WG not routing or sending traffic
-
@xxgbhxx I also use IVPN as my provider and I have it working. Here are some screen shots of how I have my various settings configured.
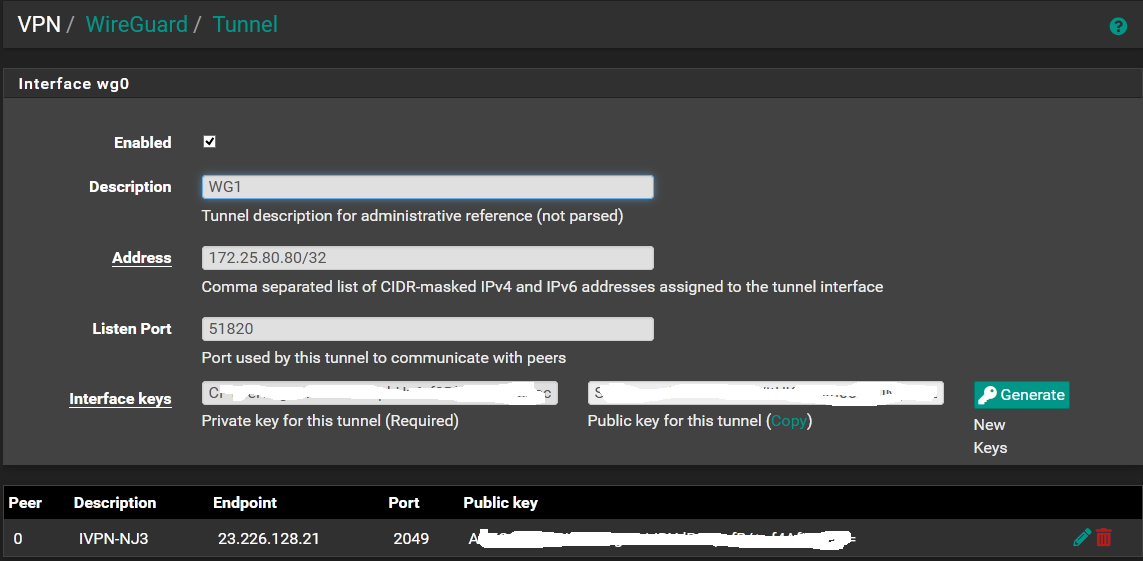
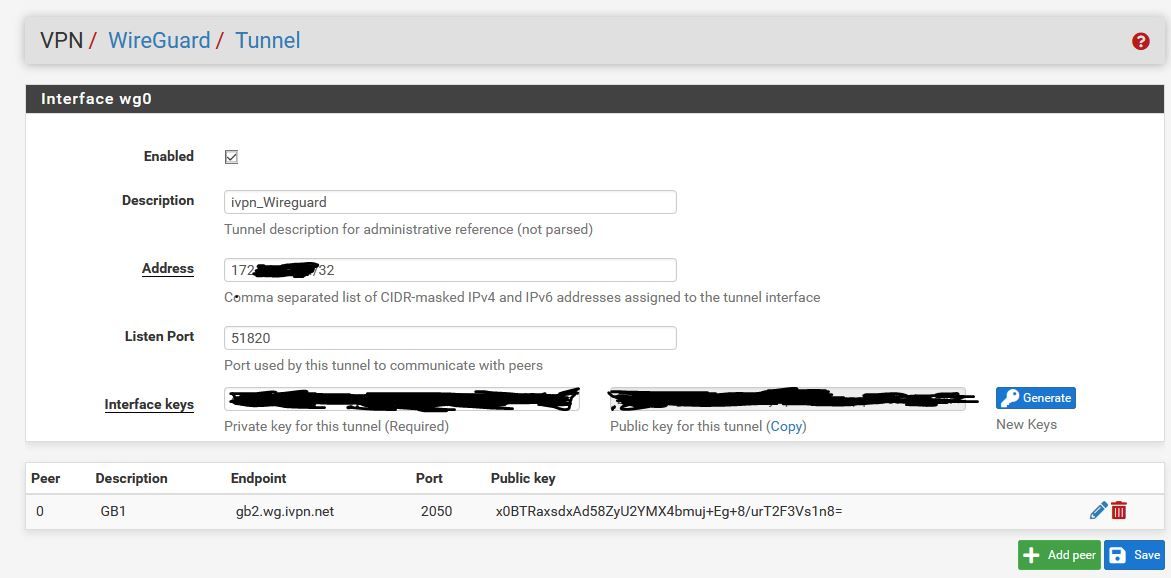
The "Address" above is the IP address that IVPN will assign to you when you take the Public Key shown above and link it into your account at IVPN. Just copy and paste it in IVPN's WireGuard Key Management in your account settings and then note the IP address they give you.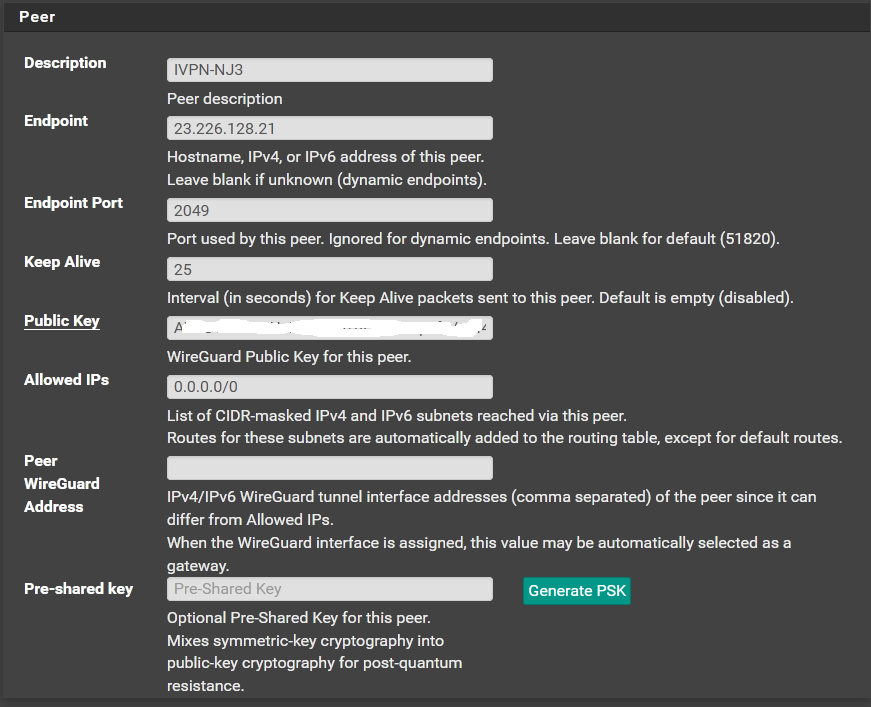
The ip address you see above in Endpoint is the IP address for one of IVPN's wireguard servers. You can just copy and paste the FQDN from IVPN's website for the server you want to use. The public key will be found on IVPN's website for the server you want to use.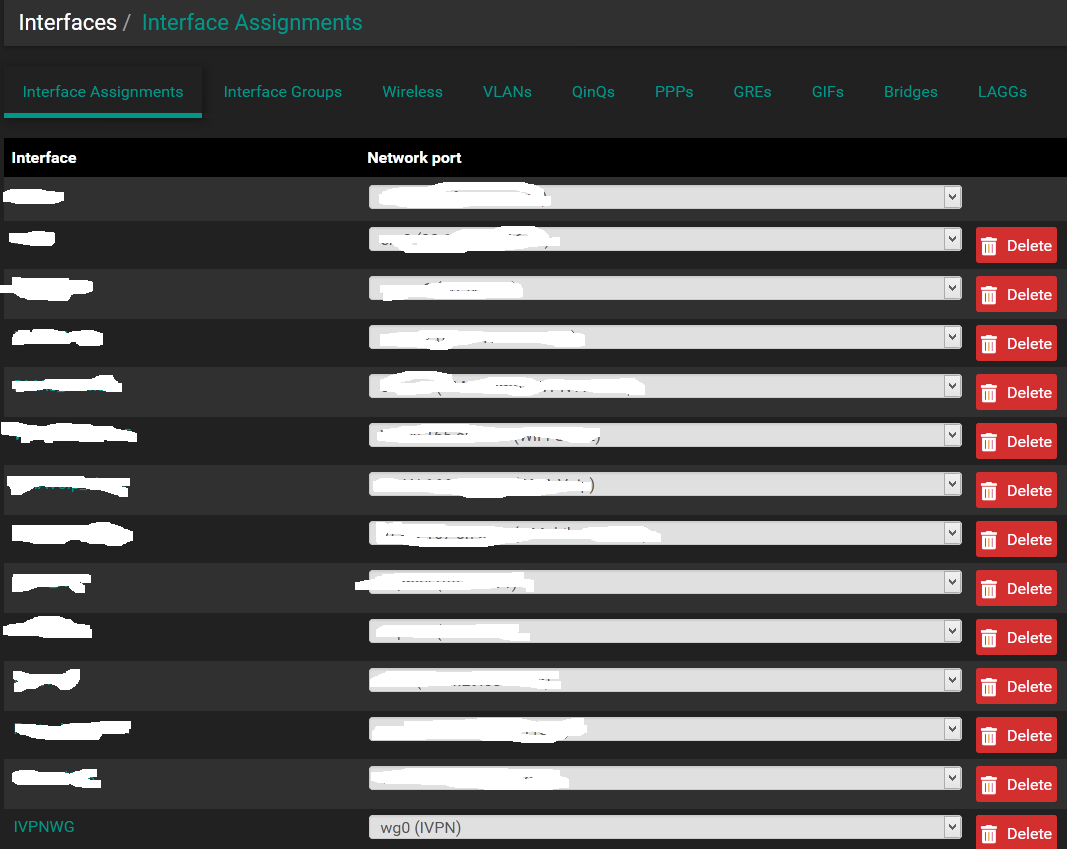
Assign the Wireguard VPN to an Interface as above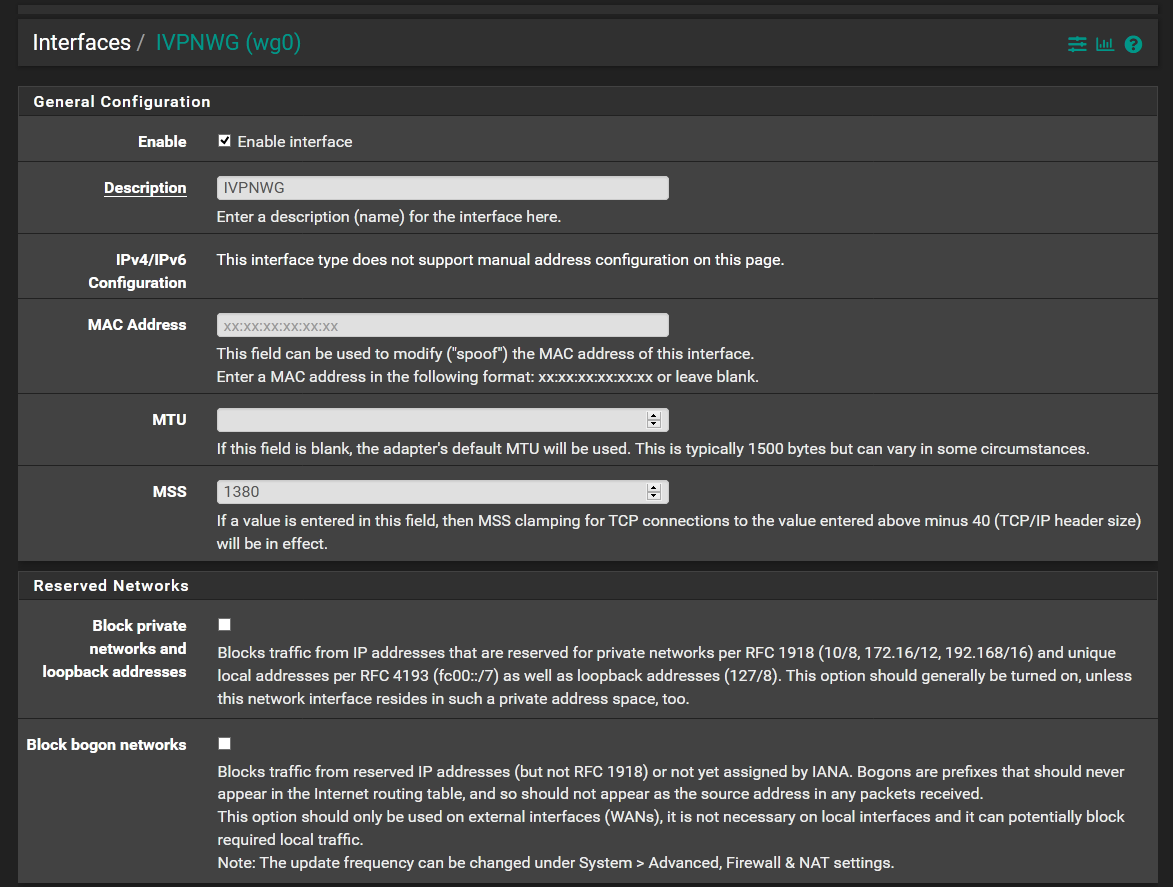
Set the MSS and enable the Wireguard VPN interface as above. I used this article as a guide on the MSS values https://www.netgate.com/blog/wireguard-in-pfsense-2-5-performance.html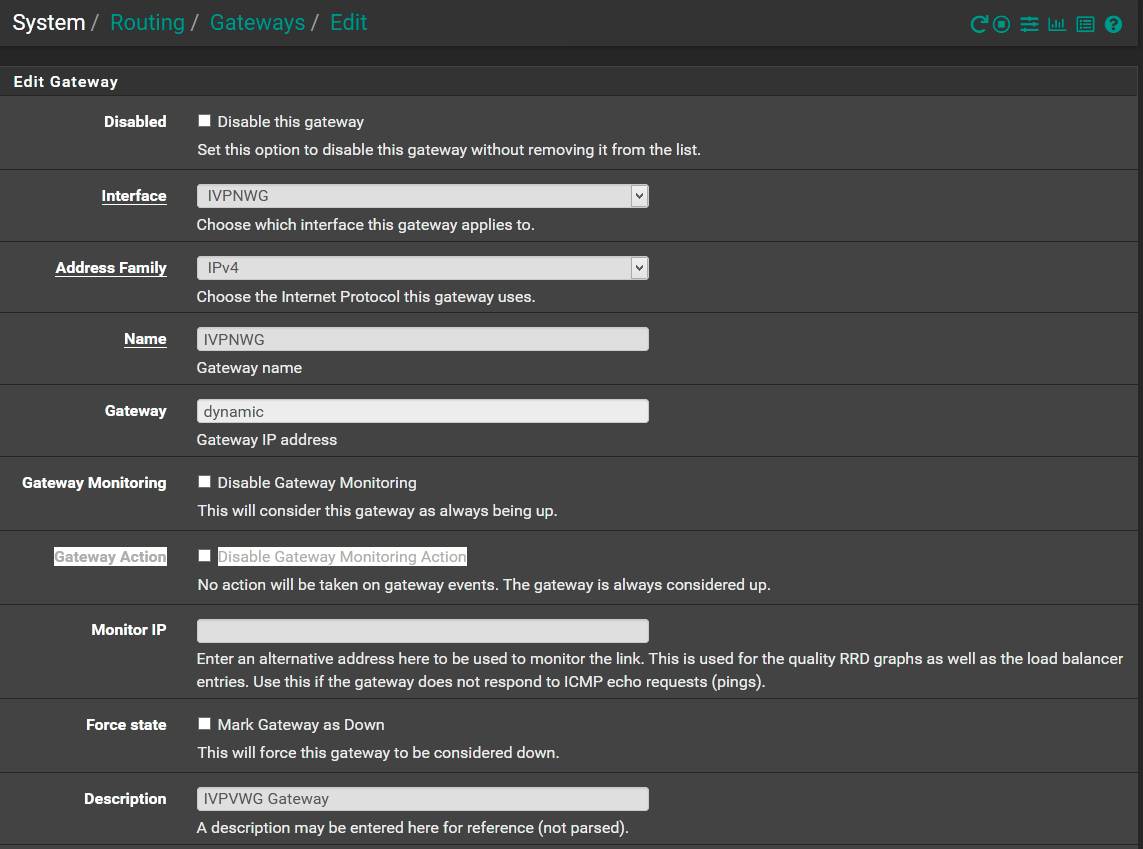
The Gateway settings are above.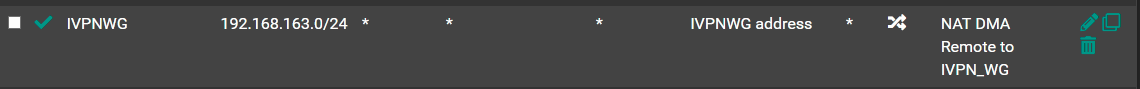
Create an Outbound NAT rule as above. The IP address is your network that you want to route through the VPN. If you have multiple subnets that you want to route through then create additional rules for them.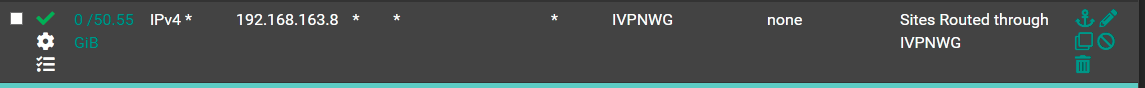
