First configuration : NAT
-
Do you have rule that prevents access to your vip?
-
@johnpoz The DMZ, VIP and ubuntu server are all on the same subnet so rules shouldn't matter, but no I don't have anything specific to that VIP.
Block to VLAN20 net
Block to LAN net
Allow DMZ to Anyand that's it.
-
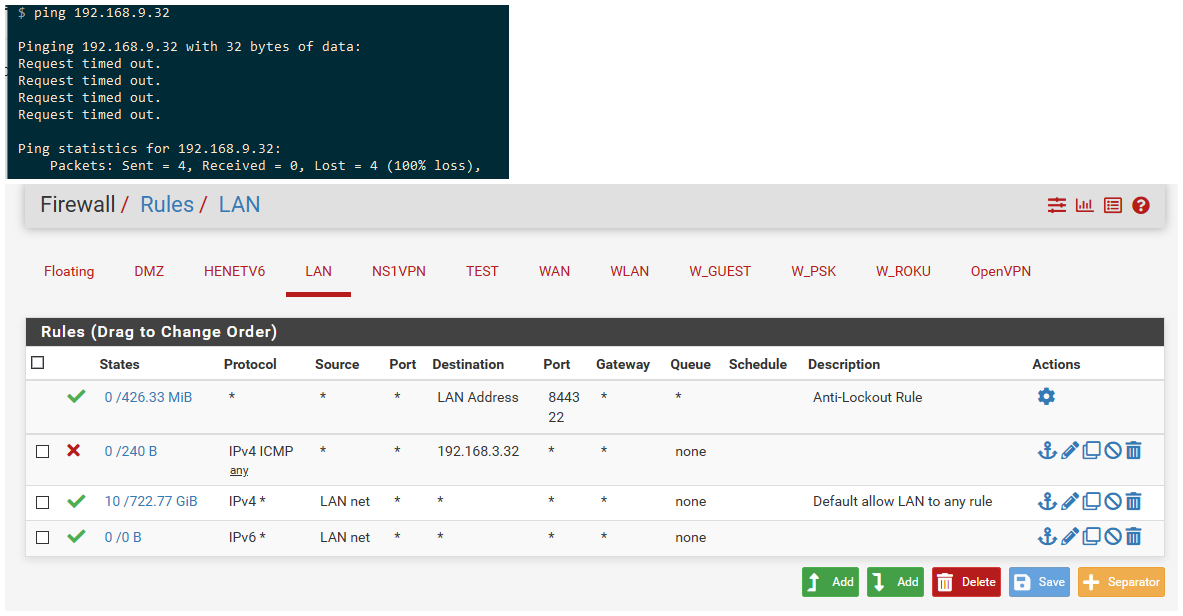
So you still need a rule that allows the nat.. Here I just blocked access on lan to 192.168.3.32
And if try and ping 192.168.9.32 it fails.
-
@johnpoz I added an Allow rule on DMZ for my VIP and it still doesn't work.
Do me a favour and recreate your test going the other way, DMZ to LAN instead of LAN to DMZ? My tiny brain is spinning trying to keep my lab setup, your config and his config all straight.
Meanwhile it's lunchtime. Back in a few.
