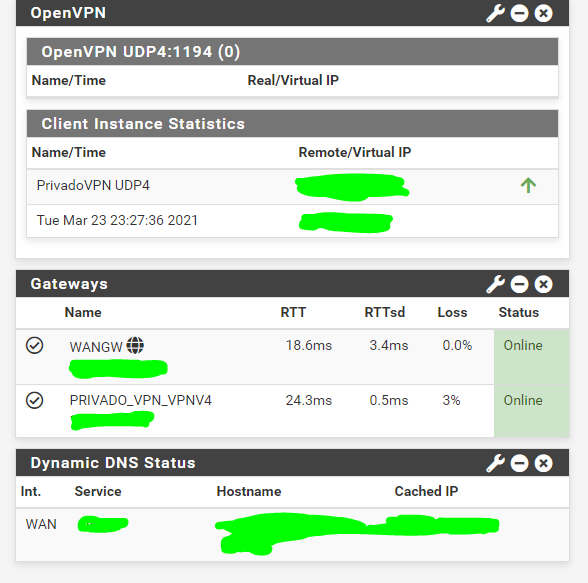
Port forward throgh vpn
-
@viragomann Thanks for replying. PRIVADO_VPN is a client and that one I am using for the port forward. OpenVPN is a server, I am not using that one for port forwarding.
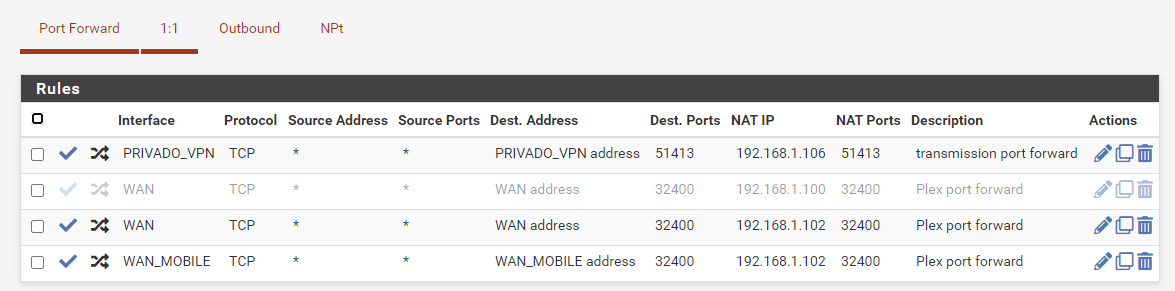
Here are also the interfaces :
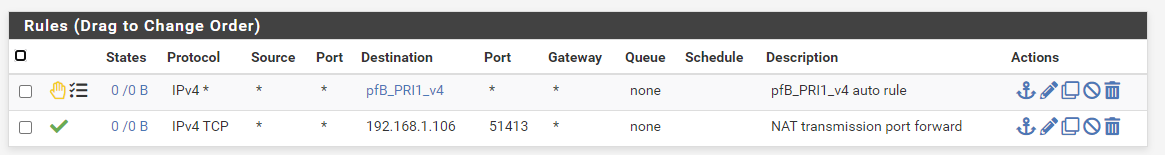
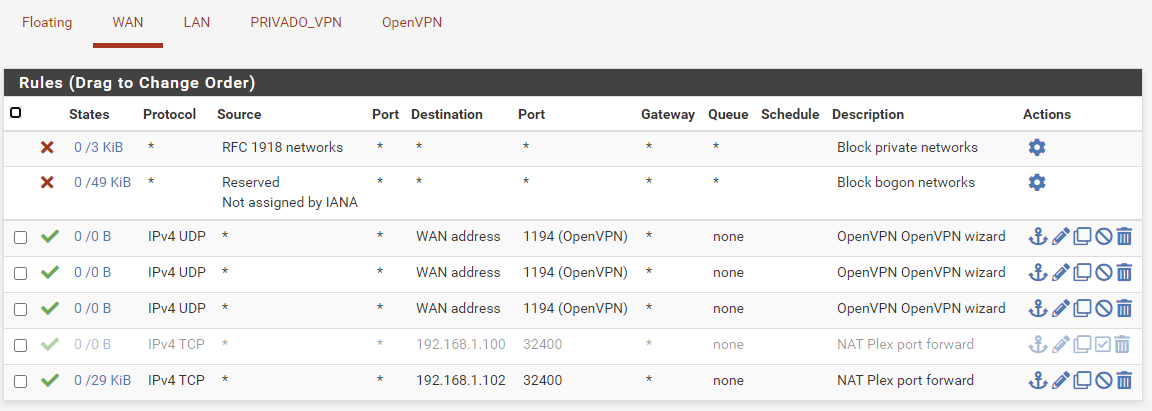
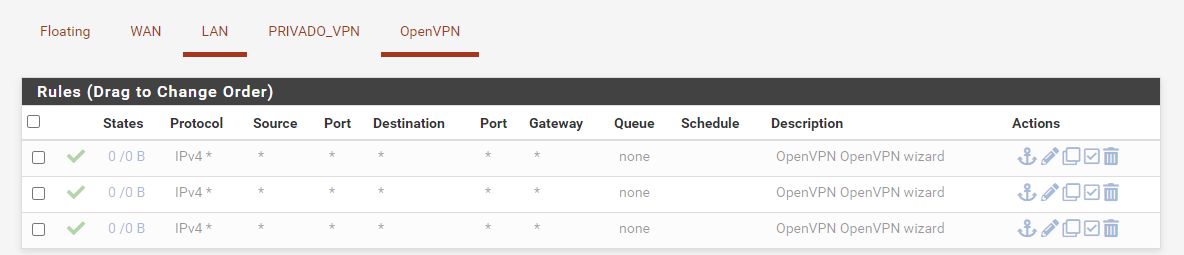
