Cannot add VLAN interface
-
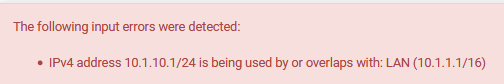
Don't use /16 on the LAN interface , if you want to use 10.1.x.x on the new Vlan interface.
-
@cool_corona said in Cannot add VLAN interface:
I have interfaces added on 2.4.5P1 no issues.
With that /16 mask? Pfsense has prevented overlapping IPs for as long as I can remember..
As @bingo600 correctly stated - don't use overlapping networks on your interfaces. It is not a valid configuration..
-
This post is deleted! -
Overlapping is overlapping - you can not do that..
If its just a parent interface with vlans on it - why are you even setting an IP on it? If you want native network on the parent, with vlans on it - they still can not overlap..
-
This post is deleted! -
its BORKED!! How is pfsense to know where an IP is at if has same network on 2 interfaces.
IP address xyz could be on the parent or the vlan..
Be it you think it worked ok before, and if pfsense lets you do from cmd line (where no code to check) is besides the point. Such a configuration is just plan BORKED!!
Such a configuration would not allow your native network clients to ever talk to vlans - because it would think that IP is suppose to be on its local network, and it would just arp for it, vs sending to the gateway.
-
It couldn't (shouldn't) have worked if you had comms from lan to vlan.
Lan would due to the /16 just have "arp'ed" for any "vlan ip" , and never used the gateway , aka. routed the package via L3. So no comms ought to be possible.You might have been saved by some kind of "Proxy Arp" , but i wouldn't have expected a FW to do proxy arp - (Don't know pfSense inners that good)
Hmm : JP beat me to it

/Bingo -
This post is deleted! -
Be it you think it works, or worked for your scenario is again besides the point... It is a completely and utterly borked setup..
It is networking 101 and basic common sense. You can not expect it to work if you put the same network on more than 1 interface.. It is borked, will always be borked..
Correct your setup. How can you think such a setup is valid?
How does a device on parent /16 network get to a device on a vlan - when that vlan IP is on its own /16.. Unless you don't actually have vlan isolation there is no way this /16 network device could arp for an IP that is he believes should be on his network.. So how would he ever talk to said device.
The only possible this could ever work is your not actually isolating your vlans.. Also borked!
-
This post is deleted! -
Dude I don't know what else to tell you.. Its BORKED!
Fix your setup.. There is nothing for pfsense to do here.. what you are trying to do is wrong - no matter how you look at it, or want to think you should be able to do it..
Even the most basic grasp of how networking works tells you how you have it setup is just plain borked..
edit:
When a client wants to talk to an IP.. Is that IP suppose to be on my network.. Does it fall inside the IP space of my address and mask. Oh its on my network - ARP!! for it.. Ok device with mac address abc, answered for IP 123.. Send the traffic to that mac..
In no scenario does the client say - oh no answer for arp, send it to my gateway... The only scenario where it "could" work is if the gateway (pfsense) was doing proxy arp and answer for any IP that doesn't answer arp.. Which there is no such thing - there is a way to do proxy arp for VIPs..
So if you have some device on your /16, and it wants to talk to a an IP that is on one of your vlans that falls under this /16 block.. How would it know where to send the traffic.. So either your L2 are not actually isolated. Or you have pfsense doing proxy arp for every single IP under the /16 that is not actually on the /16 L2..
You can not expect your setup to ever function correctly.. Pfsense will clearly warn you - as it did that what your trying to do is wrong, ie the overlapping networks warning. But how can it warn you from a cmd line setup? Pfsense can try and keep users from shooting themselves in the foot.. But it can not protect you from every scenario of shooting yourself.
Setup your networks on pfsense be them native or vlans so they do not overlap..