sshguard and oddities in the daily system log email
-
Version 2.5.1-RELEASE(amd64) with an Intel(R) Atom(TM) Processor E3950 @ 1.60GHz
Current: 800 MHz, Max: 1601 MHz 4 CPUs: 1 package(s) x 4 core(s) AES-NI CPU Crypto: Yes (active)I get a daily email from pfsense, and while it has obviously been happening for awhile now, I wanted to see what others think.
The system log is filled with this:
Apr 24 22:45:09 pfsense sshd[84241]: Did not receive identification string from 192.168.2.1 port 12268
Apr 24 22:45:09 pfsense sshguard[84766]: Attack from “192.168.2.1” on service SSH with danger 10.
Apr 24 22:45:09 pfsense sshd[85755]: Did not receive identification string from 192.168.2.1 port 46048
Apr 24 22:45:09 pfsense sshguard[84766]: Attack from “192.168.2.1” on service SSH with danger 10.Network config is this:
WAN-192.168.1.3
LAN/PFSense-192.168.2.1
Then VL20, VL30, VL40, VL50, VL60My question is, is PFsense attacking itself, since the attack appears to originate from the PFSense appliance itself?
I do have rules blocking access to the appliance itself, and I am only able to access the appliance from one computer, located on VL20(this PC, 192.168.20.2).
I do occasionally access the cli(updates) for the pfsense appliance, but usually do most things through the gui.
Should I be concerned? Or is this normal chatter?I did read this forum post. https://forum.netgate.com/topic/143932/solved-sshguard-59300-attack-from-192-xx-xx-xx-on-service-100-with-danger-10 ,however those attempts were coming from a linux workstation and these are coming directly from the appliance.
-
@mtarbox said in sshguard and oddities in the daily system log email:
My question is, is PFsense attacking itself, since the attack appears to originate from the PFSense appliance itself?
Looks like it : if "192.168.2.1" is the source... well.... dono.
What about blocking packets incoming on your LAN, with source 192.168.2.1 (TCP port 22) ?
Because a 'default' pfense would not SSH into itself I advise you to :
Reset to default and see it stops doing SSH into itself. So now you know it's your config.
With the config, but will all the VLAN deleted (using plain flat switches etc - the easy stuff) does it stop SSH'ing itself ? If so, you know now it's your config. -
@gertjan I shut down ssh. The chatter stopped immediately.
Apr 26 09:07:18 php-fpm 33833 /system_advanced_admin.php: secure shell configuration has changed. Stopping sshd.
Apr 26 09:07:18 sshd 20368 Received signal 15; terminating.Still would like to know why it was doing that. The appliance isn't forward facing, and I can only access the appliance from one machine(actually two now, but the other is my laptop which is sitting in my bag).
-
System -> Advanced -> Admin Access -> Login Protection Add your local subnets
-
@nogbadthebad I implemented that, and restarted ssh. Maybe it just needed a swift kick in the pants? I will keep an eye on the logs and move forward from there.
edit it started back up within a couple of minutes. SSH is once again turned off.
-
@mtarbox said in sshguard and oddities in the daily system log email:
I shut down ssh. The chatter stopped immediately.
Well, yeah, when there is not ssh running, it can't log.
And because it can't log, another process, sshguard can't find suspected log lines from ssh.This doesn't mean that something is still accessing 192.168.2.1, the port 22.
Two ways to make sur nothing goes wrong :
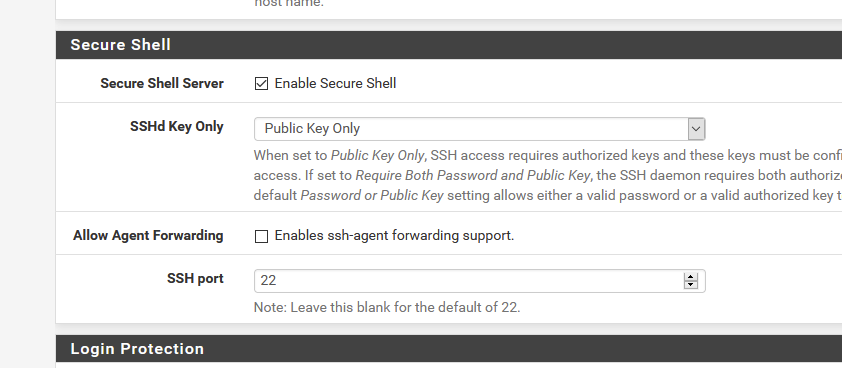
First of all : use only "Public key" (password login is bad - not done anymore except for the first time yuou connect to your new device)
Next : change port 22 to port 1022 ;)
Then use sockstat (and packet capture) and friends to see who wrom where tries to connect to your port 22.
-
@gertjan now that seemed to work. With ssh enabled, public key enabled and a change to the port number, there is no activity. I am able to ssh into the appliance. Nothing is hammering on the logs, whether I use diagnostics/packet capture or wireshark.
I will check the logs tomorrow morning and advise.
Thank you for the assistance this morning. -
@mtarbox said in sshguard and oddities in the daily system log email:
Nothing is hammering on the logs
Most probably because it isn't the 'ssh' server that hammers itself.
Some other process still keeps on going on port 22, but doesn't know that the ones living there has moved.
So sshguard won't see the warning messages from the ssh server in the logs and doesn't add its own.
Nothing in the logs doesn't mean nothing is happening.If there is a rogue ssh client running somewhere, it should be detected and be accounted for.
wireshark on interface LAN host adresses "192.168.2.1" TCP port 22" and see what pops up.
Try all the interfaces.