Kerberos Squid without authentication?
-
@mcury
thanks for the reply
so using squidguard would be the way to block users to the use internet?
but let see if i can get first squid working without the popup.once i open the navigation i get this ticket
#0> Cliente: administrador @ CASA.LOCAL Servidor: krbtgt/CASA.LOCAL @ CASA.LOCAL Tipo de cifrado de vale Kerberos: RSADSI RC4-HMAC(NT) Marcas de vale 0x40e00000 -> forwardable renewable initial pre_authent Hora de inicio: 5/7/2021 19:15:41 (local) Hora de finalización: 5/8/2021 5:15:41 (local) Hora de renovación: 5/14/2021 19:15:41 (local) Tipo de clave de sesión: RSADSI RC4-HMAC(NT) Marcas de caché: 0x1 -> PRIMARY KDC llamado: apolo.casa.local #1> Cliente: administrador @ CASA.LOCAL Servidor: LDAP/apolo.casa.local/casa.local @ CASA.LOCAL Tipo de cifrado de vale Kerberos: RSADSI RC4-HMAC(NT) Marcas de vale 0x40ac0000 -> forwardable renewable pre_authent ok_as_del egate 0x80000 Hora de inicio: 5/7/2021 19:15:41 (local) Hora de finalización: 5/8/2021 5:15:41 (local) Hora de renovación: 5/14/2021 19:15:41 (local) Tipo de clave de sesión: RSADSI RC4-HMAC(NT) Marcas de caché: 0 KDC llamado: apolo.casa.localnot sure if that counts?
