IPSec Dashboard Widget not displaying proper status
-
@ensnare said in IPSec Dashboard Widget not displaying proper status:
@jimp Understood, and thanks for the explanation. In that case an obvious suggestion: why not resolve the hostname to IP before generating swanctl.conf, and update on IP changes?
Then we have to have another daemon constantly updating the config when strongSwan can do it itself automatically in a more reliable way. Also strongSwan can check it when new connections are coming in so it's more responsive to changes than waiting on a daemon to do it periodically.
Or, is there a workaround? Because it appears in the current implementation, there is no way to get a site-to-site tunnel displaying properly when remote_addrs is a hostname. Thank you
The status is correct in the status page, just not the widget count. There is likely some room for improvement there for future versions but for the moment it's just a fact of life if you must use hostnames instead of IP addresses.
-
I'm experiencing the same issue, however my site-to-site config is set as IP addresses and does not use hostnames in the configuration. I'm seeing the same issue with the widget & status showing tunnels not connected, but also a substantial amount of logspam around dead peer detection it seems.
Host A (Primary):
Widget:
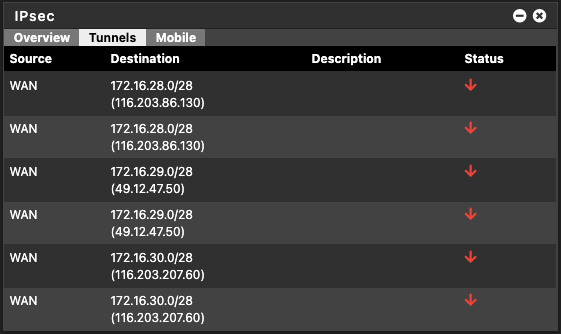
IPSec --> Status
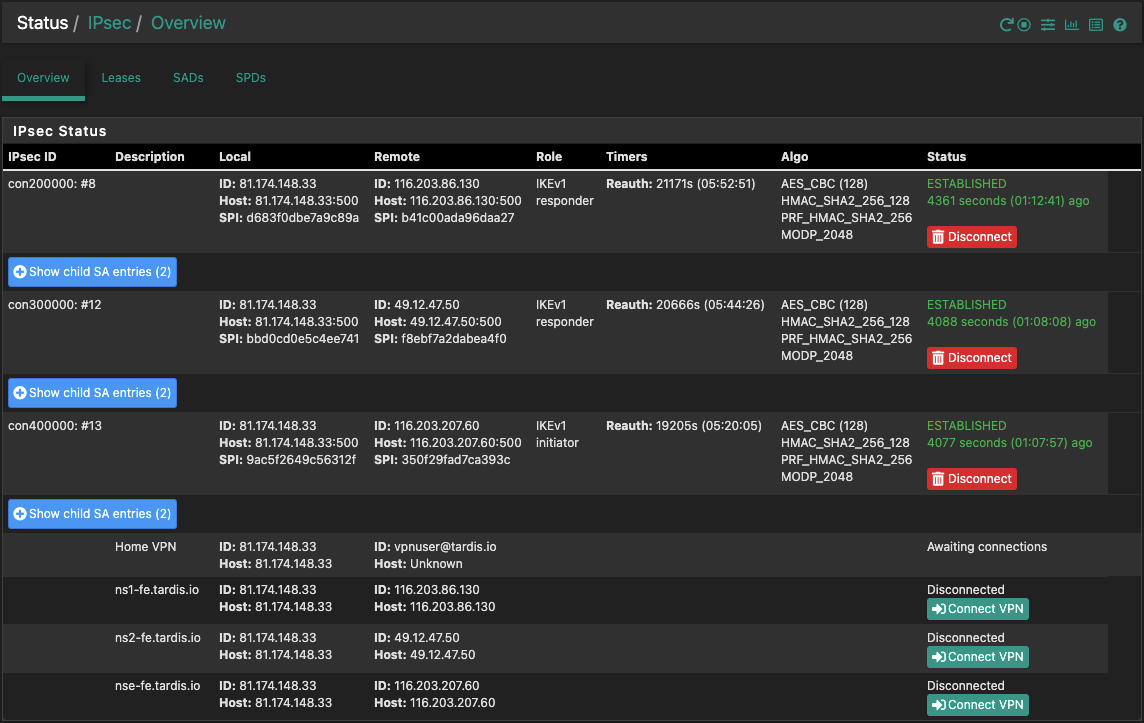
: swanctl --list-conns bypass: IKEv1/2, no reauthentication, rekeying every 14400s local: %any remote: 127.0.0.1 local unspecified authentication: remote unspecified authentication: bypasslan: PASS, no rekeying local: 10.0.0.0/8|/0 2001:470:6a3c:1115::/64|/0 remote: 10.0.0.0/8|/0 2001:470:6a3c:1115::/64|/0 con-mobile: IKEv1/2, no reauthentication, rekeying every 25920s, dpd delay 10s local: 81.174.148.33 remote: 0.0.0.0/0 remote: ::/0 local pre-shared key authentication: id: 81.174.148.33 remote pre-shared key authentication: remote XAuth authentication: con-mobile: TUNNEL, rekeying every 3240s, dpd action is clear local: 0.0.0.0/0|/0 remote: dynamic con200000: IKEv1, reauthentication every 25920s, dpd delay 10s local: 81.174.148.33 remote: 116.203.86.130 local pre-shared key authentication: id: 81.174.148.33 remote pre-shared key authentication: id: 116.203.86.130 con0: TUNNEL, rekeying every 3240s, dpd action is hold local: 172.20.0.0/24|/0 remote: 172.16.28.0/28|/0 con1: TUNNEL, rekeying every 3240s, dpd action is hold local: 10.0.0.0/8|/0 remote: 172.16.28.0/28|/0 con300000: IKEv1, reauthentication every 25920s, dpd delay 10s local: 81.174.148.33 remote: 49.12.47.50 local pre-shared key authentication: id: 81.174.148.33 remote pre-shared key authentication: id: 49.12.47.50 con0: TUNNEL, rekeying every 3240s, dpd action is hold local: 172.20.0.0/24|/0 remote: 172.16.29.0/28|/0 con1: TUNNEL, rekeying every 3240s, dpd action is hold local: 10.0.0.0/8|/0 remote: 172.16.29.0/28|/0 con400000: IKEv1, reauthentication every 