My Security Cams do not working
-
@am-steen Is the protocol correct ?
Try any, then if that work try tcp/udp.
You could do a packet capture on the host on the LAN or on the pfSense LAN interface to see what the requirements are if you don't know what protocol & ports.
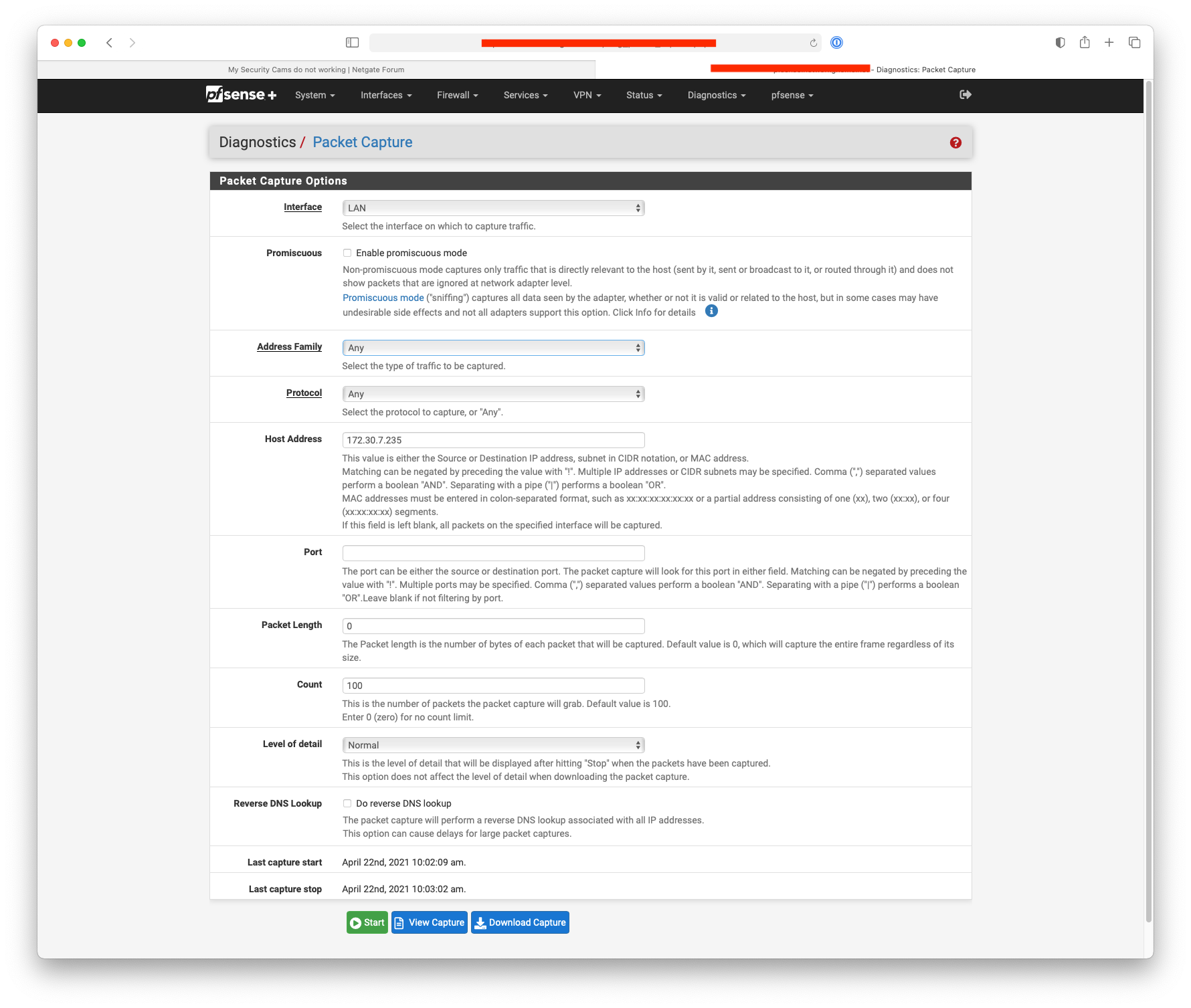
-
That rule shows no hits 0/0 - you sure your source IP is correct to allow what your wanting to allow?
