site to site vpn configuration between pfsense and cisco asa 5505
-
Given it's a task from work, I suspect they want you to do it as part of your training.
-
@jknott in same lan we can able to connect site to site VPN
-
I assume that means you can't connect between 2 sites. If so, then you have to check routing, firewall rules and perhaps NAT.
-
hostname ciscoasa enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted names ! interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 ! interface Ethernet0/2 shutdown ! interface Ethernet0/3 shutdown ! interface Ethernet0/4 shutdown ! interface Ethernet0/5 shutdown ! interface Ethernet0/6 shutdown ! interface Ethernet0/7 shutdown ! interface Vlan1 nameif inside security-level 100 ip address 192.168.30.150 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 192.168.10.150 255.255.255.0 ! ftp mode passive object network obj_any subnet 0.0.0.0 0.0.0.0 access-list outside_cryptomap_10 remark ACL to encrypt traffic from ASA to pfSense access-list outside_cryptomap_10 extended permit ip 192.168.30.0 255.255.255.0 192.168.20.0 255.255.255.0 pager lines 24 mtu inside 1500 mtu outside 1500 icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 ! object network obj_any nat (inside,outside) dynamic interface route outside 0.0.0.0 0.0.0.0 192.168.10.1 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 dynamic-access-policy-record DfltAccessPolicy user-identity default-domain LOCAL no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart crypto ipsec ikev1 transform-set pfSense-AES128SHA esp-aes esp-sha-hmac crypto map outside_map 10 match address outside_cryptomap_10 crypto map outside_map 10 set peer 192.168.10.175 crypto map outside_map 10 set ikev1 transform-set pfSense-AES128SHA crypto map outside_map interface outside crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes hash sha group 2 lifetime 86400 telnet timeout 5 ssh timeout 5 console timeout 0 threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept tunnel-group 192.168.10.175 type ipsec-l2l tunnel-group 192.168.10.175 ipsec-attributes ikev1 pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect ip-options inspect netbios inspect rsh inspect rtsp inspect skinny inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp inspect icmp inspect icmp error ! service-policy global_policy global prompt hostname context no call-home reporting anonymous call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email callhome@cisco.com destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily Cryptochecksum:586fd287f3e8c0d4f3e908e02c40f88d : end -
@jknott im new to field so pls help me with this
-
First off, you have to decide whether you're using IPSec or OpenVPN VPN. You will have to allow whichever you use through the firewall.
Are you setting up a site to site VPN? Or "road warrior" VPN?
You will have to ensure appropriate routing.
Will the VPN terminate on the firewall or behind it? This will affect routing.So, sit down with a sheet of clean paper and sketch out what you want to do. Then you will be able to tackle the various issues in a coherent manner. Include port numbers on the sketch. For example the default for OpenVPN is UDP port 1149. Also include target addresses on the sketch, so you'll know how to configure routing. I also see you're using VLANs. Include those in the sketch.
Also, while I have worked with IPSec VPNs, I've only set up OpenVPN on pfsense.
-
So you are trying to connect the 192.168.20.X subnet to the 192.168.30.X subnet?
And have a common subnet of 192.168.10.X between the firewalls?
Something like?