25920s, dpd delay 10s local: 81.174.148.33 remote: 116.203.207.60 local pre-shared key authentication: id: 81.174.148.33 remote pre-shared key authentication: id: 116.203.207.60 con0: TUNNEL, rekeying every 3240s, dpd action is hold local: 172.20.0.0/24|/0 remote: 172.16.30.0/28|/0 con1: TUNNEL, rekeying every 3240s, dpd action is hold local: 10.0.0.0/8|/0 remote: 172.16.30.0/28|/0: swanctl --list-sas con200000: #8, ESTABLISHED, IKEv1, b41c00ada96daa27_i d683f0dbe7a9c89a_r* local '81.174.148.33' @ 81.174.148.33[500] remote '116.203.86.130' @ 116.203.86.130[500] AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 established 4125s ago, reauth in 21407s con0: #25, reqid 1, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 1147s ago, rekeying in 1740s, expires in 2453s in cfe26eb3, 1655745 bytes, 1264 packets, 6s ago out c20430ee, 6392 bytes, 42 packets, 83s ago local 172.20.0.0/24|/0 remote 172.16.28.0/28|/0 con1: #26, reqid 2, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 1054s ago, rekeying in 1921s, expires in 2546s in c91c01bb, 1434954 bytes, 1407 packets, 99s ago out c7bf2c9f, 97128 bytes, 698 packets, 54s ago local 10.0.0.0/8|/0 remote 172.16.28.0/28|/0 con300000: #12, ESTABLISHED, IKEv1, f8ebf7a2dabea4f0_i bbd0cd0e5c4ee741_r* local '81.174.148.33' @ 81.174.148.33[500] remote '49.12.47.50' @ 49.12.47.50[500] AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 established 3852s ago, reauth in 20902s con0: #28, reqid 3, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 869s ago, rekeying in 2267s, expires in 2731s in c8c59fdf, 1286776 bytes, 1050 packets, 3s ago out c966e53c, 80724 bytes, 123 packets, 107s ago local 172.20.0.0/24|/0 remote 172.16.29.0/28|/0 con1: #29, reqid 4, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 852s ago, rekeying in 2150s, expires in 2748s in cf22683f, 2016 bytes, 24 packets, 134s ago out c433623f, 3744 bytes, 24 packets, 134s ago local 10.0.0.0/8|/0 remote 172.16.29.0/28|/0 con400000: #13, ESTABLISHED, IKEv1, 9ac5f2649c56312f_i* 350f29fad7ca393c_r local '81.174.148.33' @ 81.174.148.33[500] remote '116.203.207.60' @ 116.203.207.60[500] AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 established 3841s ago, reauth in 19441s con0: #27, reqid 5, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 876s ago, rekeying in 2070s, expires in 2724s in cf53a3e5, 1164684 bytes, 897 packets, 8s ago out c86a97be, 5704 bytes, 38 packets, 66s ago local 172.20.0.0/24|/0 remote 172.16.30.0/28|/0 con1: #30, reqid 6, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 846s ago, rekeying in 2058s, expires in 2754s in cbef0452, 2016 bytes, 24 packets, 137s ago out c52f80c4, 3744 bytes, 24 packets, 137s ago local 10.0.0.0/8|/0 remote 172.16.30.0/28|/0Host B (Remote):
Widget:
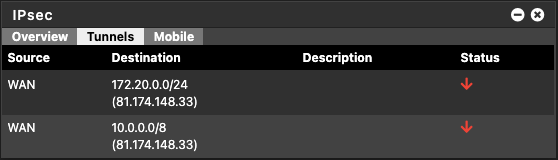
IPSec --> Status:
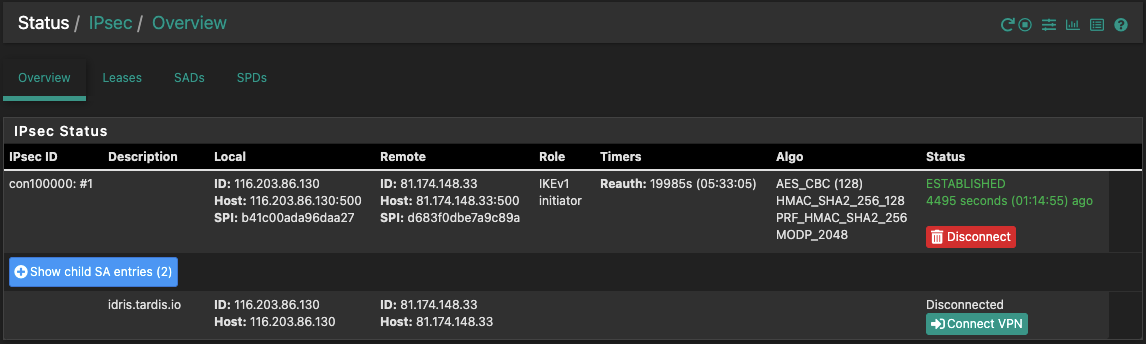
