Has anyone found solution for ExpressVPN?
-
@yv5 said in Has anyone found solution for ExpressVPN?:
Mar 30 13:26:58 openvpn 13511 MANAGEMENT: Client disconnected
Mar 30 13:26:58 openvpn 13511 MANAGEMENT: CMD 'status 2'
Mar 30 13:26:58 openvpn 13511 MANAGEMENT: CMD 'state 1'
Mar 30 13:26:58 openvpn 13511 MANAGEMENT: Client connected from /var/etc/openvpn/client1/sockWhe you open the pfSEbse dashboard,
and you have this OpenVPN widget shown,
it shows you information about the status of the connection.
This is what the "MANAGEMENT:" lines are all about. -
@daddygo
I'm a 3 years expvpn user , and have been quite satisfyed w. w. everything but the price.I'm considering switching to Nord , as i have a few friends that are satisfyed w them.
And the 3/yr price is the same a 1/yr for expI'm using it for mobile devices w. the exp app , and instead of a pfS client connecting , i have a dedicated Vlan + SSID that has a Deb10 linux as gateway , so whatever i point the DEB10 at will be the exit node for my devices on the SSID.
I am not running any "Default Inet" via VPN (Yet ....)
/Bingo
-
@bingo600 said in Has anyone found solution for ExpressVPN?:
I'm considering switching to Nord ,
I tried Nord, we didn't have such good network parameters here...
I suggest you sign up for a one-month plan and give it a try before you start bigger shoppingExpVPN is still the best, but unfortunately their Portuguese IP range is narrow....
I got the same 3 IP address, for 7 years, it's not security...
They are restarted the services every 48 hours as the service runs in RAM and so the logs are also discarded
(this causes pfSense to not be able to reconnect and the VPN will remain down until I manually restart - or I have already automated this)Theirs customer services Nord, SurfShark, ExpressVPN is a team trained in a 3-4 day course, they respond like a parrot, like auto -answer machine....hahahahahaha...
The game goes out to get you tired of communicating with them, and leaving them alone

-
@yv5 said in Has anyone found solution for ExpressVPN?:
Is ti possible you post for me all your "basic" settings for ExpressVPN
Yup,

but first......
Here you will find everything, if you get stuck pls. write:https://www.expressvpn.com/support/vpn-setup/pfsense-with-expressvpn-openvpn/
-
@gertjan Thanks
-
I have followed it ...think 10-15 time with no luck
after finish I got not internet connection
although I got some IPaddicional things I have done
in routing, modified
-
Disable Gateway Monitoring Action --> check
-
Monitoring IP 1.1.1.1
after those modification I get on dashboard
0% packets loss / online / greeenbut not internet
-
-
@daddygo said in Has anyone found solution for ExpressVPN?:
@yv5 said in Has anyone found solution for ExpressVPN?:
I apologize for my low profile of understanding DNS capabilities.
VPN GW is down because ExpVPN GW is not responding to PING

@YV5 "Do you use ExpressVPN and is working?"
I've been an ExpVPN subscriber for 10 years now.....
@YV5 "do you reccomend to buy surfshark?"
Nope!!!
but I see you are Spanish,
Yes I speak Spanish
does portuguese go to you?
I do speak Portugues too

-
Open a ticket with them and ask what version of open vpn they are running. I’d like to see an official answer
I’ll betcha it’s 2.4 still
-
I have an Expr*sVPN account for several years now, which I can use to change my WAN IP @work, if needed.
My need is : I've some dedicated servers in some data centers, and for testing purposes its good to change the IP some times.