Lastly, create a firewall rule on whatever interface you want to route out through IVPN as above. In the example above I am routing one specific device 192.168.163.8 which is on my LAN out IVPN. So that rule is at Firewall/Rules/WAN.I basically fumbled my way into making this work. I am by no means any kind of expert on wireguard or pfSense. So if any of the guru's around here have any suggestions on improving what I've done I'd be very happy to hear it and continue learning.
I hope that helps!
-
They have released a setup guide yesterday - https://www.ivpn.net/setup/router/pfsense-wireguard/
-
@ab5g It does make sense and thank you so much for taking the time to explain.
@dma_pf what a great writeup thanks so much.@ab5g Certainly that page (which I have no idea how I missed it in my reading but sometimes it's wood for the trees...) does make things a little clearer but it does lead you to a very complicated order or interdependencies depending on your setup.
So I've had another go at this over the weekend and I finally succeeded. (@dma_pf as you can see I'd fumbled my way to this same config as well)
I went back and restarted the whole process again. I'll post here exactly how I go it working in case it helps someone else (same as @dma_pf though I'd written this before he posted). I am not saying this is either secure (I'm certain it can be locked down further) or needed (I still need to do testing to make 100% sure these are all actually needed) but it worked for me.
- I installed a fresh 2.5 from scratch and accepted all the defaults
- I installed only 2 interfaces, WAN and LAN on the command line then went through the formalities in the wizzard GUI
- I set up Wireguard under VPN. For my ISP I needed to:
- Obtain my allocated peer IP from my ISP (to do this I needed to generate my key pair in the Tunnel GUI, paste the public key to my ISP and get the IP back from them)
- Enter in the IP given to me by my ISP for my end of the tunnel into "address" (the port here is irrelevant as you never get incoming connections from your ISP)
- Set up my ISP peer endpoint - they will provide you with their public key, their peer IP and the port you connect out on
- Set allowed IP's to 0.0.0.0/0 (you can tie this down if you want to but this is what I did)
- Set Keep Alive to 30 (this seemed to be a good trade off)
- Go into Interfaces and assign wg0, name it and enable it
- Go into NAT, Outbound NAT, Manual, add both WAN and Wireguard IF with an any/any rule (you can remove any of the other rules or you can make this more secure by specifying the source)
- Go to FW Rules, LAN, new rule to end
- Source LAN net, any/any/any, advanced - Gateway = Wireguard VPN
- Go to FW Rules, Wireguard-IF, new rule
- Any/any/any/any default gw
- Routing - set WANGW as the default route
After this I had it working and I was sending traffic out via the VPN. I needed to make one further change to DNS configuration to ensure I wasn't leaking DNS but apart from that it's working.