: swanctl --list-conns bypass: IKEv1/2, no reauthentication, rekeying every 14400s local: %any remote: 127.0.0.1 local unspecified authentication: remote unspecified authentication: bypasslan: PASS, no rekeying local: 172.16.28.2/32|/0 remote: 172.16.28.2/32|/0 con100000: IKEv1, reauthentication every 25920s, dpd delay 10s local: 116.203.86.130 remote: 81.174.148.33 local pre-shared key authentication: id: 116.203.86.130 remote pre-shared key authentication: id: 81.174.148.33 con0: TUNNEL, rekeying every 3240s, dpd action is hold local: 172.16.28.0/28|/0 remote: 172.20.0.0/24|/0 con1: TUNNEL, rekeying every 3240s, dpd action is hold local: 172.16.28.0/28|/0 remote: 10.0.0.0/8|/0: swanctl --list-sas con100000: #1, ESTABLISHED, IKEv1, b41c00ada96daa27_i* d683f0dbe7a9c89a_r local '116.203.86.130' @ 116.203.86.130[500] remote '81.174.148.33' @ 81.174.148.33[500] AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 established 4634s ago, reauth in 19846s con0: #5, reqid 1, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 1656s ago, rekeying in 1316s, expires in 1944s in c20430ee, 5248 bytes, 64 packets, 3s ago out cfe26eb3, 2517760 bytes, 1828 packets, 3s ago local 172.16.28.0/28|/0 remote 172.20.0.0/24|/0 con1: #6, reqid 2, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/MODP_3072 installed 1563s ago, rekeying in 1415s, expires in 2037s in c7bf2c9f, 102181 bytes, 1271 packets, 12s ago out c91c01bb, 1752956 bytes, 2037 packets, 12s ago local 172.16.28.0/28|/0 remote 10.0.0.0/8|/0As for the log spam, this is what I am seeing (taken from Host B, however this is present on all instances). This was never an issue/present in 2.4.5 prior to the upgrade:
Feb 17 19:47:31 charon 99460 12[CFG] vici client 23 connected Feb 17 19:47:31 charon 99460 09[CFG] vici client 23 registered for: list-conn Feb 17 19:47:31 charon 99460 14[CFG] vici client 23 requests: list-conns Feb 17 19:47:31 charon 99460 14[CFG] vici client 23 disconnected Feb 17 19:47:36 charon 99460 07[CFG] vici client 24 connected Feb 17 19:47:36 charon 99460 09[CFG] vici client 24 registered for: list-sa Feb 17 19:47:36 charon 99460 09[CFG] vici client 24 requests: list-sas Feb 17 19:47:36 charon 99460 09[CFG] vici client 24 disconnected Feb 17 19:47:39 charon 99460 07[CFG] vici client 25 connected Feb 17 19:47:39 charon 99460 13[CFG] vici client 25 registered for: list-sa Feb 17 19:47:39 charon 99460 09[CFG] vici client 25 requests: list-sas Feb 17 19:47:39 charon 99460 09[CFG] vici client 25 disconnected Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> sending DPD request Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> queueing ISAKMP_DPD task Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> activating new tasks Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> activating ISAKMP_DPD task Feb 17 19:47:46 charon 99460 09[ENC] <con100000|1> generating INFORMATIONAL_V1 request 2019671338 [ HASH N(DPD) ] Feb 17 19:47:46 charon 99460 09[NET] <con100000|1> sending packet: from 116.203.86.130[500] to 81.174.148.33[500] (108 