How to implement Static Routing with Dual Layer Firewalls?
-
Welcome All,
Although I have a lot of experience with computers, networking with static routes through devices I am fairly weak with. Due to requirements, there are two firewalls in use, an outer and an inner. Static routes are to be used. I do have the understanding of placing a signal static route through one firewall, but not with two, along with a DMZ.Using example IPs:
IP from the Outside: 100.100.100.99
IP for Internal Network Switch: 192.168.1.72
A Server separate from the Switch: 172.20.1.2Outer Firewall:
WAN (Facing to Outside): 100.100.100.100
LAN (Facing to Inner FW): 10.10.10.1Inner Firewall:
WAN (Facing the Outer FW LAN): 10.10.10.2
LAN1 (Facing the internal Network): 192.168.1.73
LAN2 (Facing the internal Server): 172.20.1.1DMZ:
IP: 10.10.10.3Thus:
- The route would be from the Outside IP to the Outer Firewall WAN,
- Which goes to the Outer Firewall LAN, which goes to both the DMZ and Inner Firewall WAN
- With the Inner Firewall, uses both LAN1 and LAN2:
--- LAN1 to the Network Switch
--- LAN2 to the Internal Server - And of course reverse direction
Normally, with just one firewall and the network switch, would be to disable NAT and then apply the Static Route from the WAN and LAN sides, but I am not certain how to does in such a complex manner as above.
-
On your outer firewall define your routes for your inner firewall subnets pointing to 10.10.10.2
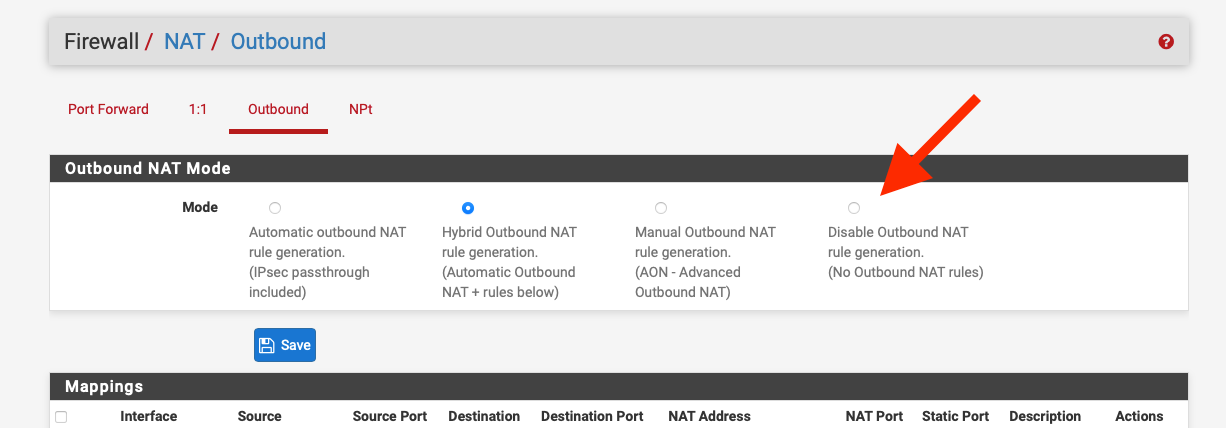
On your inner firewall disable outbound nat and set the default route to 10.10.10.1
If you're feeling brave install ffr and set up OSPF between the two devices, this would be preferable if there are loads of subnets behind your inner firewall.
-
@nogbadthebad
Thanks for the reply and insight.
Question, would the Outter FW have its NAT disabled as well?
Will put this into tests on Monday and post of the outcomes. -
If the outer firewall connects to the internet it would need to NAT local addresses.