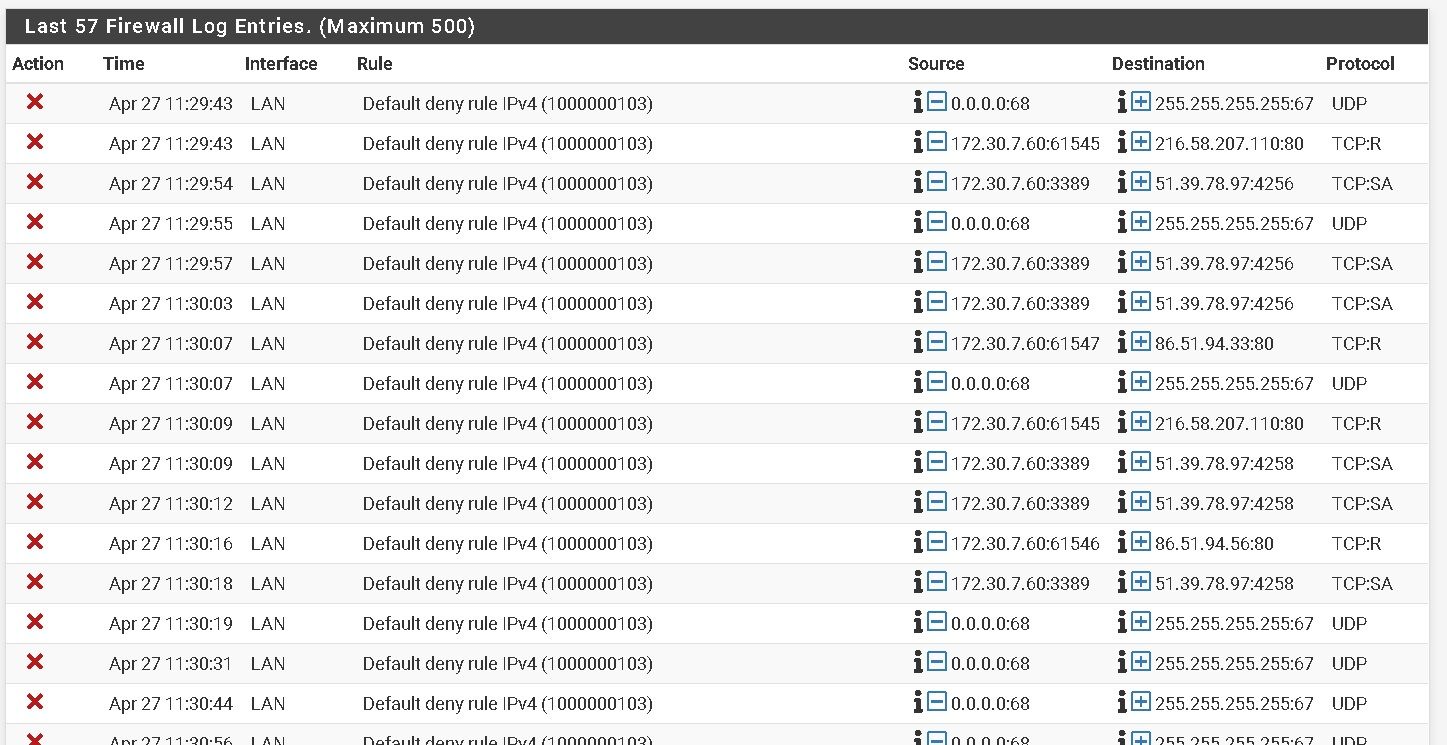
Can not forward RDP port behind a router
-
Yes is connection on cisco and when I try direct connection I put my router as pc gateway and t works, and when I try with pfsense I put pfsense LAN interface as gateway on pc.