{Subnet1 .20}---[pfSense]==={common WAN .10}===[ASA]---{Subnet2 .30}
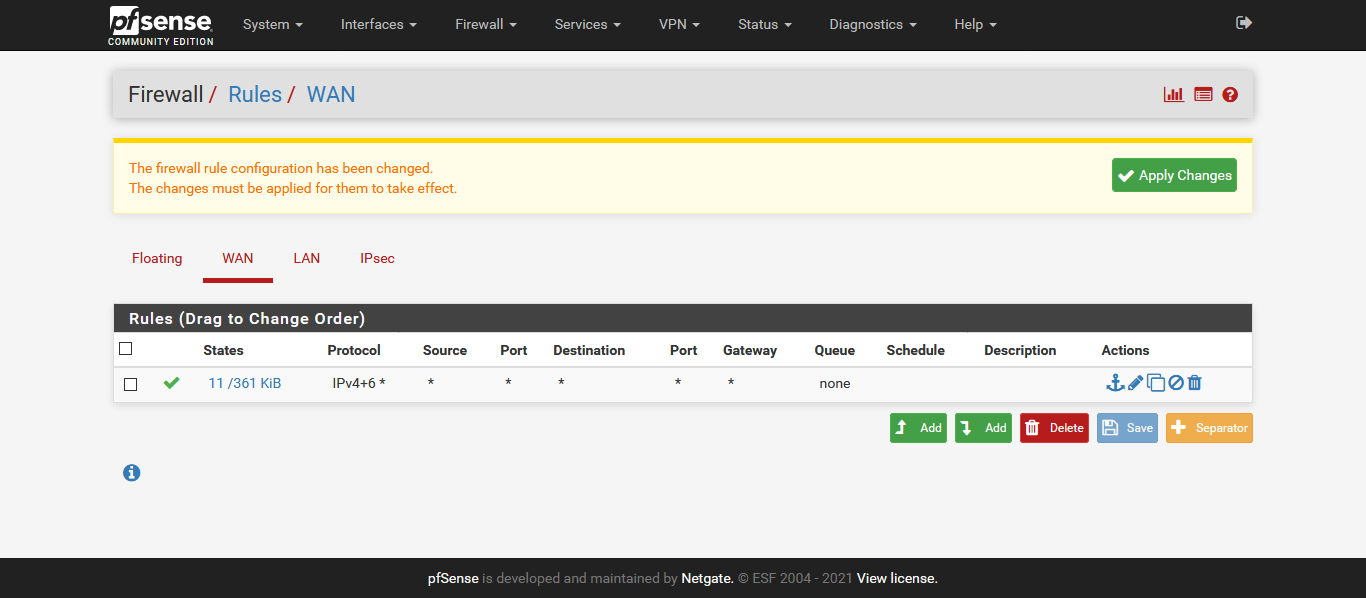
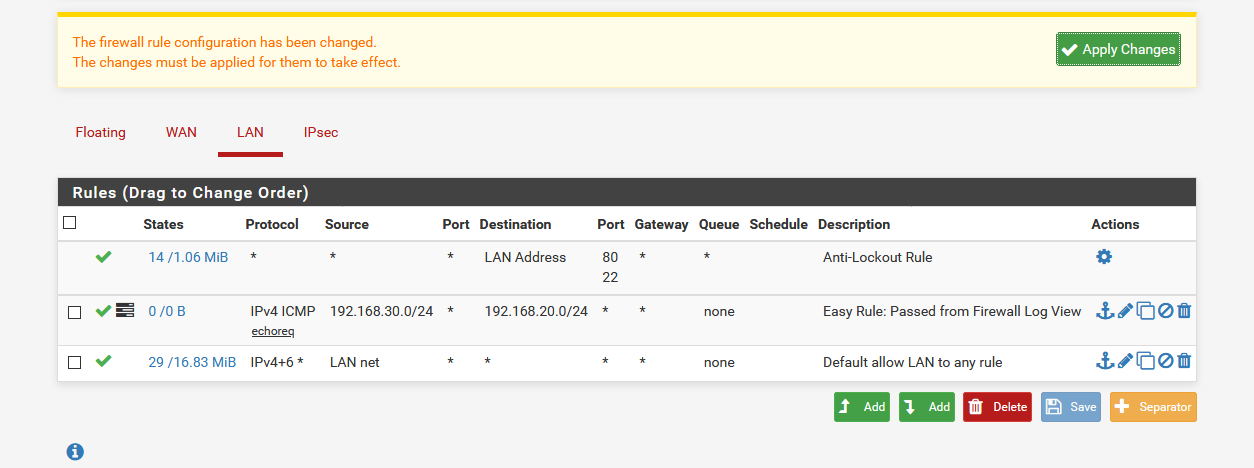
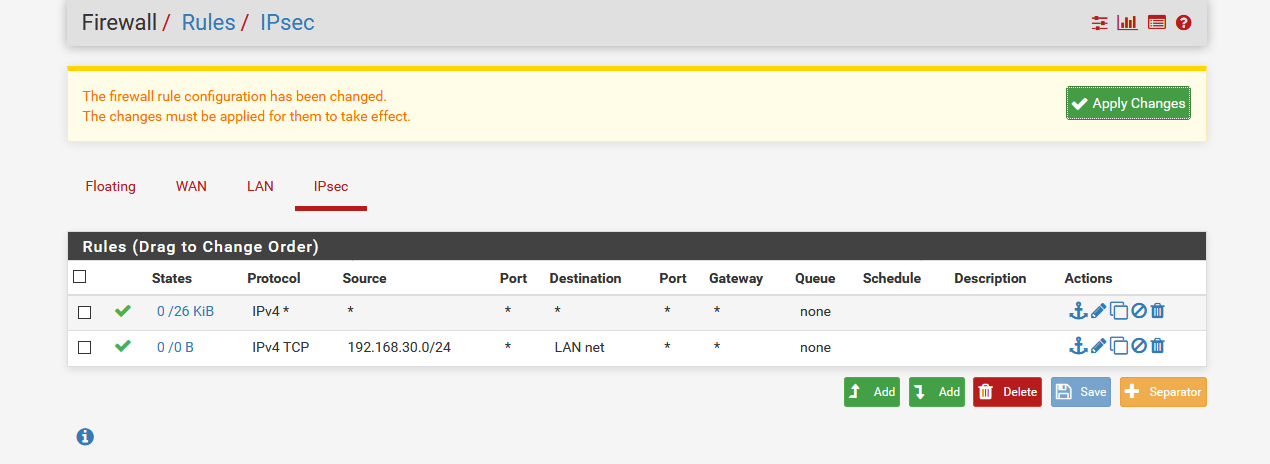
What is not working?
How is your IPSec configured in pfSense?
Do you see errors in the logs?
Steve
-
@stephenw10 I cant able to ping the local subnet but the connection was established between asa---pfsense ASA5505
-
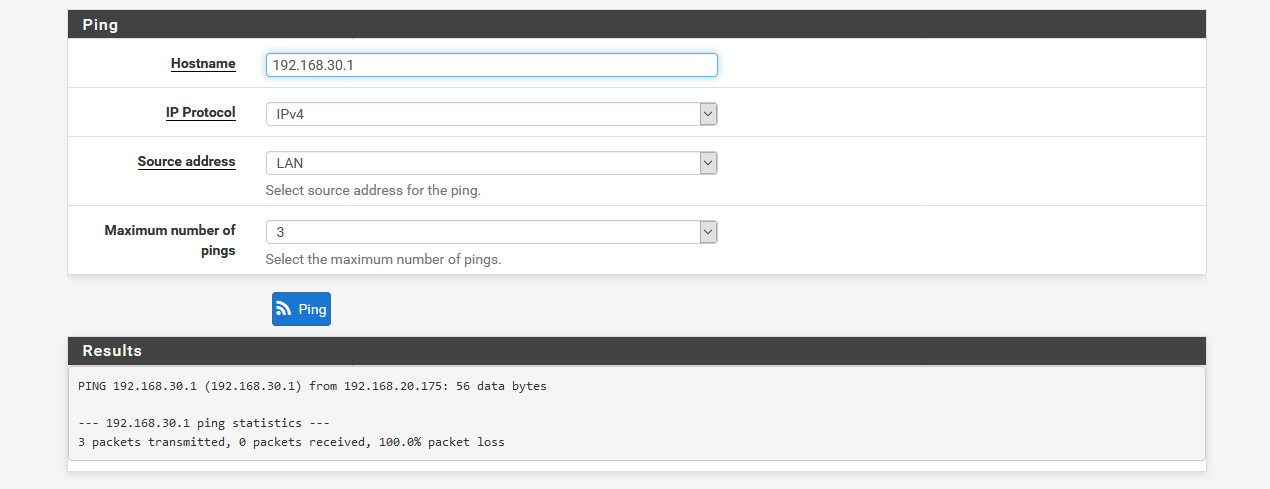
I can able to ping asa to pfsene but I can't able to ping pfsense to asa help pls
-
@jknott
I can able to ping asa to pfsene but I can't able to ping pfsense to asa help pls -
Sounds like a missing firewall rule at the ASA then.
Or you may be pinging from the wrong source in that direction. If you ping from pfSense directly be sure to select the LAN as the source.
Steve
-
-
Those don't help at all.
It's either a rule missing in the ASA.
Or you are pinging incorrectly without choosing LAN as source.
Post a screenshot of the ping failing.
