pfsense and openvpn
-
It is the first time I setup openvpn on a Windows10 virtual machine on azure, working as server (the openvpn). If I put all the files in the right folder on my pc, I can connect to the vpn. So that is working oke.
But I want to setup my pfsense as openvpn client as well.
I followed some manuals, but I do not seem to be able to get it connected.
Last errors are:
MANAGEMENT: Client connected from /var/etc/openvpn/client3.sock
Feb 3 21:34:07 openvpn 91653 TLS Warning: no data channel send key available: [key#0 state=S_PRE_START id=0 sid=00000000 00000000] [key#1 state=S_UNDEF id=0 sid=00000000 00000000] [key#2 state=S_UNDEF id=0 sid=00000000 00000000]Can anyone help me out with this, please?
-
@nick-loenders seems connected partially??
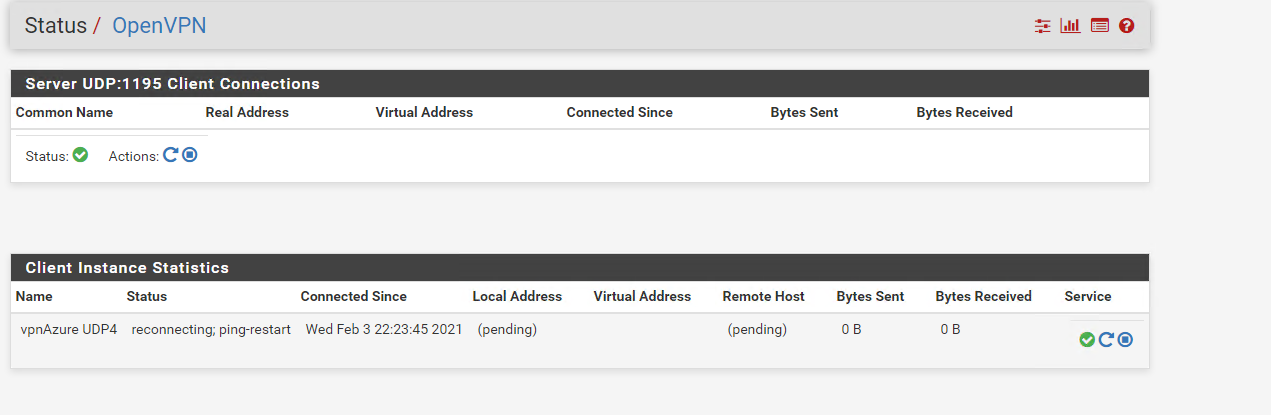
-
@nick-loenders this is i nthe log on the server:
Wed Feb 03 22:48:58 2021 OpenVPN 2.4.8 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Oct 31 2019
Wed Feb 03 22:48:58 2021 Windows version 6.2 (Windows 8 or greater) 64bit
Wed Feb 03 22:48:58 2021 library versions: OpenSSL 1.1.0l 10 Sep 2019, LZO 2.10
Wed Feb 03 22:48:58 2021 Diffie-Hellman initialized with 2048 bit key
Wed Feb 03 22:48:58 2021 Failed to extract curve from certificate (UNDEF), using secp384r1 instead.
Wed Feb 03 22:48:58 2021 ECDH curve secp384r1 added
Wed Feb 03 22:48:58 2021 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 03 22:48:58 2021 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Wed Feb 03 22:48:58 2021 interactive service msg_channel=0
Wed Feb 03 22:48:58 2021 ROUTE_GATEWAY 10.0.0.1/255.255.255.0 I=6 HWADDR=00:0d:3a:bf:68:43
Wed Feb 03 22:48:58 2021 open_tun
Wed Feb 03 22:48:58 2021 TAP-WIN32 device [Local Area Connection] opened: \.\Global{17008362-59FE-4FEF-BFA4-8853F107D2AF}.tap
Wed Feb 03 22:48:58 2021 TAP-Windows Driver Version 9.24
Wed Feb 03 22:48:58 2021 Notified TAP-Windows driver to set a DHCP IP/netmask of 10.8.0.1/255.255.255.252 on interface {17008362-59FE-4FEF-BFA4-8853F107D2AF} [DHCP-serv: 10.8.0.2, lease-time: 31536000]
Wed Feb 03 22:48:58 2021 Sleeping for 10 seconds...
