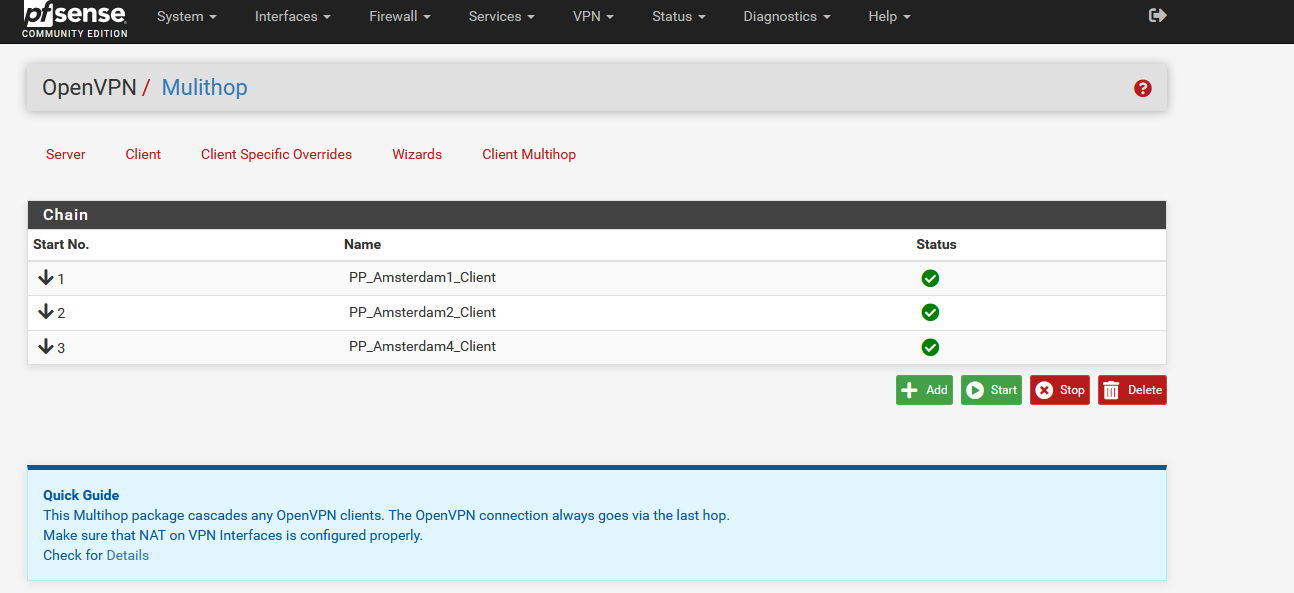
OpenVPN Multihop Package
-
OpenVPN Multihop Package
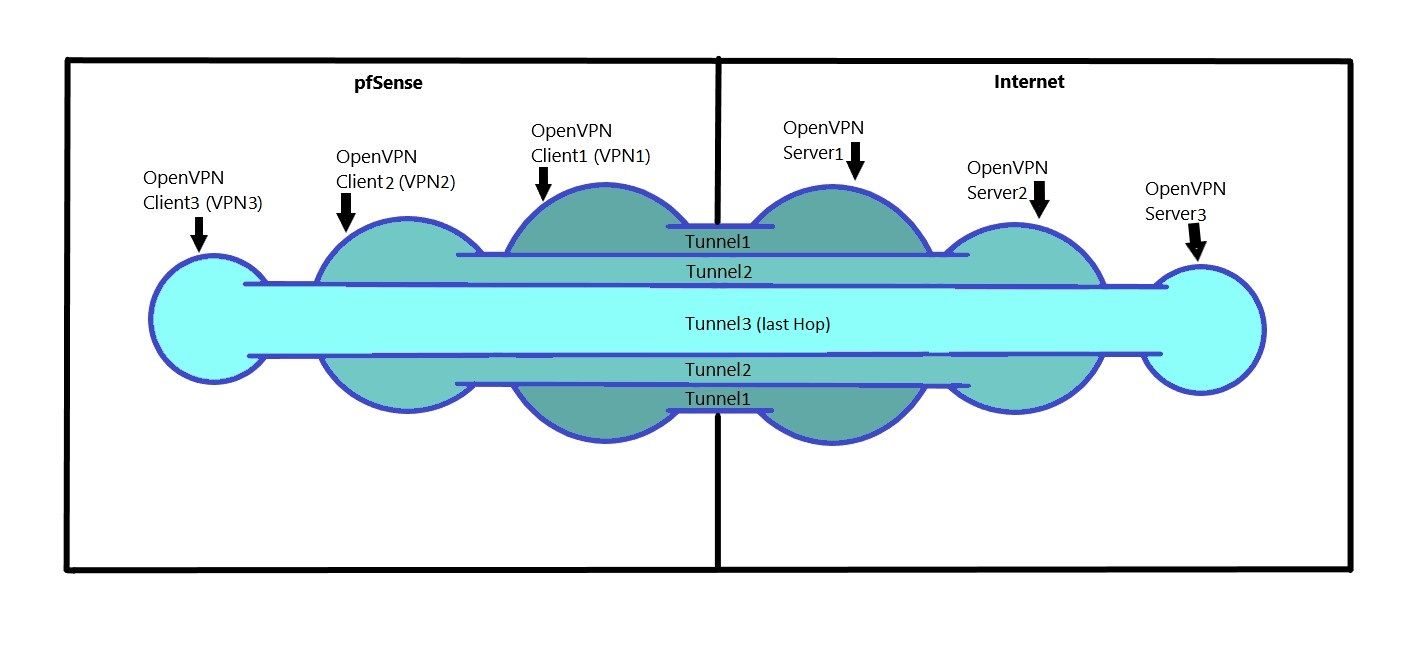
The OpenVPN Multihop Package enables the cascading (tunnel in tunnel) of (2+n) OpenVPN clients via the webconfigurator of pfSense by menu-driven configuration.
