1:1 NAT Routing Issues - Draytek IPSEC Connection to External PFSENSE
-
Evening,
I have a PFSENSE behind which some customers in a shared office need to connect to IPSEC connections with their own router. I have enabled 1:1 NAT rule for the device and internet connection seems to work.
However the customer could not get an IPSEC connection established. I have setup a Draytek router to test and I am also having trouble getting an IPSEC connection configured from the Draytek outbound to an external PFSENSE router.
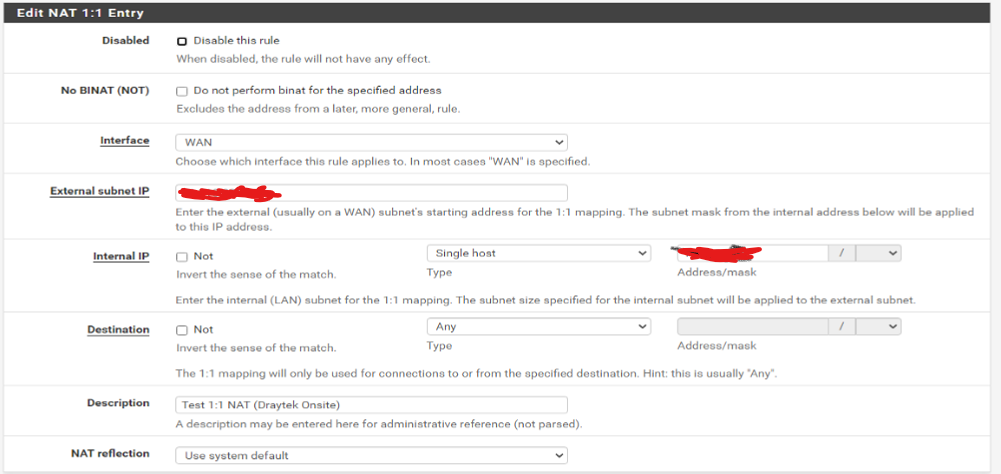
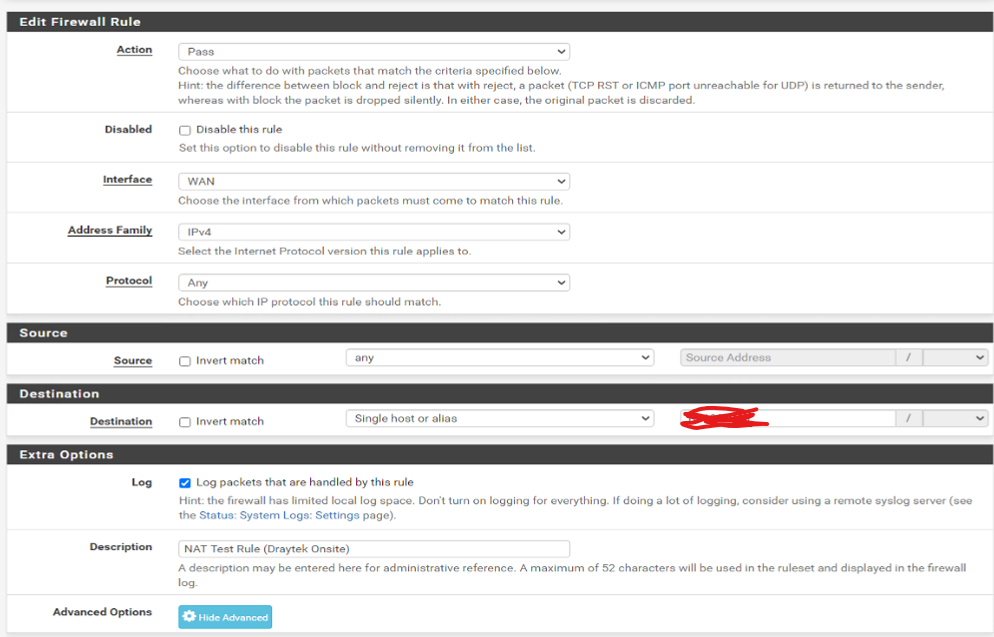
Are there some other settings i'm missing in this configuration? I'm mirroring setups I have of Drayteks connection to IPSEC on a Draytek and they aren't working.
Below are the connection logs from the IPSEC logs on the PFSENSE the Draytek is trying to connect to externally.
1.1.1.1 - Draytek Router
2.2.2.2 - External PFSENSE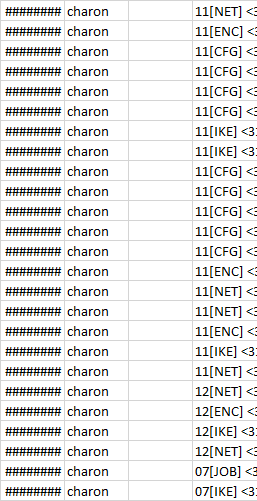
01/02/2009 00:20 charon 11[NET] <3180> received packet: from 1.1.1.1[500] to 2.2.2.2[500] (760 bytes)
01/02/2009 00:20 charon 11[ENC] <3180> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
01/02/2009 00:20 charon 11[CFG] <3180> looking for an IKEv2 config for 2.2.2.2...1.1.1.1
01/02/2009 00:20 charon 11[CFG] <3180> candidate: %any...%any, prio 24
01/02/2009 00:20 charon 11[CFG] <3180> candidate: 2.2.2.2...1.1.1.1, prio 3096
01/02/2009 00:20 charon 11[CFG] <3180> found matching ike config: 2.2.2.2...1.1.1.1 with prio 3096
01/02/2009 00:20 charon 11[IKE] <3180> 1.1.1.1 is initiating an IKE_SA
01/02/2009 00:20 charon 11[IKE] <3180> IKE_SA (unnamed)[3180] state change: CREATED => CONNECTING
01/02/2009 00:20 charon 11[CFG] <3180> selecting proposal:
01/02/2009 00:20 charon 11[CFG] <3180> proposal matches
01/02/2009 00:20 charon 11[CFG] <3180> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:AES_CBC_192/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_192/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048
01/02/2009 00:20 charon 11[CFG] <3180> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
01/02/2009 00:20 charon 11[CFG] <3180> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
01/02/2009 00:20 charon 11[ENC] <3180> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(CHDLESS_SUP) N(MULT_AUTH) ]
01/02/2009 00:20 charon 11[NET] <3180> sending packet: from 2.2.2.2[500] to 1.1.1.1[500] (448 bytes)
01/02/2009 00:20 charon 11[NET] <3180> received packet: from 1.1.1.1[500] to 2.2.2.2[500] (760 bytes)
01/02/2009 00:20 charon 11[ENC] <3180> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
01/02/2009 00:20 charon 11[IKE] <3180> received retransmit of request with ID 0, retransmitting response
01/02/2009 00:20 charon 11[NET] <3180> sending packet: from 2.2.2.2[500] to 1.1.1.1[500] (448 bytes)
01/02/2009 00:20 charon 12[NET] <3180> received packet: from 1.1.1.1[500] to 2.2.2.2[500] (760 bytes)
01/02/2009 00:20 charon 12[ENC] <3180> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
01/02/2009 00:20 charon 12[IKE] <3180> received retransmit of request with ID 0, retransmitting response
01/02/2009 00:20 charon 12[NET] <3180> sending packet: from 2.2.2.2[500] to 1.1.1.1[500] (448 bytes)
01/02/2009 00:20 charon 07[JOB] <3180> deleting half open IKE_SA with 1.1.1.1 after timeout
01/02/2009 00:20 charon 07[IKE] <3180> IKE_SA (unnamed)[3180] state change: CONNECTING => DESTROYING