Is it possible to resolve DNS via WireGuard interfaces?
-
Thankfully switching from OpenVPN to WireGuard was trivial in my situation, but I noticed something that I find odd:
I was using OpenVPN interfaces to do policy based routing. I selected those interfaces for unbound's "Outgoing Network Interfaces". This resulted in tests like the one you can find on dnsleaktest.com showing the IP addresses of the OpenVPN servers I was connected to.
Now I've replaced those OpenVPN interfaces with WireGuard interfaces. That works fine in terms of policy based routing. Of course I selected them as "Outgoing Network Interfaces" for unbound, too. I don't remember changing any other settings. However, taking the same test at dnsleaktest.com now shows the IP address of the WAN interface. The WAN interface is not selected in "Outgoing Network Interfaces".
Is this expected behavior?
Thanks!
-
Yes, it is possible. You may need to restart Unbound after setting up Wireguard, but I have done that and my phone is able to successfully resolve using the IP addresses (v4 and v6) of the pfSense end of the Wireguard connection.
-
@virgiliomi Weird, even after a couple reboots, I just can't get it to work.
Here's a short video I made demonstrating the "issue" (still not sure if it's even supposed to work the way I had imagined and described in the first post):
Youtube Video -
I still haven't found a solution to this problem and I do believe it's a bug, since the behavior is different when using OpenVPN instead of WireGuard. In short:
- Selecting OpenVPN interfaces as "Outgoing Network Interfaces" will make unbound resolve DNS using the OpenVPN interfaces.
- Selecting WireGuard interfaces as "Outgoing Network Interfaces" will make unbound resolve DNS using the WAN interface.Rebooting didn't help. Recreating the WireGuard interfaces didn't help. Reinstalling didn't help. Updating from 2.5.0-RELEASE to 2.6.0.a.20210307.0100 didn't help.
I've checked
var/unbound/unbound.confand below# Outgoing interfaces to be usedthere are the IP addresses of the WireGuard interfaces, which is why I expect "DNS leak" tests like the aforementioned dnsleaktest.com to show the IP address of the other end of the tunnel. Again, this is the case when using OpenVPN instead of WireGuard. -
@manatee Have you checked that the client you are testing is not setting it's own DNS server? I would look on that machine's settings to make sure that it points to pfsense as its DNS server. Also, check the DHCP server settings in pfsense to make sure that that the client is also being directed to use pfsense and does not point to a different DNS server.
I can confirm that it should work correctly. I can route my DNS requests out via my VPN provider and the dnsleaktest.com results shows the requests coming from my VPN provider's servers. My WAN ip address is not disclosed.
-
@dma_pf I can reproduce the issue I describe on all of my clients. None of the clients have a different DNS server address set.
The IPv4 address of the pfSense installation is the only configured DNS server address under
DNS serversin the DHCP server settings. (IPv6 isn't used in my network, as per disabledAllow IPv6setting.)These are the only DNS related rules I've configured:
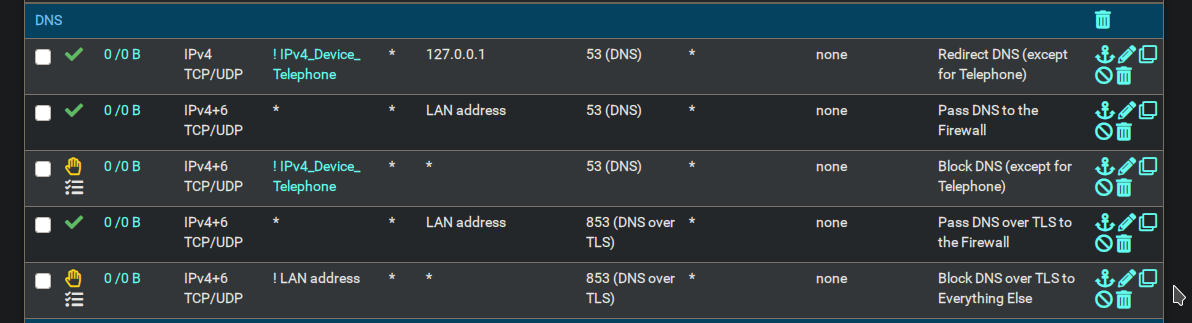
With these rules I meant to implement this. They should in theory prevent clients (except the VoIP DECT base station) from using any other DNS server besides the DNS resolver running on pfSense. Disabling these rules had no effect on the issue described, so I omitted them from previous posts in this thread.Again, I can't recall making any changes to any settings (DHCP, DNS resolver, rules, ...) when switching from using OpenVPN to WireGuard for my VPN needs, besides actually switching from OpenVPN interfaces to WireGuard interfaces and changing
Outgoing Network Interfacesof the DNS resolver settings. When reverting to OpenVPN tunnels, assigning interfaces and changing the aforementioned DNS resolver setting, the actual test portion of dnsleaktest.org shows the OpenVPN servers IP addresses once again. -
@manatee Thanks for the DNS rules postings in your last post. They basically look the same as my settings.