My @work IP isn't 'officially' static, but didn't change for the last 3 or 4 years. When I manged to blacklist myself on my own server, I need a Plan B.This is what I have right now :
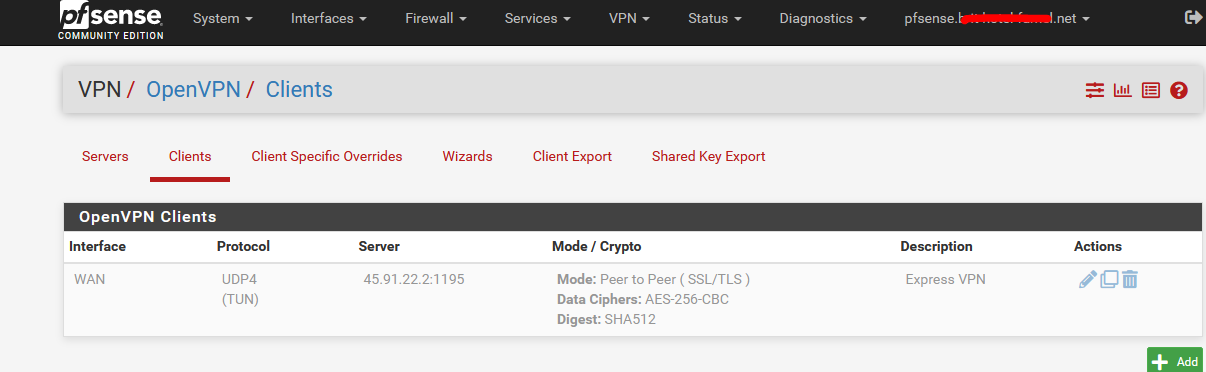
The IP used is one of the Expr*ssVPN servers in Paris, as I'm situated in the south of France.
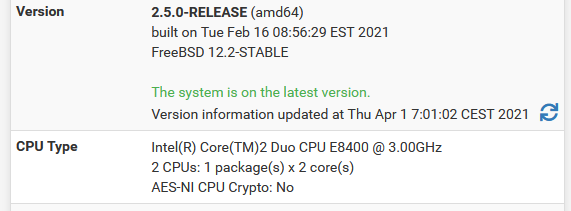
I'm running right now pfSense 2.5.0 :
I activated the client yesterday :
It connected.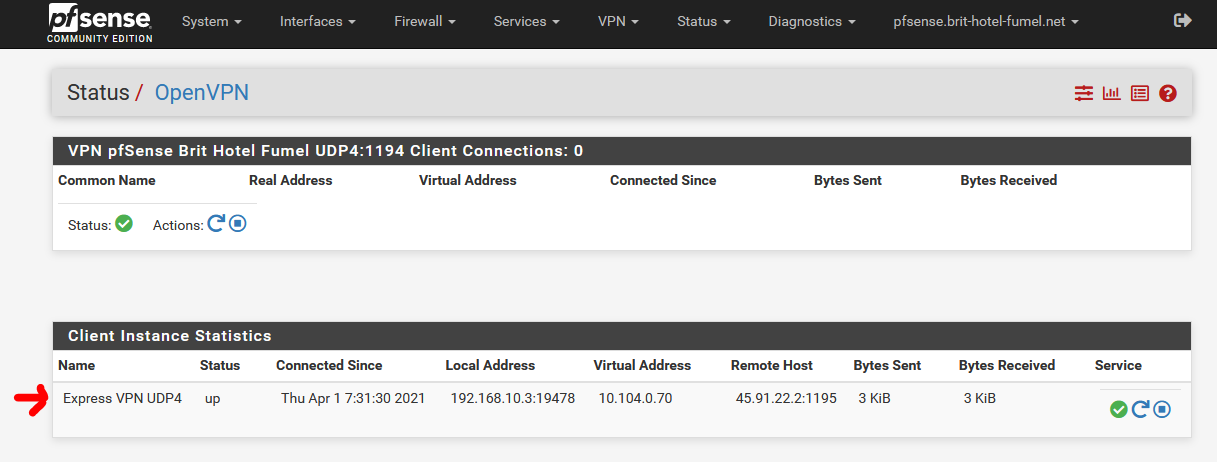
(Note :my OpenVPN server also runs - no big deal - pfSense can do both at the same time)
The OpenVPN client log is pretty clean :
Apr 1 07:51:51 pfsense openvpn[37478]: WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set. Apr 1 07:51:51 pfsense openvpn[37478]: WARNING: file '/var/etc/openvpn/client2/up' is group or others accessible Apr 1 07:51:51 pfsense openvpn[37478]: OpenVPN 2.5.0 amd64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Feb 5 2021 Apr 1 07:51:51 pfsense openvpn[37478]: library versions: OpenSSL 1.1.1i-freebsd 8 Dec 2020, LZO 2.10 Apr 1 07:51:51 pfsense openvpn[37784]: MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client2/sock Apr 1 07:51:51 pfsense openvpn[37784]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Apr 1 07:51:51 pfsense openvpn[37784]: WARNING: experimental option --capath /var/etc/openvpn/client2/ca Apr 1 07:51:51 pfsense openvpn[37784]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Apr 1 07:51:51 pfsense openvpn[37784]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Apr 1 07:51:51 pfsense openvpn[37784]: TCP/UDP: Preserving recently used remote address: [AF_INET]45.91.22.2:1195 Apr 1 07:51:51 pfsense openvpn[37784]: Socket Buffers: R=[42080->524288] S=[57344->524288] Apr 1 07:51:51 pfsense openvpn[37784]: UDPv4 link local (bound): [AF_INET]192.168.10.3:0 Apr 1 07:51:51 pfsense openvpn[37784]: UDPv4 link remote: [AF_INET]45.91.22.2:1195 Apr 1 07:51:51 pfsense openvpn[37784]: TLS: Initial packet from [AF_INET]45.91.22.2:1195, sid=1aee146b a5b8f564 Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY WARNING: depth=0, unable to get certificate CRL: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-2776-4a, emailAddress=support@expressvpn.com Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY WARNING: depth=1, unable to get certificate CRL: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY KU OK Apr 1 07:51:51 pfsense openvpn[37784]: Validating certificate extended key usage Apr 1 07:51:51 pfsense openvpn[37784]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY EKU OK Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-2776-4a, emailAddress=support@expressvpn.com Apr 1 07:51:51 pfsense openvpn[37784]: VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-2776-4a, emailAddress=support@expressvpn.com Apr 1 07:51:51 pfsense openvpn[37784]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA Apr 1 07:51:51 pfsense openvpn[37784]: [Server-2776-4a] Peer Connection Initiated with [AF_INET]45.91.22.2:1195 Apr 1 07:51:52 pfsense openvpn[37784]: SENT CONTROL [Server-2776-4a]: 'PUSH_REQUEST' (status=1) Apr 1 07:51:53 pfsense openvpn[37784]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.104.0.1,comp-lzo no,route 10.104.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.104.0.134 10.104.0.133,peer-id 257' Apr 1 07:51:53 pfsense openvpn[37784]: Options error: option 'redirect-gateway' cannot be used in this context ([PUSH-OPTIONS]) Apr 1 07:51:53 pfsense openvpn[37784]: Options error: option 'dhcp-option' cannot be used in this context ([PUSH-OPTIONS]) Apr 1 07:51:53 pfsense openvpn[37784]: Options error: option 'route' cannot be used in this context ([PUSH-OPTIONS]) Apr 1 07:51:53 pfsense openvpn[37784]: OPTIONS IMPORT: timers and/or timeouts modified Apr 1 07:51:53 pfsense openvpn[37784]: OPTIONS IMPORT: compression parms modified Apr 1 07:51:53 pfsense openvpn[37784]: OPTIONS IMPORT: --ifconfig/up options modified Apr 1 07:51:53 pfsense openvpn[37784]: OPTIONS IMPORT: peer-id set Apr 1 07:51:53 pfsense openvpn[37784]: OPTIONS IMPORT: adjusting link_mtu to 1629 Apr 1 07:51:53 pfsense openvpn[37784]: Using peer cipher 'AES-256-CBC' Apr 1 07:51:53 pfsense openvpn[37784]: Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key Apr 1 07:51:53 pfsense openvpn[37784]: Outgoing Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication Apr 1 07:51:53 pfsense openvpn[37784]: Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key Apr 1 07:51:53 pfsense openvpn[37784]: Incoming Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication Apr 1 07:51:53 pfsense openvpn[37784]: TUN/TAP device ovpnc2 exists previously, keep at program end Apr 1 07:51:53 pfsense openvpn[37784]: TUN/TAP device /dev/tun2 opened Apr 1 07:51:53 pfsense openvpn[37784]: /sbin/ifconfig ovpnc2 10.104.0.134 10.104.0.133 mtu 1500 netmask 255.255.255.255 up Apr 1 07:51:53 pfsense openvpn[37784]: /usr/local/sbin/ovpn-linkup ovpnc2 1500 1629 10.104.0.134 10.104.0.133 init Apr 1 07:51:56 pfsense openvpn[37784]: Initialization Sequence CompletedThe tunnel was up.