Two things.
First as mentioned I need to go back through all the config and tighten things down. I know what I need to tighten down (like all the "any" rules) but right now I don't know what they're going to be (so for example what IP subnet source the wireguard interface sees for the rule - very quick and easy to check/work out but just need to check what it is)
Second upgrading my existing 2.4.5 to 2.5 and/or installing my 2.4.5 config backup onto a fresh 2.5 install broke both for Wireguard. I don't know what, how or why but all I know is WG didn't work. A fresh install with EXACTLY the same WG config worked but the exact same config on my existing FW didn't work.
EDIT
OK I've now been running this a few days and it's hardly stable. I definitely need to do yet more testing to figure out what I've done wrong or what's causing the instability. I have since added in my second WAN link back into the mix and I'm not sure if it's this that's messing everything up. I need to work on it a bit more when I get the time but there's definite progress.
Thank you all so much for adding to the post, your efforts are greatly appreciated.
G
-
@pfsenss said in WG not routing or sending traffic:
https://www.ivpn.net/setup/router/pfsense-wireguard/
Ah I hadn't seen that and a great find.
I will go through that now when I have a chance and make sure I've done it right.
Thanks again for spotting that.
G
-
Here's the latest update
OK I'm starting to get suspicious something is bugged.
If I go back to 2 interfaces (LAN and WAN) and set it up as I outline above it works and seems to work through reboots.
When I start to build on that config by adding another external gateway it stops working at some point (not sure when exactly yet but I will experiment further).
First "bug" is when you try and follow the guidance from iVPN. It tells you to set the MSS for the LAN interface to 1412 but you can't without fist assinging a static V6 address. This is because when you save the 1412 change, it fails claiming you get
"The Router Advertisements Server is active on this interface and it can be used only with a static IPv6 configuration. Please disable the Router Advertisements Server service on this interface first, then change the interface configuration."
Basically the default for RA is to have it turned on even if you've not actually assigned IPv6 to and interface. This means it errors if you assign a new value for MSS. So put in a false Static v6 ip (::1 works) and then you can get into DHCP RA and turn off RA. Back to interfaces and you can then change it to 1412.
Second but occurs some point after I add the second external gateway. Just adding the interface in VMWare, adding it under interfaces and then rebooting seemed to work fine. Then I made some DNS changes and it stops working. Nothing I then do works even if I back out those changes to the exact same spot where it was all working.
I can also see elsewhere other people are experiencing similar types of issues (such as PBR not working and traffic not working)
I will always look at my setup and config first before I start blaming anything else but at the moment I'm struggling to get anything that is even slightly stable and consistent even with a pretty simple config.
Going to keep working on it and updating this thread until I come up with the answer/solution.
Again thanks for those who've inputted so far.
G
-
@xxgbhxx said in WG not routing or sending traffic:
"The Router Advertisements Server is active on this interface and it can be used only with a static IPv6 configuration. Please disable the Router Advertisements Server service on this interface first, then change the interface configuration."
This is a bug, search the forums and you'll find it. The fix is:
-
Temporarily enable IPv6 on your LAN interface and set IPv6 Configuration Type to "Static IPv6", then assign it an IPv6 address ("::1" without quotes works with mask /128). Then Save.
-
Go to Services/DHCPv6 Server & RA/LAN/Router Advertisements then set Router Mode to "Disabled". Then Save.
-
Go back to the LAN interface and set IPv6 Configuration Type back to "None" then Save.
You should now be able to change the MSS value.
-
-
@dma_pf said in WG not routing or sending traffic:
@xxgbhxx said in WG not routing or sending traffic:
"The Router Advertisements Server is active on this interface and it can be used only with a static IPv6 configuration. Please disable the Router Advertisements Server service on this interface first, then change the interface configuration."
This is a bug, search the forums and you'll find it. The fix is:
-
Temporarily enable IPv6 on your LAN interface and set IPv6 Configuration Type to "Static IPv6", then assign it an IPv6 address ("::1" without quotes works with mask /128). Then Save.
-
Go to Services/DHCPv6 Server & RA/LAN/Router Advertisements then set Router Mode to "Disabled". Then Save.
-
Go back to the LAN interface and set IPv6 Configuration Type back to "None" then Save.
You should now be able to change the MSS value.
I did search I didn't find it.
I posted the same fix above (I'd worked it out by myself, go me!)
Thanks for the update though
G
-
-
@xxgbhxx Can I make the suggestion of posting screenshots of your port forward, outbound NAT, WAN, LAN & WG rules? I'll be happy to look at them and compare them with my set up which is working.
-
@dma_pf said in WG not routing or sending traffic:
@xxgbhxx Can I make the suggestion of posting screenshots of your port forward, outbound NAT, WAN, LAN & WG rules? I'll be happy to look at them and compare them with my set up which is working.
Thank you so much for your kind offer I will do so this weekend. With 2 interfaces it's "working" at the moment and has been for 72 hours so I need to snapshot that then make the chanages with the third interface until it breaks so I can get a comparison up.
