Requirements for a specific DNS server for a specific host
-
Actual setup
- pfSense on a PC with only one WAN and one LAN
- Two unmanaged switches
- One DD-WRT router acting only as an Wifi Access Point
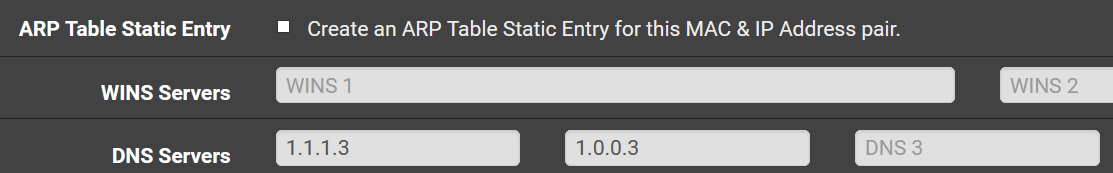
Cloudflare offers 1.1.1.3 that is allegedly malware and porn free.
If I want to assign 1.1.1.3 to the kid's alias, do I need:
To set up- a VLAN for the kid's or can one assign a DNS specific to a host?
- As DD-WRT offers VLAN capabilities (some sort of managing), would it suffice ?
Thanks
-
In DHCP you can assign a static IP to the desired PC. In the options for a static IP you can assign the DNS servers of your choice.
-
I did that for his three devices, applied changes and I tried the iPad that can still access Pornhub.
Did I miss anything ?
-
Verify that you have the correct DNS servers on the iPad. You may have to release/renew the lease if you did not get the correct DNS servers.
-
@andyrh
Something is no right.
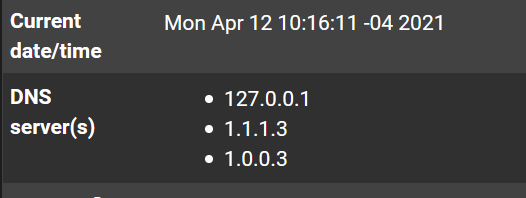
This is the capture of the General Setup.
Even my PC can still access PornHub if using pfSense as the DNSServerIf I manually configure the DNS Server on the host with 1.1.1.3, then it blocks pornhub.
-
@ninthwave
Maybe I should check this in DNS Resolver Option ?

-
@ninthwave
Still no success -
Just because you change the dns IP in dhcp reservation for a client - doesn't mean the client gets it instantly... You have to make sure the client updates its dhcp lease.
And also that it flushes any local dns cache it could have, be it in the browser itself or the local dns cache.
Also - make sure your browser is not using doh.. And just bypass whatever you set for dns anyway.
-
@johnpoz
From what I read on Wikipedia, almost all common browser nowadays use DoH.On my PC, I did a
ipconfig /flushdns ipconfig /release ipconfig /renewI can still access any porn.
On the kid's iPad and iPhone, I renewed the IP leases and I could still access any porn sites.
Once I manually set DNS Server on iOS devices, I can't access any porn.
It's like pfSense is not resorting to 1.1.1.3 at all.
-
This post is deleted! -
@ninthwave said in Requirements for a specific DNS server for a specific host:
On the kid's iPad and iPhone, I renewed the IP leases and I could still access any porn sites.
Well look on your phone to where it points to for dns via what it got from dhcp. If its not where you pointed it.. Then it didn't update its lease - or you set the dhcp settings wrong..
Click the little i next to the connection and you can see where dns points on your iphone.
It should show you if automatic, etc.
-
@ninthwave Some devices have a built-in hardcoded DNS. You should capture all DNS requests and forward them to pfSense:
Redirecting Client DNS Requests
Block anything over port 853 to block DoT.
and disable DoH via use of the canary domain. Make sure your Resolver custom settings has:
server: local-zone: "use-application-dns.net" always_nxdomainDevices with a mobile link can also reach out to get DNS that way if they think they're blocked via wifi. Good luck blocking that.
It's not perfect but should help.