You say you can ping - well something else is going on then. Because your rule is tcp only - so no ping would be allowed.
edit: If you want some client to talk to to your NVR.. Then the rule would be on the interface the client is connected too. Not on the NVR interface.
Rules are evaluated as traffic enters pfsense from the network its attached to.. First rule to trigger wins no other rules are evaluated.
If you want something to talk to vlanX from Lan - then the rule would be on the lan interface. There would be no rules required on the vlanX interface to allow that to work.
What network is 172.30.7 and what network is 172.30.5? Putting a rule on 172.30.5 to allow something to talk to it from 173.30.7 is not correct. The rule would be on 172.30.7 interface to allow traffic to 172.30.5
-
@johnpoz
Ok this is my last rule update
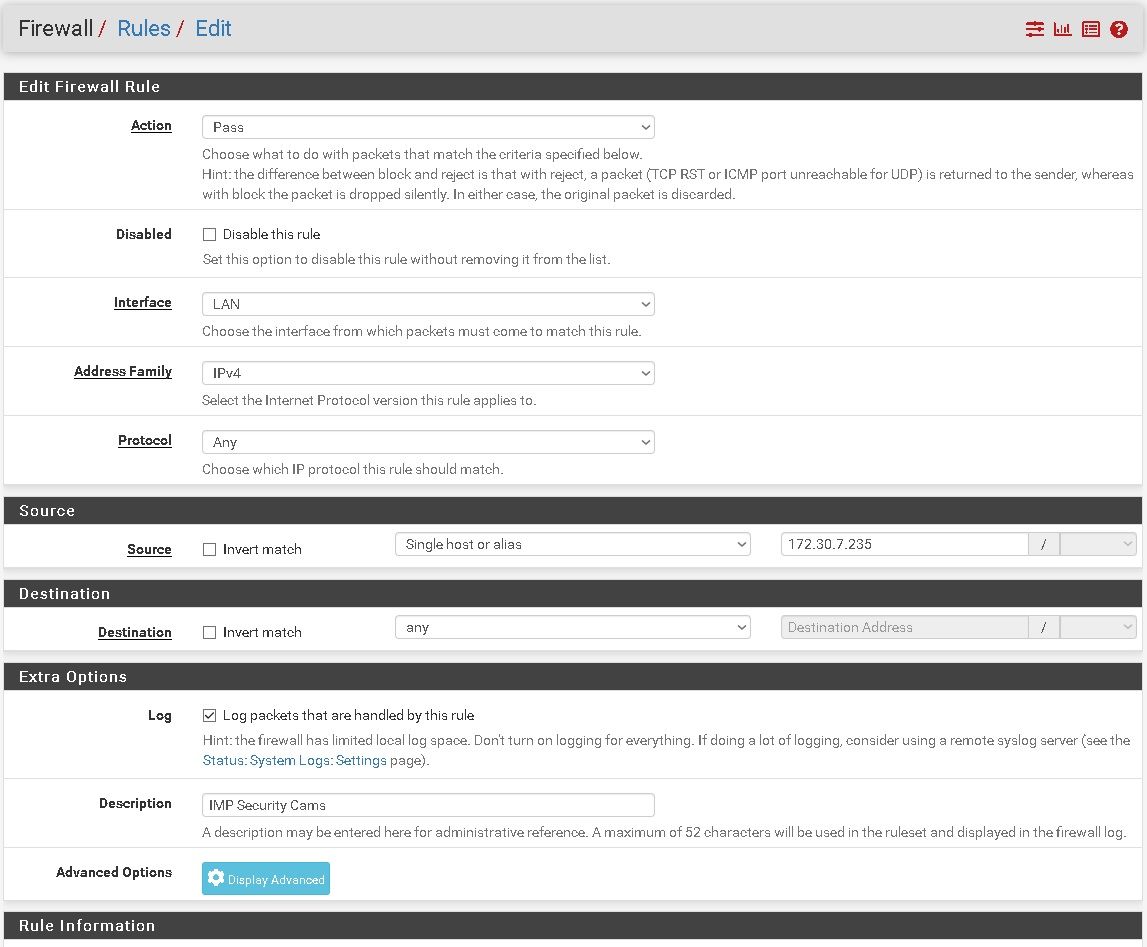
and this is firewall logs related to this pc
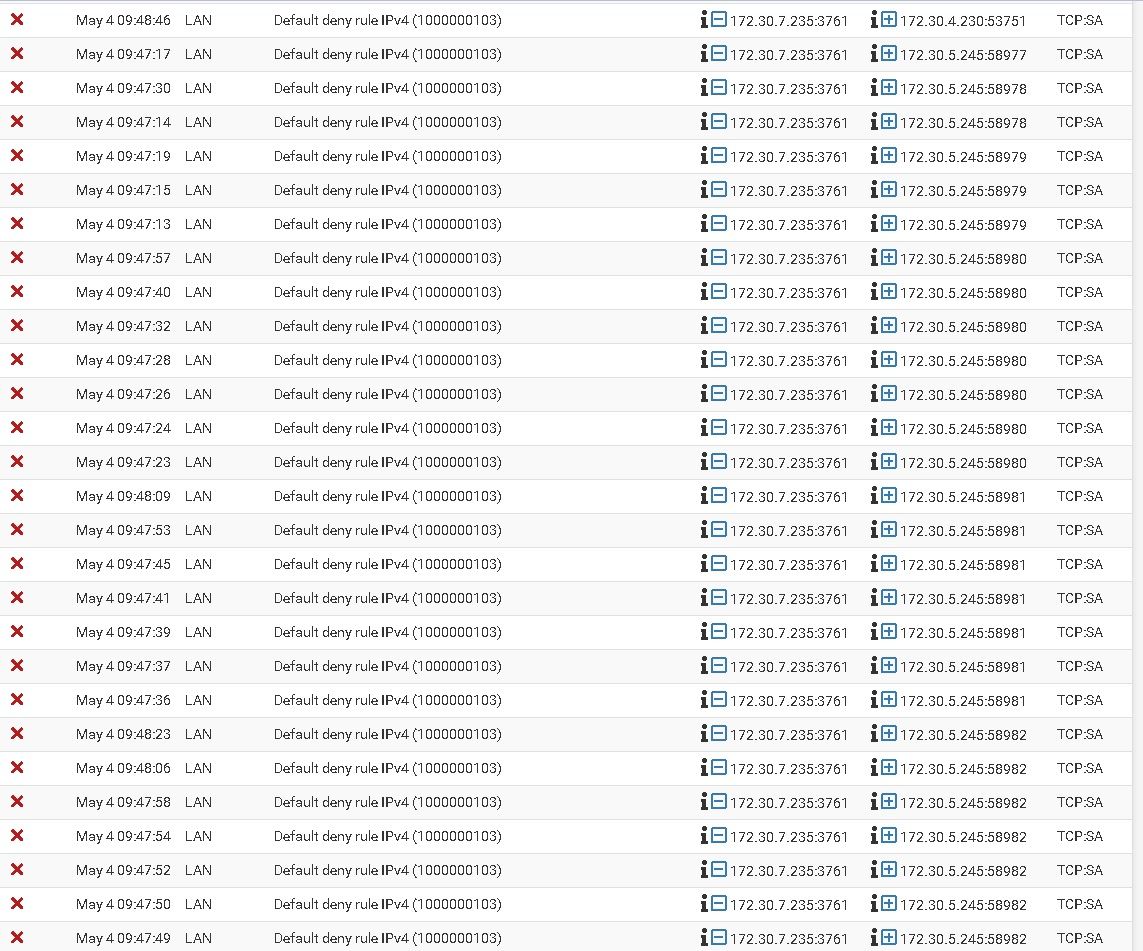
Any suggestions
-
And you have an asymmetrical problem.. Your seeing SA (syn,ack) not syn blocks.
How exactly do you have this wired?
So 5.245 tried to talk to 7.235, sends a syn to port 3761, then 7.235 answers back with syn,ack - but pfsense never saw the syn to open the state.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html
-
Are both subnets directly connected to your pfSense router, just wanting to double check?
I notice from a prevoius post you have multiple routers:-
https://forum.netgate.com/topic/163325/can-not-forward-rdp-port-behind-a-router/3?_=1620123172825
"Public IP ==> CISCO ==> VLAN 2 ==>172.30.2.100 ==> Pfsense ==> VLAN7 ==> 172.30.7.245 ==> local PC ==> 172.30.7.60"
-
@nogbadthebad
I modify everything since that post
Public IP ==> CISCO ==> VLAN 7 ==>192.168.60.100 ==> Pfsense ==> VLAN7 ==> 172.30.7.245 ==> local PC ==> another VLAN5 == >172.30.5.245 -
@johnpoz
Very sorry as I am Beginner at pfsense so I can not understand asymmetrical problem,
How To solve this, known that I can ping 172.30.7.235 from the pc 172.30.5.245
Another info. I cannot connect to NVR with web interface.