G
-
@dma_pf
Ok I've spent an hour going through this this morning. What I have found is simply adding the third interface breaks it.As I mentioned, I've had it running 3 days with only 2 interfaces and it has continued to work without issue. This is what is shown in the various screenshots for the WORKING config. I will follow these with the changes that broke the config. (by the way there's no port forwarding as the remote is the VPN provider who never initiate and inbound connection)
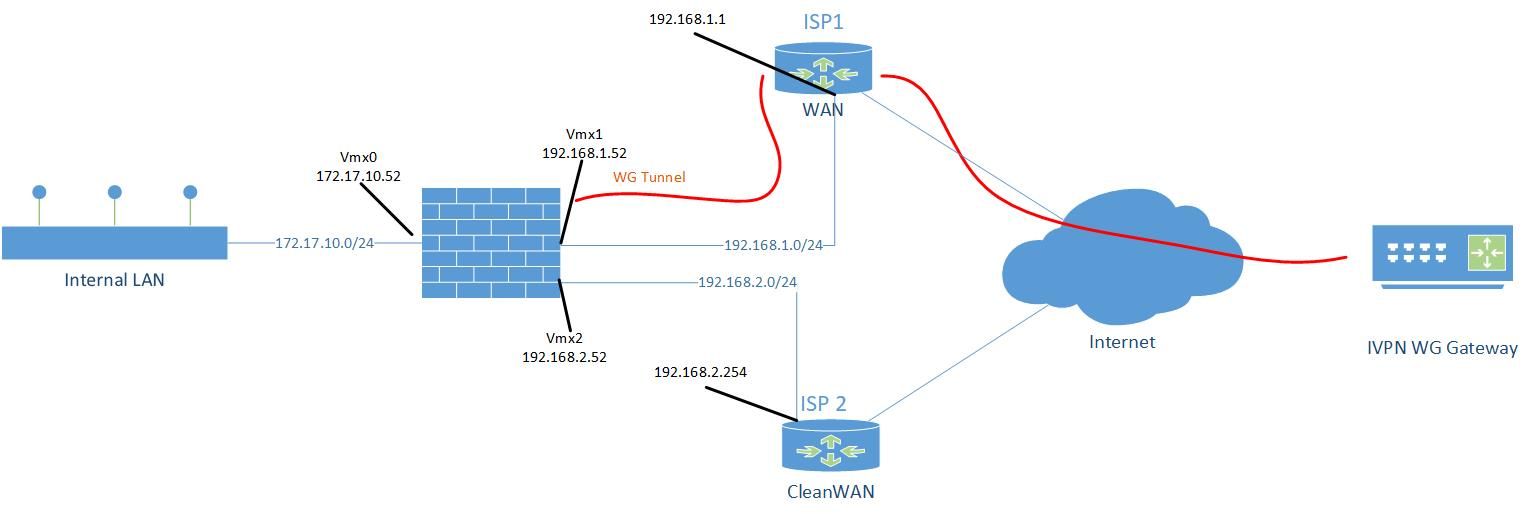
Architecture Network Diagram
Working DNS
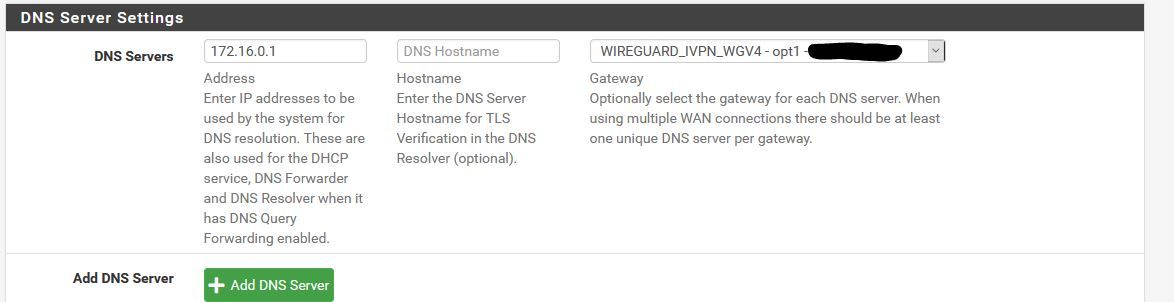
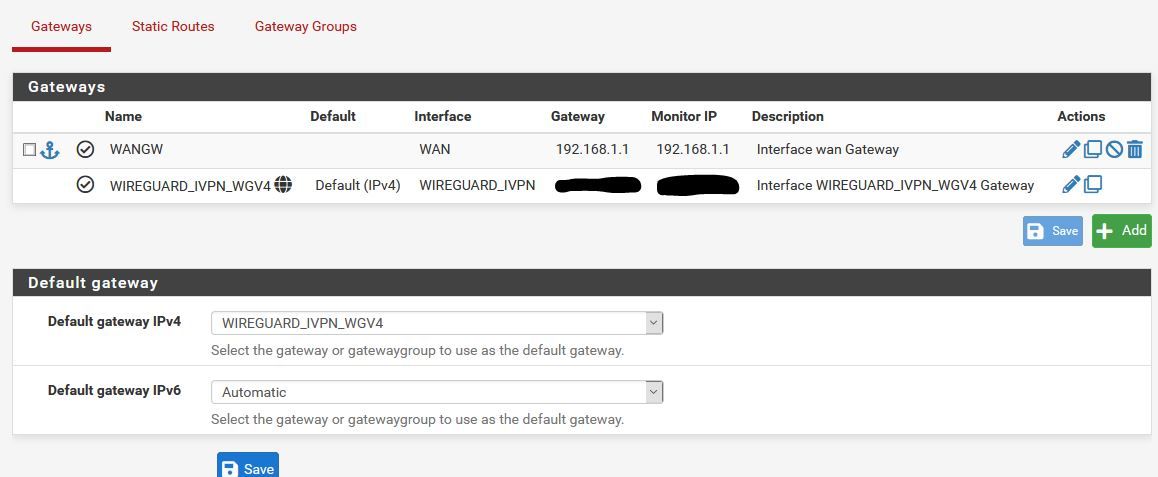
Working Gateway
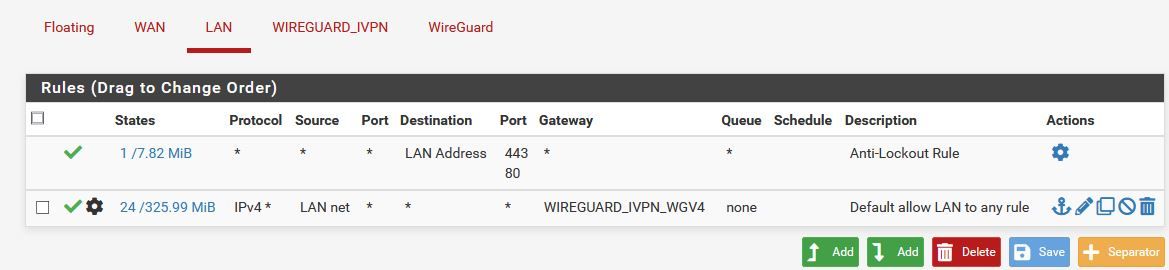
Working LAN FW Rules
Working VPN Firewall Rule
Working WAN Firewall Rule
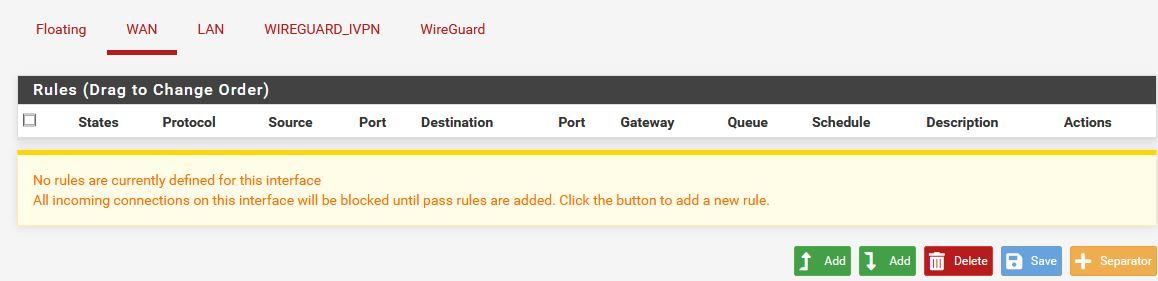
Working Outbound NAT
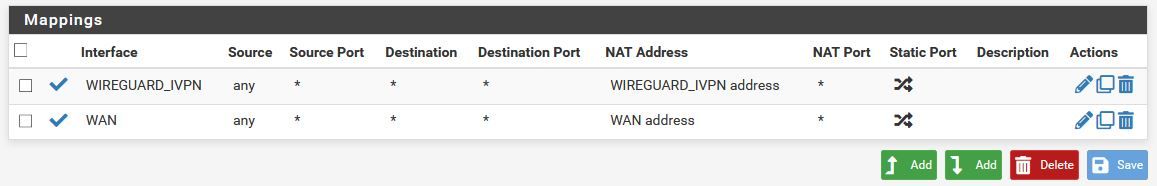
