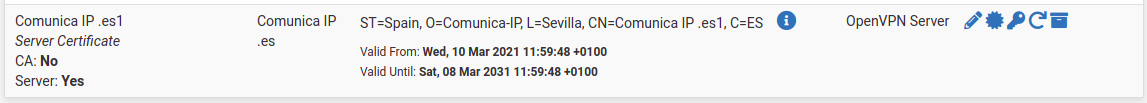
How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?
-
@jimp I am checking in a testing environment the renew certificate option in pfSense 2.5.0.
The CA Certificate renew, apparently, it does success.
The User Certificate renew, apparently, it does success.
But when I try renew the Server Certificate used by the OpenVPN server the following error is displayed:
And I can't renew the Server Certificate used by the OpenVPN Server.
What could it be?
Best regards
-
I'm not aware of what might cause that general error. There may be some aspect of the certificate that is deprecated or no longer supported in OpenSSL for new certs. Hard to say without more details.
-
@jimp What more details do you need know about the server certificate?
The certificate were created in pfSense 2.4.5-p1, in the proccess of create the OpenVPN Server, before update to pfSense 2.5.0.
Regards
-
@ramses-sevilla
Aren't these valid like 'ten years' or so ?
See my image above. -
Yes, this server certificate is valid for ten years but I am testing the renew certificates option that has been introduced in pfSense 2.5.0 and I can renew de CA Certificate and the User Certificate but when I try to renew the OpenVPN Server Certificate the following error is displayed:
And I don't know why.
Best regards
-
@ramses-sevilla
Just a guess, but have you tried disabling the server before renewing the certificate? -
@ramses-sevilla said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
Yes, this server certificate is valid for ten years but I am testing the renew certificates option that has been introduced in pfSense 2.5.0 and I can renew de CA Certificate and the User Certificate but when I try to renew the OpenVPN Server Certificate the following error is displayed:
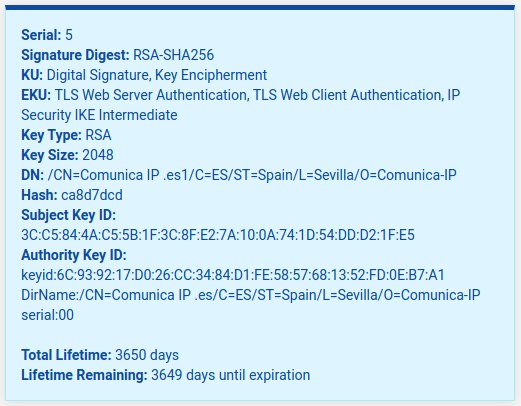
Can you share the details of the certificate as shown in the GUI list and info box (click the "i" icon)? Nothing I have tried has resulted in that error.
@provels said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
@ramses-sevilla
Just a guess, but have you tried disabling the server before renewing the certificate?That's not necessary, the renewal process will restart servers using the certificate afterward.
-
-
I have renewed all kinds of certificates, server and otherwise, in 2.5 and they all work for me. Which leads me to believe it's something in your certificate data triggering the problem.
Can you try adjusting the CN so it doesn't have a space in it?
Not that it should be a problem but typically that's a short name or hostname and not a string like that. I can't recall if I tested that sort of value.
-
It's definitely the space in the CN doing it. I can reproduce that here:
-
To adjust the CN I need create a new certificate, isn't it?
I can't modify the CN of the Server Certificate, isn't it?
The CA has space in the CN and renews the certificate without problem.
I have created a new certificate without spaces in the CN and renews fine.
Will the problem be solved?
Best regards
-
@ramses-sevilla said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
To adjust the CN I need create a new certificate, isn't it?
Yes, but since it's a server certificate which doesn't need to be sent to clients, that's typically easy, make a new cert, pick it to be used as the server cert, and that's it.
I can't modify the CN of the Server Certificate, isn't it?
Correct.
The CA has space in the CN and renews the certificate without problem.
That's expected as a CA is a different type of entry from a certificate, certificates have a lot more data in them and a lot more to go wrong.
Will the problem be solved?
Yes, I tracked it down further and the real problem is a lack of SAN entries in the certificate. Normally it will take the common name and add that as a SAN entry, but in these cases that kind of common name cannot be a valid SAN entry. The SAN list ends up empty since there are no manual entries nor the entry for the CN. The certificate renewal code was assuming all certificates have a SAN, which in these cases is not true.
You can install the System Patches package and then create an entry for
09d3fe621a56292817a85a54916e8b99e2b26c00to apply the fix. With that fix applied, you can renew certificates with spaces or x509-escaped characters in their CN which lack SANs. -
I have applied the patch and now I can renew the Server Certificate fine in my testing environment.