-
You can leave the authentication tab in Squid disabled, and use the ldapusersearch mentioned above in Squidguard.
The popup will disappear if you do it correctly.I never tried to block using only Squid , so unfortunately I can't help you..
-
@mcury
Thanks for the reply, so i used the ldapusersearchldapusersearch ldap://apolo.casa.local:3268/dc=casa,dc=local?userPrincipalName?sub?(&(memberof=%2cCN=Users%2cDC=casa%2cDC=local)(userPrincipalName=%s))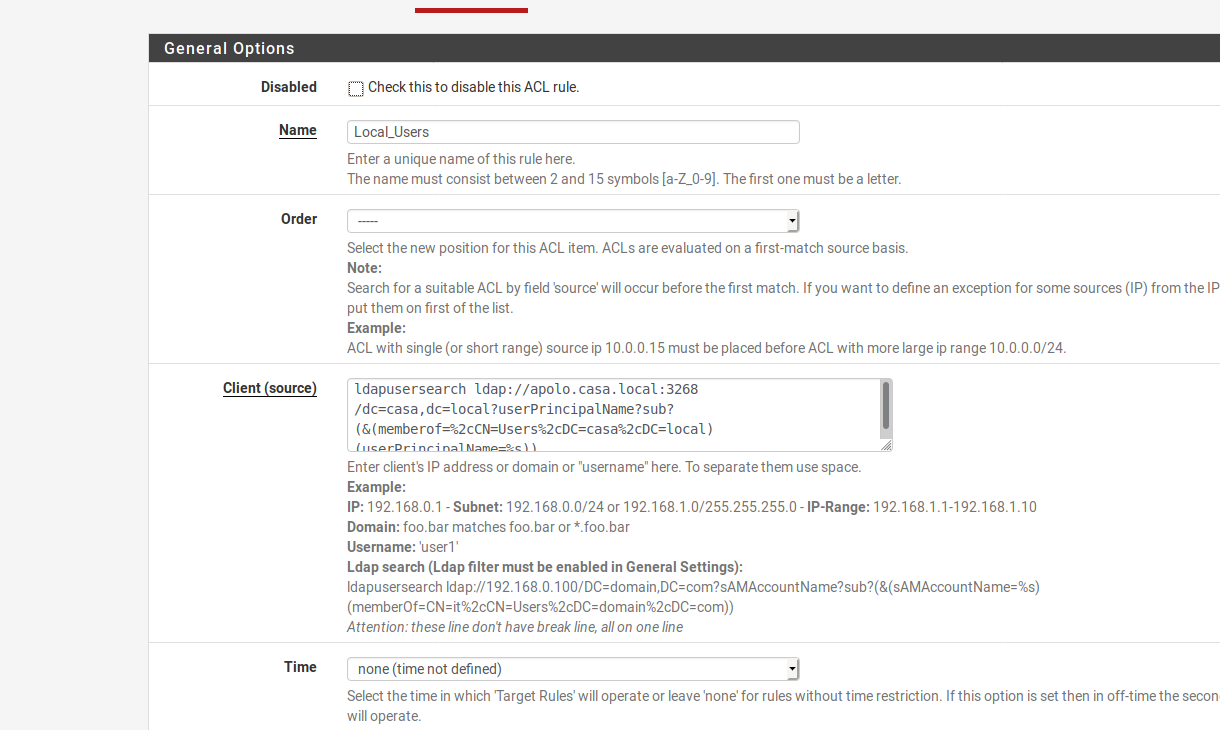
and this is the location of the usersCN=Users,DC=casa,DC=localbut im still getting the popup
i checked the squid logs so i think im missing something on squid
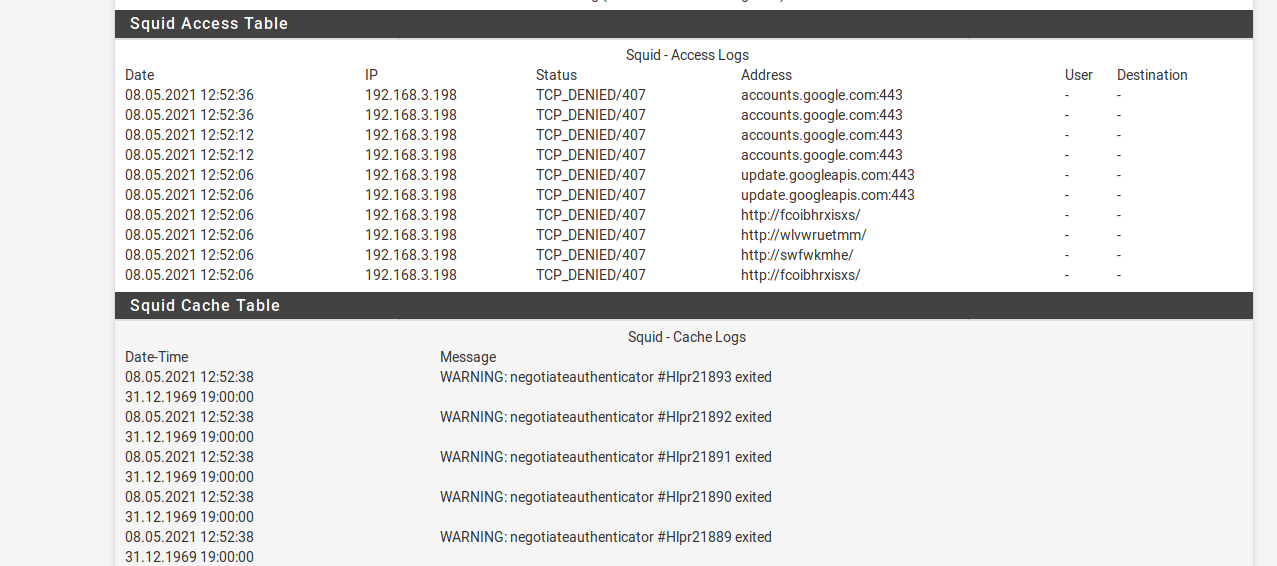
-
@killmasta93 Is the ticket being generated?
If the client is a domain member, and everything is configured correctly, the HTTP ticket will appear in klist..Check and confirm if the path to the proxy inside Internet Explorer (Windows proxy configuration), is set correctly.
Are you using Samba and DNS backend ?
