see local network ip address on pfsense
-
Please show us a screenshot(s) of what it is connecting to.
-
This post is deleted! -
@stephenw10 So I have two networks:
The first 192.168.2.0 is that of the Fritz box where all the devices are connected.
The second network is that of pfsense 192.168.1.0 where the devices in Lan and WIFI are connected via access poin.
Now the openvpn connects only on the devices of the network of the fritzbox 192.168.2.0 and works correctly.
I don't know how to connect clients on pfsense network 192.168.1.0 -
If you need to be able to access the pfSense LAN subnet (192.168.1.0/24) from the VPN then you need to add it to the field
Reti locali IPv4in the OpenVPN server.It looks like that is already there in the screenshot above though.
Steve
-
This post is deleted! -
It looks like the network you are connecting from is using the same subnet as the pfSense LAN (192.168.1.0/24).
That is a conflict. The client cannot add a route to 192.168.1.0/24 when it is already in that subnet.
Try connecting from a different subnet and retest.
Steve
-
@stephenw10 How should I do?
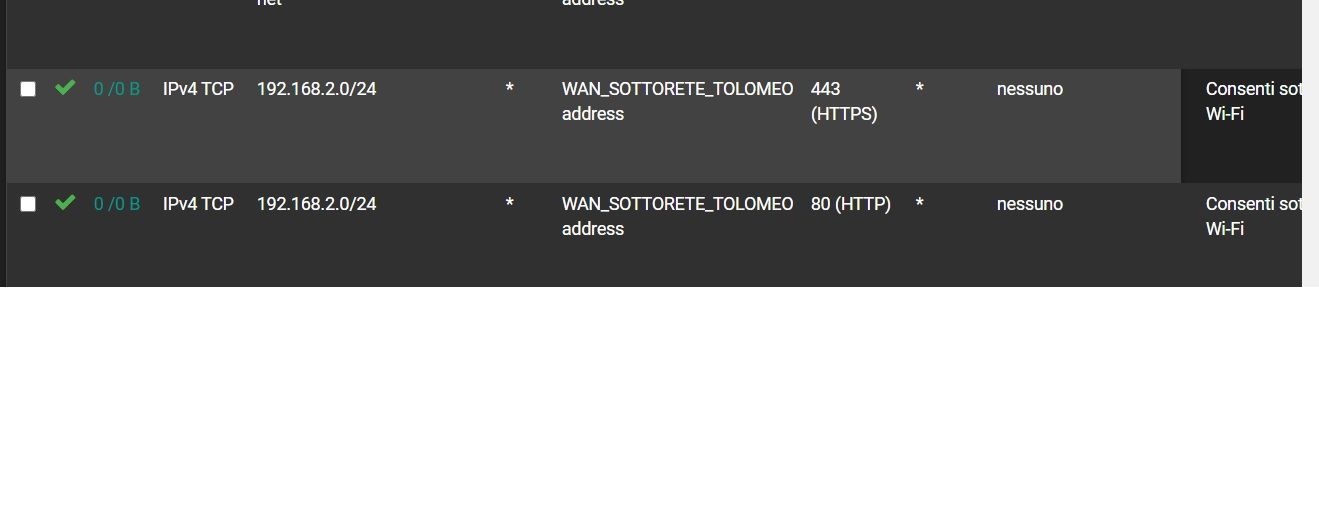
Maybe explain to me with screenshots -
@stephenw10
i connected from another network on the openvpn server but nothing always connects with the fritz box and not with pfsense -
@antonio-briguglio said in see local network ip address on pfsense:
connects with the fritz box
Please show what you mean by this?
The Fritxbox is in the 192.168.2.0/24 subnet, yes? You are not passing that as a local subnet to OpenVPN clients so it's hard to see how they could connect to it.
Steve
-
@stephenw10 I want that when I connect with openvpn the customers who surf the internet with vpn are protected by pfsense
For example, on pfsense I blocked facebok while on the router fritz facebook is working you can access it.
Now if I connect with openvpn and go to facebook it is not blocked because opeb vpn is connected to the fritz network while I would like the client to connect with open vpn and the firewall blocks facebook.
I don't know if I've made myself clear -
@antonio-briguglio said in see local network ip address on pfsense:
i connected from another network on the openvpn server but nothing always connects with the fritz box and not with pfsense
What is "from another network" ?
Your phone and the data carrier 3G/4G/5G ? Or some other place ?
You're using your "Internet IP", the WAN IP of the Fritsbox" and port number 1194, right ? Then OpenVPN server of the Fritzbox will answer.You should another port, as said x times already above, 1195 for example - same protocol = UDP. And, again, you should NAT (PAT) this port to the WAN IP of pfSense, 192.168.1.x.
Your OpenvPN server could be listeing on (its) port 1194 : just make sure that the NAT rule of the frits NAT from port (outside) 1195 to the 1194 (inside).You have to make a NAT (PAT) rule in the Fritsbox. This is not a choice. Without the NAT rule you can't access the OpenVPN of pfSense.