The cascading makes the analysis of the network traffic more difficult.
The attacker would still see outgoing encrypted traffic to another VPN server, but he cannot determine whether this is a middle or exit node. To successfully intercept and decrypt the traffic, the attacker would need to have physical access to all hops in the cascade simultaneously.
In addition, the effort required to trace the subscriber's actual connection grows exponentially* with each additional tunnel.
(*) when different VPN service providers are used.
Source from Perfect Privacy Blog.
Available functions:
The OpenVPN Multihop package can handle selective routing, for example. For this you have to deactivate "Add default route" in the last hop and specify the exit node in the LAN interface under Gateway.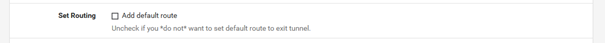
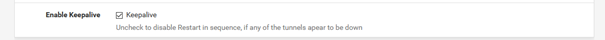
Likewise, the package offers autorestart. If the connection of one of the OpenVPN clients should be interrupted, the package restarts the connection. To do this, activate the "Keepalive" function.
Package advantages:
• Any number of multihops possible
• Combination of different OpenVPN providers possible*.
• No manual configuration via pfSense necessary anymore. Most functions are handled by the Multihop package(*) Please report successes and failures, specifying the configuration and VPN provider.
Disadvantages:
• A hardware with several fast CPU cores required/recommended
(More information)Preparations:
Choose a VPN provider of your choice and create at least two OpenVPN clients. Depending on the VPN provider, a DoT (DNS over TLS) configuration would also be useful.Application:
Description, configuration, installation as well as detailed information about further functions, can be found on Github.At this point a big thanks to the package developer Daniel Dowse.
If you encounter any problems with the package or have any constructive suggestions for improvement, please post them here in the forum or create an issue* on Github. Thank you very much.
(*) https://github.com/ddowse/pfSense-pkg-openvpn-multihop/issues
-
Hi John
This package works well, in particular the keepalive function is brilliant for keeping up unreliable connections.
1 suggestion, the descriptions used for the tunnels changes a bit in the package, can I confirm that the below is correct, maybe you could stick it in the Quick Guide (for dummies :)
The last hop = Start = First tunnel (traffic goes over other VPN tunnel(s), the VPN which sees your traffic)
The first hop = Exit = Last tunnel (traffic goes over WAN interface, the VPN which sees your IP)In your thread describing the manual process (https://forum.netgate.com/topic/157520/openvpn-client-cascade/47) you set floating firewall rules but these dont seem to be set or used by the package, are these still required to stop clients using the wrong interface?
My other question is, does the package handle the "Don't add/remove routes" settings for the tunnels, do you have to configure these before using the package? "Dont pull routes" is ok, i can see that.
Thanks for your time here
-
1 suggestion, the descriptions used for the tunnels changes a bit in the package, can I confirm that the below is correct, maybe you could stick it in the Quick Guide (for dummies :)
The last hop = Start = First tunnel (traffic goes over other VPN tunnel(s), the VPN which sees your traffic)
The first hop = Exit = Last tunnel (traffic goes over WAN interface, the VPN which sees your IP)Example of 3 tunnels:
-
The first hop of VPN Provider A = Start = First tunnel (traffic goes over WAN interface. This is the IP that others see on the Internet. VPN provider A can see that you are connected to VPN provider B.)
-
Hop 2 of VPN Provider B = (traffic goes over other VPN tunnel(s), VPN provider A can see that the traffic from VPN provider B goes through his server. VPN provider A cannot see that you are connected to VPN provider C.)