If so there are some tests you can do, check the Kerberos part in the link below, also perform the DNS tests to confirm if everything is set up as it should be.https://wiki.samba.org/index.php/Setting_up_Samba_as_an_Active_Directory_Domain_Controller
-
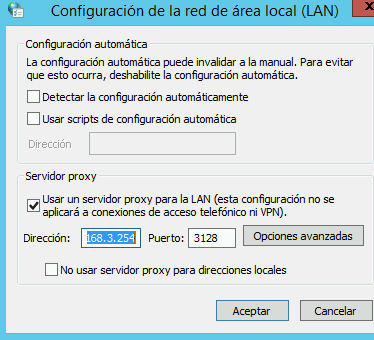
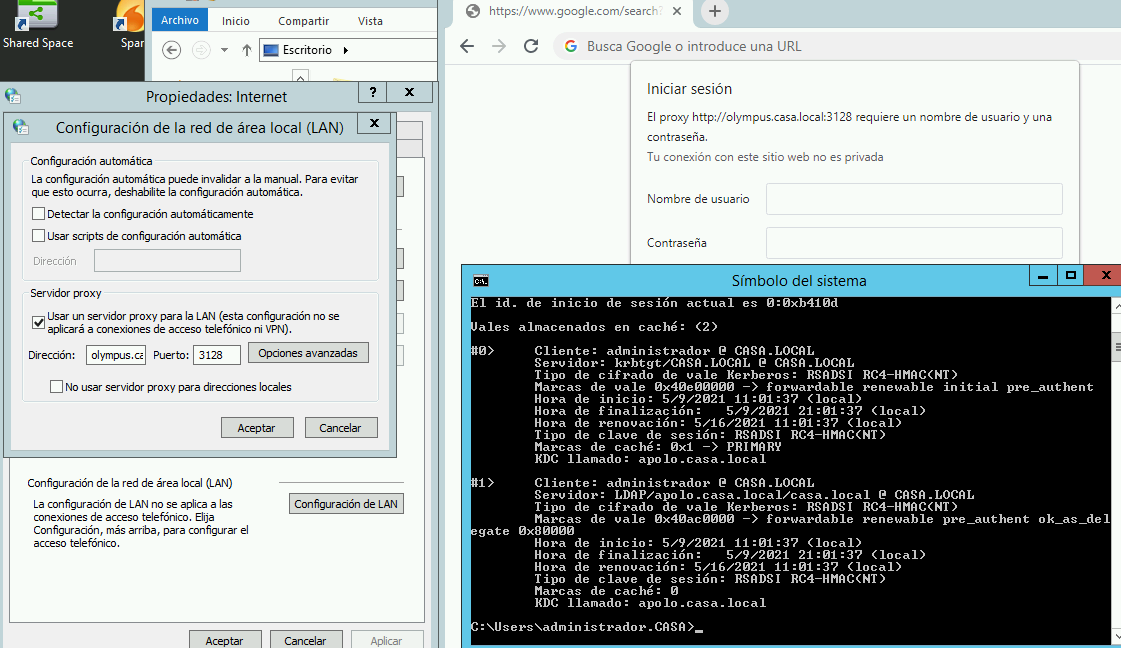
Thanks for the reply, as the proxy this is how i have it configured
when i open chrome and then check the klist i get the ticket
C:\Users\administrador.CASA>klist El id. de inicio de sesión actual es 0:0xb410d Vales almacenados en caché: (2) #0> Cliente: administrador @ CASA.LOCAL Servidor: krbtgt/CASA.LOCAL @ CASA.LOCAL Tipo de cifrado de vale Kerberos: RSADSI RC4-HMAC(NT) Marcas de vale 0x40e00000 -> forwardable renewable initial pre_authent Hora de inicio: 5/8/2021 16:21:07 (local) Hora de finalización: 5/9/2021 2:21:07 (local) Hora de renovación: 5/15/2021 16:21:07 (local) Tipo de clave de sesión: RSADSI RC4-HMAC(NT) Marcas de caché: 0x1 -> PRIMARY KDC llamado: apolo.casa.local #1> Cliente: administrador @ CASA.LOCAL Servidor: LDAP/apolo.casa.local/casa.local @ CASA.LOCAL Tipo de cifrado de vale Kerberos: RSADSI RC4-HMAC(NT) Marcas de vale 0x40ac0000 -> forwardable renewable pre_authent ok_as_del egate 0x80000 Hora de inicio: 5/8/2021 16:21:07 (local) Hora de finalización: 5/9/2021 2:21:07 (local) Hora de renovación: 5/15/2021 16:21:07 (local) Tipo de clave de sesión: RSADSI RC4-HMAC(NT) Marcas de caché: 0 KDC llamado: apolo.casa.localBut not sure what else im doing wrong, currently running zentyal as my domain controller
Thank you
-
@killmasta93 Dirección, you set the IP, told you to use the hostname and not the IP.
