OpenVPN client showing 100% packetloss following 2.5.0 upgrade
-
@nevar You don't need to disable monitoring, just use an IP to monitor and set it on the Monitor IP setting.
Go to the configurator page on Torguard, set it to Wireguard, choose your server location and plug in the private and public keys you generate in pfsense. It will pop out a configuration, just plug that data in Wireguard and into the peer.
Add a NAT rule for your WAN to LAN (or any other interface)
Add a firewall rule to allow any (everything) for the Wireguard interface.
Under LAN (or any other interface you set in NAT) allow any protocol, source set to whatever you want (I'm using aliases for certain devices), go to advanced tag the traffic (I use vpntraffic) and set the gateway to wireguard.
Create a floating rule for WAN block traffic, Any for all, go to advanced, set tagged to vpntraffic (or whatever you used in the above LAN rule. This is your killswitch, if the connection drops to the VPN, nothing can access the internet via WAN. Test Wireguard before you set the killswitch to rule out errors.
Enjoy Wireguard as a client.
-
@hypnosis4u2nv Did you post in the wrong thread? You're talking about WireGuard in an OpenVPN thread.
-
Nord has not posted their documentation for setting up NordVPN on pfSense 2.5.0.
https://support.nordvpn.com/Connectivity/Router/1626958942/pfSense-2-5-Setup-with-NordVPN.htm
I just went through this new howto doc and made a few changes to my current settings. Those were mostly in the crypto settings for the client config as far as I remember but you might want to go through everything. So far it looks good, I'm connecting and working though the VPN.
-
@griffo The previous user asked how I set it up.
-
@bjames88 said in OpenVPN client showing 100% packetloss following 2.5.0 upgrade:
Nord has not posted their documentation for setting up NordVPN on pfSense 2.5.0.
Interesting how they call out they are not going to let you use Wireguard :-)
Nord do some strange things. LIke the fact they moved to Service credentials rather than username / password. But don't give you a mechanism to revoke or cycle it.... so it's actually less secure than using your username & password as at least you can change them. -
@griffo It doesn't surprise me that they don't have Wireguard available for manual setup yet. The could be working out the best way to deal with the certs. I also liked the user of service credentials but you have a good point that you can't cycle those yourself. Hmmm...
-
@bjames88 Its strange.
After a clean install, I have not made any changes to the NordVPN guide and all is working fine for me.
But it didn't work as a not clean install/upgrade.
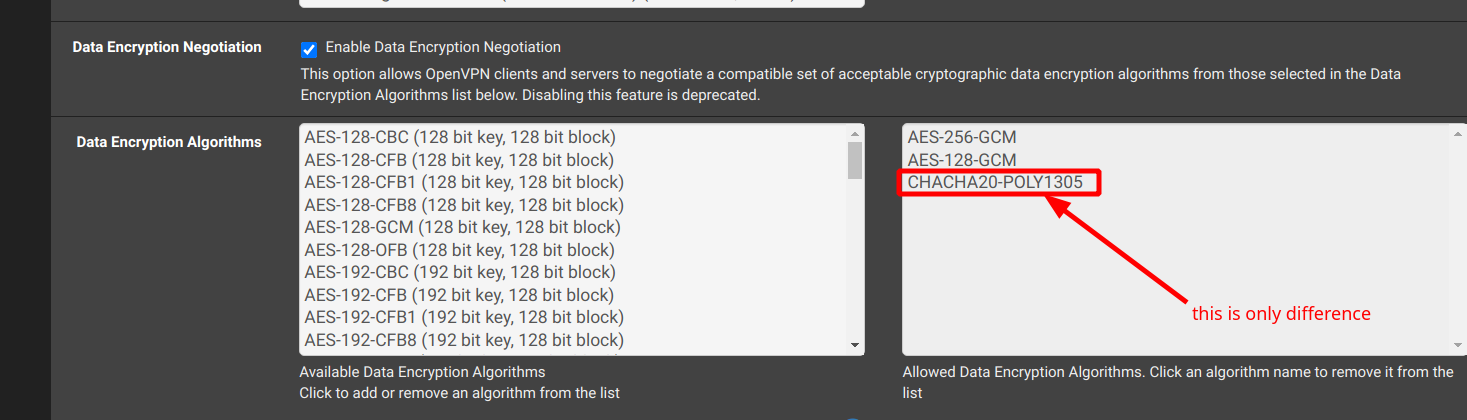
-
@rummonkey69 Had you added those Enable Data Encryption Algorithms or did they show up on their own after the upgrade? Those are not the same Algorithms shown to be added on the Nord 2.4.5 config guide.
-
@skooby I don't believe clean install will help. It is likely added option is set to enable instead of disable like for example the monitor of the gateways. When I was using 2.4, I don't believe there was monitor feature for the gateways. I recommend going through each setting for the interface, gateway and vpn profile.
-
@bjames88 it was default settings, I only added VPN server name , usernames and passwords and the custom rules as mentioned on the site.
-
@nevar yes the monitor features has been there for long time.
-
@rummonkey69 hmmm, i can only guess there some changes to it since i didn't encounter with "offline, 100% packetloss" on the gateway after i upgrade to 2.5 and only resolve my issue to enable "disable monitoring" checkboxes.
-
@nevar yeah I had to disable them when I upgraded. But no issues when clean.
-
@rummonkey69 i had the same issue with the late dev builds. No matter what i did, post upgrade Nord would not connect, or after editing it would connect but total traffic loss. A clean build and it worked fine.
-
@griffo I had issues with a clean install of pfsense and restoring my config. I'd lean towards something wrong with the old config and how it transfers over to the new version of openvpn.
-
@hypnosis4u2nv Yes same, restoring config did not work. Clean build, restoring just OpenVPN config did not work.
Clean build, manual config recreation worked.
-
Hi!
Does anyone have Torguard OpenVPN UDP / TCP working with 2.5? I have setup the OpenVPN tunnel with Torguard and it connects fine. But it stays on Gateway Monitor down. I have tried setting up a specific Ip for gateway monitoring (tried with 8.8.8.8 and 1.1.1.1) but it is still not registering the interface up. I have tried several reboots already. Now I'm thinking I have to downgrade my pfsense to (clean install ofcourse) version 2.4 to get this working.I already have a ticket open with Torguard support and awaiting their answer. In my research I stumbled on this topic. Thank you guys for helping!
-
@vjizzle here are setting that got my torguard working again:
- System > Routing > Gateways > Edit (your torguard), checked the following option: disable gateway monitoing and disable gateway monitoring action. Gateway : dynamic.
- VPN > OpenVPN > Clients > Edit (your torguard), I can't get udp working before so I stuck using tcp for Protocol. TLS keydir direction: use default direction. Unchecked "Enable Data Encryption Negotiation". Fallback Data Encryption Algorithm: AES-128-GCM. Checked "Don't pull routes" and "Don't add/remove routes"
-
@nevar
Thank you for sharing your configuration :). Disabling gateway monitoring is not an option for me. The idea is to use several tunnels in a gateway group and have a sort of "fallback" when one VPN server goes doen. So I think I will do the downgrade and wait for Torguard to officially support pfSense 2.5.Thanks again!
-
@vjizzle I tried playing with this a little while again and I couldn't get it to stay up. It would show connected and then go down.
I have working and will stick with that for a whileuuntil Netgate fixes these issues.