-
@ninthwave said in Requirements for a specific DNS server for a specific host:
@ninthwave
Maybe I should check this in DNS Resolver Option ?

It seems that's what was needed unless I am mistaken,
-
@kom said in Requirements for a specific DNS server for a specific host:
@ninthwave Some devices have a built-in hardcoded DNS. You should capture all DNS requests and forward them to pfSense:
Redirecting Client DNS Requests
Block anything over port 853 to block DoT.
and disable DoH via use of the canary domain. Make sure your Resolver custom settings has:
server: local-zone: "use-application-dns.net" always_nxdomainDevices with a mobile link can also reach out to get DNS that way if they think they're blocked via wifi. Good luck blocking that.
It's not perfect but should help.
I am not sure I get all of it.
I have read this about canary: [https://www.reddit.com/r/sysadmin/comments/dbs1ew/canary_domain_to_disable_firefoxchrome_doh/](link url)
What do you mean by "block anything above port 853" ? In the firewall rules, there is no specific protocols for DNS Request.
-
You have a couple ways to skin the cat.
If you forward to 1.1.1.3 then all clients asking pfsense will get answers from 1.1.1.3. Pointing to anything other than .3 isn't good idea if that is what your wanting to do. Because you can not be sure if you ask .3 or .X - if .X doesn't filter.. Then your responses could be unfiltered.
If you do that, then you need to point your clients you don't want to use that directly.
Your better off just setting clients directly that you want to use some specific filtering dns. But then again when you do that clients will not be able to resolve local stuff.
A simpler option if you want clients to both resolve local, and use some filtering dns upstream is to use a different local ns. Be it another unbound instance or bind, dnsmasq, etc.
This way you can point your clients you want to filter to local ns2.. Which has a conditional forwarder to local up your local records by asking pfsense (ns1 lets call it)... While anything else gets forwarded to your upstream filtering NS to resolve.
Clients you don't want to filter can just point to pfsense (ns1 in our example) and it can just resolve as normal..
While depending - it can be possible to just use single instance of your NS with views setup so that client X gets forwarded to upstream A, client Y uses just normal resolver or gets forwarded to upstream B. But you run into the possibility of shared cache which can lead to wrong results for what your asking for.
If I really wanted a client or group of clients to be able to resolve local resources while also only getting dns from some upstream filtering NS (1.1.1.3 for example).. I would use a secondary NS on the network that forwards to 1.1.1.3, and conditional forwarder to pfsense to resolve whatever.tld your local domain is.
Then only allow this 2nd NS to only query 1.1.1.3 in your firewall rules. And prevent these other clients from even talking to pfsense dns, or any other dns.
While also block dot and doh at the firewall as well.
This lets you control clients to only use a filtered dns, while also resolving your local stuff. And allowing your other stuff to resolve whatever they want.
-
@ninthwave DoT uses tcp 853 to make DNS requests over TLS. Block tcp 853 on LAN and that will block DoT.
-
I went to the extreme, through the use of DHCP and firewall rules force all clients to use my internal DNS (PiHole) servers. Only my PiHole servers are allowed access to outside DNS servers. The setup is not for the faint of heart, but it is solid.
I have found many things try to use their own DNS servers.https://forum.netgate.com/topic/156453/pfsense-dns-redirect-to-local-dns-server?_=1618256594758
For simplicity make sure each targeted device only has DNS servers that do the filtering you want. Windows for example will query all the DNS servers in its list with a small delay between the queries. This favors the 1st in the list, but will result in others answering first on occasion.
-
@andyrh said in Requirements for a specific DNS server for a specific host:
force all clients to use my internal DNS (PiHole) servers.
I wouldn't call that extreme at all ;)
I do pretty much the same thing - most everything on my network uses pihole... Which forwards to pfsense and then unbound resolves.
I like the ease of being able to see what queried what that the pihole interface allows for. I can see what devices are asking for what "a lot" for example very easy with pihole..
What has my tv being queries for example - clicky clicky there you go running log of what that specific client queried. Was it blocked, allowed, etc.