Note the 3 lines :
Options error: option 'redirect-gateway' cannot be used in this context ([PUSH-OPTIONS]) Options error: option 'dhcp-option' cannot be used in this context ([PUSH-OPTIONS]) Options error: option 'route' cannot be used in this context ([PUSH-OPTIONS])Normally, you should stop and resolve everything that says "error".
These 3 errors are already mentioned and explained (solved ?) else where on this forum and a future solution https://redmine.pfsense.org/issues/11448 ( I didn't bother installing that patch).For now, I just make it short :
The route, we deal with that ourself - see below.
Same thing for dhcp-option : our clients will take care of things.
redirect-gateway : see the firewall LAN(s) rule below. We deal with it.
These 3 errors are actually no show stoppers.I assigned the interface created by the running OpenVPN Client instance :
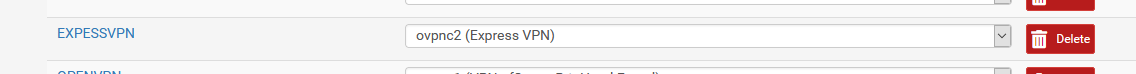
So now I have an interface called "EXPRSSVPN"
Note : just invent a name, I did not set any IPv4 or IPv6 info. Totally comprehensible, as this info is coming from the OPENVPN server (ExpssVPN). The tunnel doesn't support IPv6.The Gateway widget shows :
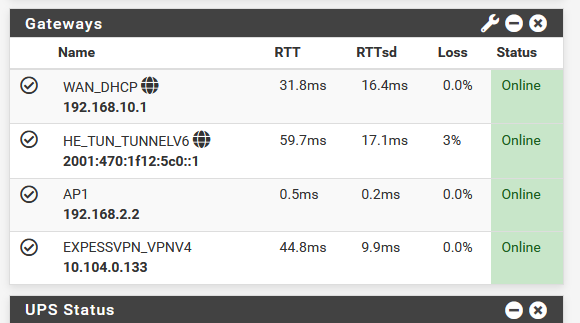
Note : AP1 is some test thing for myself. I'm using dpinger to test a device on one of my local networks.
The last line shows the VPN connection to Expr*ssVPN's server is - looks (?) - ok.
The WAN_DHCPV4 is still my default IPv4 gateway.
The HE_TUN_TUNNELV6 is still my default IPv6 gateway (which means that all local outbound IPv6 traffic, which is half of all my traffic, will still 'leak' through the IPv6 gateway (to an IPv6 he.net endpoint in Paris also)My original IPv4 and IPv6 gateway are NOT changed - and will note change.
I guess it is possible to change the IPv4 gateway for the EXP*SSVPN_IPV4 gateway (our openclient client) to simplify the setup.
I'll have a look at that in the future.Normally, I never go any further.
Yesterday, I decides to go on, and see why people are saying that Expr*ssVPN doesn't work with "pfSense 2.5.0".
Because pfSense uses the recent (not latest !) OpenVPN version 2.5.0-amd64 ?