-
Hop 2 and the last hop of VPN Provider C = Exit = (traffic goes over other VPN tunnel(s), the VPN which sees your traffic, your IP)
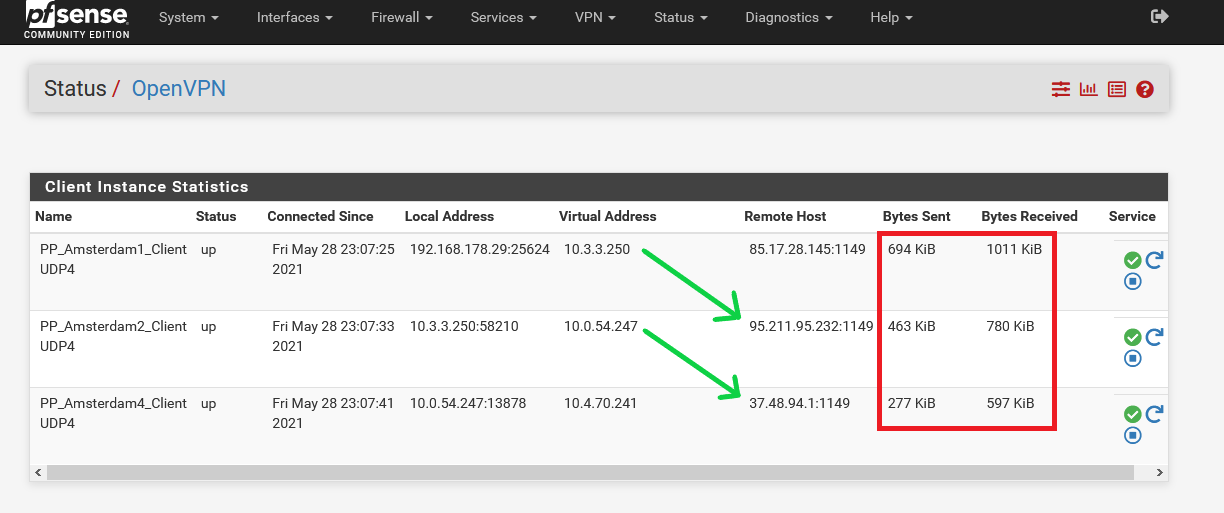
You can see the traffic in the red block. VPN 3 goes through VPN 2 and VPN (3,2) goes through VPN 1. The traffic from VPN 1 is the highest because VPN 3 and 2 go through there.
Status-> Diagnostics-> Routes:

You can see the routes in pictures 2 and 3.
In your thread describing the manual process (https://forum.netgate.com/topic/157520/openvpn-client-cascade/47) you set floating firewall rules but these dont seem to be set or used by the package, are these still required to stop clients using the wrong interface?
Kill switch/floating rules still need to be set for safety.
Theoretically, the Multihop Pakcage could take care of this. It would be more difficult to programme this because the configuration would be too individual for each pfSense user.
My other question is, does the package handle the "Don't add/remove routes" settings for the tunnels, do you have to configure these before using the package?
"Don't add/remove routes" and "route-up" settings are automatically set by Package.
-
-
Hi John
Thanks, but to be clear, does VPN provider C really see both my unencrypted traffic and my home IP?
I thought the cascade would mean VPN C would see my home IP but only VPN A would see my unencrypted exit traffic, with VPN B's IP. Did I get this wrong, is there a difference between nesting and cascading (i thought these were the same)?
I was trying to nest the connections to try and break the chain of trust, so the first one knows who I am but not what I do and the last one knows what I do but not who I am. If you see what I mean ;) As always, thanks for your help and patience
-
Thanks, but to be clear, does VPN provider C really see both my unencrypted traffic and my home IP?
VPN Provider C (last hop, hop3) sees only encrypted traffic from VPN Provider B (hop2) and not your WAN IP.
Internet provider (WAN IP) sees only encrypted traffic from VPN provider A (hop1).
Did I get this wrong, is there a difference between nesting and cascading (i thought these were the same)?
Some VPN providers advertise different technology with multihop. You have to ask the VPN provider how this works.
Nested VPN (tunnel in tunnel) is described here.
You can check the traffic over SSH with these commands:
WAN:
tcpdump -i vtnet0 -vnn port 1149 # change vtnet0 and port 1149VPN1:
tcpdump -i ovpnc1 -vnnVPN2:
tcpdump -i ovpnc2 -vnnVPN3:
tcpdump -i ovpnc3 -vnnI am not an expert in routing. I'm sure others can contribute as well.
I have edited the first image in post 1. Maybe you understand it more clearly now.
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
 W werter referenced this topic on
W werter referenced this topic on
-
@John2893ax
Hello, can you update pkg for 24.03?