Change that 192.168.3.254 and use the proxy hostname, hostname.casa.local -
@mcury
thanks for the reply so i changed to hostname but still get the popup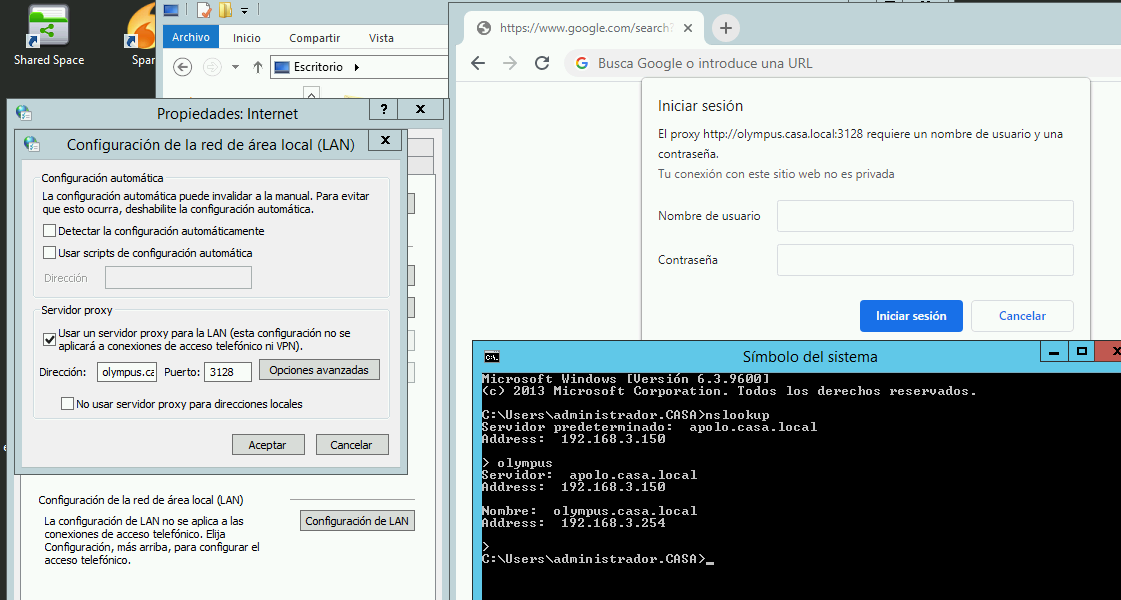
i also checked if the get the ticket
im not sure if the above steps when configuring squid i did it correctly which i think might be the problem?
-
Check if your pfsense can perform the following command successfully.
kninit administrator
If it works, update here and we follow from that.
-
@mcury
Thanks for the reply this is what i get[2.4.5-RELEASE][root@Olympus.casa.local]/root: kinit administrador administrador@CASA.LOCAL's Password: [2.4.5-RELEASE][root@Olympus.casa.local]/root: klist Credentials cache: FILE:/tmp/krb5cc_0 Principal: administrador@CASA.LOCAL Issued Expires Principal May 9 20:09:35 2021 May 10 06:09:35 2021 krbtgt/CASA.LOCAL@CASA.LOCAL -
Now check if your pfsense can perform these commands:
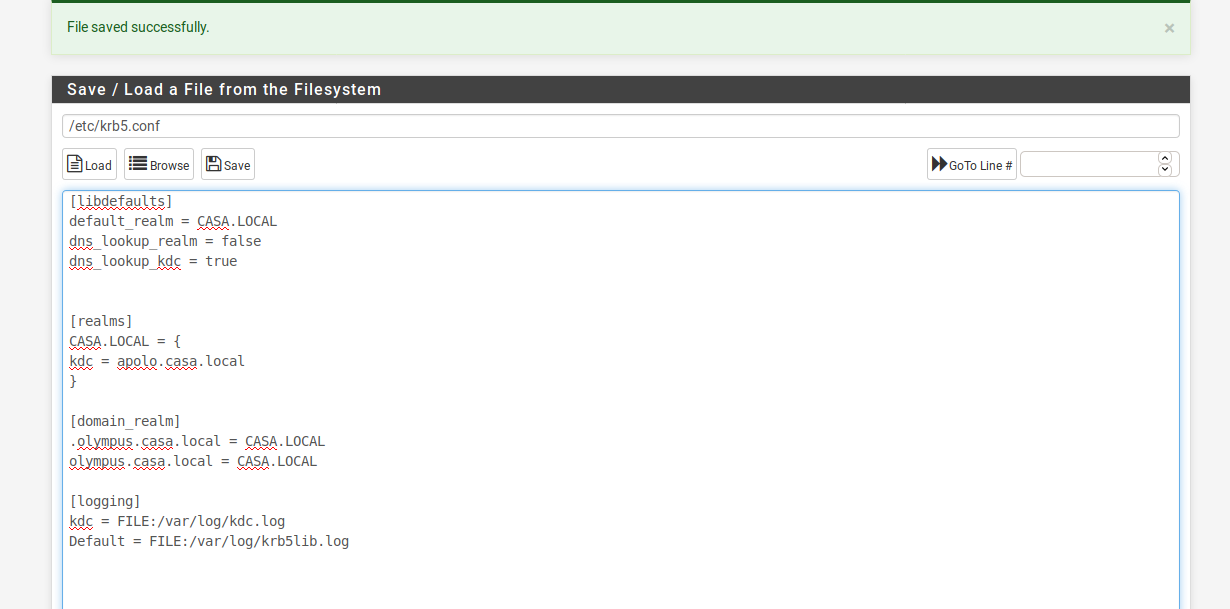
Assuming that olympus is the hostname of the AD DNS server and the domain is casa.localhost -t SRV _ldap._tcp.casa.local. host -t SRV _kerberos._udp.casa.local. host -t A olympus.casa.local.I would remove these lines from krb5.conf to test:
You will need to generate a new keytab after changing these settingsdefault_tgs_enctypes = aes128-cts-hmac-sha1-96 default_tkt_enctypes = aes128-cts-hmac-sha1-96 permitted_enctypes = aes128-cts-hmac-sha1-96 -
@mcury said in Kerberos Squid without authentication?:
host -t A olympus.casa.local.
Thanks for the reply, as for the AD DNS the server is called apolo which has an ip of 192.168.3.150 and olympus is the pfsense with IP 192.168.3.254
i ran the following commands without removing the lines and seemed to worked
[2.4.5-RELEASE][root@Olympus.casa.local]/root: host -t SRV _ldap._tcp.casa.local. _ldap._tcp.casa.local has SRV record 0 100 389 apolo.casa.local. [2.4.5-RELEASE][root@Olympus.casa.local]/root: host -t SRV _kerberos._udp.casa.local. _kerberos._udp.casa.local has SRV record 100 100 88 apolo.casa.local. _kerberos._udp.casa.local has SRV record 0 100 88 apolo.casa.local. [2.4.5-RELEASE][root@Olympus.casa.local]/root: host -t A apolo.casa.local. apolo.casa.local has address 192.168.3.150 -
@killmasta93 said in Kerberos Squid without authentication?:
[2.4.5-RELEASE][root@Olympus.casa.local]/root: host -t SRV _kerberos._udp.casa.local.