What is the suitable firewall rule to fix this asymmetrical problem ?? -
@am-steen said in My Security Cams do not working:
What is the suitable firewall rule to fix this asymmetrical problem ??
That is not how you fix an asymmetrical problem.
How do you have this wired together.. If these were 2 vlans attached to pfsense - then it would be impossible to have an asymmetrical problem. Unless your vlans are not actually isolated..
You see a SA block, when pfsense never saw the SYN (S) to create the state.
-
@johnpoz
Yes there are 2 VLANS connected to my pfsense and as you say are not actually isolated..
They have interconnecting through my cisco router. -
@am-steen said in My Security Cams do not working:
They have interconnecting through my cisco router.
What? You need to draw how you have things actually connected if you want anyone to be able to help you.
-
Public IP ==> CISCO ==> VLAN 7 ==>192.168.60.100-LAN ==> Pfsense Vmachine ==> LAN-VLAN7 ==> 172.30.7.245 ==> VLAN5-local PC ==> == >172.30.5.245
-
That doesn't tell me anything.
From that I would assume vlan 7 and vlan 5 are directly connected to your pfsense machine. So how is there an interconnection?
Break out the crayons if need be and provide an actual diagram showing the L2/L3 connections.
Most common issue with asymmetrical traffic is trying to use a network with hosts on it as a transit. A network that attaches more than 1 router is a transit, you do not put hosts on a transit. Or yes you end up with asymmetrical issues. Unless you host route on every host in the transit, or you nat the downstream networks at the downstream router.
Is vlan 7 and lan-vlan7 the same L2? If so why does it look like you have two different L3s on it?
-
@am-steen Create a bridge so 172.40.7.235 can ping 172.30.5.245 ... network 172.40.7.0 and network 172.30.5.0 or create a floating firewall rule.
-
@nollipfsense said in My Security Cams do not working:
Create a bridge so 172.40.7.235 can ping 172.30.5.245
NO!! That is not a solution - that is more of borked attempt at doing completely and utterly WRONG!
You don't bridge two different L3s together. If he wants to route from 1 router to 2nd router - then you do that with a transit network.
But your never going to get it to work - if you can not even draw up how you want it to work in the first place.
If he wants network A handing off router 1, and network B off router 2 - that is very simple and common to do.. You just create a transit network and setup routes at each router telling the router where to go to get to network X..
Draw up how you want it to be - and be more than happy to walk you through it.. The simple solution is to just use 1 router.. Unless you can explain why you want/need to use to routers then use just 1.. More than 1 router add complexity, and without a need to do it - why would anyone do that? In any sort of home setup, there is rarely a need to use more complex setup when there is a simpler less complex solution.
-
@johnpoz
Ok How To create a transit network
I want to direct traffic between VLAN5 and VLAN7 where each one is connected to an interface ?? -
There is no need for a transit if vlan5 and vlan7 are off the same router..
Draw your network. Grab a napkin and some crayons..
This is not a drawing
Public IP ==> CISCO ==> VLAN 7 ==>192.168.60.100 ==> Pfsense ==> VLAN7 ==> 172.30.7.245 ==> local PC ==> another VLAN5 == >172.30.5.245
Where is vlan 7? You do not have vlan7 hanging off both routers? With 2 different IP ranges?
And then what does "another" vlan 5 mean?
I want to direct traffic between VLAN5 and VLAN7 where each one is connected to an interface ??
There is no need to do anything other than firewall rules if vlan 7 and vlan 5 are both connected to pfsense. But you do not have the same L2 (vlanX) connected to 2 routers with hosts on it.. A vlan that is connected to more than 1 router is by definition a transit network. if you have a vlanX on router 1 with IP range xyz on it, you do not also have vlanX with iprange abc on a different router calling it the same vlan.. Because its not the same vlan!
edit: Here is an example..
