pfSense HAproxy and Let's Encrypt
-
I'm running pfSense 2.4.5-RELEASE-p1.
I have followed the setup for using pfsense haproxy and let's encrypt using the same configuration as described here to create a wildcard cert for my domain: https://www.youtube.com/watch?v=FWodNSZXcXs
I've entered my ISPs Client ID and secret into the Acme Certificate configuration and have successfully created the cert.
I've setup 2 different test websites, one on Windows Server 2016 and one on a Synology NAS. I setup the front end and backend haproxy settings the same way and made sure my cert was in the Frontend settings.
When I browse to either website I get to the websites but they still show "Not Secure".
What am I missing?
-
@timcin said in pfSense HAproxy and Let's Encrypt:
What am I missing?
No idea because you haven't actually posted what you have done.
-
@timcin https certificates only work with domain names and the browser will throw a warning if connecting by IP address. If you did connect to your services by domain name then you have a configuration error. Look at the certificate in the browser making sure it is using *.yourdomain.com.
-
@papdee
Thanks for the reply.
I have used my official domain name.
I've also setup a CAA record on my DNS provider's DNS page.The cert is there in the pfsense cert manager and it was successful in being created however it is not being forwarded to the website. All I see on the website is "Not Secure" and when I click on that to see the certificate there is none there.
-
open up terminal and type in:
openssl s_client -showcerts -connect www.yourdomain.com:443 </dev/null
this will let you see if you actually have a certificate, who it belongs to, and can be read by the connecting client.