Working WG Tunnel Rule
Working WG Peer Rule
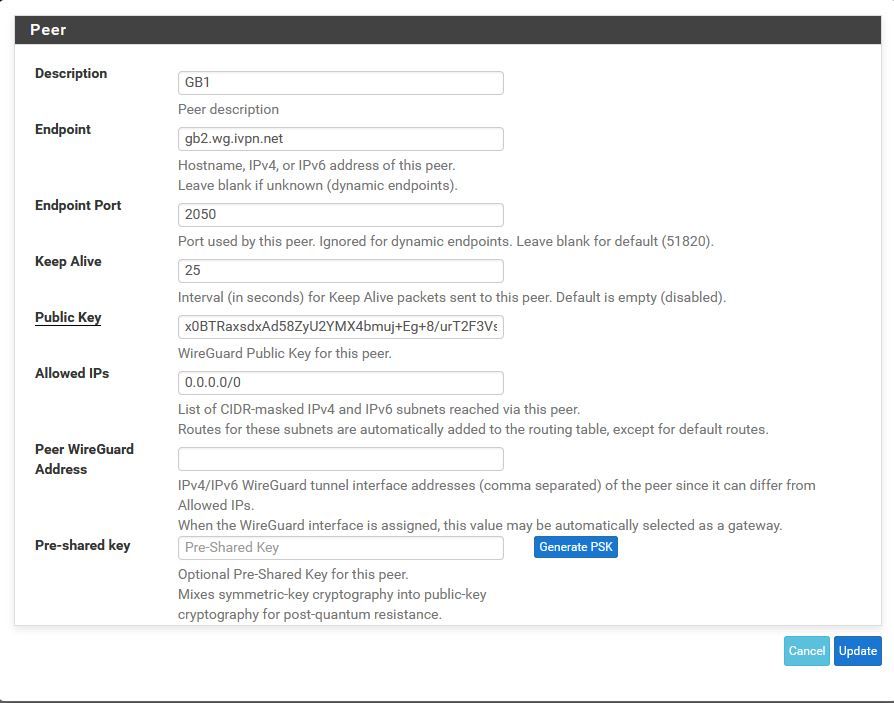
So this is where it has been for the past 72 hours. Everything has been working perfectly fine (though to be fair I only have a single machine testing this but ever time I've gone to check it's worked without a problem).
I then did the following
In VMWARE
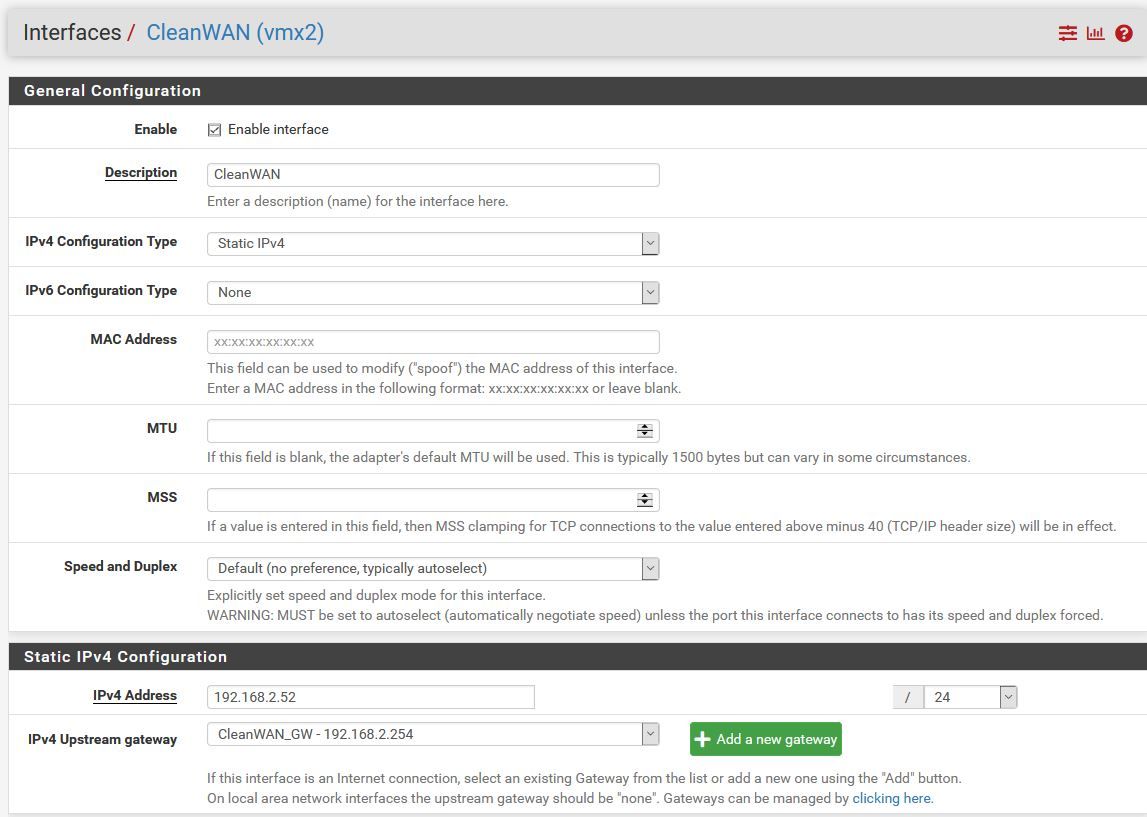
Add new "physical" Interface on the network of my other Internet connection (VMX2)In PF
- Interfaces add new interface VMX2
- Interfaces OPT2
-- Description "CleanWAN"
-- Static IPv4
-- Address 192.168.2.52/24
-- Add a new gateway
-- Gateway Name "CleanWAN_GW"
-- Gateway IP 192.168.2.254
-- Gateway Description "Clean Internet Feed" - Enable Interface
Then "Apply Changes"
Without touching or doing anything else at this point I reboot to check everything is working and it no longer does.
