Hide GUI
-
HELP! My IT guy passed away unexpectedly. He set up pfSense in my small business. My credit card company called and said we failed compliance testing. They want my GUI login interface to be invisible. I don't want to mess things up. How do I do this to satisfy them? THANKS! Joe
-
They want my GUI login interface to be invisible.
By default, the GUI can not be seen / used / noticed on the WAN side.
It's all considered as "bad practice" to do so.The default pfSEnse has not WAN firewall rules - and no NAT rules.
This means : nothing from the outside (the Internet) can go "in".Your hosting services locally that handle credit card transaction ?
Get yourself an "admin". -
My credit card machine has an IP address on my LAN. Yearly, we have to go thru a credentialing process to assure security. Not sure what changed from last year, but their tech guy sent me a screen shot of my login screen and apparently this is a no no on their end. I am not sure how he was able to do this. I would appreciate any help. I am not an IT person, but know enough to get myself in trouble. Since my IT person passed, I don't want to muck up anything by messing with settings. Thanks again.
Joe
-
I don't know what's happening there, but many companies do not allow any management interfaces on the main LAN. I have set up networks where the management interfaces are on a VLAN that users don't have access to.
-
Did they do the check from outside your network or inside your network?
If outside - then yeah that would be bad.. Post up your wan rules.
If from inside your network, ie the lan side. If on lan then yes the antilock out rules would allow the gui to be accessed from lan network.
And yes @JKnott is correct - if your doing stuff with CC and such, you prob do not want the webgui available from that network. Your CC stuff should prob be on different vlan than all your other stuff, ie not your normal lan.. And you would yes prevent this network from accessing the web gui of your firewall.
You have 2 options - disable the antilock out rule on your lan and setup only specific IP on your lan to be able to access the gui. Or better solution would be to move your CC stuff to a different vlan.. And isolate it as much as possible from talking to anything else on your network that it doesn't need to talk to do its CC stuff.
Sorry to hear about loss of your IT guy - but your best bet here is to get another IT guy that knows how to properly secure a network for PCI compliance.
-
My credit card machine has an IP address on my LAN.
I've got a couple of them in my (company) LAN.
And I can host or make visible on my WAN IP whatever I want.
Why should my bank bother ?As far as I know, these device (in France - the place where they invented the Credit Card) bank or other organisations don't care.
These devices uses their own TLS based connections, which are 'unbreakable'.
These devices do not accept 'connections' from anywhere. Again : they are located in the same LAN as the PC on which I'm writing this post. They just allow a simple end user keyboard (pad) control.
These devices can only connect - that is : they make the initiative - to a known server "at the bank".Btw : if the IT guy isn't the boss of the company : replace him : people come and go, that happens all the time. That's what people do.
Making a backup of the pfSense config - so you can step back with the click of a button - is a matter of .... clicking a button.
Then : remove that firewall rule that enables GUI access from the outside = as it is at best very bad practice anyway (your bank is doing you a favour in fact, they should send you a bill for this audit - and normally you would have a not so friendly talk the IT guy ....)You can show the firewall rules on your WAN interface, like this(these are mine, used for our company, a hotel ) :

but if you do not understand what these rule do or imply, don't worry, you're right, or get some one involved that understand these things.
Just for my own curiosity : You're talking about basic Payment terminal equipment here, right ? what country / bank ? or do you really want to store credit card details of people on your local equipment (and if so, why ?? beause such a thing opens a huge security can-of-worms here where I live)
-
Thanks for the reply. I am in NY state .. USA. Just a terminal machine attached to my LAN with its own IP address. Nothing is stored .. just transmitting the card and amount to the processing company.
-
Well the "fastest/simplest" way to meet your criteria of hiding the pfsense gui from the machine on your lan would be.
To create a rule to allow "your" machines IP to access the gui.. Then turn off the antilockout rule, and then a rule to block all other IPs from accessing it.
Keep in mind that rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
So put the rule that allows access to the gui from your machines IP above the rule that blocks access to the gui..
-
@jalab Thank you .. makes sense. By chance, what is the "rule" for doing this? Appreciate it.
