First configuration : NAT
-
Hello,
I'm quite lost with NAT I think.
I'm trying to configure a 3 interfaces SG-1100:- WAN = 192.168.1.253/24
- DMZ = 10.10.12.254/24 + Linux server @ 10.10.12.1
- LAN = 10.10.10.254/24
LAN to WAN (outbound NAT) looks working.
LAN to DMZ (1:1) is not.
WAN to DMZ (port forward) not testedWhat I want : each 10.10.10.0/24 IP to be nat 1:1 on DMZ interface in 10.10.12.0/24.
So I tried 1:1 with :- Interface : DMZ
- External IP : 10.10.12.0/24
- Internal IP : 10.10.10.0/24
But I can't manage to ping 10.10.12.1 from my lan :/
Any idea what I should look at?Side question: how do I get rid of all "IPv6 alerts" in system logs?
-
@freyja said in First configuration : NAT:
What I want : each 10.10.10.0/24 IP to be nat 1:1 on DMZ interface in 10.10.12.0/24.
Why? What are you really trying to do here?
-
@freyja said in First configuration : NAT:
LAN to DMZ (1:1) is not.
Huh? Why would you be natting anything between 2 rfc1918 network?
-
@kom said in First configuration : NAT:
Why? What are you really trying to do here?
@johnpoz said in First configuration : NAT:
Huh? Why would you be natting anything between 2 rfc1918 network?
I want to mask my internal network.
My server (10.10.12.1) is in DMZ and all my other devices are in LAN.
I want to be able to communicate directly with any device in LAN from my server for several purpose (like SNMP monitoring, Syslog; NFS, SMB, etc).
I want any of my LAN device to have a unique IP in DMZ.
Exemple: my internal switch with IP 10.10.10.253 in LAN must be seen as 10.10.12.253 in DMZ
As I have many devices in my LAN, I would like to NAT all of them at once and not one by one.Note: it is something I'm already doing with my PIX, I would like to reproduce the same behaviour.
static (inside,dmz) 10.10.12.0 10.10.10.0 netmask 255.255.255.0Note2: not doing so would mean I have to reconfigure absolutely every services on my server and I would like not to do it if possible.
-
@freyja said in First configuration : NAT:
I want to mask my internal network.
What? Mask it from who? Yourself?
-
@johnpoz no, from anyone that would be able to connect to my server in DMZ and able to successfully exploit a vulnerability.
Should I really need to explain why I want to do that?
The simple answer is : I was doing this with my Pix and all my configuration is based on that.I want to reproduce this behavior.
Isn't it possible with pfSense?
Does it have any drawbacks? -
@freyja said in First configuration : NAT:
from anyone that would be able to connect to my server in DMZ and able to successfully exploit a vulnerability.
You understand if your calling it a dmz.. it wouldn't be able to even connect to your lan - no matter if they know the IP or not..
While you can allow connections from your lan to your "dmz" vlan - just set your rules so that anything in the dmz can not start a conversation with anything in your lan.
Or just allow specific that you might need, for example some of my restricted vlans.. like my roku vlan can talk to my plex on port 32400.. But they need to know what that IP is, etc.. Be it hidden or not wouldn't matter.. If say they exploited some box and know that it was talking to plex be it IP looking like it was 10.1.10.x or 10.1.12.x etc.. The traffic is either allowed or not - masking what the IP is does nothing.
Example - here is a limited vlan example. devices in this vlan can ping pfsense IP in that vlan, dns and ntp. But everything else is not possible.
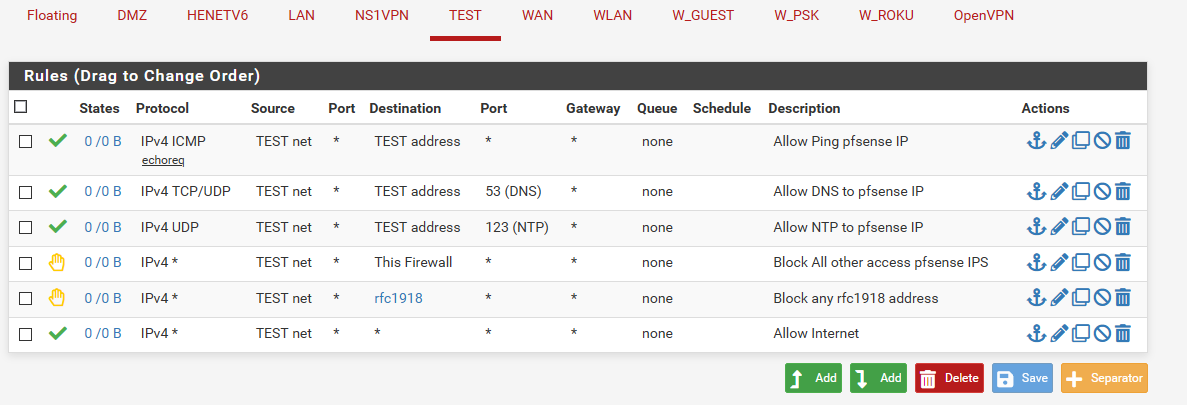
-
@johnpoz I understand all of that... I shouldn't have to say it but I work in computer security for more than twenty years, so yeah I know all of that.