NOT Working Gateway
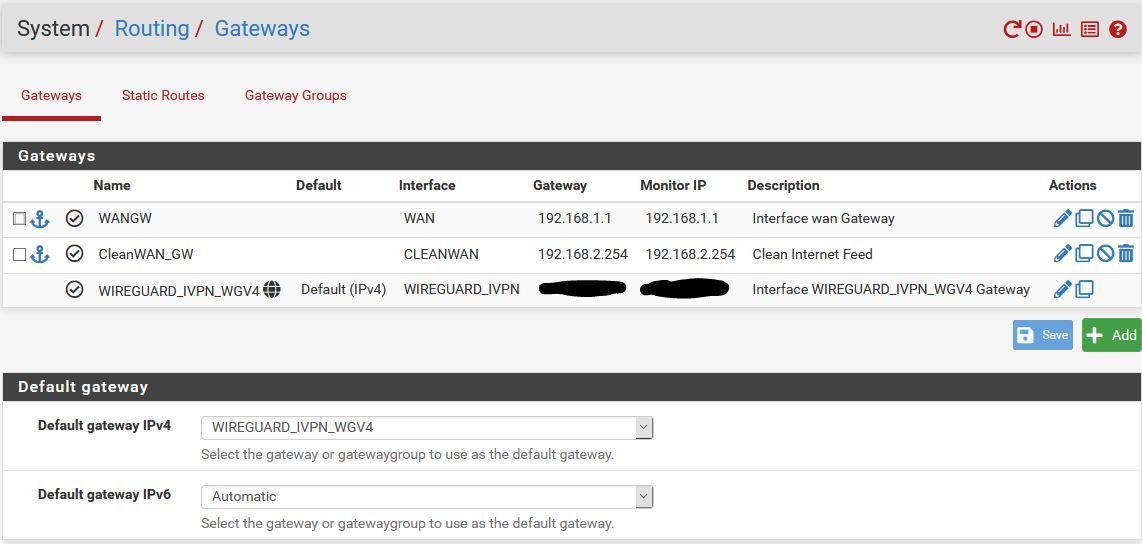
NOT Working CleanWAN Interface
Absolutely nothing else in the setup has changed or has been touched at this point. Unless I'm missing something fundamental (which I might be!) there is absolutely no reason this should stop working at this point.
I can always instantly tell if it's stopped working because the dashboard shows unable to tell if there's an update
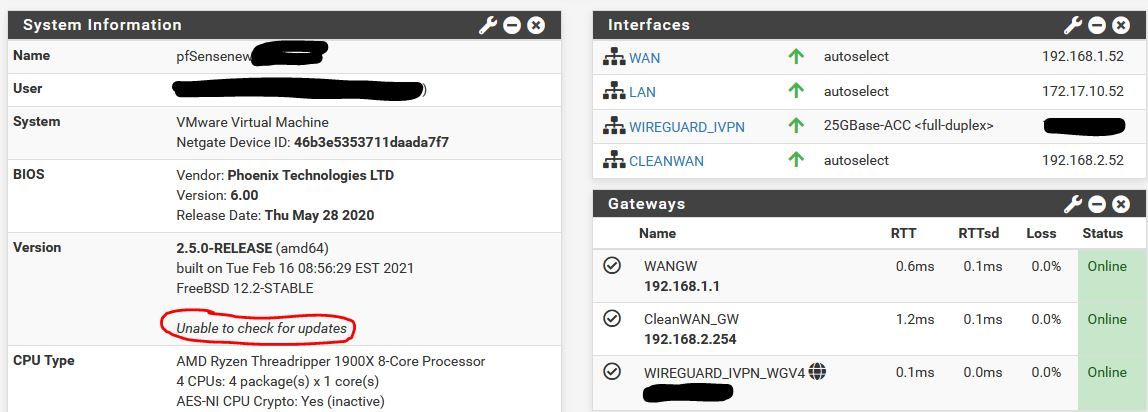
Another point to note is that it continues to work right up until the point I re-boot. So the changes I apply to enable VMX2 and the CleanWAN interface work until I reboot which I think is why I've been confused/unsure what's been causing it.
So where do I go from here?
G
-
@xxgbhxx Thanks for your last post. I'm a little bit confused so hopefully you can answer a couple of questions. So here they are:
-
In the Architecture Network Diagram you have ISP1 and ISP2. Are these 2 actually different ISP's with unique IP addresses out to the internet? Can you describe their connection out to the net (cable, fiber, wireless, etc.)?
-
In the Architecture Network Diagram are Vmx1 and Vmx2 both virtual adapters? Are they bound to the the same physical NIC? If so are they bound to the same port on the NIC? How many ports are on that NIC?
-
Is pfSense installed virtually and hosted by Vmware? Are both Vmx1 and Vmx2 devices configured within the pfSense virtual machine settings?
-
How are you planning to determine what needs to go out to either Vmx1 or Vmx2? (certain devices, particular destinations, failover, etc.)
-
-
-
Yes they are completely different ISP's on completely different equipment (actually two completely different companies) with completely unique IP's on the internet. They're both Fibre to the Cabinet (FTTC) connections that come into the house on copper. They are even completely different piece of copper.
-
Yes Vmx0, 1 and 2 are three completely different virtual adapters. They are bound to the same NIC but it's a quad port NIC so each virtual network is on it's own physical port. It's a direct 1 to 1 connection.
-
Yes pfSense is VMWare hosted (and I've been running it in this config for 10 years). Vmx1 and 2 are virtual NIC's assigned to this VM in VSphere. Those two NIC's are on two virtual switches in VMware. Each switch is assigned a different physical uplink. One uplink is plugged into one ISP router, the other uplink is plugged into the other router.
-
As you can see from the rule above, it's set to send all LAN traffic to that interface. For the CleanWAN interface/connection, within pfBlocker I create alias which maps the ASN's for Netflix and Amazon Prime to a single Alias called "Clear_Connect". Once that's done I then put a new PBR rule above that LAN one for all IP's in those ASN's to route on the clear interface. This is how I've been using PF for the past 10 years with OpenVPN on he same ISP.
G
-
-
@xxgbhxx You default gateway IPv4 cannot be WIREGUARD_IVPN_WGV4. Set it to WAN and reboot / restart the WireGuard tunnel. It should start working then
-
The VPN providers own guide says to set it to the WG interface as do many other guides.
Can't look past it was working with 2 interfaces set to that. Are you suggesting that adding that thirsd interface means I can't leave it set to the WG interface?
Either way I've just tried it and it made no difference so I don't think it's that.
Thanks for the suggestion though.
G
-
@xxgbhxx - The default gateway should is for your entire system, I'm comfortable in having it set to the WAN links and then use policy based routing for the source IP's that I want to use the tunnel.
With default gateway for the system set as 'WIREGUARD_IVPN_WGV4' - you are telling the system to use it for everything. When the tunnel goes down - it may render things unreachable. Anyways, I've seen more predictable performance when not seeing the default gateway to the 'WIREGUARD_IVPN_WGV4'.Also from the Netgate docs
"Before assigning the interface, make sure default gateway for the firewall is not set to Automatic or the firewall may end up using the wg interface as the default gateway, which is unlikely to be the desired outcome. "You can delete the WG interface, reboot once - then set the default GW to WAN and then add the WG interface. After this add a route in LAN to match source host that you want to send over the tunnel.
