SECTION: versions.pi-hole.net. 3600 IN TXT "Raspbian=9,10 Ubuntu=16,18,20 Debian=9,10 Fedora=31,32 CentOS=7,8" ;; Query time: 356 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Sat Dec 26 19:21:24 CST 2020 ;; MSG SIZE rcvd: 127 root@pi-hole:/home/pi#So they fixed working with some antiquated dns windows server 2008??? That is EOL!!! By just bypassing it. To break everyone else that would be filtering dns other than their own.. Ie pretty much every pihole user on the planet ;) This is just some of the stupidest shit ever.. WTF!!!
While I am a fan of pihole - this is just borked.. Same goes with some of the nonsense they are trying to do with dnssec.. If your going to forward, dnssec is pointless - he doesn't get that either.. Maybe we should fork their code ;)
-
@johnpoz said in Need help with my VLAN firewall rules to make sure they do what I think they do:
While I am a fan of pihole - this is just borked..
Totally agree .. Fix for an old outdated OS , and "bork" everyone else.
Same goes with some of the nonsense they are trying to do with dnssec.. If your going to forward, dnssec is pointless - he doesn't get that either..
I thought they wouldn't touch DoH at all as "PH is not a security product"
Maybe we should fork their code ;)
He..He
Intriquing , but i doubt i have time for that./Bingo