Configuring multiple static ip adresses on only one NIC
-
@kom Could you please give me the example of that configuration (assigning VIPs to another gateway and making decided devices traffic over it).
I also need to access to the internet over 1.2.3.7. I want any of my servers gives response over 1.2.3.7 but also can access to the internet over 1.2.3.7 from internally.
Why I want my networks to use different public static ips is that to secure them more accurately.
if any body get into my network won't be able to find the webservers, application servers, backup servers etc. -
@antionline
Inbound NAT affects the incoming connections. Outbound NAT would be necessary if you want to have the web server connect outbound using something besides the WAN IP.If the additional IP addresses are dedicated to each web server then 1:1 NAT might be more what you're looking for.
@kom said in Configuring multiple static ip adresses on only one NIC:
I'm not seeing why you are needing to put your normal traffic out 1.2.3.7 instead of 1.2.3.4
One reason would be if the web server is for a client and the client is told its IP is 1.2.3.7 but then a different IP is used for outbound connections.
-
@antionline Having different virtual WANs doesn't make anything more secure. Put your servers on a VLAN or separate VLANs instead.
-
@steveits That's already happening by default. The web serve responds to 1.2.3.7 and replies under that address, but it's outbound comms use the default WAN.
-
@kom said in Configuring multiple static ip adresses on only one NIC:
but it's outbound comms use the default WAN.
From my reading, that's what he wants to change.
-
@steveits For a home config I still don't understand why the web server(s) need to fetch their updates via a specific WAN address, but I suppose he could go to System - Routing - Gateways and add his extra IPs as gateways, then create an outbound NAT rule to direct his servers out those gateways.
-
I guess I'm not trying to analyze the reason. :) I do know I've been in that situation though where someone else is hosting a web server and I have to figure out what different IP connects out to SQL or whatever else, so I can set a firewall rule.
Here's a link to the Outbound NAT docs for the OP. I've not had to mess with gateways to get outbound NAT to work, though?
-
@steveits said in Configuring multiple static ip adresses on only one NIC:
I've not had to mess with gateways to get outbound NAT to work, though?
If your outbound mode is auto then I believe these are created for you automagically when you create the gateway, but if you're using manual or hybrid, you have to create them yourself.
-
@kom Yes I already have 5 vlans, all seperated and blocking each other LAN to LAN.
-
@kom YES default gateway IP remains, using outbond connections as virtual ip doesn't effect the main WAN nic connection ip. I think I have to but nevest model of pfsense which has more than 1 WAN input port.
-
@kom
My configuration is small business.1.2.3.4 -> MAIN WAN ip
Additive ip blocks below
50.50.50.1
50.50.50.2
50.50.50.3
50.50.504All of the 5 static ip has the same gateway ip -> 1.2.3.3 provided from my ISP
-
@steveits Hi steve,
You can think like we have 2 seperate buildings. 1 building has the data center , 2 building is office.
I am trying to access internet over 1 nic WAN port with several ip blocks.
My datacenter should have a different ip adress from my office ip.
Still not figured it out yet.
I keep trying several combinations..
-
@antionline
Don't forget that you need a firewall rule on each vlan interface that directs the traffic to the gateway you want. The default Allow All to Any rules use the default gateway.Also bear in mind that I have never done this myself and might be talking out of my ass.Edit: Looks like ass it is. You can't add VIPs as gateways and most of what I said was nonsense. I'm curious enough to spin this up and try it. I'll let you know what I find.
Edit2: OK that wasn't too hard. Create your VIPs for each extra IP address you own. Go to Firewall - NAT - Outbound. Change your mode to Hybrid and then Save.
In my lab, I have the following:
WAN: 10.10.3.1/16
LAN: 192.168.2.1/24
OPT1: 192.168.3.1/24
VIPs: 10.10.3.2, 10.10.3.3, 10.10.3.4
Client1: 192.168.2.11
Client2: 192.168.3.11In my case, when I ping out from Client 1 or 2, the target shows the traffic coming from 10.10.3.1 which is my pfSense WAN address.