If this fails then check you actually have been issued a valid certificate by ACME script on the pfsense box by opening a shell and typing:
openssl x509 -in etc/ssl/certs/yourdomain.com.pem -text
If it shows a valid certificate then it is most likely a misconfiguration with HAPROXY. Make sure HAPROXY is terminating the HTTPS connection on the front side.
-
Still zero info on how you have haproxy setup, or how your actually trying to connect.
I run 2 different certs with https offload on haproxy. I even share this port 443 that I listen on the outside.. And access both resources fine from the inside bouncing off the proxy, or outside..
Here example - this would be a start.. Showing how your setup. You can see my frontends, and backend setup for this site.
And then me accessing it via browser. Showing its using acme.
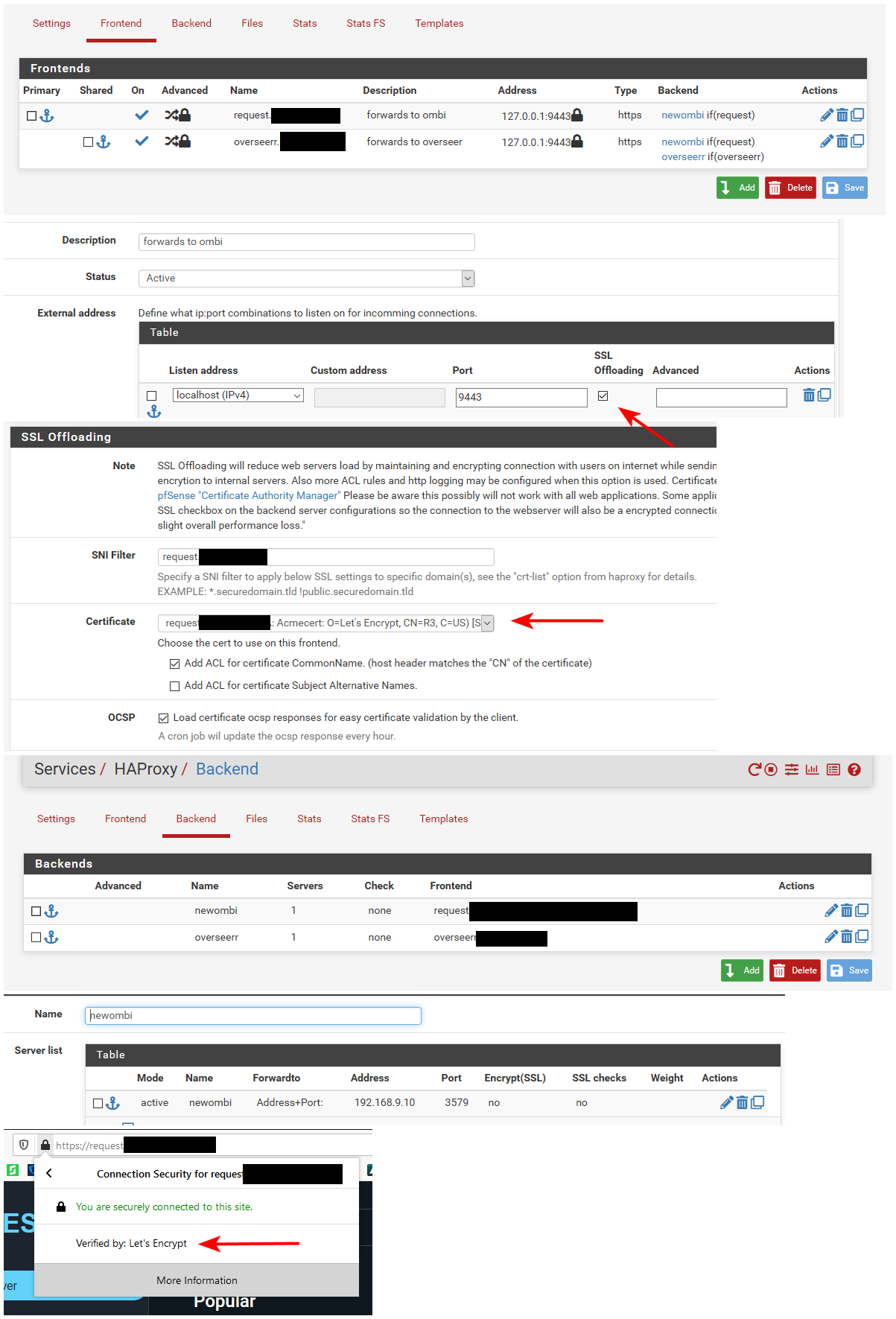
The frontend does the ssl offload, while the proxy talks to the back over just http to specific port.
-
@papdee said in pfSense HAproxy and Let's Encrypt:
openssl x509 -in etc/ssl/certs/yourdomain.com.pem -text
Correction...
openssl x509 -in /conf/acme/yourdomain.com.pem -text
and
openssl x509 -in /conf/acme/yourdomain.com.all.pem -text
finally....
make sure on the backend you UNCHECK the option to check the server certificate if you are using a self-signed certificate on your backed servers and using HTTPS OFFLOADING on the frontend.
-
Ok, now that I have time today I can respond.
I cleared out all the certs I had made except for my open vpn cert.
Starting out new.
You can see I replaced my actual domain name and username for this post.
Also I took some of the the cert info in the begin certificate area to shorten the post.I created a Staging cert for a test web server called XYZ.
