Received used SG-1100 - can it hold malware?
-
Formatting it should not be necessary since it creates a new filesystem from the image overwriting everything that was there. It doesn't hurt though.

-
@stephenw10 said in Received used SG-1100 - can it hold malware?:
Yes, that ^.
Reflash it if you don't know it's history. Resetting to the default config will not remove any custom scripts etc.
Steve
I will flash the device with a fresh image from netgate, that part will be easy.
But if I understand correctly, there can actually be custom scripts on such a device. Can they do harm? And most importantly:
I connected the SG-1100 to my network (a segregated VLAN) and I connected my laptop to the SG1100 for about an hour or so. Could such a custom script have already been executed by now and reside on my laptop? Sorry guys I'm no whizz kid when it comes to security stuff.Like I said above, chances are narrow that the seller left such scripts on the device just to play around with my network, but still, I'd like to know what could be done.
Thanks!
-
It's highly unlikely that there would have been anything on that device. If there were any custom scripts on there they would be for something like disabling the status LED (because it is very bright!) or starting a custom service etc.
https://docs.netgate.com/pfsense/en/latest/development/boot-commands.html#shell-script-optionSomething like that would not be removed by simply defaulting the config but would be unlikely to be any sort of security issue.
It's theoretically possible a malicious script could have been installed. In reality the chances are close to zero. Even if there had been your laptop would have to have had some exposed vulnerability for anything long-term to have happened.
Steve
-
@stephenw10 Thank you Steve, I'll just consider it safe after flashing.
Thanks all for contributing to this topic!
Mike
-
@gertjan said in Received used SG-1100 - can it hold malware?:
Hi,
Now it time to unleash the real danger :
Yourself.And remember :
For the rest of live of this device (actually : any device that has a file system) :
Do not - never remove the power . Do as your own PC : use the GUI to shut down or re start.Hi @Gertjan , thanks for that. I will happily follow your advice and from now on will not cut power on the netgate appliances.
Reading the pfSense manual on netgate.com I need to "Halt System" first and then wait for the halt process to finish before unplugging the device from power. Correct?eventually : ebay again and get a UPS, and connect the UPS to the SG-1100 and set things up accordingly.
I actually have a UPS for my Synology. But the USB cable is in use by the Synology. Not sure if I can get a second device to power down upon power failure.If the power goes down, goto Youtube > Netgate > and look for the 'fsck' video.
While you're there, look at all the videos, even the ancient ones that discus general pfSense usage. One of the guys who wrote it, explains it. (try that with Windows)I did a search on the netgate youtube channel, but all that came up was an academy video posted 2020 on how to run fsck in console. That was very helpful, but I doubt it's what you were referring to. No older videos available.
pfSense is rather rich with its functionalities.
Don't think you have to use them all. Use only what you can manage and understand.
Take your time.
Make config backups.
And enjoy.
Good advice, thanks a bunch.Cheers,
Mike -
eventually : ebay again and get a UPS, and connect the UPS to the SG-1100 and set things up accordingly.
I actually have a UPS for my Synology. But the USB cable is in use by the Synology. Not sure if I can get a second device to power down upon power failure.
-
@mikegraw376 said in Received used SG-1100 - can it hold malware?:
I actually have a UPS for my Synology. But the USB cable is in use by the Synology. Not sure if I can get a second device to power down upon power failure.
Good news.
A copy of a 'screen' of my Syno at work :

Guess :what : the Syno is connected to the UPS server, the device 192.168.1.1 - which is pfSense.
pfSense has a APC connected to one of it's USB ports.
The settings on the UPS package page shows :