-
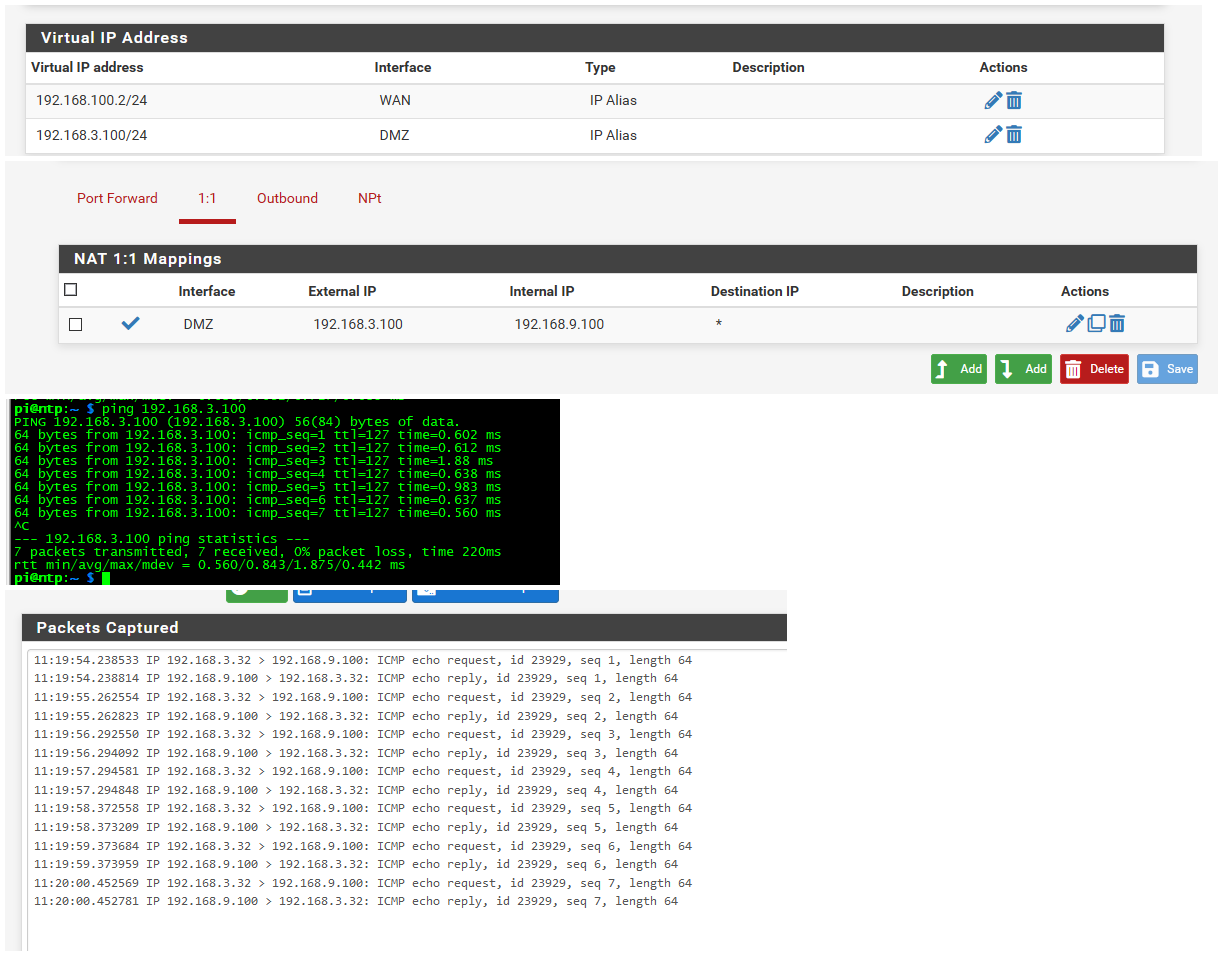
Ok flipped it - doesn't matter
Put the vip on the dmz interface, setup the 1:1 nat on the dmz interface, created a firewall rule to allow that access to the 9.100 IP..
Works just fine..
For my next trick - I will go wash my car in the rain.. Then water my lawn.. Same sort of nonsense as doing this sort of thing.
-
@johnpoz OK I got it working. I had my allow rule pointing to my VIP instead of the LAN address I was natting to.
-
Yeah the nat rule is evaluated before the firewall rule - but the actual traffic has to be allowed for it to work.. Just like any normal port forward..
-
@johnpoz I know all of that which makes it extra-stupid on my part.
-
Hi both, thanks for your investigations.
However, it's not a single IP I would like to nat 1:1 but a whole network.
If you need screens, I'll post them this afternoon.
-
And how would you do that when some IPs on the network you want to nat are on device on that L2..
If you have 10.1.10 on A, and 10.1.12 on B you can not 1:1 nat either of those for a whole network.. You would need a 3rd network. Say 10.1.11
-
@johnpoz why that ?
Of course I would not NAT the server IP.
Honestly, it's working with the Pix and it's bugging me it's not working with pfSense/Netgate :(Should I make a NAT exception for the Server IP and the pfSense IP (if possible)?