bytes) Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> activating new tasks Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> nothing to initiate Feb 17 19:47:46 charon 99460 09[NET] <con100000|1> received packet: from 81.174.148.33[500] to 116.203.86.130[500] (108 bytes) Feb 17 19:47:46 charon 99460 09[ENC] <con100000|1> parsed INFORMATIONAL_V1 request 3098609444 [ HASH N(DPD_ACK) ] Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> activating new tasks Feb 17 19:47:46 charon 99460 09[IKE] <con100000|1> nothing to initiate Feb 17 19:47:47 charon 99460 13[CFG] vici client 26 connected Feb 17 19:47:47 charon 99460 10[CFG] vici client 26 registered for: list-sa Feb 17 19:47:47 charon 99460 09[CFG] vici client 26 requests: list-sas Feb 17 19:47:47 charon 99460 09[CFG] vici client 26 disconnected Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> sending DPD request Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> queueing ISAKMP_DPD task Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> activating new tasks Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> activating ISAKMP_DPD task Feb 17 19:47:56 charon 99460 10[ENC] <con100000|1> generating INFORMATIONAL_V1 request 3217847920 [ HASH N(DPD) ] Feb 17 19:47:56 charon 99460 10[NET] <con100000|1> sending packet: from 116.203.86.130[500] to 81.174.148.33[500] (108 bytes) Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> activating new tasks Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> nothing to initiate Feb 17 19:47:56 charon 99460 10[NET] <con100000|1> received packet: from 81.174.148.33[500] to 116.203.86.130[500] (108 bytes) Feb 17 19:47:56 charon 99460 10[ENC] <con100000|1> parsed INFORMATIONAL_V1 request 866177057 [ HASH N(DPD_ACK) ] Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> activating new tasks Feb 17 19:47:56 charon 99460 10[IKE] <con100000|1> nothing to initiate Feb 17 19:48:00 newsyslog 39991 logfile turned over due to size>500K Feb 17 19:48:00 newsyslog 39991 logfile turned over due to size>500K Feb 17 19:48:00 charon 99460 15[CFG] vici client 27 connected Feb 17 19:48:00 charon 99460 10[CFG] vici client 27 registered for: list-sa Feb 17 19:48:00 charon 99460 11[CFG] vici client 27 requests: list-sas Feb 17 19:48:00 charon 99460 10[CFG] vici client 27 disconnected Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> sending DPD request Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> queueing ISAKMP_DPD task Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> activating new tasks Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> activating ISAKMP_DPD task Feb 17 19:48:06 charon 99460 10[ENC] <con100000|1> generating INFORMATIONAL_V1 request 3767522245 [ HASH N(DPD) ] Feb 17 19:48:06 charon 99460 10[NET] <con100000|1> sending packet: from 116.203.86.130[500] to 81.174.148.33[500] (108 bytes) Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> activating new tasks Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> nothing