-
@ab5g said in WG not routing or sending traffic:
@xxgbhxx - The default gateway should is for your entire system, I'm comfortable in having it set to the WAN links and then use policy based routing for the source IP's that I want to use the tunnel.
With default gateway for the system set as 'WIREGUARD_IVPN_WGV4' - you are telling the system to use it for everything. When the tunnel goes down - it may render things unreachable. Anyways, I've seen more predictable performance when not seeing the default gateway to the 'WIREGUARD_IVPN_WGV4'.Also from the Netgate docs
"Before assigning the interface, make sure default gateway for the firewall is not set to Automatic or the firewall may end up using the wg interface as the default gateway, which is unlikely to be the desired outcome. "You can delete the WG interface, reboot once - then set the default GW to WAN and then add the WG interface. After this add a route in LAN to match source host that you want to send over the tunnel.
As I see it you have 2 choices
- EVERYTHING goes VPN and PBR stuff on WAN that doesn't
- EVERYTHING goes WAN and PBR stuff on VPN that doesn't
You're suggesting 2 I've configured 1.
Either way it shouldn't matter, both should work. Option 1 DID work when I only had 2 interfaces.
For my system everything DOES go down the VPN except for a small subset of streaming services that don't allow VPN. I've not set up that PBR yet (but it's what @dma_pf was asking in question 4 above). Right now I'm not worried about that PBR bit.
Anyway, I did as you suggested. I deleted the WG interface and rebooted. I set the default GW to WAN and then re-added the WG interface. I then re-added the WG FW rule any/any and I've left the same LAN rule as above that tells all LAN traffic to use the tunnel. That didn't work.
I don't think it's anything to do with the way I've done it. I just don't think it's working as intended. There's indications that there's something "wrong" with PF and WG as theres another thread on PBR with two interfaces not working as instended/expected.
Keep the suggestions coming happy to try anything at this point.
G
-
@xxgbhxx said in WG not routing or sending traffic:
As I see it you have 2 choices
- EVERYTHING goes VPN and PBR stuff on WAN that doesn't
- EVERYTHING goes WAN and PBR stuff on VPN that doesn't
I've always used option 2. I've got interfaces for 2 native networks, 4 vlans a site-to-site OpenVPN tunnel, and 3 Wireguard connections to IVPN. My Default Gateway IPv4 is set to WAN_DHCP and the Default Gateway IPv6 is set to None. I then policy route my traffic either out the WAN or through IVPN (Wireguard) in rules per each interface.
In PF
Interfaces add new interface VMX2
Interfaces OPT2
-- Description "CleanWAN"
-- Static IPv4
-- Address 192.168.2.52/24
-- Add a new gateway
-- Gateway Name "CleanWAN_GW"
-- Gateway IP 192.168.2.254
-- Gateway Description "Clean Internet Feed"
Enable InterfaceThen "Apply Changes"
Without touching or doing anything else at this point I reboot to check everything is working and it no longer does.It seems very strange that just adding an interface would make the others not work. I'm assuming you've tried to ping out to the internet (8.8.8.8 and google.com) with a Source Address of WAN, Wireguard_IVPN and CleanWAN? Do you any get responses?
-
@dma_pf said in WG not routing or sending traffic:
@xxgbhxx said in WG not routing or sending traffic:
As I see it you have 2 choices
- EVERYTHING goes VPN and PBR stuff on WAN that doesn't
- EVERYTHING goes WAN and PBR stuff on VPN that doesn't
I've always used option 2. I've got interfaces for 2 native networks, 4 vlans a site-to-site OpenVPN tunnel, and 3 Wireguard connections to IVPN. My Default Gateway IPv4 is set to WAN_DHCP and the Default Gateway IPv6 is set to None. I then policy route my traffic either out the WAN or through IVPN (Wireguard) in rules per each interface.
In PF
Interfaces add new interface VMX2
Interfaces OPT2
-- Description "CleanWAN"
-- Static IPv4
-- Address 192.168.2.52/24
-- Add a new gateway
-- Gateway Name "CleanWAN_GW"
-- Gateway IP 192.168.2.254
-- Gateway Description "Clean Internet Feed"
Enable InterfaceThen "Apply Changes"
Without touching or doing anything else at this point I reboot to check everything is working and it no longer does.It seems very strange that just adding an interface would make the others not work. I'm assuming you've tried to ping out to the internet (8.8.8.8 and google.com) with a Source Address of WAN, Wireguard_IVPN and CleanWAN? Do you any get responses?
It's just a consequence of my simple setup. 99% of my traffic goes via VPN so it makes sense to me that's the default.
Yes it's strange, hence why I'm so confused. Right now, in it's broken state when I go to a command prompt on the firewall
No Interface Specified
8.8.8.8 no response
1.1.1.1 no response
192.168.1.1 (Internet gateway) responds
google.com (doesn't resolve as the DNS is the other side of the WG connection)Specify WAN (192.168.1.52)
8.8.8.8 responds
1.1.1.1 responds
192.168.1.1 responds
google.com no response (can't resolve)Specify Wireguard_IVPN (172.26..)
8.8.8.8 no response
1.1.1.1 no response
192.168.1.1 responds
google.com no response (can't resolve)Specify CleanWAN (192.168.2.52)
8.8.8.8 responds
1.1.1.1 responds
google.com no response (can't resolve)Perhaps the interesting one for me is the fact that using wg0 as the source interface it gets a response from the WAN gateway. I wouldn't expect the tunnel to be able to see that IP as it's on a completely different subnet range. The firewall has to be rooting somehow but I'm not quite sure how/why.
But apart from that it's pretty much responding as I'd expect. DNS doesn't work as it's not contactable through the VPN. Bypassing the VPN means everything you'd expect to be contactable is contactable.
I'm really at a loss. I am looking at a number of the other posts on this forum though and it's clear that WG isn't probably production ready yet. There's a number of people seemingly having a lot of "odd" behaviour, especially with multiple connections. If I hadn't built from complete scratch I'd put it down to some legacy issue with my existing firewall but this is a brand new 2.5 build with absolutely zero other config on it before hand. You're absolutely right, it should break just by adding an interface and yet, here we are.
Thanks again for your effort it really is hugely appreciated.
G
-
@xxgbhxx said in WG not routing or sending traffic:
Specify Wireguard_IVPN (172.26..)
8.8.8.8 no response
1.1.1.1 no response
192.168.1.1 responds
google.com no response (can't resolve)Try changing the Endpoint Address of the IVPN Peer from gb2.wg.ivpn.net to its actual IP address of 185.59.221.225 and repeat this test.
-