_kerberos._udp.casa.local has SRV record 100 100 88 apolo.casa.local.
_kerberos._udp.casa.local has SRV record 0 100 88 apolo.casa.local.I would remove the following lines from krb5.conf to test:
You will need to generate a new keytab after that, then replace the keytab in pfsense, and logout and login again with the client to test.Following lines to remove will use the default enctypes.
default_tgs_enctypes = aes128-cts-hmac-sha1-96
default_tkt_enctypes = aes128-cts-hmac-sha1-96
permitted_enctypes = aes128-cts-hmac-sha1-96 -
@mcury
Thanks for the reply, so did the following deleted the following lines and recreated the keytab but same issue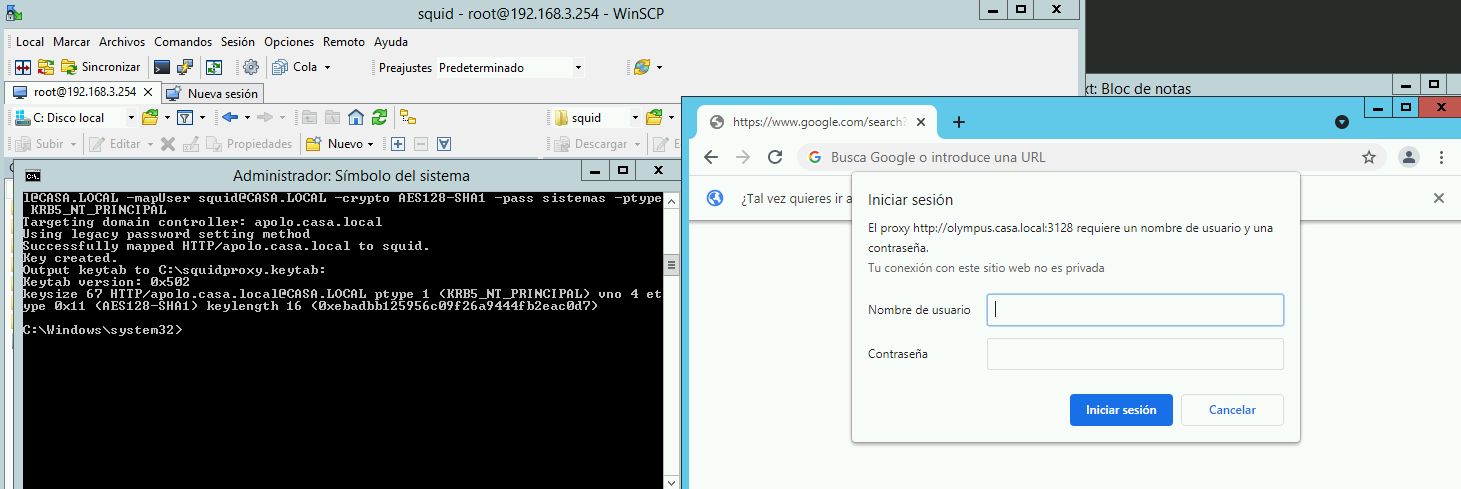
-
auth_param negotiate program /usr/local/libexec/squid/negotiate_kerberos_auth -d -k /usr/local/etc/squid/squidkeytab.keytab
auth_param negotiate children 1000
auth_param negotiate keep_alive on
acl auth proxy_auth REQUIRED
http_access deny auth
http_access allow authname is squidkeytab.keytab and not squidproxy.keytabb ?