Here are the rules for OpenVPN, I also disabled them for testing and it still doesn't work (what you see in the picture is normally active but it doesn't make a difference):
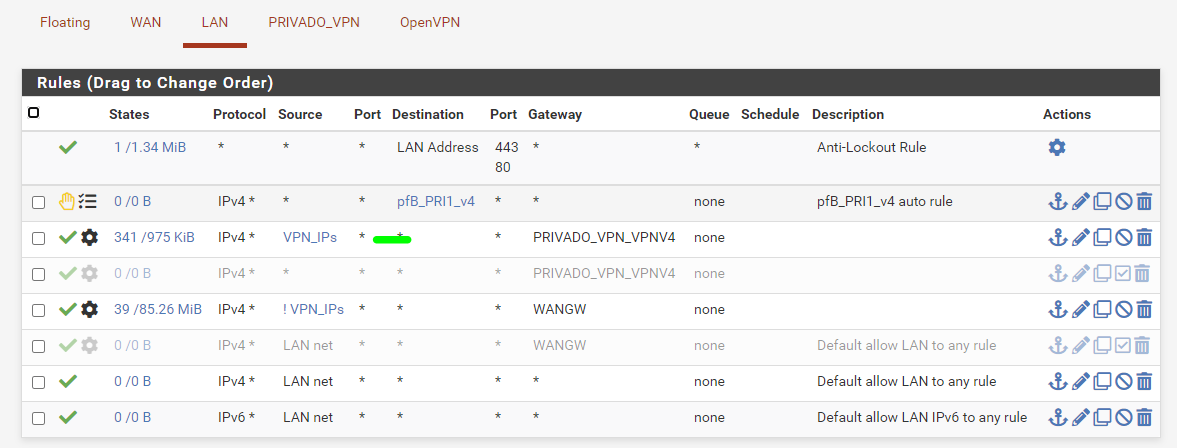
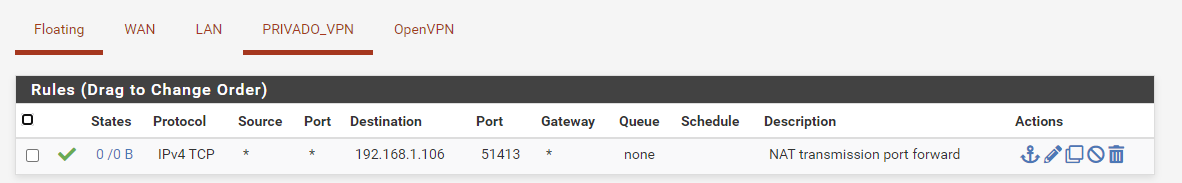
I reposted this image so it's more clear :
The difference here from the original post is that I disabled the pfb_PRI1 rule as @Bob-Dig suggested.
