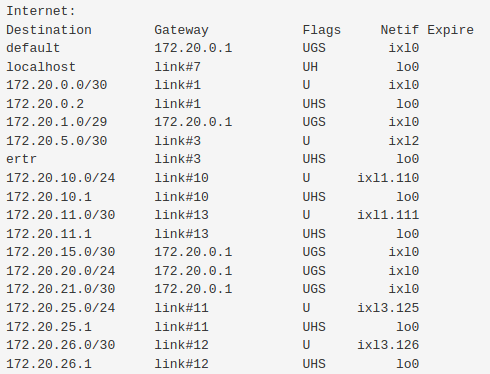
DNS Resolver Split outgoing interface
-
I have my pfsense box acting as a DNS resolver for all the clients on my network.
Recently I setup up a domain controller which also acts as a DNS server, but I did not want clients using it as the primary dns server, so I set up a domain override on pfsense for any .local domain traffic (Windows Domain traffic) to get forwarded to the domain controller.
Initially I had the problem where the queries weren't being forwarded because the domain controller is located off one of my LAN interfaces. So I added that interface to the outgoing interface list in the DNS resolver.
That solved computers looking up the DC, but now pfsense is attempting to use this LAN interface as the source for internet DNS lookups (as well as its WAN interface).
Is there a way to split which interface the resolver chooses for certain queries?
Like only the LAN outgoing interface should be used by this domain override and not for internet lookups? -
Hey @erasedhammer ! Can you share your interfaces status ? Can you also offer more details of you need to put in place there?
-
Brief overview of my network layout:
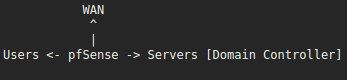
So my domain controller that is also a dns server is in the Servers subnet
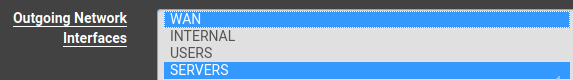
In my DNS resolver, the outgoing interfaces are selected as : WAN, Servers
Users subnet have pfsense set to their DNS resolver. But if the domain they are looking up is .local, then the domain override sends the queries to the DCMy problem is that from an upstream router, I can see pfsense doing queries for internet domains from BOTH the WAN interface IP and the Servers interface IP, since I selected both Servers and WAN as outgoing dns resolver interfaces.
But domain override doesn't work unless you select the interface that the other dns server is on as an outgoing interface.I just want internet DNS queries to originate from the WAN interface IP, and .local queries to originate from the Servers interface IP.
-
@erasedhammer said in DNS Resolver Split outgoing interface:
attempting to use this LAN interface as the source for internet DNS lookups (as well as its WAN interface).
How exactly would it do that, unless there is a gateway setup on this interface or using this interface?
Your saying its sending a query to say 1.2.3.4 from 192.168.1.1 (pfsense lan IP).. To where? What mac address.. You can only use an interface to talk to IPs on that network.. Unless there is a gateway, how would it send traffic to 1.2.3.4 from 192.168.1.1??
Could you post up what your seeing..
-
Sorry, should have clarified, this pfsense box sits behind a firewall. Pfsense is not doing NAT, acting as a router/firewall for local traffic.
Initially on the edge firewall I wasn't allowing any traffic from the gateway IPs for pfsense's lan subnets, just that pfsense boxes' WAN IP. Which is how I noticed that setting two outgoing interfaces, pfsense just hops between them for sending queries to upstream DNS servers.
I am just wondering if there is any way to make the dns resolver only use an outgoing interface for certain domains?
-
@erasedhammer said in DNS Resolver Split outgoing interface:
I am just wondering if there is any way to make the dns resolver only use an outgoing interface for certain domains?
It would only use an interface that it either attached to network its trying to send the query too. Or to a gateway it thinks could talk to that network via your routing, via specific routes or default routes.
How would it send traffic out an interface to an IP that does not reside on that interface, or to a gateway IP it talks to via that network.
If it want to talk to say 1.2.3.4 for domain.tld via your override. It can and will only send traffic out an interface that is on the network 1.2.3.4 sits on, and it can arp for. Or to a gateway it is setup with a route to the network 1.2.3.4 sits on, or a default gateway.. Where hey I don't have a route to 1.2.3.4 network - just send it to my default gateway..
-
@johnpoz
I am not sure how its doing, all I know is it IS doing it.From pfsense:
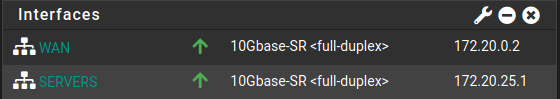
From upstream router:
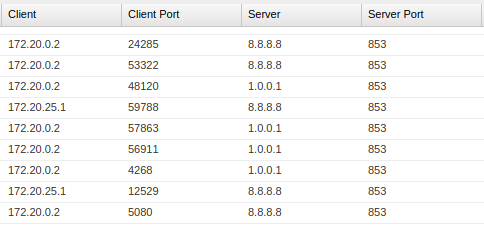
As you can see, its sending queries from both.
-
@erasedhammer said in DNS Resolver Split outgoing interface:
Recently I setup up a domain controller which also acts as a DNS server, but I did not want clients using it as the primary dns server,
Why would one invest in a domain controller but not have their clients use it as the source of information for the domain?
Genuinely curious.
-
@derelict
The domain override exists for clients to ask the domain controller domain related DNS queries. What I didn't want is the domain controller handling internet DNS queries.But to directly answer your question, the domain controller is virtualized on a less than reliable server right now. It isn't that critical right now, nothing important relies on it at this point, just a couple of VDIs.
-
Lets see your gateway and routing table.. The only way pfsense would talk to some gateway from its lan IP, if the gateway is attached to the lan network.
This is how any router would work. Its not something special to pfsense.
-
@johnpoz
Heres the gateway list:
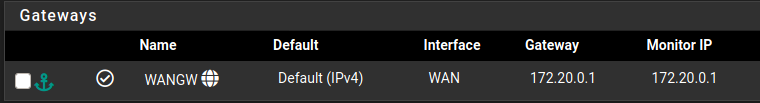
I don't have any internet static routes though, so everything gets sent to that default gateway.
-
But lets see the routing table.. Pfsense shouldn't use the lan IP when it wants to talk to 172.20.0.1
It shouldn't be able to.. Makes no sense to use that IP when trying to talk to something that is not on that network.
-
-
Maybe @Derelict has some idea.. I am drawing a blank to how/why it could/would do that..
-
Have you set the gateway for your server interface? I think you will need to create static routes and set these dns policies in DNS resolver. You will also need to allow this traffic in the rules and put the SERVERS gateway in advanced configuration of these rules for users to use this weird configuration.
What a tricky scenario.
-
What do you mean by gateway for the server interface? It is a gateway in itself.
And by static routes, do you mean static routes inside the dns resolver itself? I am unfamiliar with how to do that.Is it a weird configuration? Domain overrides can be used for more than my weird domain controller setup.
I think if the domain override could work without selecting additional outgoing interfaces, I wouldn't be seeing this behavior. -
@erasedhammer What have you selected as the outgoing interfaces in DNS Resolver/unbound?
No, you cannot source a connection for a specific domain from a specific source address. This is something dnsmasq (DNS Forwarder) could do but unbound cannot, unfortunately.
-
-
@erasedhammer So it is doing exactly what you told it to do? Source queries from both addresses?
-
Correct, but the domain override and telling it to use an internal DNS server does not work without selecting the servers interface as outgoing.
I guess that is the root of my question, why can't the domain override work without the interface being selected in the outgoing interfaces list.