1:1 NAT with IPSec
-
So 10.0.0.0/16 and 10.1.0.0/16 are both the Remote networks for different IPsec tunnels?
The tunnels would have to be configured to send traffic to arbitrary addresses (0.0.0.0/0) back though the tunnel for reply traffic to work correctly.
Your WAN rules need to pass traffic to 10.1.1.237 and 10.0.0.175, not the outside VIPs since NAT happens before firewall rules are checked.
-
@derelict said in 1:1 NAT with IPSec:
So 10.0.0.0/16 and 10.1.0.0/16 are both the Remote networks for different IPsec tunnels?
No.
10.0.0.0/16 is the local Office0 LAN network.
10.1.0.0/16 is the local Office1 LAN network.
Both are connected via single IPSec tunnel.
10.0.0.175 is local to Office0
10.1.1.237 is local to Office1 which means it is remote to Office0.The tunnels would have to be configured to send traffic to arbitrary addresses (0.0.0.0/0) back though the tunnel for reply traffic to work correctly.
I don't understand that. Could you please elaborate?
Your WAN rules need to pass traffic to 10.1.1.237 and 10.0.0.175, not the outside VIPs since NAT happens before firewall rules are checked.
I see. Thanks! -
@pvn So what does IPsec have to do with anything?
-
@derelict Office0 reaches 10.1.1.237 which is in Office1 LAN via the IPSec tunnel.
-
@pvn Going to need a diagram. I can't make sense of what you are saying.
-
@derelict Hope this will bring some clarity
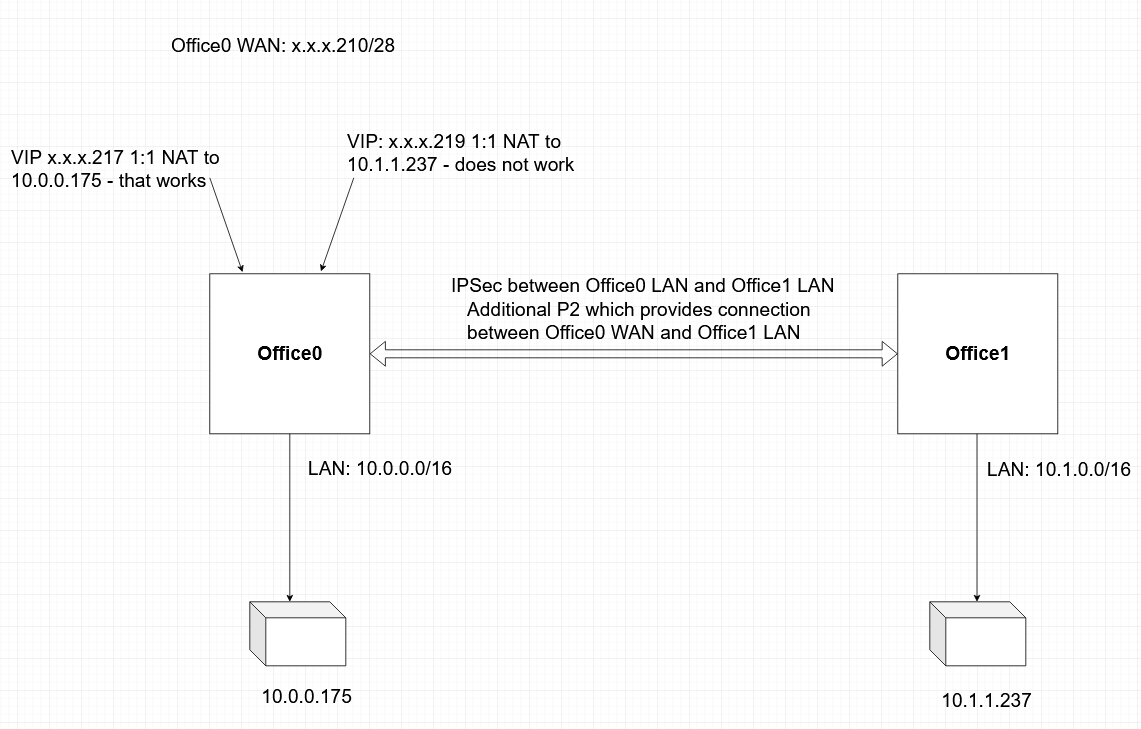
-
@pvn The IPsec tunnel will need a Phase 2 for all traffic:
0.0.0.0/0 <-> 10.1.0.0.16 or the reply traffic for the inbound connections will follow its routing table (go out WAN there).
OpenVPN is much more friendly to such NAT configurations.
A phase 2 for the WAN addresses does no good because the source address of the traffic is "any" " or "any address on the internet".
You could, perhaps, make a P2 like this on Office 0:
Local Network: 0.0.0.0/0
NAT Address: Any unused RFC1918 address, say 10.11.12.13/32
Remote Network: 10.1.0.0/16On Office 1:
Local Network: 10.1.0.0/16
Remote Network: 10.11.12.13/32That should work. The caveat would be you will lose all of the source addresses at Office 1 because all connections inbound will appear to come from source 10.11.12.13.
-
@derelict Genius! I never considered 0.0.0.0/0 as a Local Network in IPSec. That was the key!
Thank you very much. I learned something new. I owe you lunch!
-
@pvn That can have odd effects on the Office 1 side since all traffic will be interesting to IPsec.
-
@derelict Yep, we discovered that the hard way. I had to remove the P2 with 0.0.0.0/0.