I have the production environment with a cluster in pfSense 2.4.5-p1. I had thought update to pfSense 2.5.0 because I need renew CA, Server and User Certificates but I have seen in the forum that the update to pfSense 2.5.0 break some services (Hardware, IPsec, DHCP Relay,...) that I have configured in my environment.
I have some doubts:
-
Do you recommends me wait to the next pfSense version?
-
Will all patches be included in the next version?
-
How long will it take to get out the next version?
-
Can I renew a Certificate without problems if It has expired?
Best regards
-
-
@ramses-sevilla said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
Do you recommends me wait to the next pfSense version?
That's up to you.
Will all patches be included in the next version?
This fix will be, but not every single commit that's happened recently. Primary focus is on fixing regressions and other important behavior that isn't functioning properly.
How long will it take to get out the next version?
Not too long, but we don't have a firm ETA. Sometime in the next few weeks, most likely.
Can I renew a Certificate without problems if It has expired?
Yes, though if you wait until it expires, it may be rejected by clients after it expires.
You could renew the certificate on a 2.5 lab system and then copy the certificate back over into the older configuration and use it there in the meantime.
-
Well, recopiling...
I have a pfSense 2.4.5_1 cluster with OpenVPN Server in production.
This pfSense have:
Certificate Authorities --> ca-prod-1 --> Valid from: 23 Apr 2020 --> Valid Until: 21 Apr 2030 (Internal) --> OpenVPN Server
Server Certificate (OpenVPN) --> srv-prod-1 --> Valid from: 23 Apr 2020 --> Valid Until: 21 Apr 2030
User Certificate --> usr-prod-1 --> Valid from: 23 Apr 2020 --> Valid Until: 21 Apr 2030