Public IP ==> CISCO ==> VLAN 2 ==>172.30.2.100 ==> Pfsense ==> VLAN7 ==> 172.30.7.245 ==> local PC ==> 172.30.7.60
My pfsense is default configuration, I did not add any thing except nat rule
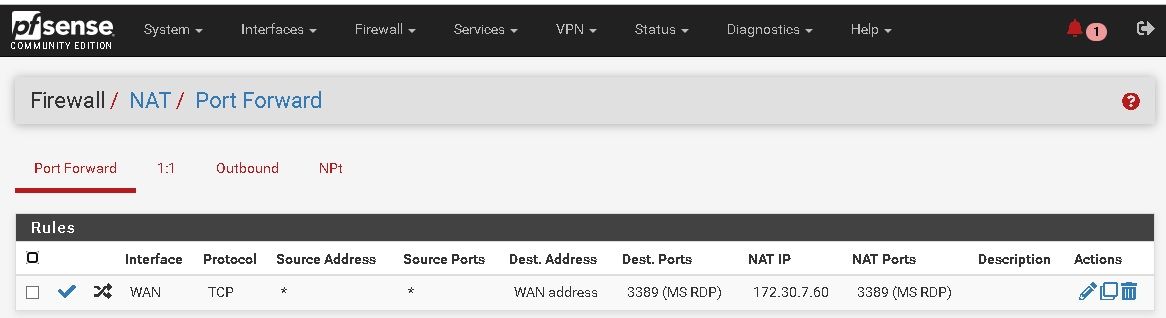
and disable RFC 1918 on WAN
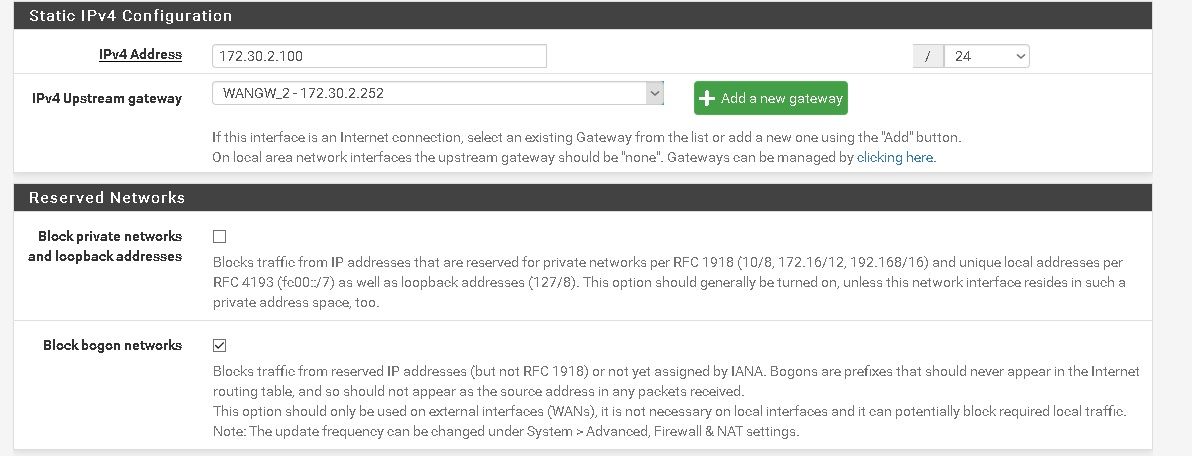
-
@am-steen said in Can not forward RDP port behind a router:
Main router ip 172.30.7.225
pfsense lan ip 172.30.7.245
pfsense wan ip 172.30.2.100 ==> vlan 2
my client pc 172.30.7.60Presuming these network are all /24, your main routers LAN, the pfSense LAN and your PC are within the same network segment. That is the best recipe for asymmetric routing.
It can only work that way if you do masquerading on this connection on pfSense. -
@viragomann
The problem is that my router and client pc are on same network so that I use vlans to add pfsense as it needs different in and out subnets.
My router and client pc are on network 172.30.7.0 so I add vlan2 for pfsense wan and I left vlan7 (172.30.7.0) for its lan, in this situation I can forward RDP port to client pc .