-
@avkr said in Port forward throgh vpn:
OpenVPN is a server
That is not correct. OpenVPN is an implicit interface group containing all OpenVPN instances running on pfSense. So as well the client.
If you want to separate the servers filter rules, assign an interface to the server instance also.@avkr said in Port forward throgh vpn:
Here are the rules for OpenVPN, I also disabled them for testing and it still doesn't work (what you see in the picture is normally active but it doesn't make a difference):
Did you also clear the states after disabling the rules?
-
@viragomann said in Port forward throgh vpn:
That is not correct. OpenVPN is an implicit interface group containing all OpenVPN instances running on pfSense. So as well the client.
If you want to separate the servers filter rules, assign an interface to the server instance also.i did not know this. thanks. I assigned another interface as you suggested.
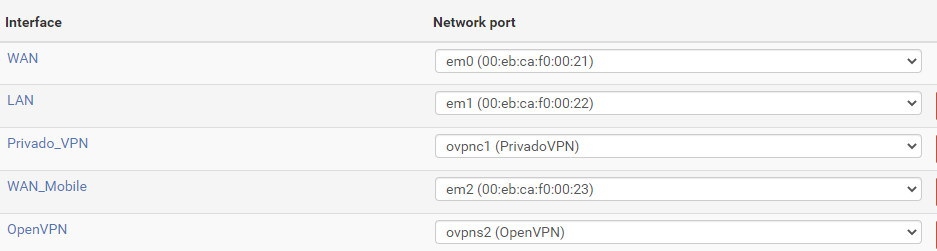
@viragomann said in Port forward throgh vpn:
Did you also clear the states after disabling the rules?
Before I didn't, but I tried also resetting the states now, it still behaves like before.
I have another question though, something that came to my mind, maybe I will say something stupid but here it goes anyway:
When I open the port doesn't it also need to be somehow configured also on the server-side where the privado client connects? Maybe I need to configure something in the client configuration (which I got from the VPN provider).
-
@viragomann I also completely disabled the OpenVPN server, the interface(ovpns2), and the rules associated with it then reset the states, and still doesn't work.
-
@avkr
It's not a good advice to call an interface "OpenVPN", cause this is an implicit interface group, which is present if any OpenVPN instance is configured on pfSense.
So you will have two "OpenVPN" tabs now, which may lead to confusions.@avkr said in Port forward throgh vpn:
When I open the port doesn't it also need to be somehow configured also on the server-side where the privado client connects? Maybe I need to configure something in the client configuration (which I got from the VPN provider).
On the server side the traffic has to be forwarded to you, of course. We assume, that this is already given.
@avkr said in Port forward throgh vpn:
I also completely disabled the OpenVPN server, the interface(ovpns2), and the rules associated with it then reset the states, and still doesn't work.
It's not a question of a running server instance, but of the rules on the OpenVPN interface group tab.
Also check the floating rules. -
@viragomann i will save my current configuration and then do a factory reset, then configure everything only with the privado client and my port forward rule to 192.168.1.106 on a fresh install and then ask advice then from there because like this it's hard to identify the problem. As I understand it there may be something that could interfere with my rule and that's why it's not working. thanks for the advice so far.