to initiate Feb 17 19:48:06 charon 99460 10[NET] <con100000|1> received packet: from 81.174.148.33[500] to 116.203.86.130[500] (108 bytes) Feb 17 19:48:06 charon 99460 10[ENC] <con100000|1> parsed INFORMATIONAL_V1 request 3843431717 [ HASH N(DPD_ACK) ] Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> activating new tasks Feb 17 19:48:06 charon 99460 10[IKE] <con100000|1> nothing to initiate Feb 17 19:48:14 charon 99460 11[CFG] vici client 28 connected Feb 17 19:48:14 charon 99460 08[CFG] vici client 28 registered for: list-sa Feb 17 19:48:14 charon 99460 10[CFG] vici client 28 requests: list-sas Feb 17 19:48:14 charon 99460 10[CFG] vici client 28 disconnected Feb 17 19:48:27 charon 99460 06[CFG] vici client 29 connected Feb 17 19:48:27 charon 99460 08[CFG] vici client 29 registered for: list-sa Feb 17 19:48:27 charon 99460 08[CFG] vici client 29 requests: list-sas Feb 17 19:48:27 charon 99460 16[CFG] vici client 29 disconnected Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> sending DPD request Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> queueing ISAKMP_DPD task Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> activating new tasks Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> activating ISAKMP_DPD task Feb 17 19:48:31 charon 99460 16[ENC] <con100000|1> generating INFORMATIONAL_V1 request 485220965 [ HASH N(DPD) ] Feb 17 19:48:31 charon 99460 16[NET] <con100000|1> sending packet: from 116.203.86.130[500] to 81.174.148.33[500] (108 bytes) Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> activating new tasks Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> nothing to initiate Feb 17 19:48:31 charon 99460 16[NET] <con100000|1> received packet: from 81.174.148.33[500] to 116.203.86.130[500] (108 bytes) Feb 17 19:48:31 charon 99460 16[ENC] <con100000|1> parsed INFORMATIONAL_V1 request 1050251960 [ HASH N(DPD_ACK) ] Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> activating new tasks Feb 17 19:48:31 charon 99460 16[IKE] <con100000|1> nothing to initiate -
OK after checking dozens of my local systems I finally found one that has the problem.
I opened https://redmine.pfsense.org/issues/11435 to track it. Not sure how easy it will be to fix, but doesn't look too hard.
-
I committed a fix for this which is working OK for me.
You can install the System Patches package and then create an entry for
ead6515637a34ce6e170e2d2b0802e4fa1e63a00to fix the status page and57beb9ad8ca11703778fc483c7cba0f6770657acto fix the widget. -
@jimp Thanks so much I just upgraded to the new version and saw these same issues. Your patch definitely resolved my issues on 21.02
-
@jimp Thanks for the quick update. Those patches fixed my setup too.
-
@jimp Works great. Thanks so much. Also noticed that Status > IPSec loads more quickly now.
-
works for me too. thx
-
I get this only on the firewall I did a fresh install of 2.5.0 on. All of the ones that were upgraded don't do it. I'll just wait for 2.5.1.