If there is some way to add pfsense wan and lan on same network this solves the problem.
One note I can not change main router sub net.Is there are any other solutions ???
-
@am-steen
As mentioned above, I assume the SYN packet of the RDP does not pass pfSense.
So how do you get the RDP connection from outside to pfSense WAN address?It's a poor setup though, but it should work, if you forward RDP to pfSense on the Cisco and set pfSense LAN IP as default gateway on the PC.
-
@viragomann
Ok After adjusting IP to be on same network it seems the RDP traffic passed to pfsense nut it not connected to client pc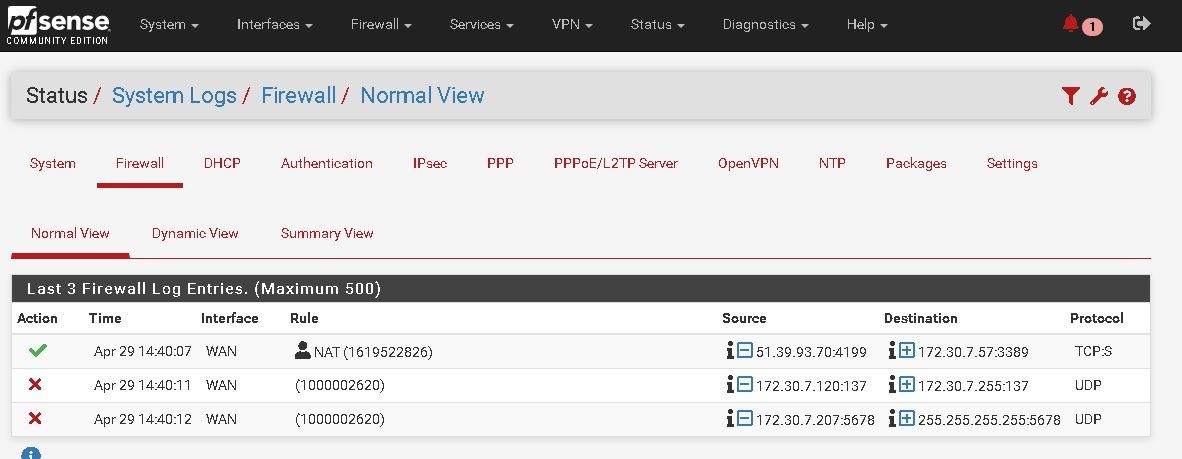
any idea ??
-
@am-steen said in Can not forward RDP port behind a router:
After adjusting IP to be on same network
What exactly did you do here?
Is pfSense still the default gateway on the destination PC?
-
@viragomann
Public ip==Main router == 192.168.60.1 == pfsense wan == 192.168.60.100
Pfsense lan == 172.30.7.245
Client pc == 172.30.7.57
Client gateway == 172.30.7.245And from log it is clear rdp traffic enters pfsense but not exiting to pc as there is no connection.
So what I am missing here ??
-
@am-steen
Maybe the client doesn't allow it?Indeed the log shows only that the Syn-packet had passed pfSense.
For further investigation sniff the traffic on the LAN interface filtered for RDP port to see if the packets are going properly to the client and if responses are coming back from it. -
@am-steen I'm not sure I'm clear yet :) but when you say the "client PC" is 172.30.7.57 do you mean that's the PC to which you're trying to connect? (your original rule shows .60) I would consider the "client" as the remote and the "host" as the target but I've seen software reverse those names before.
Definitely check the firewall on the PC, it may only be allowing connections from its local subnet. Also check that Remote Desktop is enabled, since it isn't by default.
If you are in the 172.30.7.x subnet and connecting to 192.168.60.100:3389 then ensure NAT reflection is enabled for that rule.