-
You can't have the same IP in 2 places. if you have device 10.1.10.x on a device in A, how can you also say 10.1.10.x nats to 10.1.12.x
In my example, I don't have a 192.168.9.32 device, nor do I have a 192.168.3.100 device
-
@johnpoz I don't have such device, the only concern is how pfsense is handling arp, does it create a nat only when a device goes through the netgate or does it make a reservation for the whole network ?
Basically if internall I don't have a 10.10.12.1 device, i will not have any problem reaching the server in DMZ, of course if I have a 10.10.10.1 device and try to reach 10.10.12.1 from it, it wont work but that's not what I have.
So should I configure a /24 1:1 NAT (with eventually a NAT exclusion if necessary and possible) or should I break it down in smaller subnets (/25, etc)? Better option: can we nat an IP range instead of a subnet?
-
If you create vip in a range.. It will answer arp for any of those IPs.. The only way to create such a range is via the proxy arp vip.
This can be problematic if you have a host in that actual range. On which device answers the arp first, or at all..
Like I said your complicating the design of the network - for no real added security at all. More complex leads to greater chance of issues, greater chance of configuration mistakes..
There is really no reason to nat rfc1918 to rfc1918.. I could see doing it if you were trying to get a device without a gateway to talk to something else in another vlan.. If you needed vlans that are on the same IP space to be able to talk to each other.. There are some reasons where you might have to do it.
I am not seeing it at all in this scenario.. It sure is not a security anything to do it this way, if anything it reduces your overall security because your more complex setup makes for more likely mistakes that expose more than you desire.
-
@johnpoz there are plenty of reasons I'm doing this but that's not the subject (again, the simple fact I want to reproduce what I already have should be enough for you).
I guess I will have to find by myself or ask somewhere else.
At least with cisco I had plenty of different scenarii cases I can try (with plenty of errors I have to admit).
I've never been in front of such hostility on what I'm trying to implement.
-
@freyja No hostility. Asking why you're doing what you're doing isn't an attack. Maybe you're doing something unusual to get around some edge case we haven't seen before and we could learn from it. Either way you seem quite reluctant to explain what you're doing.
there are plenty of reasons I'm doing this
Like what, for instance?
In a lot of cases, people decide on a course of action that is either wrong or sub-optimal and they ask specific questions when they would be better off explaining what they want to accomplish and getting suggestions on the best way to do it with pfSense.
Anyway, you have been given your NAT solution. There is no automatic way to map every LAN client to a VIP on your DMZ and a NAT for that VIP. You will have to set them up one by one.
-
Hi,
I was able to make the NAT work, it was a typo in the subnet mask of the interface (/32 instead of /24).
My inside devices are correctly natted into DMZ according to their LAN IP (i.e. 10.10.10.20 natted to 10.10.12.20).However, it looks like I have an ARP problem, the netgate doesn't answer arp request for these IP except its own IP.
If I force the entry in ARP table of my server the flow is working perfectly.
Any idea ? -
Here is a short extract of tcpdump on dmz interface of netgate:
11:56:35.832233 ARP, Request who-has 10.10.12.102 tell 10.10.12.1, length 46
11:56:35.896216 ARP, Request who-has 10.10.12.100 tell 10.10.12.1, length 46
11:56:35.896226 ARP, Request who-has 10.10.12.201 tell 10.10.12.1, length 46
11:56:36.339999 ARP, Request who-has 10.10.12.48 tell 10.10.12.1, length 46
11:56:36.877575 ARP, Request who-has 10.10.12.102 tell 10.10.12.1, length 46 -
As an addition, I think there were some misunderstanding somewhere.
I'm not using any VIP, I'm using only interface IP and I do not see anywhere how to configure ARP -
@freyja said in First configuration : NAT:
I'm not using any VIP
Then why in the world would you think some interface would answer an arp request, when it doesn't have that IP on it..
If you want pfsense to answer arp for an IP that is not assigned to the interface - it needs a vip, if you want it to answer arp for every IP in a cidr then setup a proxy arp vip.
https://docs.netgate.com/pfsense/en/latest/firewall/virtual-ip-addresses.html#proxy-arp
Where you could have an ISSUE - which I thought I went over with already. Is if you have pfsense arp for any IP in /X - if you have some device on the network with an IP. Which arp is your client looking for IP abc going to see first - the actual client, or pfsense vip?