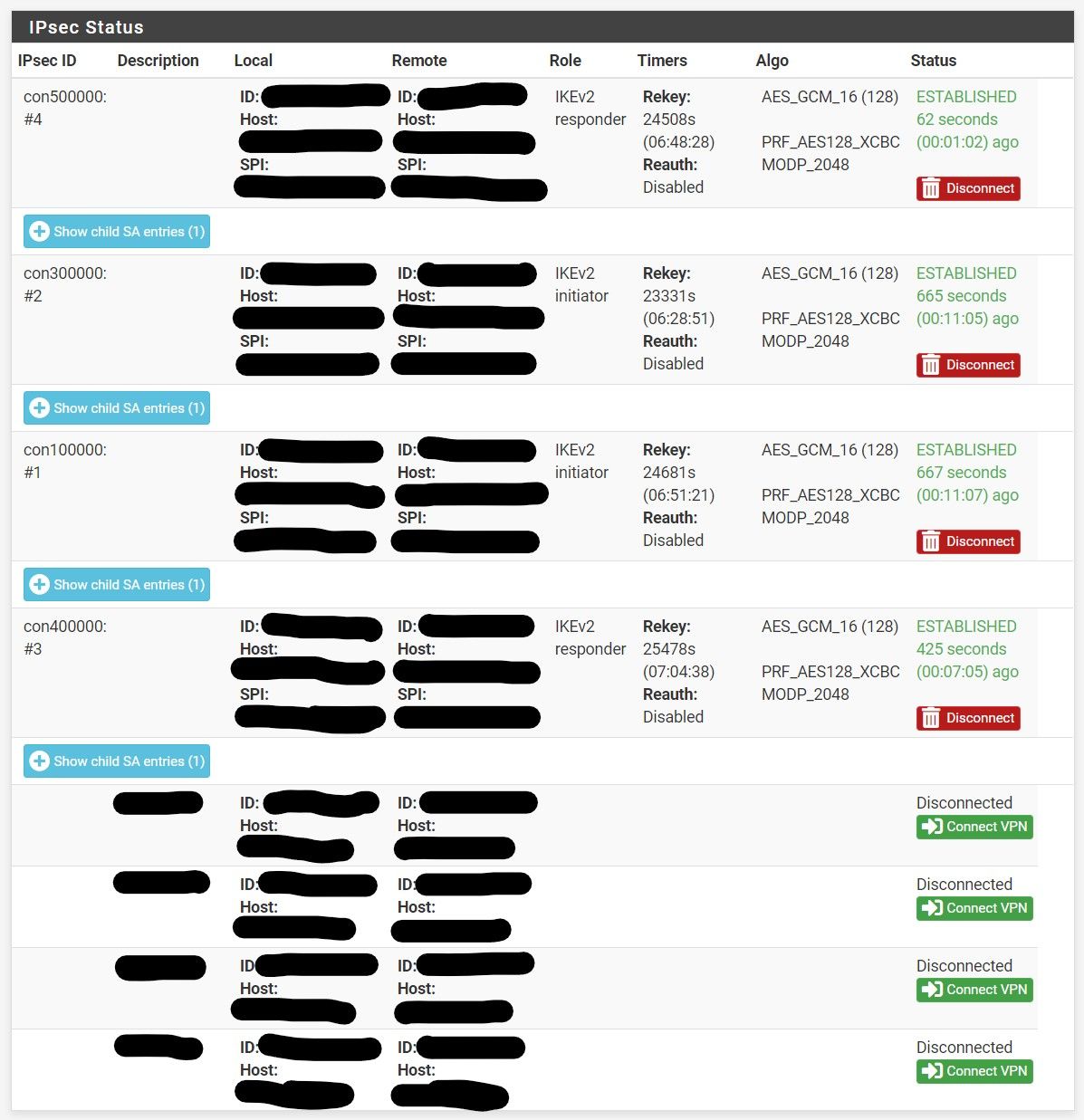
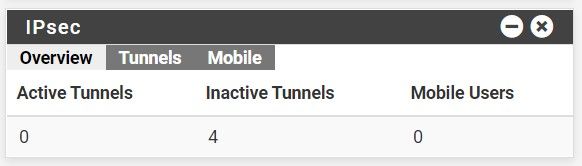
-
The status problem is already known and fixed. To ensure you have all of the current known and fixed IPsec issues corrected, You can install the System Patches package and then create entries for the following commit IDs to apply the fixes: