route one site via openvpn
-
Trying to route one site via a openvpn configuration.
Was able to setup the openvpn client and it is connected
trouble I am having is routing the desired traffic over the vpn.
I tried to create rules by both port and ip however none of them actually catch the traffic
under firewall I tried
Lan ---

VPN --

will be first to admit I may be missing something obvious. Would like to limit routing to specific ip/port as dont want to route all traffic form that device via VPN.
thanks
-
@l4z0a5
Which VPN is this? A site2site where both are managed by you or a VPN provider you connect with your client to?Which kind of traffic do you want to route over? Is it upstream traffic or is the destination device on the remote site?
-
The vpn provider is keepsolid. Set it up as a client based on their docs and it does show up.
 )
)I am wanting to route my iptv via the vpn as the isp appears to throttle streaming. I tried with an alias for either the url or port as it is unique for it.
-
@l4z0a5
Did you configure the Outbound NAT for the VPN? -
@l4z0a5 Your LAN rule shown above currently has all traffic from LAN net (everyone) from any port going to destination KeepSolidVPN to any port. What's in the KeepSolidVPN alias? You don't route traffic by using the address of the VPN as the destination. The destination is where you're trying to go. The VPN is just the gateway to get there.
If you want to route one client's traffic out the VPN, the Source should be that client's IP address, any port, any destination, any port, gateway your VPN. Don't forget to reset the states for that client or the existing states will continue out the default gateway.
-
thanks guys
this is my outbound NAT. I may have added one of the rules to see if it made a difference.
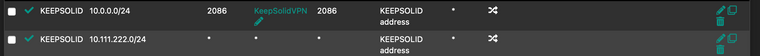
my alias is
KeepSolidVPN site1.com, site2.comMy thought on the firewall rule was that it would see all traffic on the LAN match traffic based on the info in keepsolidvpn and route traffic that matched to the keep solid gateway. Tried the same with ports as well without luck.
I specifically want to only route traffic by destination domain or port. The app is on my tv and would like rest of the traffic to go out via regular WAN eg. Netflix.
-
@l4z0a5 You don't need that first nat rule, assuming your lan is 10.111.222.0/24. I don't know what you're trying to do with that rule.
-
This post is deleted! -
The outbound nat rule you just deleted is wrong. Here is an example. I want the IPs in KOM_VPN_USERS to use the VPN tunnel if they try to talk to anything on the 10.10.0.0/16 network. Everything else goes out the default WAN. The outbound NAT rule tells pfSense to send the packets using the OpenVPN interface address. My home network is 192.168.88.0/24.
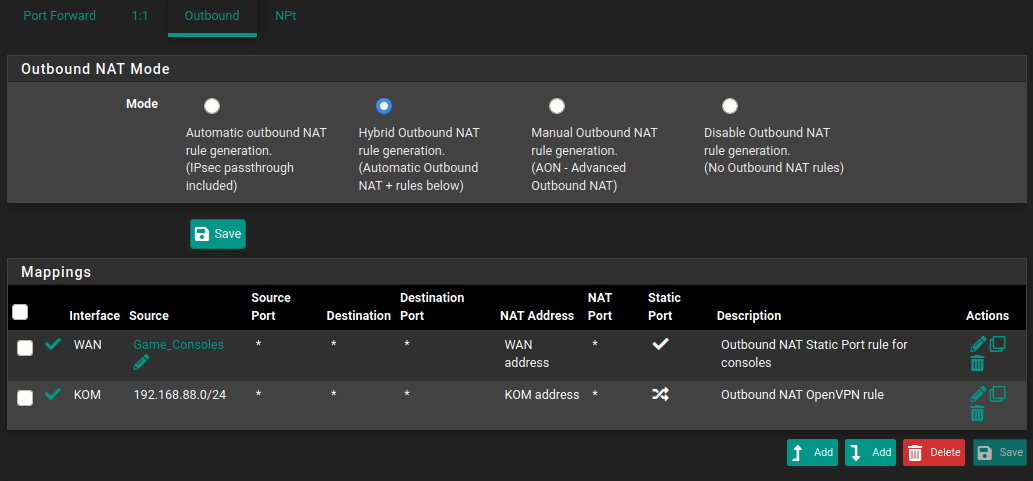
-
@kom
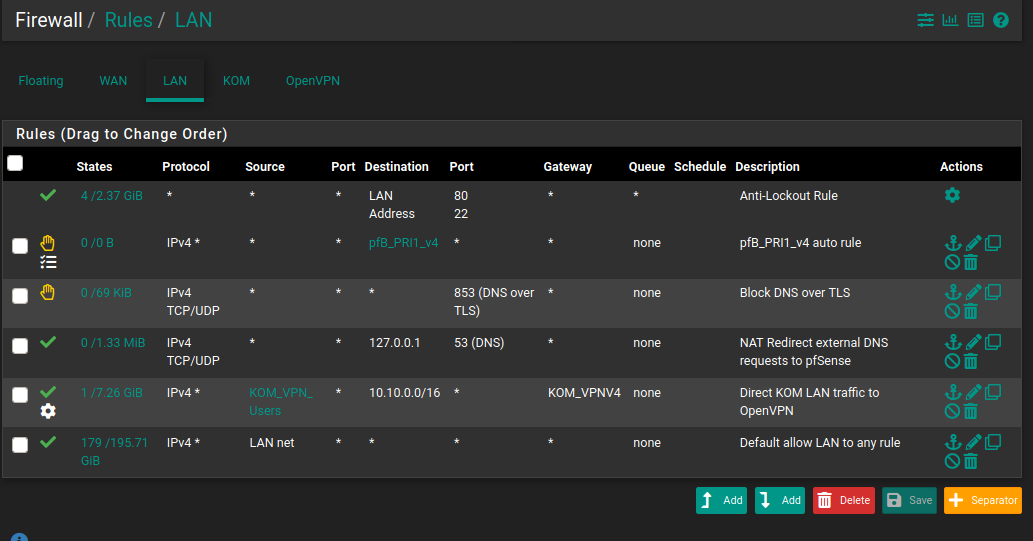
Thanks KOM.. finally got it work had more than one issue but all good now. more testing but setup an alias to https://www.whatismyip.com and shows neither my WAN or other VPN gateway :)my rules just incase anyone ever has the same thing
Alias:

Firewall -> Rules -> LAN
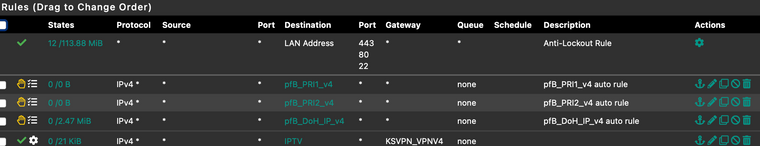
KSVPN Just the name I gave it under Interfaces/Interface AssignmentsFirewall/NAT/Outbound

how I ended up here
one of the issues I had was the gateway was actually down.
tried to route via existing vpn which finally got to work with the proper NAT rules.
Changed the monitoring gateway to 8.8.8.8 which then showed the gateway up
-
@l4z0a5 said in route one site via openvpn:
Changed the monitoring gateway to 8.8.8.8 which then showed the gateway up
Then you're not really monitoring the gateway but Google. The IP address and gateway for the tunnel should be provided by the server end when they first connect.
-
@kom I agree with you but for some reason it was failing to ping the gateway. thanks for your help along the way