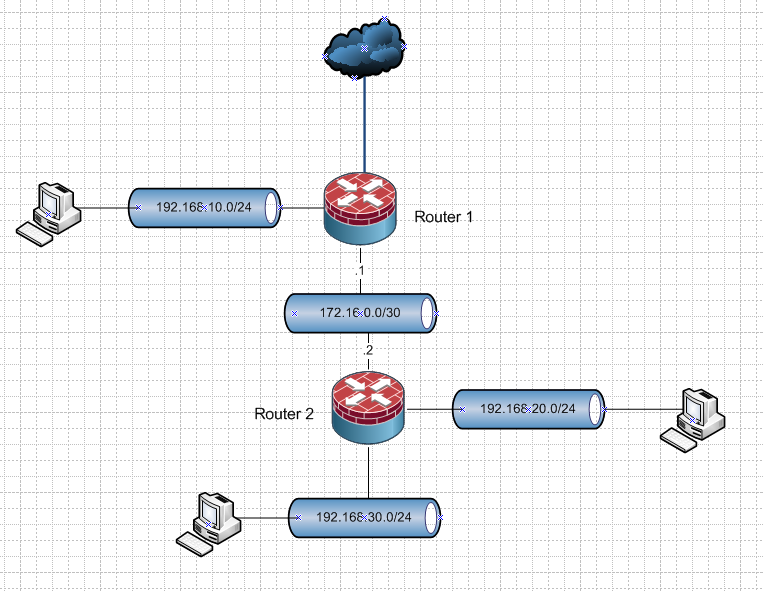
I have 2 routers, with networks hanging off both of them. Lets call them vlan 10, 20 and 30.. With their corresponding networks 192.168.10,.20 and .30 /24 on them.
The network that connects the 2 routers (NO HOSTS) on it.. Vlan 16 if you want to put an ID on it.. Is the transit.
Vlan 10,20 and 30 are not connected to both routers.
Router 1 would have a route on it, pointing to 192.168.20 and .30 to 172.16.0.2
The default route on router 2 would point to 172.16.0.1
You would need some firewall rules to allow what you want to allow to talk to what. And in such a scenario router 2 would not nat. Router 1 would be natting all the networks to the public internet.If you draw up how you have or want your stuff connected - more than happy to help on how to do that. But you don't have the same network hanging of both routers..
You don't call 192.168.10 vlan 5, and then 192.168.20 another vlan 5 ;)
edit2: If you do something like this
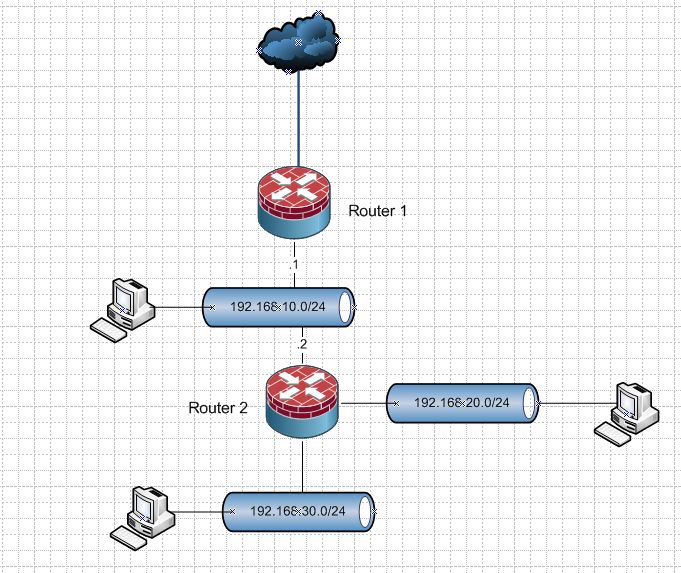
Then router 2 has to nat.. Where all traffic moving upstream looks like it came from its 192.168.10.2 address. And for 192.168.10 to talk to .20 or .30 address you would have to port forward. Or you would run into asymmetrical traffic flow. Unless you created routes on each host that sits in 192.168.10 telling each host how to get to the networks off router 2.
-
@johnpoz Okay!
-
@nollipfsense Sorry if that maybe came off a bit harsh ;)
But needed to stress that bridging 2 different network ip ranges together is never a solution and would just make matters worse..
-
@johnpoz said in My Security Cams do not working:
Sorry if that maybe came off a bit harsh ;)
Not at all, everything is cool