This is not my question, I would like to know if it's possible to do it or not?
Because I don't want to have to reconfigure anything and my reasons to obfuscate my lan stand because I don't like simplify the job for hackers. But really, why should I have to justify myself on something rather standard?
-
Sure you can nat to anything you want - you would just have to set it up... Just POINTLESS..
Not asking you to justify anything - just trying to understand why anyone would do such a thing.. Does nothing but over complex something that serves no purpose. And provides no extra anything from a security standpoint.
-
@johnpoz please stop because it's going nowhere.
That's your opinion, not mine.
Simply the fact that I would not have to reconfigure everything should be enough for you.I just want to know how to do it. If you don't want to help, fine, but please stop with what you are doing
-
@freyja I can't get it working either after playing with it for a few minutes. I wonder if this is another manifestation of the multi-wan NAT bug?
-
For this to work - the IPs that would be natted would have to exist on pfsense interface - so @KOM you setup vips in this 10.1.10 network on pfsense?
If you have a network 10.1.10 as lan, and 10.1.12 as dmz
And you want to hit 10.1.10.X and get natted 1:1 to dmz that .X would have to be an IP on pfsense lan interface. Or why would the traffic ever get sent to pfsense to get natted and sent to its 1:1 match up in 10.1.12
Here - I setup a vip on my lan 192.168.9.32, setup a 1:1 nat to 192.168.3.32 (my dmz vlan)
Now I ping 192.168.9.32 from client on my lan 192.168.9.100, it gets answers. And via the sniff done on pfsense dmz interface you can see the traffic was sent and answered by 192.168.3.32
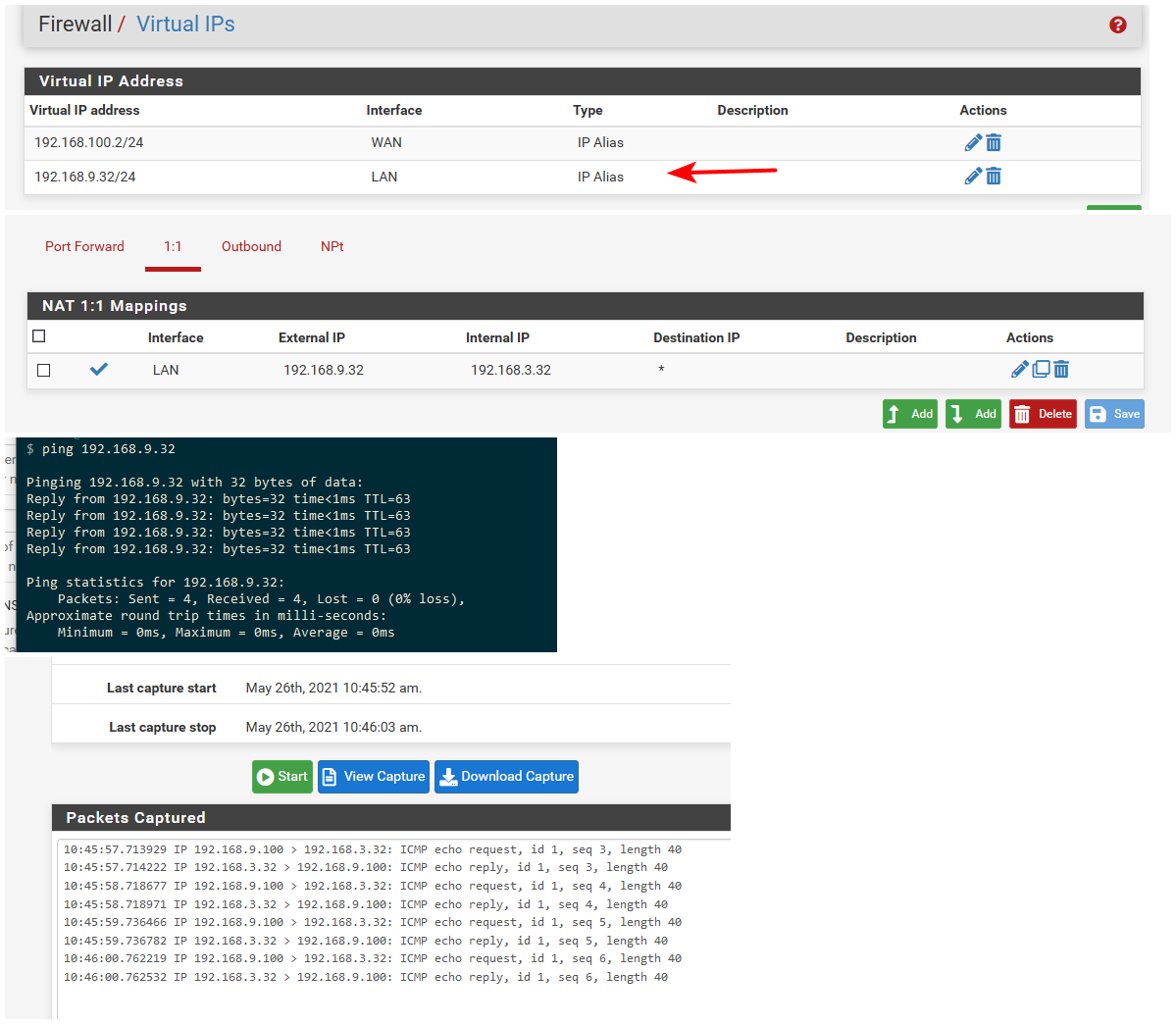
Now if this has something to do with the multi wan nat issue - but seems to be working as expected on 21.02.2
This sort of setup just doesn't make any sense from any way you look at.. Be it you hide the actual IP from lan or not - the access is still there..
-
@johnpoz Sure did. When I couldn't get it going, I double-checked the docs at
https://docs.netgate.com/pfsense/en/latest/nat/1-1.html
In my KVM lab, I created my VIP on my DMZ, then a 1:1 NAT to a Mint box on LAN. Server on DMZ could not ping the VIP successfully. Now I also have block rules on DMZ to prevent traffic to LAN, but I assumed the NAT would bypass that. Perhaps I'm wrong?
-
Do you have rule that prevents access to your vip?
-
@johnpoz The DMZ, VIP and ubuntu server are all on the same subnet so rules shouldn't matter, but no I don't have anything specific to that VIP.
Block to VLAN20 net
Block to LAN net
Allow DMZ to Anyand that's it.
-
So you still need a rule that allows the nat.. Here I just blocked access on lan to 192.168.3.32
And if try and ping 192.168.9.32 it fails.
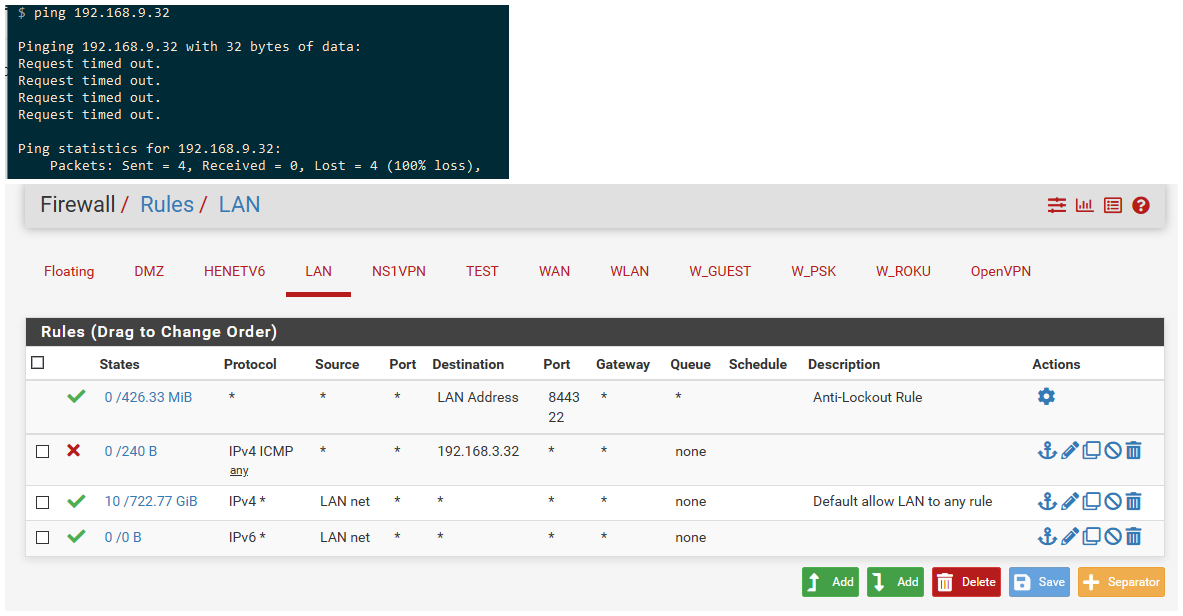
-
@johnpoz I added an Allow rule on DMZ for my VIP and it still doesn't work.