Wed Feb 03 22:49:08 2021 Successful ARP Flush on interface [10] {17008362-59FE-4FEF-BFA4-8853F107D2AF}
Wed Feb 03 22:49:08 2021 C:\windows\system32\route.exe ADD 10.8.0.0 MASK 255.255.255.0 10.8.0.2
Wed Feb 03 22:49:08 2021 ROUTE: CreateIpForwardEntry succeeded with dwForwardMetric1=25 and dwForwardType=4
Wed Feb 03 22:49:08 2021 Route addition via IPAPI succeeded [adaptive]
Wed Feb 03 22:49:08 2021 Could not determine IPv4/IPv6 protocol. Using AF_INET6
Wed Feb 03 22:49:08 2021 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Feb 03 22:49:08 2021 setsockopt(IPV6_V6ONLY=0)
Wed Feb 03 22:49:08 2021 UDPv6 link local (bound): [AF_INET6][undef]:1194
Wed Feb 03 22:49:08 2021 UDPv6 link remote: [AF_UNSPEC]
Wed Feb 03 22:49:08 2021 MULTI: multi_init called, r=256 v=256
Wed Feb 03 22:49:08 2021 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Wed Feb 03 22:49:08 2021 ifconfig_pool_read(), in='pfsense-tienen,10.8.0.4', TODO: IPv6
Wed Feb 03 22:49:08 2021 succeeded -> ifconfig_pool_set()
Wed Feb 03 22:49:08 2021 IFCONFIG POOL LIST
Wed Feb 03 22:49:08 2021 pfsense-tienen,10.8.0.4
Wed Feb 03 22:49:08 2021 Initialization Sequence Completed
Wed Feb 03 22:49:08 2021 Initialization Sequence Completed
Wed Feb 03 22:52:23 2021 Authenticate/Decrypt packet error: packet HMAC authentication failed
Wed Feb 03 22:52:23 2021 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:95.254.142.29:11873 -
We are going to need to see some details of how it's configured but this looks like actually some kind of cert/key/hash mismatch:
Wed Feb 03 22:52:23 2021 Authenticate/Decrypt packet error: packet HMAC authentication failedSteve
-
@stephenw10 I got it working.... but I am still seeing:
WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1557', remote='link-mtu 1550'
WARNING: 'cipher' is used inconsistently, local='cipher AES-256-CBC', remote='cipher AES-256-GCM'
WARNING: 'auth' is used inconsistently, local='auth SHA1', remote='auth [null-digest]'
WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo'
Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSAAllthough in my C:\Program Files\OpenVPN\easy-rsa\keys\server.ovpn
I have:versions see below)
compress lz4-v2
;push "compress lz4-v2"enable it in the client config file.
comp-lzo
cipher AES-256-GCMand on the pfsense I have:
Where do/can I adjust the settings?
AND what settings can I best set for the fastest vpn speed, security less important? -
@nick-loenders Biggest problem now is actually that I can ping from a client within the lan to the openvpnserver; but that is it.
I want to do a mapping to a folder on the server, but it does not seem to find a route? -
The compression type has to match. It's generally better to use 'omit preference' there. You appear to have different values set there.
What subnets are you pushing to the client? Is it configured to route all traffic over the tunnel?
Where are connecting from exactly?
Is the server configured to allow traffic from the remote subnet?
Steve
-
@stephenw10
My server.ovpn is set like:
port 1194proto udp
dev tun
ca "C:\Program Files\OpenVPN\config\ca.crt"
cert "C:\Program Files\OpenVPN\config\server.crt"
key "C:\Program Files\OpenVPN\config\server.key"dh "C:\Program Files\OpenVPN\config\dh2048.pem"
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
push "route 172.16.17.0 255.255.255.0"
push "route 10.8.0.0 255.255.255.0"push "dhcp-option DNS 172.16.17.254"
push "dhcp-option DNS 10.8.0.2"client-to-client
duplicate-cn
keepalive 10 120
tls-auth ta.key 0 # This file is secret
cipher AES-256-GCM
compress lz4-v2
push "compress lz4-v2"max-clients 60
persist-key
persist-tunstatus openvpn-status.log
verb 3
explicit-exit-notify 1
-------------
I only hope it is using this server.ovpn file? :)
The setup is that
I have a windows 10 vm with openvpnserver.
I have a pfsense at anothe location which is running openvpn-client, which connects to the openvpserver.
On the LAN network of the pfsense I have client pcs and from there I need to map a shared folder which is located on the openvpnserver.So my openvpnserver is 10.8.0.1
My pfsense openpvn client ip is 10.8.0.6
The pc has ip in the range 172.16.17.0/24 and it can ping to 10.8.0.1, but not make a mapping.The tunnel does not have to be going to the internet. the client-pc's only need to be able to map the shared folder.
-
You shouldn't be pushing a route to the local subnet (172.16.17.0/24) over the tunnel. The client end is local to that subnet. It will be refusing that route anyway.
You should have a route to the servers internal IP not just the tunnel subnet which may or may not respond.How are you trying to map the shares?
Steve
-
I see on your other thread that the server is using 10.0.0.0/24 as it's internal IP and you are not pushing that as a route so pfSense has no route to it.
I also see there you list the pfSense LAN subnet as 172.14.10.0 which is not what you wrote here and also not a private subnet.
Steve
-
@stephenw10
ok, so I put
push "route 10.8.0.0 255.255.255.0"
push "route 10.0.0.0 255.255.255.0"in the server.ovpn file and restarted the tunnelservices.
I do a mapping using:
net use q: \10.8.0.1\test /user:pcname\username passwordbut nothing.
-
by the way, how can I know it is certainly using this file:
C:\Program Files\OpenVPN\easy-rsa\keys\server.ovpn ??and is it ok if I just change that file, or do I need to do anything else when I change the contents of this file?
-
You don't actually need to push a route to the tunnel subnet since the client has an interface in it.
The tunnel IP is a virtual interface that may not respond like other interfaces. You should try to map the drive to the real server IP in the 10.0.0.0/24 subnet.
Since it's a TLS/SSL server you might also need a client specific override for the pfSense client so the server knows where the 172.16.17.0/24 subnet is.
Steve
-
@stephenw10
I appreciate the fast response.
But I really need more info on where to add/change what :(
It is the first time I do this kind of advanced thing -
I've never tried to configure that in Windows so I can't really help you there.
-
@stephenw10
But you can tell me how it should look like in the openvpnclient on the Netgate?
maybe I need to put some ip's there as well? or do some weird nat ruling?plus, the openvpn server, whether if it is running on Windows or Linux, the parameters stay the same, no?
-
If the server is configured as SSL/TLS with a tunnel subnet larger than /30 then all values are passed from the server to the client when it connects.
As long as the client in pfSense is not configured with 'do not pull routes' then it should get a route to 10.0.0.0/24 when it connects. You can check the system routing table to make sure though.Steve