Joe -
Rule for what - I just explained to you what rules..
I SERIOUSLY suggest you get someone in IT to do this for you - if you have no idea what I meant above about block and allow rules..
-
Thanks -- I do know how to do it .. actually set up my 2016 server and network when the IT company I hired after my other guy died completely screwed everything up .. so I guess my question is what ports and rules apply specifically to the GUI log on screen .. which is what they want blocked .. thought you could save me some time searching for this info.......
-
Well most likely default 80 or 443.. But could be anything.. Mine is on 8443 for example..
You really need to look here
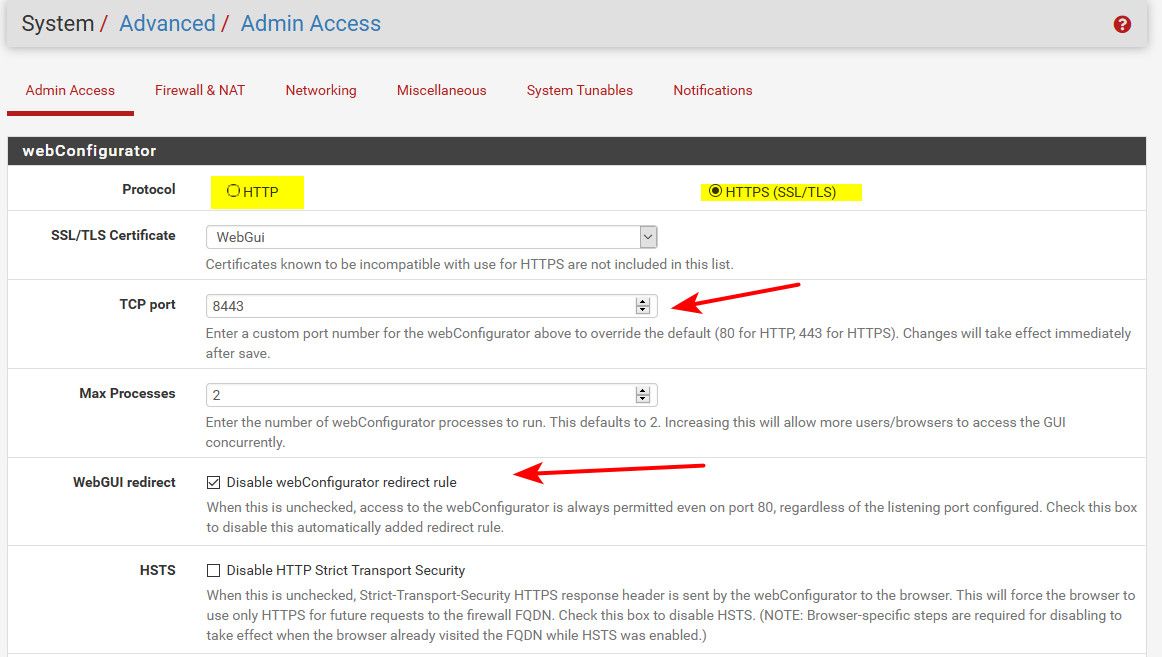
And if you have the redirect from 80 to your https port enabled or not, etc.
You could just block all access to "this firewall" alias - but then I don't know what your doing for dns, ntp, etc. Which can also point to the firewall IP. Or maybe you need to be able to ping it, etc..
This is not like 1 thing, all users setups could be different. For all we know your running only http on port 92, etc.
Your antilock rule would show you what ports are being used for the gui, and ssh if your using that, etc.
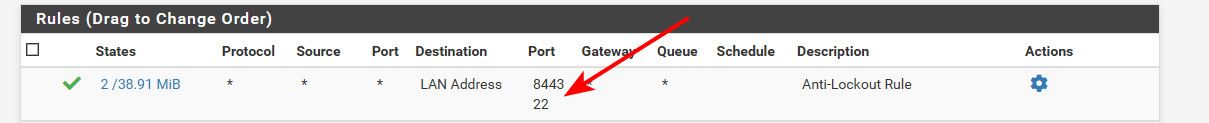
-
This post is deleted! -
Perfect .. that helped immensely .. Thank you!!