How to block randomized MAC addresses?
-
I want to block devices from connecting to my pfSense network that have a randomized MAC address. I understand that the second digit of all randomized MAC addresses is either a 2, 6, A or E. How do you block MAC addresses that have one of those numbers as the 2nd digit?
I'm not really interested in discussing the pros and cons of randomized MAC addresses. There are plenty of other threads for that. I just want to know how to block them from connecting to my network.
-
On the DHCP server page, you can allow only known devices.
-
Is there a way to only block randomized addresses (i.e. those with a 2, 6, A, or E as the second digit)? I don't want to block all unknown MAC addresses, just those that have randomized MAC addresses. I want to force family members or friends that connect to my home network to have to turn off randomized MAC addresses. I track every device that connects to my network, but these randomized MAC addresses fill up my logs with unknown devices.
-
Off the top of my head - I don't think there is a way to do this.. you would have to create a deny partial list of mac that contain all the possible combo's of possible private - which doesn't seem viable..
I am not aware of any way to parse if the mac for what your looking for.
-
@jknott said in How to block randomized MAC addresses?:
On the DHCP server page, you can allow only known devices.
And even if it was possible on dhcp, using a static ip address would bypass everything.
pfsense cannot impose restrictions based on mac addresses -
@netblues That would also block any locally-generated MAC address such as VMs, etc.
If the network is untrusted put up an SSID/VLAN for those untrusted devices and filter so they can only get to the internet and not the trusted networks.
-
There are other problems associated with random MAC adresses.
If one has defined schedules for the kids to lose internet access at a specified time in order for them to go to bed, then said schedules and rules are worthless if the kids activates random MAC adresses because the device will get a new IP adress out of static one assigned to the NIC's MAC.
And by default, when iOS updates from 12 to 13, it automatically activate random MAC adress.
-
@ninthwave This sounds more like an L3 problem than an L2 problem. As @Derelict said, throw these devices on a vlan and choke the vlan off from the internet on a schedule as desired. Let the kids randomize their mac addresses all they like. When the vlan is cut off from the internet, that's it. As long as they don't have the wifi password to get onto a different ssid/vlan and they can't plug into a port on a different vlan, there isn't much they can do other than try to connect to the neighbour's wifi, which I'm sure they would try. :)
Good luck keeping the kids off the internet but if you're going to try, your best chance is at L3, not L2.
-
If it was just his and his kids devices he could setup static arp as a solution to keep unknown macs from working. While that works - it doesn't scale well if you had hundreds of devices, etc.
And not going to work for guests. But personally - I don't really care for what a guest devices mac address is - they are just guests and can only use the internet..
But yeah the specific vlan for these devices, where you want to cut off access at specific times is better solution where you just cut off anything in that vlan.. Then it doesn't matter what IP they are using - be it from dhcp via real mac or a private mac, or some IP they set static on their device, etc.
-
Very good at blocking whatever MAC is the captive portal.
-
Thanks. I will eventually have to set up a separate VLAN and maybe use the Captive Portal features as well when my kids get older. Right now we physically restrict their access to internet devices so that hasn't been as much of an issue.
I run a simple network monitor that tracks who connects to my network, and over the past 10 years or so I've had about 350 unique MAC addresses connect to the network. Recently that number has been going up much faster though, mainly because of these randomized MAC addresses. I go into the device settings and turn it off where I can, but with major updates it gets turned back on and between myself, my wife, my kids and various extended family we have probably 10 - 15 Apple devices that connect to the network from time to time that all generate random MAC addresses.
It sounds like my best bet is to set up the separate VLAN with a different SSID, limit that to just internet access and stop worrying about what connects to it. However, I am still going to end up with randomized MAC addresses on my main network because of my own personal devices and devices of my wife and kids that I want to be able to access all of the various network resources like cameras, Sonos, etc.
-
However, I am still going to end up with randomized MAC addresses on my main network because of my own personal devices and devices of my wife and kids that I want to be able to access all of the various network resources like cameras, Sonos, etc.
So let them access them? The security comes from the wireless network and its security credentials and who has them, not from what MAC address connects.
If that is the kind of granularity you want in your network, you probably need APs that can announce multiple SSIDs and put the traffic on different VLANs or security zones. Guests can't connect to the VLAN with the stuff you want to protect because they don't have the credentials. They connect to the guest VLAN and can only get to the internet. Doing this at layer 2 (MAC addresses) will require a Layer 2 solution. This might be your wireless gear, switching gear, etc. pfSense is a Layer 3 firewall.