After creating the cert I tried running your commands. The first one just got
stuck and I had to do a CTRL-C to get back to the prompt. The second command
could not see the certs. So you can see I went to the actual folder and the
cert is there.Cert_for_XYZ Renewing certificate account: Test keys for XYZ test site server: letsencrypt-staging-2 getCertificatePSK creating new key /usr/local/pkg/acme/acme.sh --home '/tmp/acme/Cert_for_XYZ/' --accountconf '/tmp/acme/Cert_for_XYZ/accountconf.conf' --createDomainKey -d 'www.mydomainname.com' --keylength '2048' --log-level 3 --log '/tmp/acme/Cert_for_XYZ/acme_createdomainkey.log' Array ( [path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ ) [Sat Apr 24 09:44:34 EDT 2021] Creating domain key [Sat Apr 24 09:44:35 EDT 2021] The domain key is here: /tmp/acme/Cert_for_XYZ//www.mydomainname.com/www.mydomainname.com.key LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBdWZyaWZ6W~ ~ ~ ~ VYTJyVwpPbHozMVVFUTJwLy9ndzRyWHlwWmV6YzZ1STZycUNnYzZXRHdBb0dZVlRNVlZYdGc4MjhHCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg== /usr/local/pkg/acme/acme.sh --issue -d 'www.mydomainname.com' --dns 'dns_dynu' --home '/tmp/acme/Cert_for_XYZ/' --accountconf '/tmp/acme/Cert_for_XYZ/accountconf.conf' --force --reloadCmd '/tmp/acme/Cert_for_XYZ/reloadcmd.sh' --log-level 3 --log '/tmp/acme/Cert_for_XYZ/acme_issuecert.log' Array ( [path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [Dynu_ClientId] => ################## [Dynu_Secret] => #################### ) [Sat Apr 24 09:44:44 EDT 2021] Registering account [Sat Apr 24 09:44:45 EDT 2021] Already registered [Sat Apr 24 09:44:45 EDT 2021] ACCOUNT_THUMBPRINT='uAje2PM2jB8k7vE2mhhu-zZaygw6Vh1O0aMak15Aefg' [Sat Apr 24 09:44:45 EDT 2021] Single domain='www.mydomainname.com' [Sat Apr 24 09:44:45 EDT 2021] Getting domain auth token for each domain [Sat Apr 24 09:44:47 EDT 2021] Getting webroot for domain='www.mydomainname.com' [Sat Apr 24 09:44:48 EDT 2021] Adding txt value: inw4XWyk_CfOCrTFH1TmjBpT13bxxey1-nlcYzmjbyE for domain: _acme-challenge.www.mydomainname.com [Sat Apr 24 09:44:48 EDT 2021] Getting Dynu token. [Sat Apr 24 09:44:48 EDT 2021] Getting https://api.dynu.com/v2/dns/getroot/www.mydomainname.com [Sat Apr 24 09:44:49 EDT 2021] Getting https://api.dynu.com/v2/dns/getroot/mydomainname.com [Sat Apr 24 09:44:49 EDT 2021] Creating TXT record. [Sat Apr 24 09:44:51 EDT 2021] The txt record is added: Success. [Sat Apr 24 09:44:51 EDT 2021] Let's check each dns records now. Sleep 20 seconds first. [Sat Apr 24 09:45:11 EDT 2021] Checking www.mydomainname.com for _acme-challenge.www.mydomainname.com [Sat Apr 24 09:45:12 EDT 2021] Domain www.mydomainname.com '_acme-challenge.www.mydomainname.com' success. [Sat Apr 24 09:45:12 EDT 2021] All success, let's return [Sat Apr 24 09:45:12 EDT 2021] Verifying: www.mydomainname.com [Sat Apr 24 09:45:16 EDT 2021] Success [Sat Apr 24 09:45:16 EDT 2021] Removing DNS records. [Sat Apr 24 09:45:16 EDT 2021] Removing txt: inw4XWyk_CfOCrTFH1TmjBpT13bxxey1-nlcYzmjbyE for domain: _acme-challenge.www.mydomainname.com [Sat Apr 24 09:45:16 EDT 2021] Getting Dynu token. [Sat Apr 24 09:45:16 EDT 2021] Getting https://api.dynu.com/v2/dns/getroot/www.mydomainname.com [Sat Apr 24 09:45:17 EDT 2021] Getting https://api.dynu.com/v2/dns/getroot/mydomainname.com [Sat Apr 24 09:45:18 EDT 2021] Checking for TXT record. [Sat Apr 24 09:45:18 EDT 2021] Getting https://api.dynu.com/v2/dns/100086013/record [Sat Apr 24 09:45:18 EDT 2021] Removing TXT record. [Sat Apr 24 