Steve
-
-
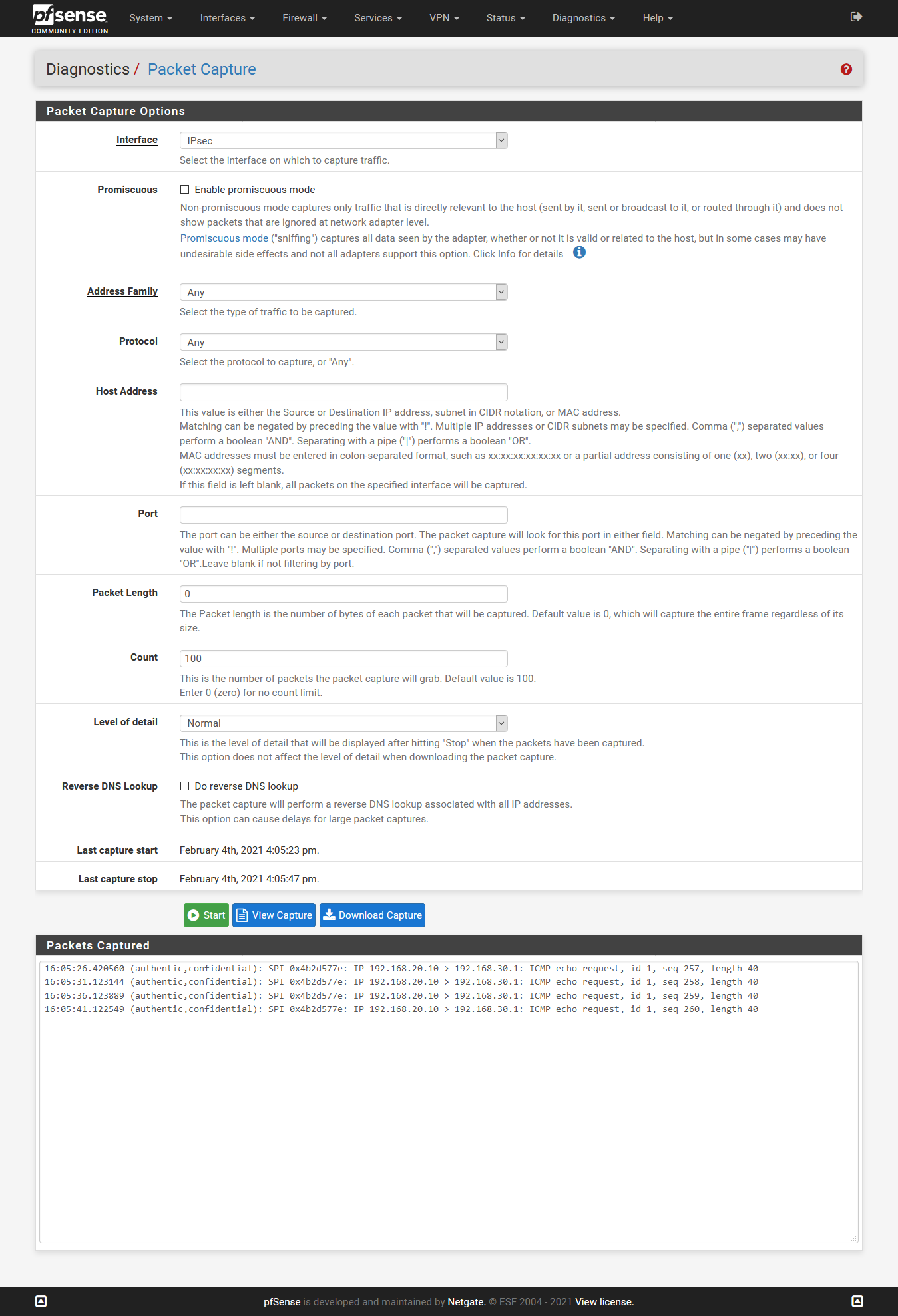
OK great. So that ping should match the ipsec policy and be carried.
If you run a packet capture on the ipsec interface you would see the requests leave.It looks like you are missing a rule on the other side to pass it.
Steve
-
@stephenw10
 .