To renew the Expiration Date of the Certificates, I need:
-
First.- I need renew the Expiration Date of the Certificate Authority. I don't need send nothing to the OpenVPN Client nor modify nothing in the OpenVPN Server and everything will continue working fine. Right?
-
Second.- I need renew the Expiration Date of the Server Certificate. I don't need send nothing to the OpenVPN Client nor modify nothing in the OpenVPN Server and everything will continue working fine. Right?
-
Third.- I need renew the Expiration Date of the User Certificates. I need resend each renewed certificate to the user. Right?
- Doubts:
If expires the Expiration Date of the User Certificate, can I renew and send the renewed certificate later?.
What would happen if the Certificate Authoritie expires?. Would everything still working?. Can I renew the Certificate Authoritie later?
What would happen if the Server Certificate expires?. Would everything still working?. Can I renew the Server Certificate later?
Best regards
-
-
@jimp thanks so much by your answers.
I have other issues renewing Certificates.
When I create a new User and I check the option of create Centificate, I select this options:
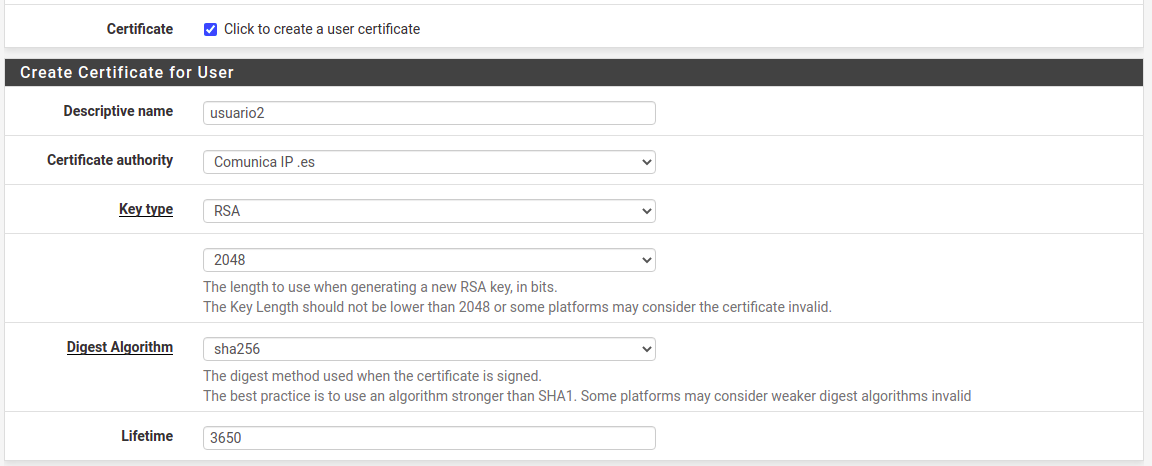
If I go to "VPN > OpenVPN > Client Export" the new User appear to export it:
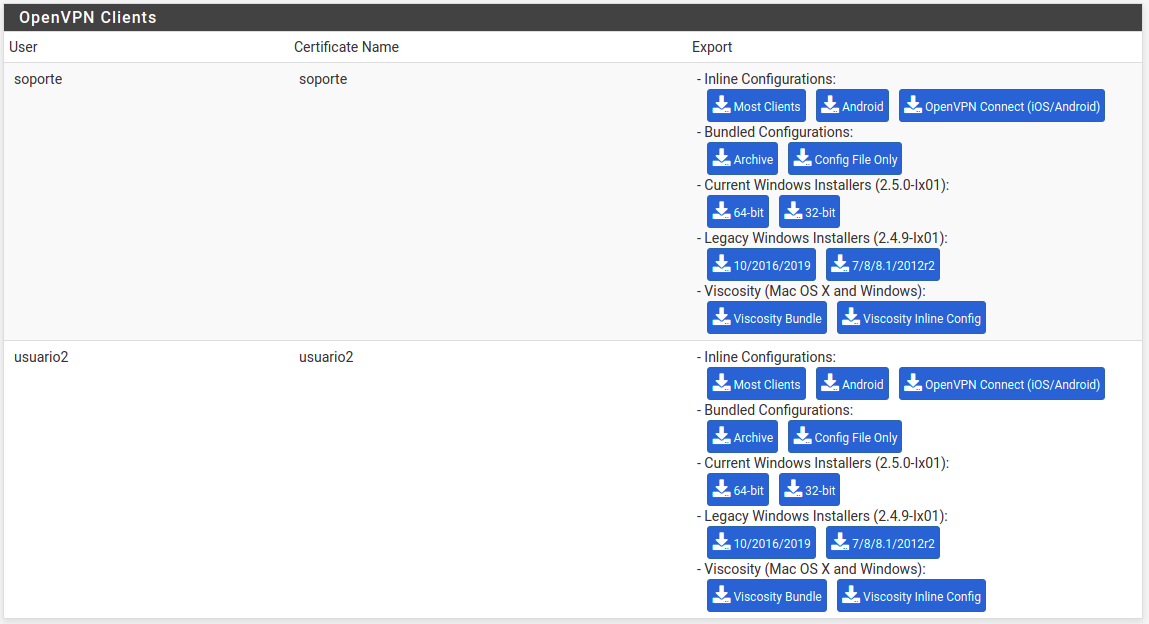
Well, if I try renew the Certificate of the new User (usuario2) it shows this:
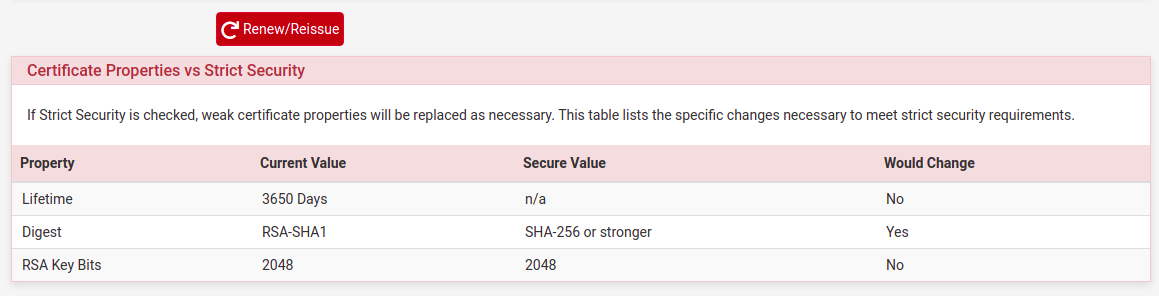
But I have selected Digest SHA256 when I have created the new User (usuario2).
If I renew the Certificate of the new User and later go to "VPN > OpenVPN > Client Export", the new User (usuario2) not appear to export it:
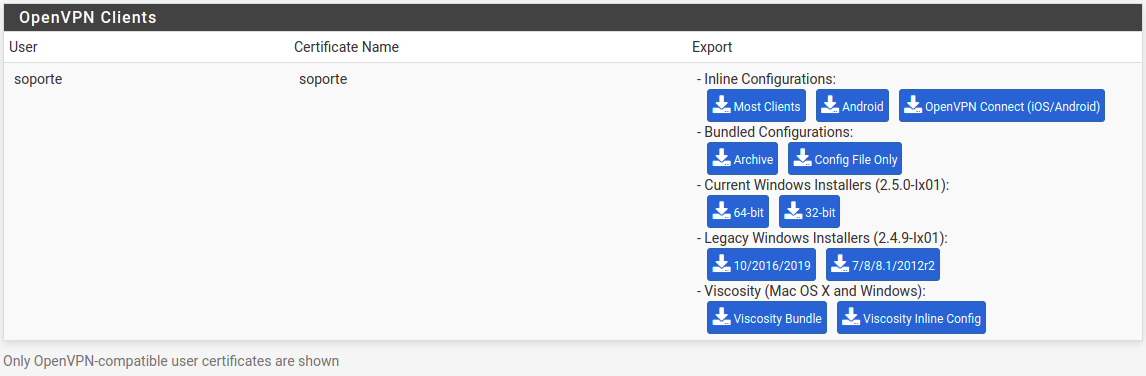
This occur even if I marck the option "Enforce strict security parameters" when renew the User Certificate.