09:45:28 EDT 2021] Removed: Success [Sat Apr 24 09:45:28 EDT 2021] Verify finished, start to sign. [Sat Apr 24 09:45:28 EDT 2021] Lets finalize the order, Le_OrderFinalize: https://acme-staging-v02.api.letsencrypt.org/acme/finalize/19228281/38184595 [Sat Apr 24 09:45:29 EDT 2021] Download cert, Le_LinkCert: https://acme-staging-v02.api.letsencrypt.org/acme/cert/fa61fed98f212813d7b54f17cb5f099a0334 [Sat Apr 24 09:45:30 EDT 2021] Cert success. -----BEGIN CERTIFICATE----- MIIFVTCCBD2gAwIBAgITAPph/tmPISgT17VPF8tfCZoDNDANBgkqhkiG9w0BAQsF~ ~ ~ ~ 99YGoLoYVep2QwimrZNtv/9QzvEZWp/r0YMjv8flP2hy0shdzDtsNg2LzfvTk4de ZJjfl0HGNGg5jAY0AYylVmPePduUSG5dl2z97HgUvl3xz1gRA/ANG/lM2hMWr0m+ WshWGIS2SbbiuroshnlR/J+fVmeSUX7Agg== -----END CERTIFICATE----- [Sat Apr 24 09:45:30 EDT 2021] Your cert is in /tmp/acme/Cert_for_XYZ//www.mydomainname.com/www.mydomainname.com.cer [Sat Apr 24 09:45:30 EDT 2021] Your cert key is in /tmp/acme/Cert_for_XYZ//www.mydomainname.com/www.mydomainname.com.key [Sat Apr 24 09:45:30 EDT 2021] The intermediate CA cert is in /tmp/acme/Cert_for_XYZ//www.mydomainname.com/ca.cer [Sat Apr 24 09:45:30 EDT 2021] And the full chain certs is there: /tmp/acme/Cert_for_XYZ//www.mydomainname.com/fullchain.cer [Sat Apr 24 09:45:30 EDT 2021] Run reload cmd: /tmp/acme/Cert_for_XYZ/reloadcmd.sh IMPORT CERT Cert_for_XYZ, /tmp/acme/Cert_for_XYZ/www.mydomainname.com/www.mydomainname.com.key, /tmp/acme/Cert_for_XYZ/www.mydomainname.com/www.mydomainname.com.cer update cert![Sat Apr 24 09:45:36 EDT 2021] Reload success
[2.4.5-RELEASE][username@pfSense.mydomain.com]/home/username: openssl x509 -in /conf/acme/mydomain.com.pem -text
Error opening Certificate /conf/acme/mydomain.com.pem
34380815688:error:02001002:system library:fopen:No such file or directory:/build/ce-crossbuild-245/sources/FreeBSD-src/crypto/openssl/crypto/bio/bss_file.c:413:fopen('/conf/acme/mydomain.com.pem','r')
34380815688:error:20074002:BIO routines:FILE_CTRL:system lib:/build/ce-crossbuild-245/sources/FreeBSD-src/crypto/openssl/crypto/bio/bss_file.c:415:
unable to load certificate[2.4.5-RELEASE][username@pfSense.mydomain.com]/home: cd /conf/acme
[2.4.5-RELEASE][username@pfSense.mydomain.com]/conf/acme: ls
Cert_for_XYZ.all.pem mydomain_GUI.all.pem
Cert_for_XYZ.ca mydomain_GUI.ca
Cert_for_XYZ.crt mydomain_GUI.crt
Cert_for_XYZ.fullchain mydomain_GUI.fullchain
Cert_for_XYZ.key mydomain_GUI.keyNext steps are to go into haproxy and setup the backend and frontend.
-
Well, I finally go it to work. I recreated my test configuration and now the cert shows up on my test website. Don't know what the problem was. There must have been some error somewhere.
-
@timcin said in pfSense HAproxy and Let's Encrypt:
There must have been some error somewhere.
Wouldn't know with the zero amount of details you provided.. Other than you renewing your acme cert log? <rolleyes>
Or that you can not run some cmd line details on something that has also zero do do with nothing..
Glad you got it working - but this thread is completely useless to anyone ever having any sort of issue at all.
-
@johnpoz you a moderator?
-
Do you have some sort of problem with my personal opinion of the lack of info given in this thread @papdee
Yes I am a global moderator.. That has little to do with my personal opinion on specifics, just like you can post your opinion on something, so can I ;)
Where did the OP give any details worth anything? Love for you to point them out to me..
Do you actually feel this thread has use to the next guy having a problem? I am not seeing it.