Something else ?I know how the story goes on :
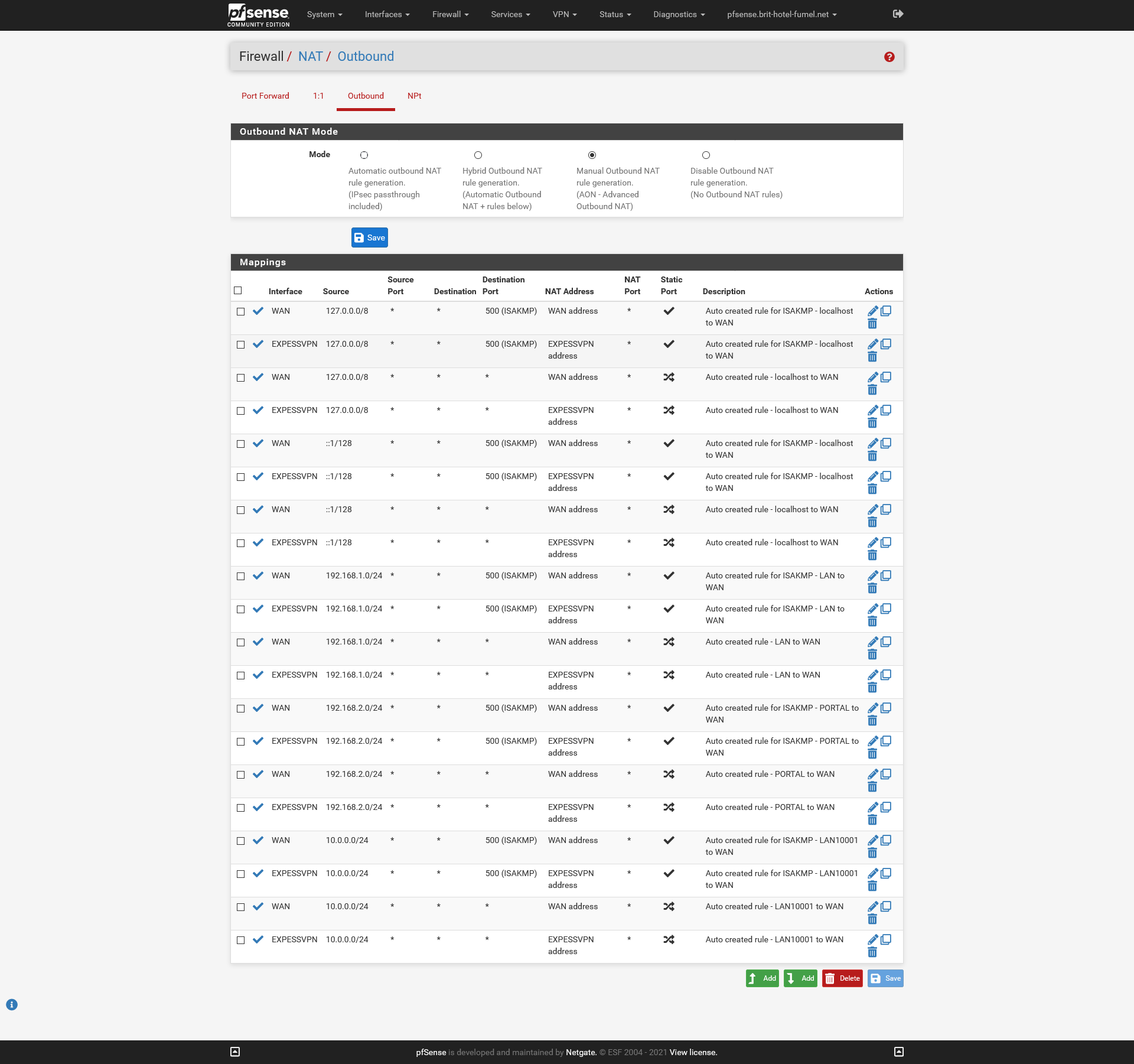
Go to : Firewall > NAT > OutboundSwitch to the third option ( == Manual Outbound NAT rule generation. (AON - Advanced Outbound NAT) )
Then, on that same page, duplicate all ( all of them, is that needed / useful ??) lines listed in the Mappings table and change interface "WAN' to ''EXPR*SSVPN".Final result :
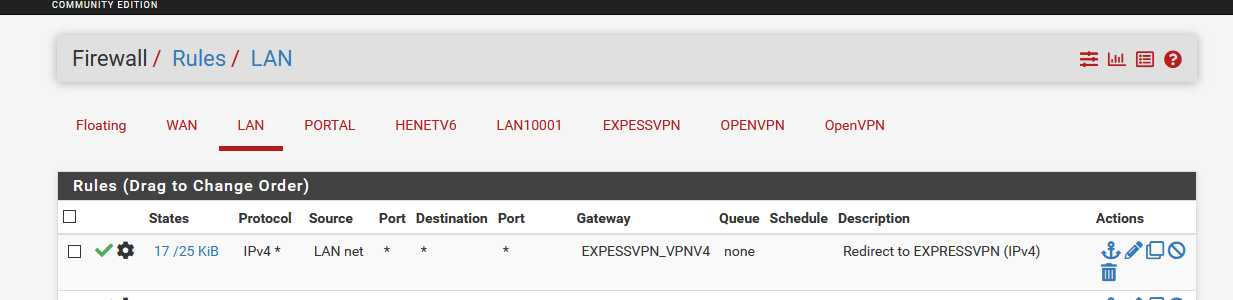
I have to add a firewall rule to my LAN interface - at the top (make things work first), so it's taken in account immediately (still, do not forget to check floating rules - disable all/some floating rules during test phase) :
A small test, because I'm always optimistic in the morning :
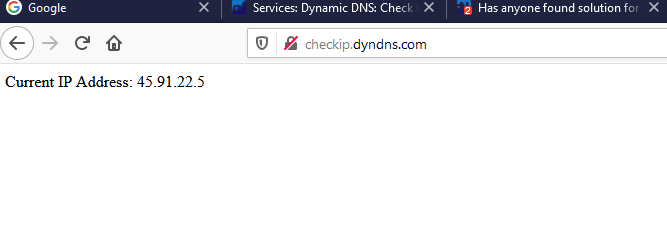
That's not my normal WAN IP, it's the Expr*ss VPN IP.
It works.Edit : This starts to look like another pfSense success story.
A speed test :
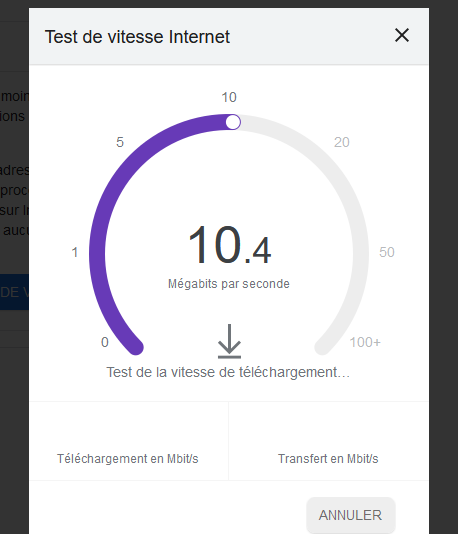
That's awful. A MTU issue ? whatever,it's usable. I'll check that later on.
My normal ISP speed is a whopping 23 Mbits/sec (VDSL) - a very correct speed when you are situation in the middle of very rural south west France .Note : the fibre is just outside of the door : it's ready to be hooked up to our installation, but the French president just announced yesterday another 4 week lock-down so nothings will get done this month.
But it works. As advertised.Extra steps I took :
What I find important :
When setting up things, I like to compare settings. The differences will explain the "no--go".These are the settings (opvn file) you have to download from the Exp*ssVPN site - login as a registered user and you can get it :
dev tun fast-io persist-key persist-tun nobind remote france-strasbourg-ca-version-2.expressnetw.com 1195 remote-random pull comp-lzo no tls-client verify-x509-name Server name-prefix ns-cert-type server key-direction 1 route-method exe route-delay 2 tun-mtu 1500 fragment 1300 mssfix 1200 verb 3 cipher AES-256-CBC keysize 256 auth SHA512 sndbuf 524288 rcvbuf 524288 auth-user-pass( I removed the cert details that Expr*ssVPN includes, the cert info should be used in the pfSEnse GUI to create the CA and the certificate, and these are used in the GUI OpenVPN client settings )
Here is the pfSense OpenVPN opvn file which you can find here :
/var/etc/openvpn/client1"client1" could also be "client2" - or 3, depends, if you have more then one OpenVPN client set up.