For instance I'm sure if you deployed WPA2 Enterprise and gave each user specific user credentials, you could find wireless gear that issued DHCP addresses based on that, not the MAC address.
-
@derelict said in How to block randomized MAC addresses?:
For instance I'm sure if you deployed WPA2 Enterprise and gave each user specific user credentials, you could find wireless gear that issued DHCP addresses based on that, not the MAC address.
 That's incredible what sorts of measures parents have to resort to in order to have kids go to bed instead of spending the whole night on the tablets or phones.
That's incredible what sorts of measures parents have to resort to in order to have kids go to bed instead of spending the whole night on the tablets or phones.My girlfriend bought an Oculus Quest and since it's standalone, no WiFi is required once the games are installed. The final solution cannot come from pfSence then. The Quest has to come back in our bedroom at night time.
It reminds me of the McCain Deep'n Delicious cake ad where the husband wakes up in the middle of the night to grab a piece of cake...
-
With real wifi gear you can put two different SSIDs on the same VLAN. Put the kids on one and everyone else on the other. Don't give them the creds for the one that stays up all the time. Tell the WIFI GEAR to shut off that ssid overnight.
Then they just turn off WiFi and use cellular. :P
-
I came across this post when I was trying to do this exact same thing.
All the other answers work and are likely the better solution.To simply answer the question though.....
Go to Services --> DHCP Server
Scroll down to MAC Deny.
Paste this in:
A2,B2,C2,D2,E2,F2,12,22,32,42,52,62,72,82,92,02,A6,B6,C6,D6,E6,F6,16,26,36,46,56,66,76,86,96,06,AA,BA,CA,DA,EA,FA,1A,2A,3A,4A,5A,6A,7A,8A,9A,0A,AE,BE,CE,DE,EE,FE,1E,2E,3E,4E,5E,6E,7E,8E,9E,0ENothing with one of these privatized MAC addresses will get a DHCP address.
Yes, it doesnt prevent outright spoofing.
No, it isnt a perfect solution. -
Pfsense doesn't filter on MAC addresses.
-
Just be aware that many virtual machines use private MACs too.
-
@jknott said in How to block randomized MAC addresses?:
Pfsense doesn't filter on MAC addresses.
Mine does. DHCP Server service does anyway.
This works exactly as I have described it.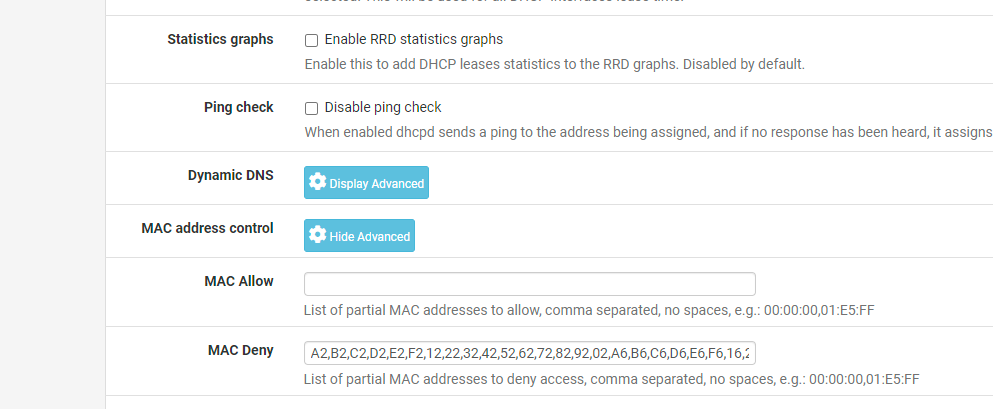
-
@andyrh said in How to block randomized MAC addresses?:
Just be aware that many virtual machines use private MACs too.
All of my VMs use VMware's allocated MACs.
00:50:xxxxxxxxxNot sure about VirtualBox or other solutions.
-
@jadejaws said in How to block randomized MAC addresses?:
Mine does. DHCP Server service does anyway.
That's not filtering. It's assigning an IP address to a MAC address. If it was filtering, you could create a rule to do that. I have worked with other firewalls that can filter on MACs.