-
@mcury
Thanks for the reply, just realized that it was an error but after changing same issue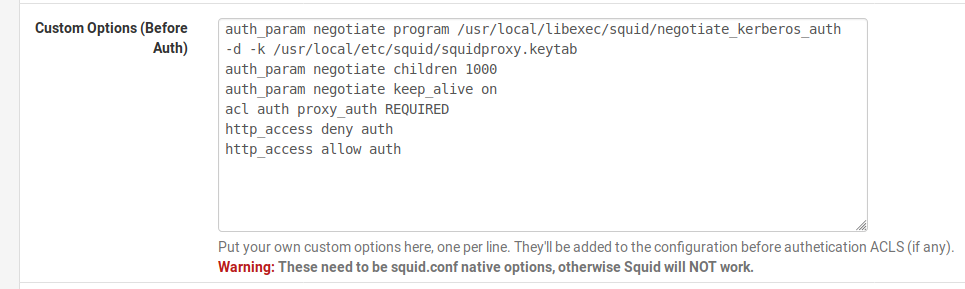
-
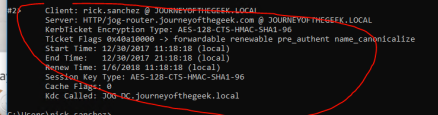
This is the ticket that should appear in klist..Everything seems to be OK with your configuration, at least between pfsense and AD.
Show squid logs again after changing the keytab.
Can you test with another client? -
@mcury
Thanks again for the reply, so im trying another machine which is in the domain but same issue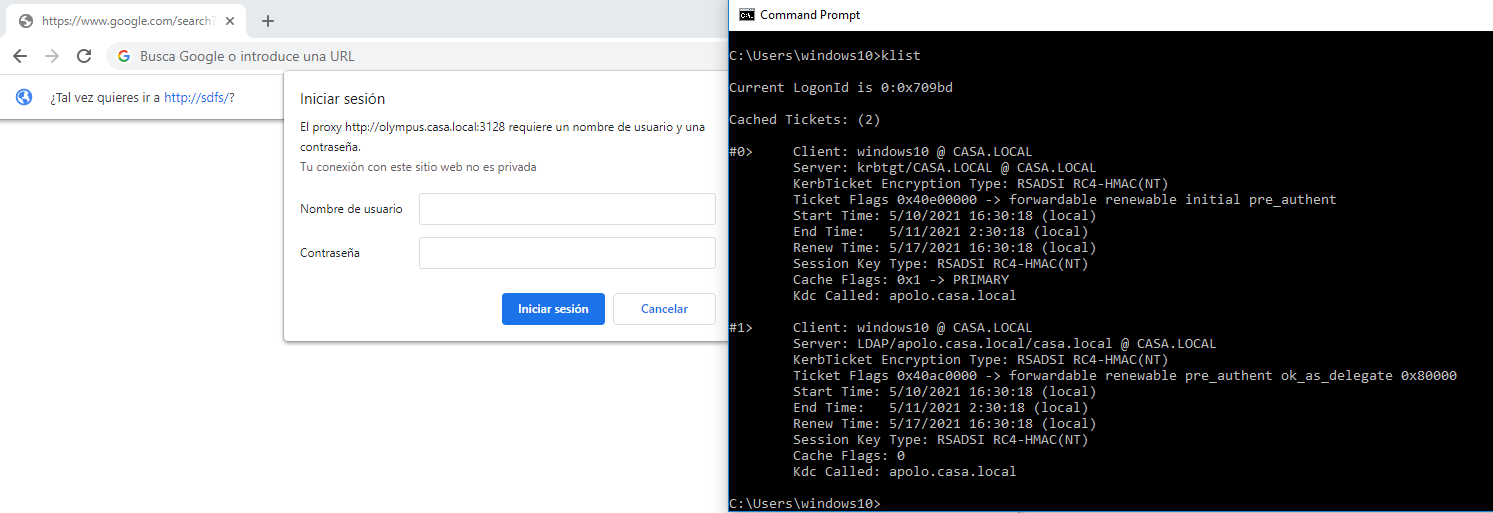
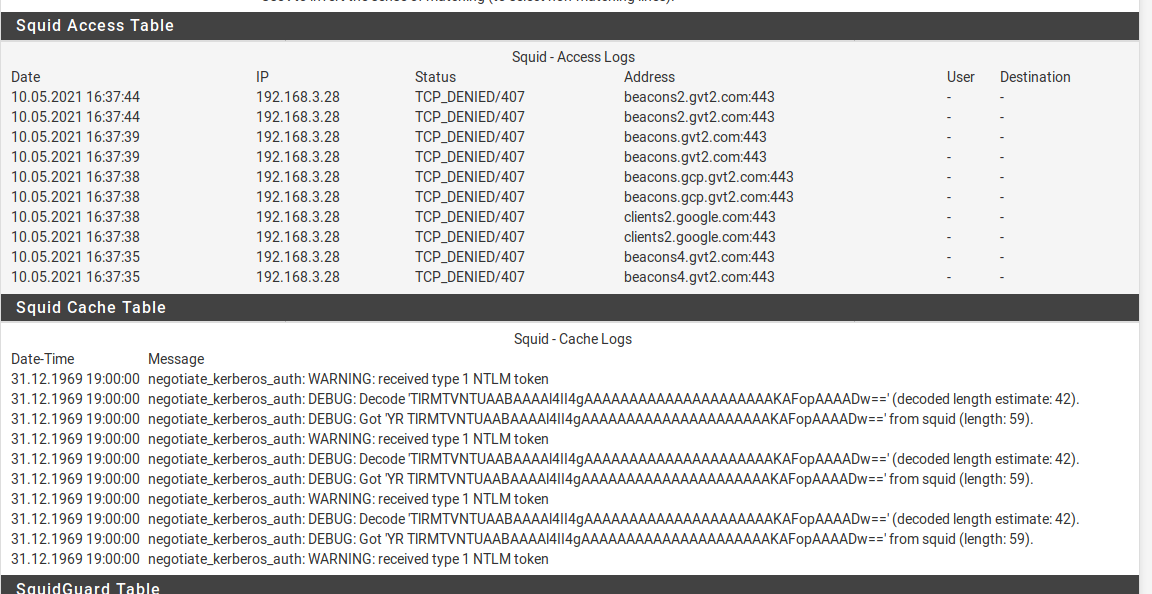
-