The file is called :
config.opvnMy /var/etc/openvpn/client2/config.opvn :
dev ovpnc2 verb 3 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_client2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA512 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 192.168.10.3 tls-client client lport 0 management /var/etc/openvpn/client2/sock unix remote 45.91.22.2 1195 udp4 auth-user-pass /var/etc/openvpn/client2/up capath /var/etc/openvpn/client2/ca cert /var/etc/openvpn/client2/cert key /var/etc/openvpn/client2/key tls-auth /var/etc/openvpn/client2/tls-auth 0 data-ciphers AES-256-CBC data-ciphers-fallback AES-256-CBC allow-compression asym comp-lzo yes resolv-retry infinite route-nopull fast-io sndbuf 524288 rcvbuf 524288 verify-x509-name Server name-prefix remote-cert-tls server key-direction 1 route-delay 2 tun-mtu 1500 fragment 1300 mssfix 1450 auth-nocacheThe last 8 lines are added like this :
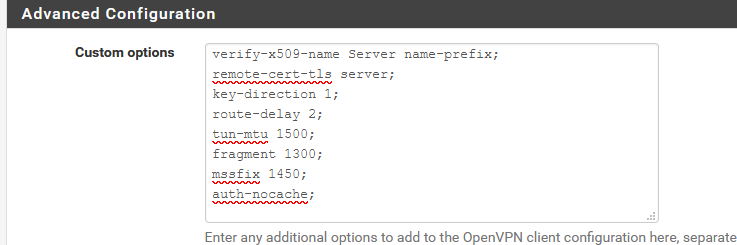
Now look at this :
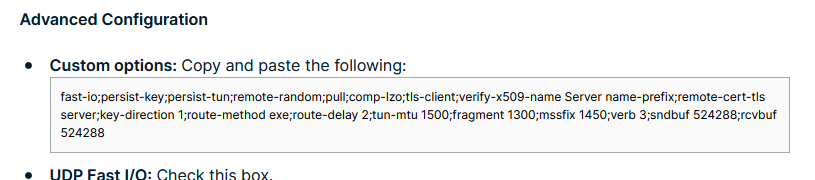
some of these are already in the pfSense fabricated config.opvn file.
I remove them.And that's about it.
I rebooted pfSense.
My IPv4 was :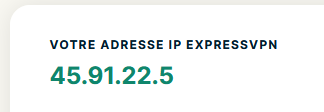
which is a "EXP*SSVPN" IP in Paris - not my WAN IP (ISP Orange)
About the "Data Encryption Negotiation" setting and "Data Encryption Algorithms" :
So, what is it that you guys did, that I didn't, so it works for me but not for you ?

Again, I'm using a vanilla pfSense 2.5.0.
Followed the somewhat outdated https://www.expressvpn.com/fr/support/vpn-setup/pfsense-with-expressvpn-openvpn/
Inspected the logs,
Compared the config files proposed and used,
Fired up the openVPN client,
Assigned an "openvpncx" interface,
Changed to NAT outbound manual mode (a mappings),
Did a minimal "LAN" (my 192.168.1.0/24) redirect.
Tested it, works,
Rebooted, still works,
Done
Again : normally, I don't use my ExpssVPN account to redirect my entire 'work' network. I don't have to do so. Never found a reason that convinced me to do so. I don't care that my 'resolver mode' DNS transmits very visible 'youprn.hub' DNS requests coming from the captive portal (remember : work = a hotel with clients in the rooms using my Internet connection).
Maybe, as it works now, I could redirect my captive portal traffic over VPN, and use an IP from Expr*ssVPN IP somewhere outside of Europe. No more issues when some one downloads the latest Disney movie over my Internet connection, something that has consequences when you use a European ISP connection. I'll think about it (better have that fibre first). -
So, no more Expr**VPN issues ?
Or was I just lucky while using a Expr*ssVPN server "france-strasbourg-ca-version-2.expressnetw.com 1195" (Paris) -
ça va? gertja!!
mon ami ---> you're THE MAN
your post solve all my problems with Expressvpn
merci!!!


















Jorge
-
@yv5 said in Has anyone found solution for ExpressVPN?:
I have followed it ...think 10-15 time with no luck
Sorry for my late reply, the OVH DC (French) fire, caused a lot of work for me, but I see @Gertjan helped