Do me a favour and recreate your test going the other way, DMZ to LAN instead of LAN to DMZ? My tiny brain is spinning trying to keep my lab setup, your config and his config all straight.
Meanwhile it's lunchtime. Back in a few.
-
Ok flipped it - doesn't matter
Put the vip on the dmz interface, setup the 1:1 nat on the dmz interface, created a firewall rule to allow that access to the 9.100 IP..
Works just fine..
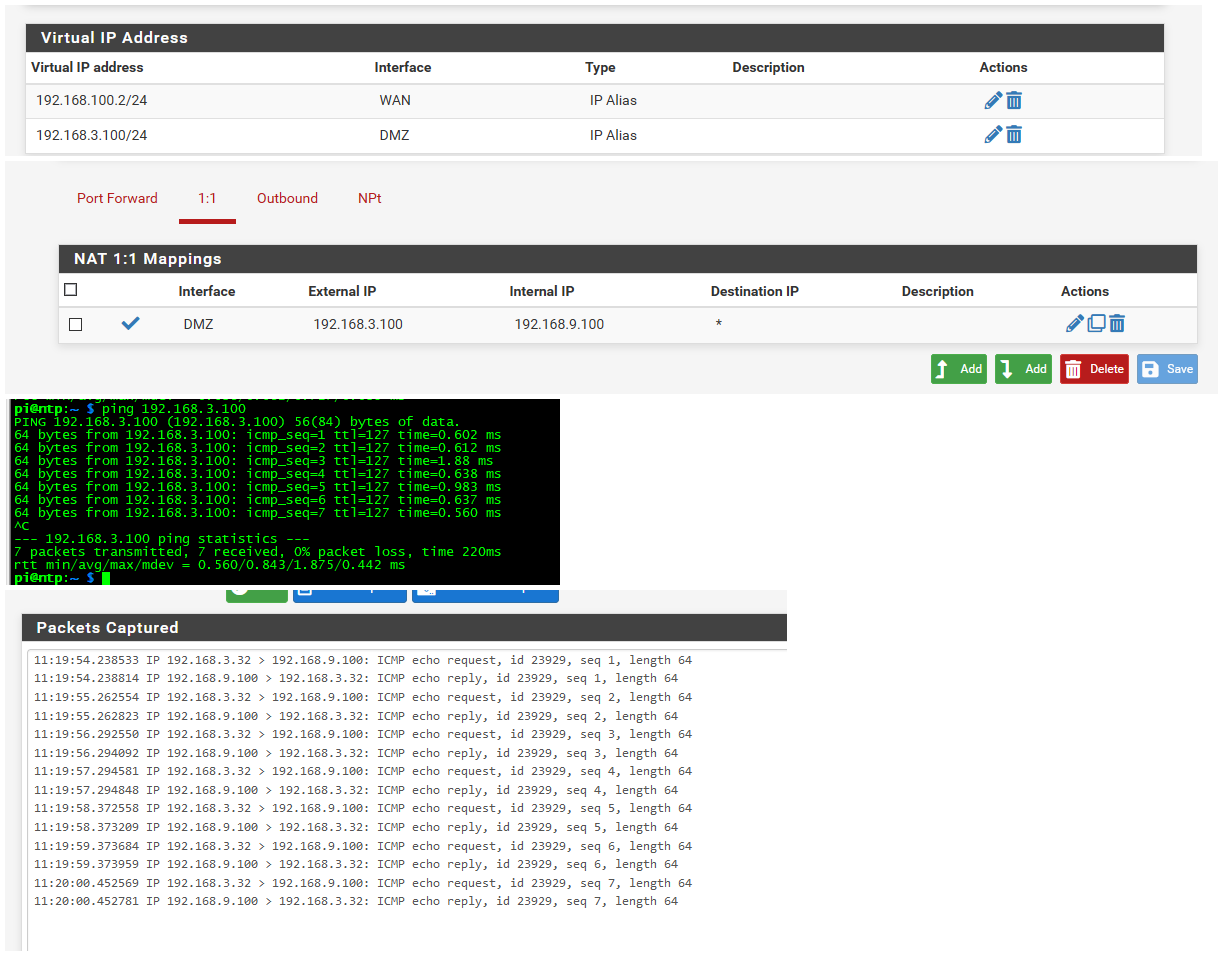
For my next trick - I will go wash my car in the rain.. Then water my lawn.. Same sort of nonsense as doing this sort of thing.
-
@johnpoz OK I got it working. I had my allow rule pointing to my VIP instead of the LAN address I was natting to.
-
Yeah the nat rule is evaluated before the firewall rule - but the actual traffic has to be allowed for it to work.. Just like any normal port forward..