which tells NUT (the name of the pfSense package I use) to expose it services on that network, my LAN.
A the user/password the Syno uses so it's NUT package can connect to pfSense.
This user/password pair is hard coded into the Syno UPS sofware.Works flawlessly.
At home, I do it the other way around, as my pfSense is running out of a VM - so no USB avaible. That is, not when you're using the build in "Pro" version of hyper-V.
So the UPS is connected by USB to the Syno diskstation.
And my pfSense NUT is connected to the IP of my Syno, which exposes the UPS facilities on my LAN.Also works fine.
-
@gertjan Let me get this straight. You have connected your APC UPS to the pfSense box via the USB cable so the pfSense box powers down upon power failure. Then the Synology "listens" to the pfSense box and also powers down?
-
@mikegraw376 Here's what he said: "And my pfSense NUT is connected to the IP of my Syno, which exposes the UPS facilities on my LAN."
-
Yeah I was going to say the same thing your syno should be able to act as ups server - and other devices should be able to get info from it - that on ups, how much power left - and then they can determine if should shut down.
Or yeah vise versa..
Never bothered to look into actually doing it - because my pfsense is on different ups than my nas.
-
@gertjan
I finally took some time to sort this out. As I understand it your screen shot shows a setup where the UPS USB connection is to your pfSense box and from there the event is propagated to the Synology via the pfSense NUT package. I explored the UPS tab on my NAS but it doesn't look exactly like yours: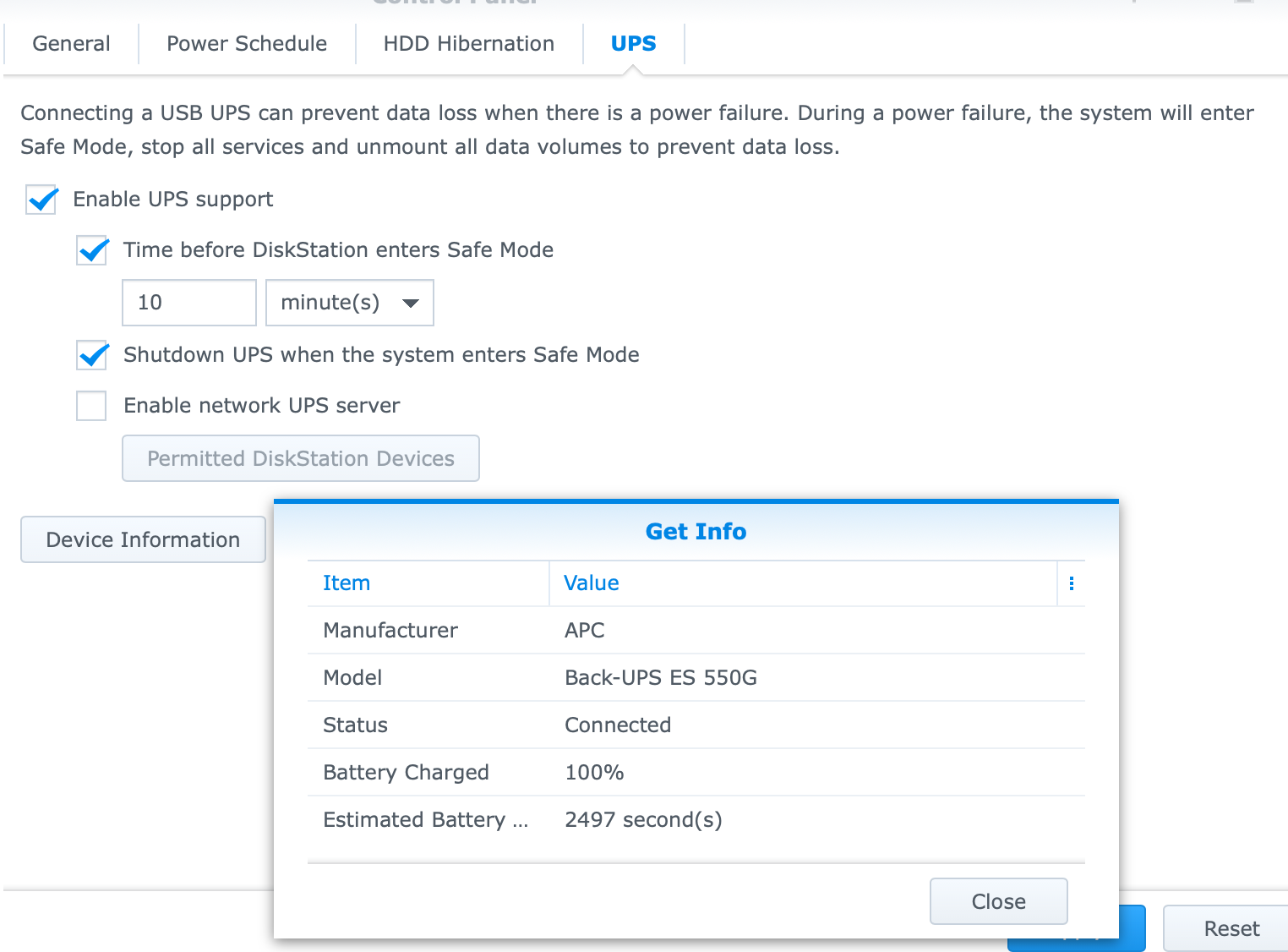

Specifically, your screen shot show the line "Network UPS type:" that I don't see. I do see the option to "Enable network UPS Server" which opens an IP table.
So I'm a bit lost on how I should proceed.
Also, I'm not all that excited about storing my Syno password in the NUT package. Can this be a dummy user that has no rights? Alternatively, could you point out why storing this password in the NUT package is safe?
Thanks!
Mike -
Your prob not seeing the network option for ups, because your ups is connected locally... If you disconnect the ups usb from your nas, it should show you the option of a network ups.. where you can point it to the nuts package running on pfsense.
edit: I pulled the usb plug from ups going to nas.. Disabled ups support in nas, hit apply.. Then went back into ups on nas - and now it shows pick network ups.

-
@johnpoz Thanks John, that did it.
Still a bit worried about that password though. But that could be due to my ignorance about how it is stored and whether or not that can be considered safe. I have plans to open up access to the Synology from the internet, most likely by setting up a VPN using pfSense. So it needs to be ultra safe.Thanks,
Mike -
Well the password you send to ups running on pfsense would be just that, password to access the ups.. Make it whatever you want, and different than any other password you have, etc.
edit: Oh guess you can't change that..
This user/password pair is hard coded into the Syno UPS sofware.
Its just ups password, its not going to be your admin password to your nas, etc. Some looking and yeah username is monuser and password is secret.. Just like shown above.. Not sure why you would be worried about that??
-
@johnpoz i misunderstood. I though gertjan typed "secret" to make his screen shot and then changed it back to his real pw. And I also thought it would have to be a Synology user pw.
wrong on both accounts . No more worries on my part.
thanks a lot for explaining.
ill report back as soon as I made it work
-
@johnpoz said in Received used SG-1100 - can it hold malware?:
edit: Oh guess you can't change that..
@johnpoz said in Received used SG-1100 - can it hold malware?:
Some looking and yeah username is monuser and password is secret.. Just like shown above.. Not sure why you would be worried about that??
Right.
It's hard coded in the UPS script settings in the NAS.
You can edit them of course.
But the next update of your NAS (DSM) will reset them.Here it is : /usr/syno/etc/ups/upsd.users (SSH into your Diskstation)
edit :
Keep in mind that in this cas eit's the NAS connecting to the pfSense IP 192.168.1.1, the NAS is thus the client.
You can protect NTP access of your pfSense as you wish, using firewall rules.