Did you create the user and enabled it in AD ?
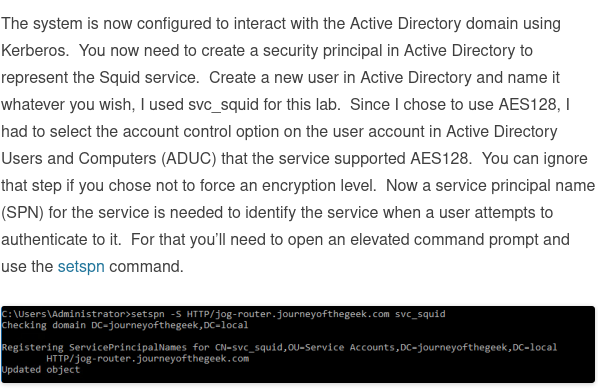
-
@mcury
Thanks for the reply, correct already did that
on the Service principal name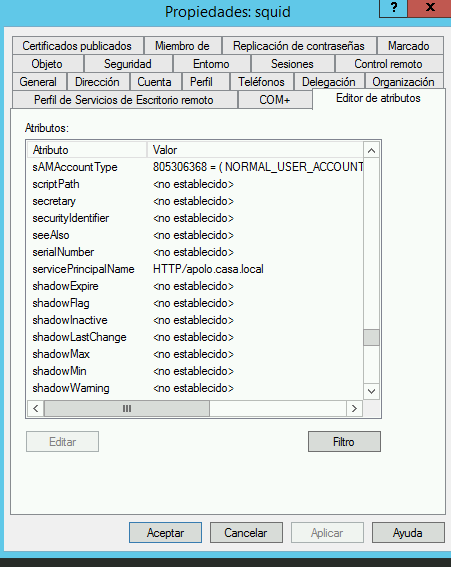
-
Maybe you are facing the same problem as this guy was, take a look:
Quote:
You should see a request from the client to Active Directory asking for a TGS for HTTP/<fqdn of proxy>. If that does not happen or get refused by AD the client will fall back to NTLM (wrapped into the Negotiate response) which is waht you see on the proxy.I would set a packet capture like that guy did to check, port 88