VLANs blocked by Firewall
-
@cburbs Yes, the static address is outside the range. Resetting to default values did not change the results.
-
Normally, with these :
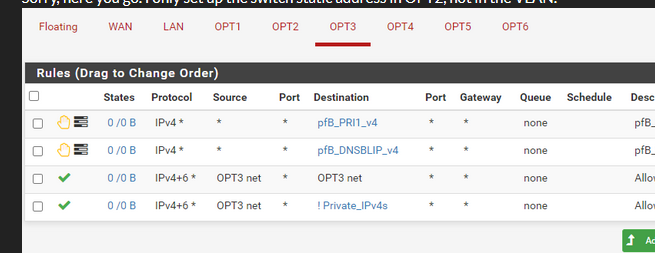
Traffic can enter OPT3.
Before the final, hidden "drop all" (non-vsible) there is a another hidden rule that let DHCP traffic (UDP, port 67 and ...) come in.
So, what ever happens, DHCP should work. But you can see it work.
Place an pass rule at the top with proto is UDP and port = 67.
Do not use "OPT3 net" as a source, as DHCP traffic is mostly broadcast = 0.0.0.0What you should see now is that these :
should start to count.
If not : check the NIC, cable, switch and the most obvious one : VLAN settings.
Btw : when issues, go check the real firewall.
It's here, a file : /tmp/rules.debug -
Some of this stuff has already been mentioned, but the rules on OPT3 have zero hits. So there are multiple areas to look at.
My suggestion:
- Put an any/any rule at the top of OPT3 and disable everything else until basic IP communication is established.
- Remove VLAN1 from g8 on the switch
- Remove the 10.70.0.0/24 subnet from OPT2 and leave it undefined
- Bounce the DHCP server on OPT3
- Reboot the PC connected to g1 or g2
After the above, provided the switch is configured properly... everything should be passed and working as expected.
A cleanup item once you get everything working... remove that OPT3 net/OPT3 net rule... it's doing absolutely nothing.
-
@marvosa
Hi,
The switch loses connectivity when VLAN1 is removed from g8, tried it before.
Also, upon rebooting the router, there is a brief connection through VLAN10. Only lasts a couple of seconds though. Logs below -DHCP Leases

DHCP Log
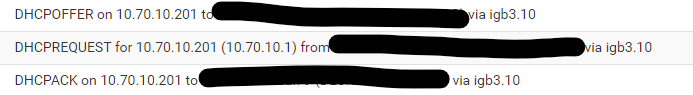
Then it drops,
Firewall log

-
Also, upon rebooting the router, there is a brief connection through VLAN10. Only lasts a couple of seconds though. Logs below -
Sounds like traffic may be passing until the rules get loaded. Did you add the any/any rule?
-
@marvosa
I did. That's the only rule in OPT3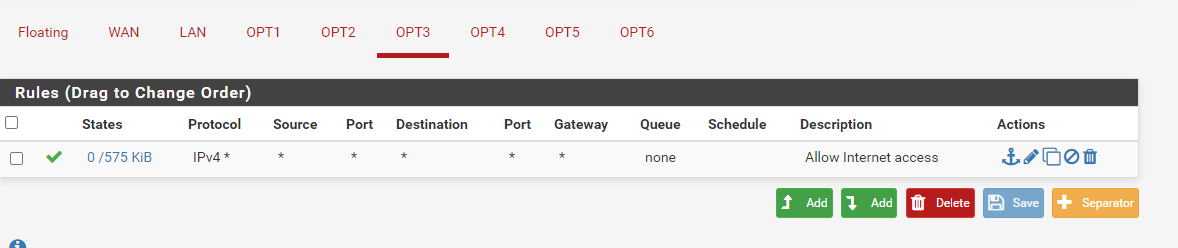
-
This setup is on igb3 correct?
Have you tried to get a vlan going correctly on igb0 instead - maybe something flaky going on with igb3.
I just came across this so maybe look into this - https://community.netgear.com/t5/Managed-Switches/GS110TP-won-t-retain-VLAN-membership-on-port-8/td-p/1446089
See if that is set for port mirroring.
Or I guess just try port 7 as your trunk/tagged port and see what happens as well.
-
I agree. The usual suspects are typically... something's not configured properly, not plugged in properly, or not function properly.
Not seeing anything glaring in the configs, so I'd start trying things like...different ports on the switch, different cables, try moving the VLANs to a different NIC, try a different switch, etc.
I've also read a few posts where after trying everything... people have reset PFsense to factory default, re-built their config from scratch and everything somehow magically starts working.
-
-
@r801248 said in VLANs blocked by Firewall:
I guess I'll go that route and reset and reconfigure the box.
Thanks,
Look at the last thing I posted to see if you see anything odd with port 8 -
Try port 7 before you do a reconfigure as your trunk port just to see.
Then maybe reconfigure.
-
@cburbs
There's no port mirroring, but I'll try 7 as you suggested.Thanks,
-
@r801248 Status update?
-
It did not work on port 7 either. I will reset pfSense to factory defaults over the weekend as the wife works from home and we need the connection.
Thanks,
-
@r801248 any update on this?