Forwarding traffic from a LAN IP to another LAN IP
-
@draand28
You'd better done that with hostnames from the beginning.@draand28 said in Forwarding traffic from a LAN IP to another LAN IP:
I also could've changed the IP of the new server, but it will interfere with some other hardcoded pieces of software that have the new IP registered in them.
Does that mean, that the old IP 192.168.1.228 is still in use by a device?
-
You are right, it would have been way easier to work with hostnames, but now it's too late for that.
Yes, the old 192.168.1.228 IP is still in use.
I just need a redirecting rule or something for internal traffic that wants to connect to the old IP on 8080, to the new IP, also on 8080.
-
@draand28
For redirecting the traffic, it has to be sent to pfSense at first. So this will only work if client and server are connected to different interfaces on pfSense. If this is the case, you can forward it by a simple NAT rule. -
Unfortunately, this is not the case. They are all on the same interface. Although, I have an extra PCIe x1 gigabit network card that I may be able connect to the pfsense machine, then connect the Wi-Fi Access point to it. (the IoT devices are connected via Wi-fi).
Would this setup work for sure? I need to decide as soon as possible what I'll do (either establish this new LAN interface for Wi-fi only or change the IP of the old server and the new one and try to change all the IP binds of the new server).
-
@draand28
Yes, as I said, if clients and the servers are on different interfaces you can simply NAT the traffic.If they are all on the same interface there may be two dirty solutions though. Either add the old IP to pfSense and change it at the server and forward all traffic destined to it, the 8080 to the one server, other traffic to the other one, or configure the forwarding on the device which owns that IP.
Consider that forwarding within the same subnet only works in conjunction with masquerading, i.e. translating the soure IP into that one of the forwarding device.
-
@draand28 said in Forwarding traffic from a LAN IP to another LAN IP:
Hello,
I have migrated my Blynk server to another phsyical server (with another IP address) and I'm trying to create a NAT rule that will redirect all internal traffic that points at 192.168.1.228:8080 to 192.168.1.240:8080. Both of these IPs are internal IPs, of course.
I could've replaced the IP of the new server in the source code of the IoT devices that are required to connect to the Blynk server, but I no longer have the original code and the one I tried to redo is a little buggy.
If you programmed those devices your self (ESP8266 ?) , chances are that you haven't set the protection bit on the device MCU.
You could try to read out the MCU firmware , and (binary/hexedit) patch the IP : 192.168.1.228 to 192.168.1.240.
Then program the firmware back.Else you have to do as @viragomann said.
Make sure your IOT devices and the server are on separate networks (Lan's), in order to get NAT to work/Bingo
-
I have added a second NIC, assigned it as OPT1, assigned a new subnet for it (192.168.0.1/24), Configured DHCP ipv4 for it (192.168.0.100 to 192.168.1.199) and it doesn't seem to work (any device that I connect to the new OPT1 interface doesn't have an IP assigned nor does it connect to 192.168.0.1 (pfsense webGUI for that subnet)).
I have NAT/Outbout set to Hybrid (the new subnet is already set in Automatic rules).
Config for OPT1:
IPv4: Static IPv4
IPv6: None (I set it to none because I can't use Track interface as I do in LAN, as it is already assigned to WAN prefix).
Ipv4 Address: 192.168.0.1/24DHCP OPT1 config:
Enable: tick
Range: 192.168.0.100-192.168.0.199
Gateway: 192.168.0.1I hope this is not too offtopic.
Edit: Yes, it is a ESP8266 module, but I went too far at this point to get back to the binary/hexedit patch method.
-
1: You dont have your IOT devices static mapped in the "old" dhcp do you ?
2: Solve the DHCP issue , maybe use a PC on the OPT1 to debug , and see if you get dhcp at all.
3: When DHCP is solved and your devices gets ip's , do some checks from the pc to the IOT server , so ensure the nat works.
4: restart your IOT devices to get a new address.
I do hope the ESP's are using DHCP and not static ip's , else you're FSCK'ed.
-
@draand28 said in Forwarding traffic from a LAN IP to another LAN IP:
I have added a second NIC, assigned it as OPT1, assigned a new subnet for it (192.168.0.1/24), Configured DHCP ipv4 for it (192.168.0.100 to 192.168.1.199) and it doesn't seem to work
Did you split your LAN subnet or simply add another DHCP range to it?
-
@bingo600 1. No, they are not static mapped for sure (they are just connecting to the said SSID + pass and request an IP from the DHCP server)
2. DHCP now works on OPT1 (second subnet) after disabling IPv6 on OPT1, but it has no internet connection.
Also, 192.168.0.1 (IP address for pfsense webgui for this subnet, the gateway) isn't accesible. - connection timeout.For some reason when I connect my windows laptop to LAN (via a switch) DHCP doesn't work, I always get the following address: 169.254.225.232 (but my ubuntu servers connected on the same subnet work fine). I tried enable/disable NIC for the windows laptop and a restart but it didn't help.
Edit: After a restart of pfsense, I am now able to connect with my windows laptop to the original subnet 192.168.1.1 (LAN, not OPT1).@viragomann I added another DHCP range to it (with a new subnet, 192.168.0.1, the old LAN subnet being 192.168.1.1)
Edit 2: After the reboot something weird happens, all devices from the OPT1 interface now have DHCP leases, I can see them in the firewall log requesting different connections, but still no Internet access.