.Below I have mentioned the cli of asa
ASA Version 8.4(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
switchport access VLAN 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.30.150 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 192.168.10.150 255.255.255.0
!
ftp mode passive
clock timezone GMT 0
object network NETWORK_OBJ_192.168.20.0_24
subnet 192.168.20.0 255.255.255.0
object network NETWORK_OBJ_192.168.30.0_24
subnet 192.168.30.0 255.255.255.0
object-group service DM_INLINE_SERVICE_1
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object icmp echo-reply
access-list outside_cryptomap_10 remark ACL to encrypt traffic from ASA to pfSense
access-list outside_cryptomap_10 extended permit ip 192.168.30.0 255.255.255.0 192.168.20.0 255.255.255.0
access-list outside-in extended permit ip any any
access-list outside_access_in remark icmp reply to vpn
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 host 192.168.30.0 host 192.168.20.0
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_2 192.168.30.0 255.255.255.0 192.168.20.0 255.255.255.0
access-list inside_access_in extended permit ip host 192.168.20.175 host 192.168.30.0
access-list global_access extended permit ip any any
access-list OUTSIDE_IN extended permit icmp any any echo-reply
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-731.bin
no asdm history enable
arp timeout 14400
nat (inside,outside) source static NETWORK_OBJ_192.168.30.0_24 NETWORK_OBJ_192.168.30.0_24 destination static NETWORK_OBJ_192.168.20.0_24 NETWORK_OBJ_192.168.20.0_24 no-proxy-arp route-lookup
!
nat (inside,outside) after-auto source dynamic NETWORK_OBJ_192.168.30.0_24 interface
access-group inside_access_in in interface inside
access-group OUTSIDE_IN in interface outside
access-group global_access global
route outside 0.0.0.0 0.0.0.0 192.168.10.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.30.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set pfSense esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto map outside_map 10 match address outside_cryptomap_10
crypto map outside_map 10 set peer 192.168.10.175
crypto map outside_map 10 set ikev1 transform-set pfSense
crypto map outside_map 10 set reverse-route
crypto map outside_map interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
username franco password rkfkSGltksT7dMZG encrypted
tunnel-group 192.168.10.175 type ipsec-l2l
tunnel-group 192.168.10.175 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:ad5e08543ca85592802a161b0b39c406
: end -
It could also be the host at 192.168.30.1 rejecting it.
You should use a non-default password on the ASA.

Steve
-
-
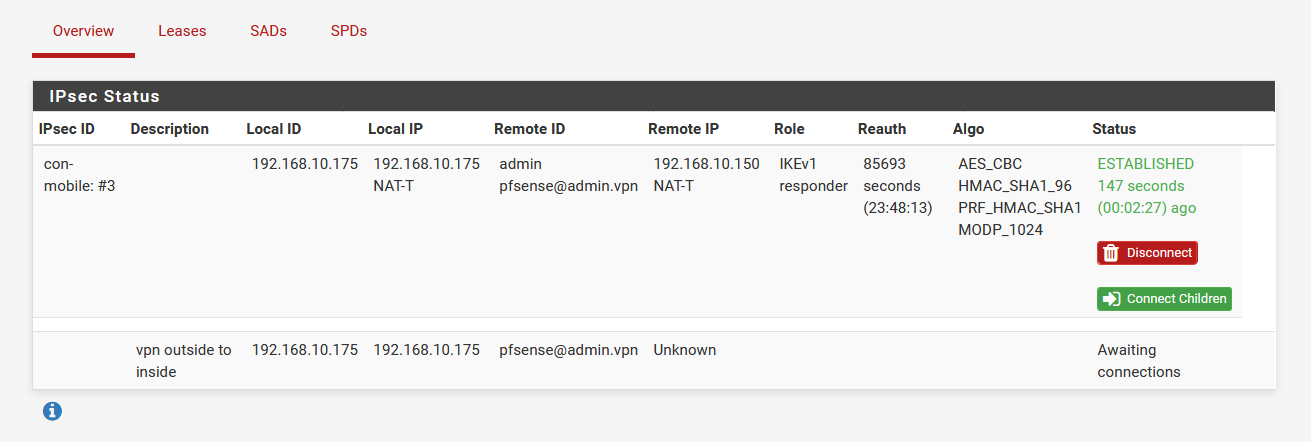
Ok, why is it configured as mobile IPSec? That's a site-to-site tunnel.
In that screenshot it is up at phase1 only. You need phase2 to be up to carry any traffic.
But you said you could ping from the ASA to pfSense so it must have been up then.What exactly are you showing us there?
Steve
-
@stephenw10 sorry bro i have completed the site to site VPN this was ipsec remote VPN config so you able to help with this plz..