-
@avkr
So you're sure that you get the traffic forwarded from the VPN provider to the stated port?To troubleshoot do a packet capture on the vpn client interface to check if the packets arrive there.
If so, do a capture on the internal interface to see if the server is responding. -
@avkr No need to do that. Don't have any rules on the so called OpenVPN Interface and only do it on the specific interface.
Make sure, that your vpn provider really gave you that port and as protocol TCP. -
@viragomann said in Port forward throgh vpn:
So you're sure that you get the traffic forwarded from the VPN provider to the stated port?
No, I am not sure.
To troubleshoot do a packet capture on the vpn client interface to check if the packets arrive there.
If so, do a capture on the internal interface to see if the server is responding.I did something but i am not sure this is correct:
I used the online port check tool ([https://www.yougetsignal.com/tools/open-ports/](link url)) to verify first if the other port forward rule (from WAN to 192.168.1.102:32400 ) works and did packet capture (As this is the first time i did this in my life i want to see a difference between working/not working and try to be methodical )
Packet capture on WAN while the tool is checking (the painted IP is my public WAN IP, 192.168.178.XX is the IP my pfsense box gets from my cable modem, pf sense is connected to a DMZ port on the cable modem ):
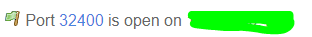
19:59:44.944566 IP 198.199.98.246.59477 > 192.168.178.XX.32400: tcp 0
19:59:44.944964 IP 192.168.178.XX.32400 > 198.199.98.246.59477: tcp 0Now on the LAN:
20:03:04.840298 IP 198.199.98.246.60224 > 192.168.1.102.32400: tcp 0
20:03:04.840647 IP 192.168.1.102.32400 > 198.199.98.246.60224: tcp 0Out of my limited knowledge, i can conclude here that a package arrived on the WAN on port 32400 and got forwarded to the correct IP (192.168.1.102 port 32400) so the rules do what it should do.
So now the same but testing the rule PRIVADO to 192.168.1.106:51413
Packet capture on privado while the port check tool is running(painted IP is the public IP from PRIVADO) :
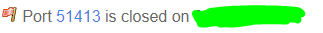
here the packet capture gets nothing from 198.199.98.246(which i am 100% sure is the IP from the port check tool). the window is blank.
now on the LAN
20:13:40.608865 IP 192.168.1.106.51413 > 66.183.144.106.46010: UDP, length 28
20:13:40.608890 IP 192.168.1.106.51413 > 178.143.35.38.26146: UDP, length 28
20:13:41.126421 IP 192.168.1.106.51413 > 66.183.144.106.46010: UDP, length 28I only see that my 192.168.106 IP wants to go outside but nothing from the outside to it in the same way as for the first rule. nothing from 198.199.98.246
After testing the second rule the conclusion that I draw is that packets are not coming into my privado client so that means whatever I do it won't work because the server to which the client connects cuts them off somewhere on the way. AKA my provider sucks.
I repeated these tests a couple of times every time with the same result.
Can you please confirm what I did is correct so I am not running around in circles as I did for the past few days?
-
@avkr said in Port forward throgh vpn:
So now the same but testing the rule PRIVADO to 192.168.1.106:51413
Packet capture on privado while the port check tool is running(painted IP is the public IP from PRIVADO)
here the packet capture gets nothing from 198.199.98.246(which i am 100% sure is the IP from the port check tool). the window is blank.Did you set any filter in the capture here like host or port or protocol?
Possibly the provider nats the sorce IP, but that shouldn't be done at all.
So if not having filters and you see nothing, the packets are not forwarded to you.
-
@viragomann i set a filter on the ports of interest, not on the IP.
-
@viragomann thanks a lot for helping out
-
This post is deleted!