-
@draand28 said in Forwarding traffic from a LAN IP to another LAN IP:
- DHCP now works on OPT1 (second subnet) after disabling IPv6 on OPT1, but it has no internet connection.
Outbound NAT should have been added automatically if you have "Hybrid"
Have you allowed internet access via a firewall rule on OPT1 (new interface)Also, 192.168.0.1 (IP address for pfsense webgui for this subnet, the gateway) isn't accesible. - connection timeout.
Only LAN has an automatic rule to allow WebGui access (80/443/22)
You have to add that rule manually to other interfaces -
@bingo600
Ok, I have added internet access and pfsense access for the 2nd subnet, everything works fine. ESP boards are now requesting to connect to 192.168.1.228 (the blynk server).What are the exact settings that I need for the NAT rule to forward all traffic from 192.168.0.1XX:8080 to 192.168.1.240:8080?
So far I tried (but it didn't work):
Interface: OPT1
Protocol: TCP/UDP
Source: any, port 8080
Destination: any
Destination port range: 8080
Redirect target ip: 192.168.1.240
Redirect target port: 8080
NAT reflection: Enable (Pure NAT)
Filter rule: Rule NAT -
@draand28 said in Forwarding traffic from a LAN IP to another LAN IP:
@bingo600
Ok, I have added internet access and pfsense access for the 2nd subnet, everything works fine. ESP boards are now requesting to connect to 192.168.1.228 (the blynk server).What are the exact settings that I need for the NAT rule to forward all traffic from 192.168.0.1XX:8080 to 192.168.1.240:8080?
So far I tried (but it didn't work):
Interface: OPT1
Protocol: TCP/UDP
Source: any, port 8080
Destination: any
Destination port range: 8080
Redirect target ip: 192.168.1.240
Redirect target port: 8080
NAT reflection: Enable (Pure NAT)
Filter rule: Rule NATAre you using portforward or outbound nat or ?
I'm not a pfSense NAT guru , only using portforward at home
But i'd change destination from any to 192.168.1.228
And drop reflection -
You might be able to do it with a port forward too, if only port 8080 is interesting.
But NAT is a better way , as that means all requests would be xlated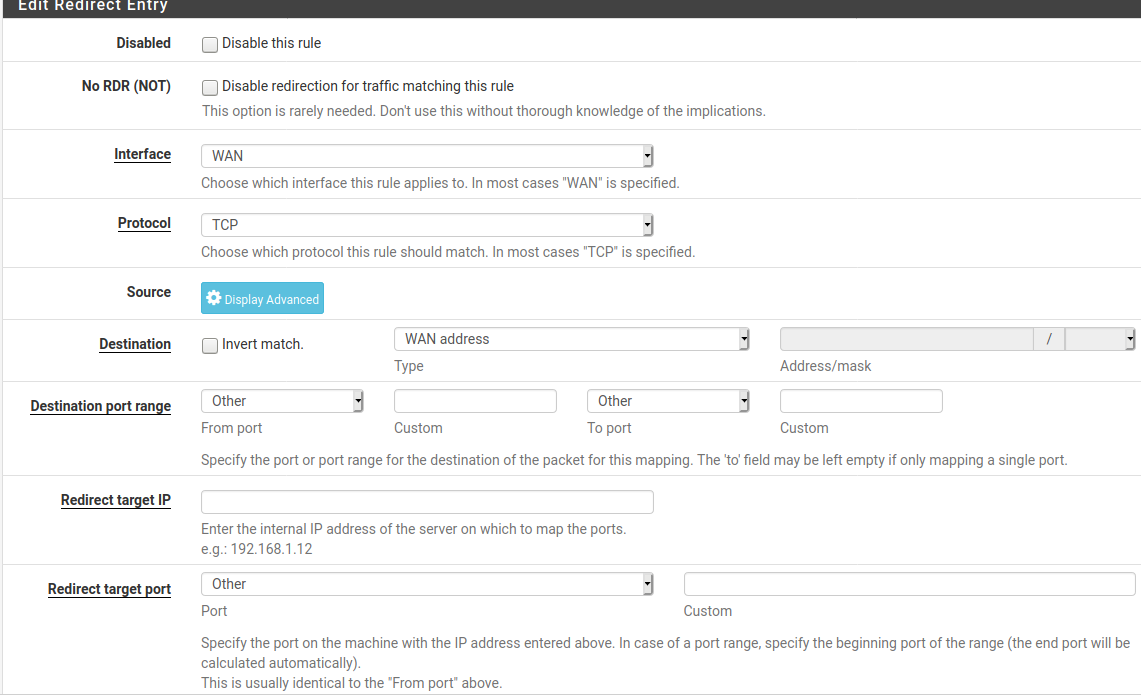
Interface OPT1
Proto TCP
Source -- Leave alone
Dest - Single host or alias = 192.168.1.228
Dest port range = 8080
Redirect target ip = 192.168.1.240
Redirect port - Other = 8080Leave rest as is
-
@bingo600
Yes, I was trying with Port Forwarding.Thanks for the tip. Everything is in order now - after I changed the settings to your example (ESPs started appearing in blynk app, also the connection works both ways (I can send instructions to the ESPs)).
My issue is finally solved! Thank you both for the fast answers.
-