-
@steveits
You are right I do not understand how it works but, it works after changing NAT Reflection.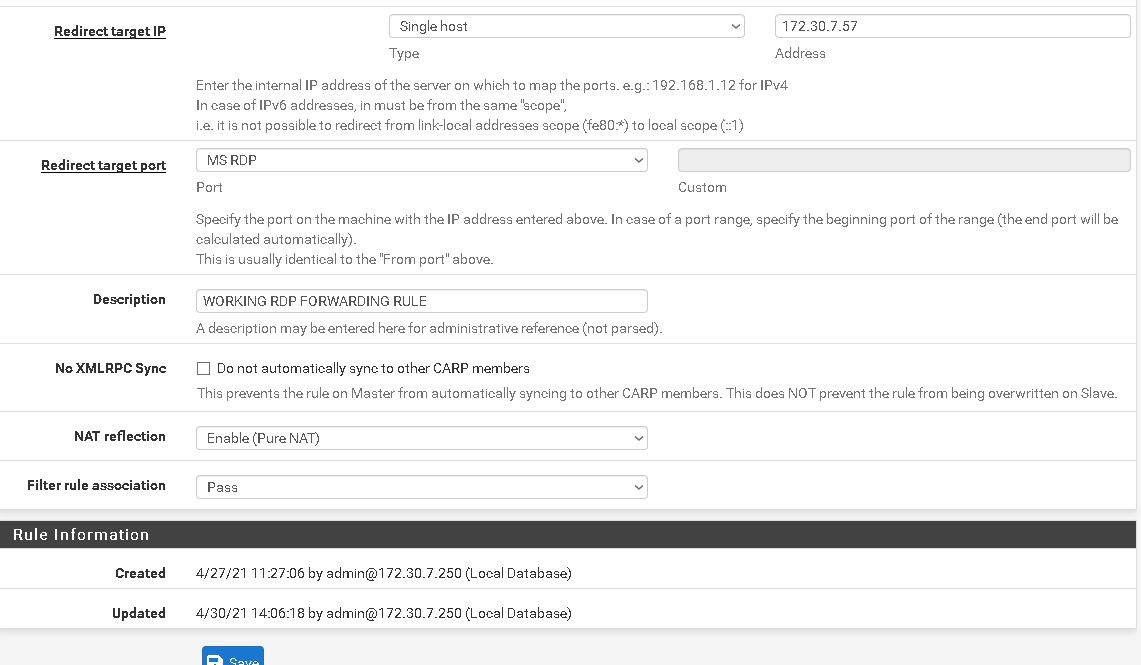
I notice that the NAT rule moved from WAN Rules
I do not understand but it works after trails -
@am-steen said in Can not forward RDP port behind a router:
I do not understand how it works but, it works
This is a very, very dangerous approach in respect of firewalls!
-
@am-steen Glad to hear it. NAT Reflection lets devices on LAN use NAT forwarded ports on the WAN.
-
@viragomann
So what to do
I disable firewall on client pc but not connecting
If RDP works that way this means that there is no issue with client pc, and the issue with pfsense.Also as I say I do not understand what NAT reflection do
Do you have another safe solution ??
-
@am-steen
No, in this case it should be okay.
However, it's not clear fo me why you succeed with NAT reflection.NAT reflection reproduces the NAT rule on the internal interface. So obviously you're hitting the pfSense WAN IP from the internal network.
I was assuming, you're accessing the external IP of the router in front of pfSense. -
@viragomann
l add packages like snort and others for protecting my network from cyber attacks,As you know the main purpose of pfsense firewall is protection.
So My question: is this NAT Reflection setting will cancel this firewall packages protection and left my network open ??
-
@am-steen
No, the NAT reflection does not decrease security. At least not concerning the firewall settings. It does exactly the same as if you copy the NAT rule from WAN to LAN, but additionally it does masquerading on the concerned packets. That means it replaces the source IP in packets into its own LAN interface IP.
So the destination device sees the access is coming from pfSense instead of the origin source IP. -
OK many thanks to you and to Mr. SteveITS also you helped me so much.