Routing from a VLAN to a specific interface for just one not connected IP address
-
@ymcan said in Routing from a VLAN to a specific interface for just one not connected IP address:
(10.1.0.5) sits behind a router on the MGMT
You need to make a Gateway
System -> Routing -> GatewaysAnd make it point to the router ip on the MGMT , that "has" the (10.1.0.5) ip behind it.
Then you need to make a static route
System -> Routing ->Static RoutingDefining the the single ip of interest : 10.1.0.5/32 , with a gateway name of the one you created above.
Remember that 10.1.0.5 must also know how to get back to the pSense ip conecting to it.
/Bingo
-
@bingo600: Thank you for the fast reply, I really appreciate that.
Just one question, would doing this not also route traffic from the LAN and Client VLAN to the MGMT network if someone there tries to access 10.1.0.5? This is the main reason I have not tried this yet, as I only want traffic from the Staff VLAN to be able to reach the IP in question.
-
@ymcan
Yes, it does, but you can controll the access by firewall rules. If you don't allow it, no access is possible. -
@viragomann said in Routing from a VLAN to a specific interface for just one not connected IP address:
@ymcan
Yes, it does, but you can controll the access by firewall rules. If you don't allow it, no access is possible.So let me get this right. I set up the settings @bingo600 gave me, and then set up firewall rules on both the LAN and the Client VLAN that block any traffic to 10.1.0.5.
Just want to make sure I understand.
-
@ymcan
Yes, you can do that. How exactly depends on your needs.For instance, on some interfaces you mitht generelly want to block any access to other internal network, but allow internet access. So best way to achieve this is to create an alias and add all RFC 1918 networks to it (since you only use such now and in the future). Then use this alias at destination in the block rule.
However, consider you have to allow access to your DNS, if you're using an internal like pfSense. So you have to add an additional firewall rule for this and put it above of the block rule.
Below the block rule you can put then an allow any rule for permiting internet access. -
@viragomann
Thank you very much, that is very helpful. I now feel confident in how to set this up. I'll go and give a try, and if I do something wrong, I can always come back and ask again.Abundant blessings
-
I am slowly getting somewhere I think. I can now ping the 10.1.0.5 server from the Staff VLAN, however when I try to browse to https://10.1.0.5:9191/, where there should be a web page, I doesn't work, it just tells me that is not reachable.
This is how my routes are set up:
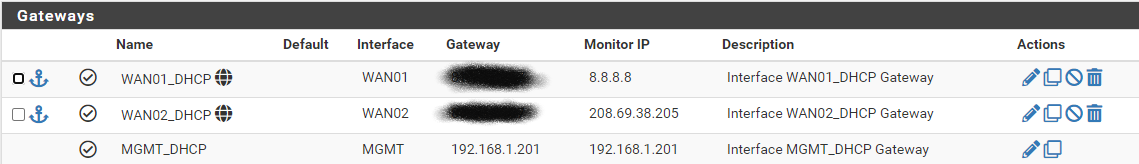
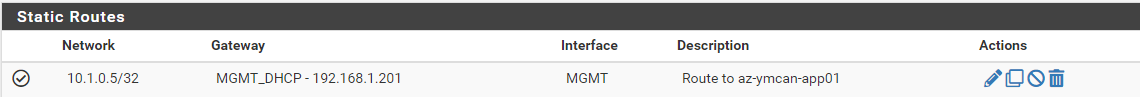
And these are the firewall rules on my STAFF interface:
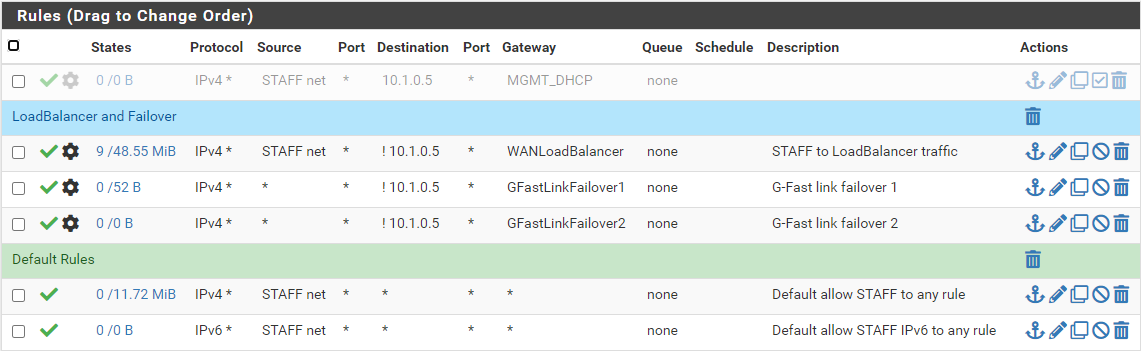
Any help would be greatly appreciated.
-
@ymcan said in Routing from a VLAN to a specific interface for just one not connected IP address:
An additional problem is that the MGMT network has IP range 192.168.1.0/24 and the machine I am trying to route to (10.1.0.5) sits behind a router on the MGMT network.
Does this router use pfSense as default gateway? Otherwise you have to add a static route to it as @bingo600 hinted in the bold line.
If 10.1.0.5 doesn't use this router as default gateway, you have also add a static route to it.@ymcan said in Routing from a VLAN to a specific interface for just one not connected IP address:
however when I try to browse to https://10.1.0.5:9191/,
Does the server respond to this URL?
If yes, does it also respond if the access is coming from outside its network segment? -
@viragomann
Thank you for your reply. I'll follow that up and see if I can get it to work.The one thing that doesn't make sense to me is that I can ping the remote machine, that would suggest to me the routing is working.
-
@ymcan said in Routing from a VLAN to a specific interface for just one not connected IP address:
The one thing that doesn't make sense to me is that I can ping the remote machine, that would suggest to me the routing is working.
No, ping (ICMP) is no garantee for proper routing. There might be an asymmetric routing issue, which doesn't affect ICMP, but will break TCP.
You can check out the route by using a traceroute tool from both networks, from the STAFF and from 10.1.0.5. Both have to pass exactly the same devices.
-
@viragomann
Thank you so much for taking the time to answer my queries, and to educate me, I really appreciate that. I'm learning new things all the time.