Add an outbound NAT rule:
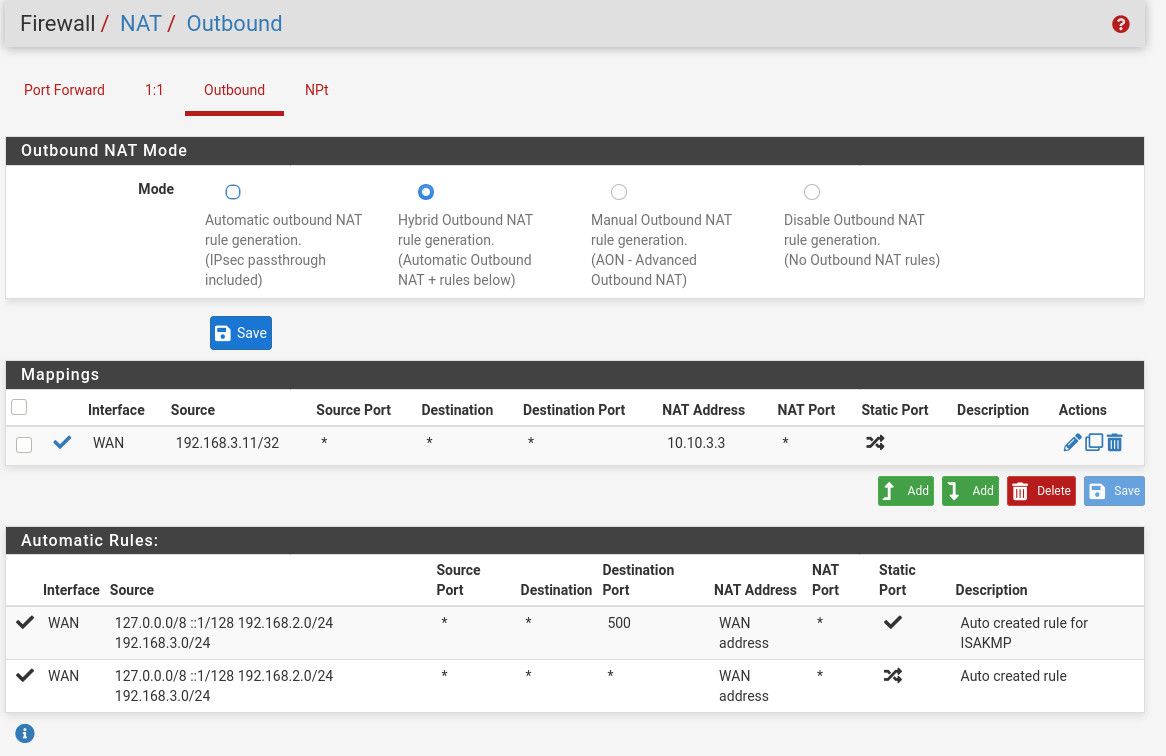
The top rule shows that my Client2 at 192.168.3.11 is going to have its outbound traffic NAT'd to be coming from 10.10.3.3 instead of my WAN's address 10.10.3.1. Make sure you use a /32 mask if it's just one host you're NATing.
10:41:09.792137 IP 10.10.3.3 > 10.10.4.1: ICMP echo request, id 14027, seq 1, length 64 10:41:09.792175 IP 10.10.4.1 > 10.10.3.3: ICMP echo reply, id 14027, seq 1, length 64 10:41:10.794770 IP 10.10.3.3 > 10.10.4.1: ICMP echo request, id 14027, seq 2, length 64 10:41:10.794791 IP 10.10.4.1 > 10.10.3.3: ICMP echo reply, id 14027, seq 2, length 64 10:41:11.798430 IP 10.10.3.3 > 10.10.4.1: ICMP echo request, id 14027, seq 3, length 64 10:41:11.798460 IP 10.10.4.1 > 10.10.3.3: ICMP echo reply, id 14027, seq 3, length 64 10:41:12.802155 IP 10.10.3.3 > 10.10.4.1: ICMP echo request, id 14027, seq 4, length 64 10:41:12.802183 IP 10.10.4.1 > 10.10.3.3: ICMP echo reply, id 14027, seq 4, length 64 -
@kom You know this job. this works very well. I can ping remotely via another public static ip immediately. seems very good solution. well done.
Ok Now I have another problem, one of my server is "windows server 2019". When I change the outbond NAT of my servers public Ip changes.(works ok). But on the other hand I have virtualization under this server which is centos 7 installed via hyperv.
servers client ip is 192.168.0.51
centos virtualization client ip is 192.168.0.41When I "dig +short myip.opendns.com @resolver1.opendns.com" to get the centos public ip it returns 10.10.10.1 which is "Auto created rule for ISAKMP - localhost to WAN" by pfsense-> pfblockerNG.
How can I make my centos virtualization's public static ip to real ip adress instead of pfsense auto ruleset controlled one(10.10.10.1)?
-
@antionline External DNS for your domain is controlled by you I assume, so you can assign any IP address you want to myip.opendns.com. Nothing to do with pfSense.
-
@kom
I add bypass script under DNS Resolver-> General Settings->Custom Options at the below of the page.Added this;
server:
access-control-view: 192.168.0.41/32 bypass
access-control-view: 192.168.0.0/16 dnsbl
do-tcp: yes
minimal-responses: yes
prefetch: yes
qname-minimisation: yes
rrset-roundrobin: yes
view:
name: "bypass"
view-first: yes
view:
name: "dnsbl"
view-first: yes
include: /var/unbound/pfb_dnsbl.*confThan I $ dig +short myip.opendns.com @resolver1.opendns.com -> returned and resolved normal public ip instead of PFBLOCKERNG VIP 10.10.10.1..
-
@antionline Could you not have just added a host override to point your domain to your internal IP address?
-
@kom I could find bypass methodby scripting, I don't know how to override method.
-
@antionline Services - DNS Resolver. Scroll down to the bottom, Host Overrides.
-
@kom I added my host override section. it is the same thing with my bypass script.
Can both bypasses PfblockerNG?