I am also using Unbound (with out Forwarding) through out my network. I was looking at your video again and noticed a difference between your setup and mine in Services/DNS Resolver/General Settings. In my setup I have "Network Interfaces" set to All. I figured I'd test my setup with the setting set to LAN to see if it would duplicate your results. But when I tried to change the setting I was presented with this:
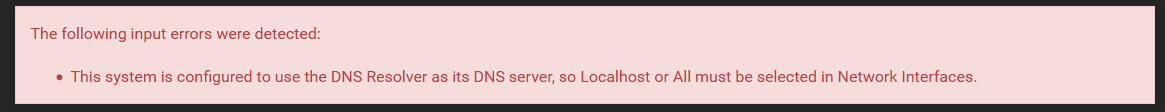
If you look at the article regarding DNS redirection that you linked to in your last post it also says:
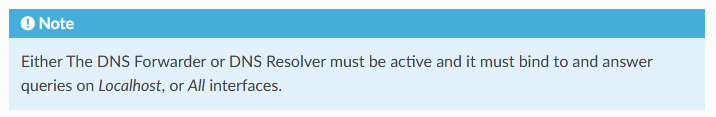
Hope this helps.
-
@dma_pf Thanks again for your reply!
Unfortunately I think you might have confused
Network InterfacesandOutgoing Network Interfaces!
I didn't show it in the video, because it shouldn't make a difference, but I do have
LANandLocalhostselected asNetwork Interfaces(for responding to queries from clients). If I hadn't, I'd receive the error message you posted a screenshot of.However, I only have the WireGuard interfaces selected as
Outgoing Network Interfaces(that the DNS Resolverwillshould use to send queries to authoritative servers and receive their replies). Yet unbound will still use theWANinterface, as if it were selected for the latter setting, which it definitely is not. I havedoubletriplequadruple checked.I've even reinstalled pfSense from scratch, on a new SSD. I configured it without restoring settings from a backup. I only set up what was necessary to get me connected to the internet and the WireGuard interfaces. This didn't fix the issue either. At this point I genuinely wonder if I have somewhat of a "one in a million" configuration/environment that triggers this issue or if people who are affected by this issue simply don't know (or care) that they are.

-
@manatee Just wanted to let you know that I stumbled across this post because I am having the issue as well. Nothing new to add but with OpenVPN DNS resolves through OpenVPN servers, but when I try to make Wireguard my Outgoing Network Interface in my DNS resolver, it seems to be failing all together. Did you ever get yours working or are you just using OpenVPN?
-
@bearded_beef +1 any resolution.?
-
@cjangrist @Bearded_Beef @Manatee
Well, time to give something back :) registered just to try & provide a solution...
I had the same issue; PFsense with Wireguard and trying to use DNS resolver to send all queries through the Wireguard interface. Connectity was OK, but DNS would fail to resolve for clients on the LAN. When trying nslookup from a LAN client:
** server can't find domain.com: REFUSEDIt seems you need to create an Unbound DNS resolver Access List:
Services -> DNS Resolver -> Access Lists -> new Access List
Access List Name: WireGuard
Action: Allow
network: add your LAN & Wireguard networks here- YOUR ASSIGNED WIREGUARD PEER IP (the one that is put on the OPT interface)
- ANY LAN Network behind pfsense you want to use, I used a /16 supernet here to collect all my LAN networks
Apply (and perhaps reboot) and everything started working for me...
Hopefully this helps someone, good luck :)Greets,
Junta
-
@JuntaSense thank you so much - this did it!
-
L LaUs3r referenced this topic on