The other User that appears (soporte) is a User that I had created in pfSense before update to pfSense 2.5.0, and I can renew without problems, It not shows the problem of SHA2 when renew the Certificate and It appears in "VPN > OpenVPN > Client Export" to export it. In case It helps you.
What can be the problem now?
Best regards
-
I can't reproduce that here at all, but I'm also on RC snapshots (2.5.1 RC / 21.02.2 RC). Might be something we already fixed since the release.
If I make a user cert from the user manager with SHA256, it gets SHA256. It shows for export. Renewal doesn't flag anything as needing changed. After renewal, it still shows for export.
-
@jimp hi,
I have update pfSense 2.4.5-p1 to pfSense 2.5.1RC and I have the same problem.
If I create the User Certificate (with SHA256):
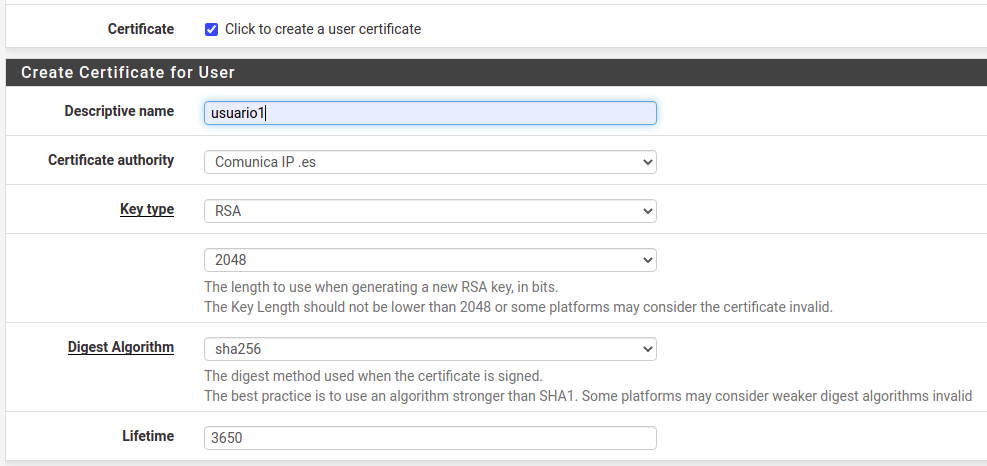
When I create the new user from User Manager, if I renew the User Certificate, It shows:
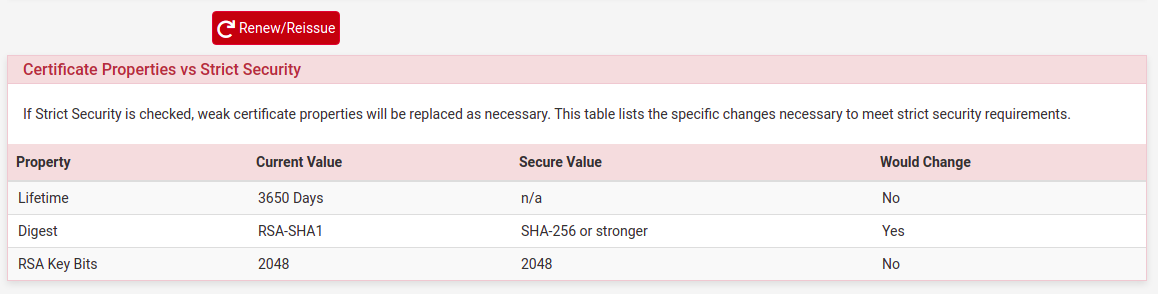
And not appears in "VPN > OpenVPN > Client Export" to export.
If I renew a User that was already created in pfSense 2.4.5-p1, I haven't problem.
If I create a new User Certificate (SHA256) from Certificate Manager, when I renew the User Certificate, show that the certificate is SHA256 and I haven't problem. And If I edit the User that disappeared and associate this renewd certificate to the user, the User apppears again in "VPN > OpenVPN > Client Export" to export.
I don't undertand what happens...
Best regards
-
OK, that time I was able to reproduce it. It seems to be from creating the certificate while also creating the user, it doesn't happen when creating from the cert manager or when adding a new cert to an existing user.
Now that I can reproduce it I'll see if I can come up with a fix.
Thanks!
-
So there are two problems:
- Creating the cert while creating the user doesn't respect the digest but it also doesn't set the type to 'user' properly: https://redmine.pfsense.org/issues/11705
- When renewing, if the type is empty, it assumes server certificate, which is why it no longer is available in the export package: https://redmine.pfsense.org/issues/11706
We'll get fixes in for those soon.