Or, make your live easier on yourself : remove the Fritsbox, make pfSense your one and unique router. No need to NAT in this case.
Example :
Like you, I have a router in front of my pfSense.
I have to, because the DSL carrier over the phone line is non-standard.
This ISP router doesn't have 'bridge' (pppoe) capabilities.I had to add a NAT / PAT rule into this ISP router :
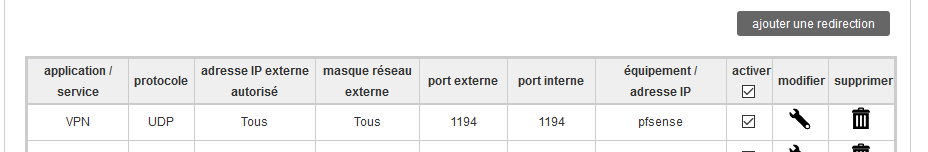
It states :
Protocol = UDP
Permitted outside IP addresses : everybody (all Internet IP's)
The port on the ISP WAN IP : 1194
The port to translate to : 1194 (my pfSense OpenVPN is set up to listen on port 1194)
The host name of the device on this router's LAN : 'pfSense' = the only the only device on this 'LAN' = in my case 192.168.10.3
This 192.168.10.3 is the WAN IP of my pfSense.Note :
I'm not using the Wifi capabilities of the ISP router; I've shut it down. I use my own AP's on a LAN behind pfSense.
Neither the TV functions.
No telephones.
The ISP is just routing pure Internet, nothing else.The ISP router has OPENVPN server capabilities : I don't use it. Because, why would I ? I would still be on the wrong side of my main firewall : pfSense.
When connected to the OpenVPN serser of pfSense, I can access all the pfSense LAN devices - and all other devices on others OPTx networks.On pfSense, I have just one WAN firewall rule :
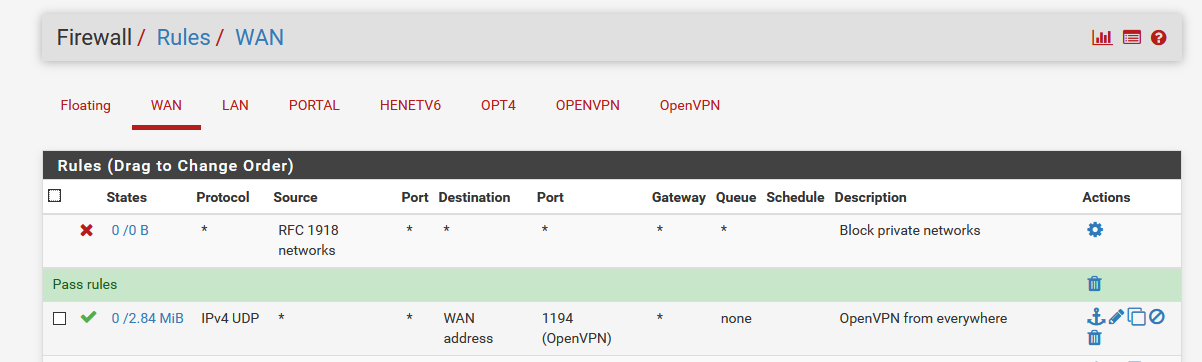
This rule is normally created for you if you have used the OpenVPN server wizard. you could also make it yourself, as it is soooooo easy.
-
OK, then you need to send all traffic over the tunnel. Check this:
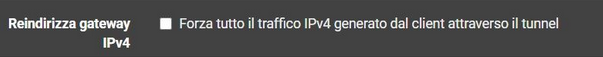
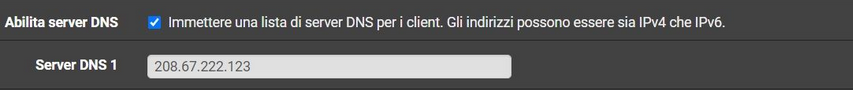
And you need to set pfSense as the DNS server for clinets:
Set 192.168.1.1 here:
Steve
-
This post is deleted! -
This post is deleted! -
This post is deleted! -
@stephenw10 Now it recognizes the lan I have done some tests peróquello openvpn does not connect both on the squid and squidguard package where I have set other filters eg block facebook and both pfblokerng where it does not block spam geoip ...
So the problem is squid squidguard and pfblokerng doesn't block the content that I have blocked -
Do you have Squid configured to redircet traffic on the OpenVPN interface? Or the assigned interface if you have done that.
The SG-1100 it not really appropriate for running Squid, Squidguard and pfBlocker without careful tuning to limit RAM usage.
Steve
-
@stephenw10 no and I don't know how to do it if you make me screnshoot
-
You should open a new thread for that. It looks like OpenVPN is working OK and you have now moved to a Squid problem.
I would not recommend running Squid, Squidguard and pfBlocker on the SG-1100 though.
Steve
-
@stephenw10 Hi I opened another post but no one in this forum answered me.
Can you help me make it work I need it for work thanks
https://forum.netgate.com/topic/160813/configure-squid-to-redirect-traffic-on-the-openvpn-interface?_=1613265742228